NESTA PÁGINA
Exemplo: configure uma malha de ponte com roteamento central EVPN-VXLAN usando roteadores MX como spines
Este exemplo mostra como configurar EVPN e VXLAN em uma malha DE IP para oferecer suporte ao encaminhamento ideal de quadros Ethernet, fornecer segmentação de rede em ampla escala, permitir o aprendizado MAC baseado em plano de controle e muitas outras vantagens. Este exemplo é baseado em uma arquitetura EVPN de ponte (CRB) roteada centralmente em uma malha Clos de 5 estágios.
Nas interfaces IRB de arquitetura crb oferecem conectividade de Camada 3 a servidores e VMS que pertencem a diferentes VLANs e redes. Essas interfaces IRB servem como o gateway padrão para tráfego entre VLAN dentro de uma malha, e também para destinos que são remotos para a malha, por exemplo, no caso da Interconexão de Data Center (DCI). Em um design crb você define as interfaces IRB apenas nos dispositivos spine. Tal design é, portanto, referido como sendo roteado centralmente, pois todo roteamento ocorre nas spines.
Para um exemplo de um projeto de ponte com roteamento de borda (ERB), veja Exemplo: Configuração de uma malha de ponte com roteamento de borda EVPN-VXLAN com um gateway Anycast
Para obter informações de fundo sobre a tecnologia EVPN-VXLAN e arquiteturas suportadas, veja EVPN Primer.
Requisitos
O exemplo original usava os seguintes componentes de hardware e software:
-
Dois roteadores da Série MX da Juniper Networks atuam como gateways IP para o overlay da EVPN
-
Quatro switches QFX5100 da Juniper Networks. Dois desses switches atuam como dispositivos PE na topologia EVPN, e os outros dois switches agem como transporte ip puro para a underlay.
-
Junos OS Release 16.1 ou posterior.
- Atualizado e validado novamente usando o Junos OS Release 21.3R1.9
-
Começando pelo Junos OS Release 17.3R1, a EVPN-VXLAN também tem suporte para switches EX9200. Anteriormente, apenas o encapsulamento MPLS era suportado. Neste exemplo, o switch EX9200 funcionaria como um gateway IP para overlay EVPN. Existem algumas diferenças de configuração entre os roteadores da Série MX e os switches EX9200. A seção de configuração posteriormente neste tópico tem mais informações sobre a configuração específica de um EX9200.
- Veja o resumo do hardware de uma lista de plataformas suportadas.
Visão geral
As VPNs de ethernet (EVPNs) permitem que você conecte grupos de sites de clientes dispersos usando pontes virtuais de Camada 2 e LANs virtuais extensíveis (VXLANs) permitem que você estique a conexão de Camada 2 em uma rede de Camada 3 intervindo, ao mesmo tempo em que fornece segmentação de rede como uma VLAN, mas sem a limitação de escala das VLANs tradicionais. A EVPN com encapsulamento VXLAN lida com a conectividade de Camada 2 na escala exigida pelos provedores de serviços de nuvem e substitui protocolos de limitação como STP, liberando sua rede de Camada 3 para usar protocolos de roteamento mais robustos.
Esta configuração de exemplo mostra como configurar a EVPN com o encapsulamento de VXLAN. Neste exemplo, os roteadores da Série MX são chamados de Core-1 e Core-2. Os switches QFX5100 são chamados leaf-1, Leaf-2, Spine-1 e Spine-2. Os roteadores de núcleo atuam como gateways IP para overlay EVPN, os switches leaf atuam como dispositivos PE na topologia EVPN, e os switches spine agem como transporte ip puro para a underlay (também conhecido como "lean spine").
Topologia
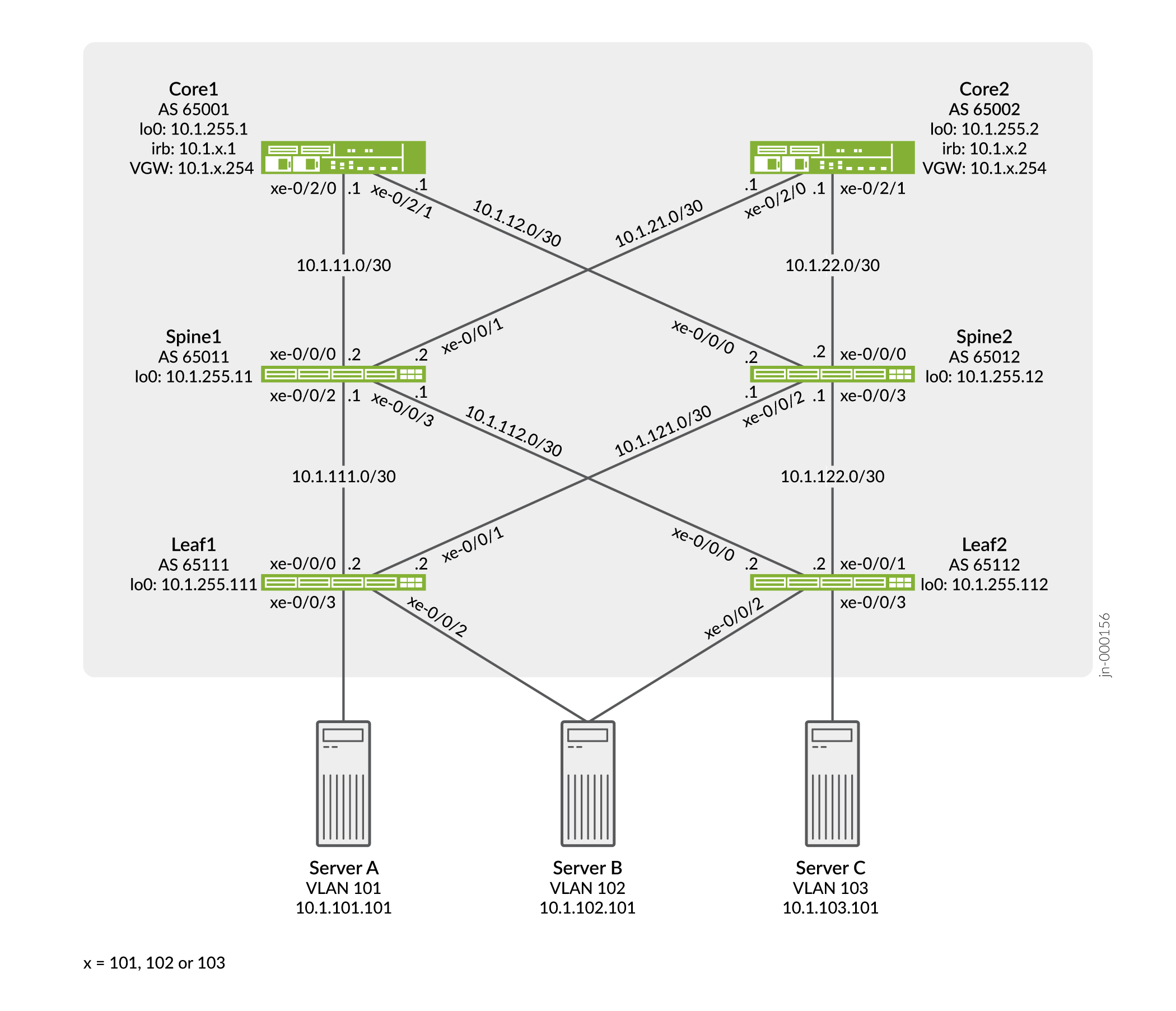
Em nossa topologia de amostra, demonstramos o acesso ao servidor usando interfaces não registradas e com tronco (taged). Uma interface de tronco usa tags VLAN explícitas. Tanto o servidor A quanto o C estão configurados para o tronco, enquanto o servidor B usa uma interface de acesso não registrada para ambas as folhas.
Configuração
Configuração rápida da CLI
Para configurar este exemplo rapidamente, copie os seguintes comandos, cole-os em um arquivo de texto, remova qualquer quebra de linha, altere os detalhes necessários para combinar com a configuração da sua rede e, em seguida, copie e cole os comandos no CLI no nível de [edit] hierarquia.
Leaf-1
set system host-name leaf-1 set chassis aggregated-devices ethernet device-count 2 set interfaces xe-0/0/0 unit 0 family inet address 10.1.111.2/30 set interfaces xe-0/0/1 unit 0 family inet address 10.1.121.2/30 set interfaces xe-0/0/2 ether-options 802.3ad ae0 set interfaces xe-0/0/3 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members v101 set interfaces ae0 esi 00:01:01:01:01:01:01:01:01:01 set interfaces ae0 esi all-active set interfaces ae0 aggregated-ether-options lacp active set interfaces ae0 aggregated-ether-options lacp system-id 00:00:00:01:01:01 set interfaces ae0 unit 0 family ethernet-switching interface-mode access set interfaces ae0 unit 0 family ethernet-switching vlan members v102 set interfaces lo0 unit 0 family inet address 10.1.255.111/32 set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set policy-options policy-statement vrf-imp term t1 from community com101 set policy-options policy-statement vrf-imp term t1 then accept set policy-options policy-statement vrf-imp term t2 from community com102 set policy-options policy-statement vrf-imp term t2 then accept set policy-options policy-statement vrf-imp term t3 from community com103 set policy-options policy-statement vrf-imp term t3 then accept set policy-options policy-statement vrf-imp term t5 then reject set policy-options community com101 members target:65000:101 set policy-options community com102 members target:65000:102 set policy-options community com103 members target:65000:103 set routing-options router-id 10.1.255.111 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65111 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.111.1 peer-as 65011 set protocols bgp group underlay neighbor 10.1.121.1 peer-as 65012 set protocols bgp group EVPN_VXLAN_CORE type internal set protocols bgp group EVPN_VXLAN_CORE local-address 10.1.255.111 set protocols bgp group EVPN_VXLAN_CORE family evpn signaling set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.1 set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.2 set protocols evpn encapsulation vxlan set protocols evpn multicast-mode ingress-replication set protocols evpn vni-options vni 101 vrf-target target:65000:101 set protocols evpn vni-options vni 102 vrf-target target:65000:102 set protocols evpn extended-vni-list 101 set protocols evpn extended-vni-list 102 set switch-options vtep-source-interface lo0.0 set switch-options route-distinguisher 10.1.255.111:1 set switch-options vrf-import vrf-imp set switch-options vrf-target target:65000:1 set vlans v101 vlan-id 101 set vlans v101 vxlan vni 101 set vlans v102 vlan-id 102 set vlans v102 vxlan vni 102
Leaf-2
set system host-name leaf-2 set chassis aggregated-devices ethernet device-count 2 set interfaces xe-0/0/0 unit 0 family inet address 10.1.112.2/30 set interfaces xe-0/0/1 unit 0 family inet address 10.1.122.2/30 set interfaces xe-0/0/2 ether-options 802.3ad ae0 set interfaces xe-0/0/3 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members v103 set interfaces ae0 esi 00:01:01:01:01:01:01:01:01:01 set interfaces ae0 esi all-active set interfaces ae0 aggregated-ether-options lacp active set interfaces ae0 aggregated-ether-options lacp system-id 00:00:00:01:01:01 set interfaces ae0 unit 0 family ethernet-switching interface-mode access set interfaces ae0 unit 0 family ethernet-switching vlan members v102 set interfaces lo0 unit 0 family inet address 10.1.255.112/32 set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set policy-options policy-statement vrf-imp term t1 from community com101 set policy-options policy-statement vrf-imp term t1 then accept set policy-options policy-statement vrf-imp term t2 from community com102 set policy-options policy-statement vrf-imp term t2 then accept set policy-options policy-statement vrf-imp term t3 from community com103 set policy-options policy-statement vrf-imp term t3 then accept set policy-options policy-statement vrf-imp term t5 then reject set policy-options community com101 members target:65000:101 set policy-options community com102 members target:65000:102 set policy-options community com103 members target:65000:103 set routing-options router-id 10.1.255.112 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65112 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.112.1 peer-as 65011 set protocols bgp group underlay neighbor 10.1.122.1 peer-as 65012 set protocols bgp group EVPN_VXLAN_CORE type internal set protocols bgp group EVPN_VXLAN_CORE local-address 10.1.255.112 set protocols bgp group EVPN_VXLAN_CORE family evpn signaling set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.1 set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.2 set protocols evpn encapsulation vxlan set protocols evpn multicast-mode ingress-replication set protocols evpn vni-options vni 102 vrf-target target:65000:102 set protocols evpn vni-options vni 103 vrf-target target:65000:103 set protocols evpn extended-vni-list 102 set protocols evpn extended-vni-list 103 set switch-options vtep-source-interface lo0.0 set switch-options route-distinguisher 10.1.255.112:1 set switch-options vrf-import vrf-imp set switch-options vrf-target target:65000:1 set vlans v102 vlan-id 102 set vlans v102 vxlan vni 102 set vlans v103 vlan-id 103 set vlans v103 vxlan vni 103
Spine-1
set system host-name spine-1 set interfaces xe-0/0/0 unit 0 family inet address 10.1.11.2/30 set interfaces xe-0/0/1 unit 0 family inet address 10.1.21.2/30 set interfaces xe-0/0/2 unit 0 family inet address 10.1.111.1/30 set interfaces xe-0/0/3 unit 0 family inet address 10.1.112.1/30 set interfaces lo0 unit 0 family inet address 10.1.255.11/32 set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set routing-options router-id 10.1.255.11 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65011 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.11.1 peer-as 65001 set protocols bgp group underlay neighbor 10.1.21.1 peer-as 65002 set protocols bgp group underlay neighbor 10.1.111.2 peer-as 65111 set protocols bgp group underlay neighbor 10.1.112.2 peer-as 65112
Spine-2
set system host-name spine-2 set interfaces xe-0/0/0 unit 0 family inet address 10.1.12.2/30 set interfaces xe-0/0/1 unit 0 family inet address 10.1.22.2/30 set interfaces xe-0/0/2 unit 0 family inet address 10.1.121.1/30 set interfaces xe-0/0/3 unit 0 family inet address 10.1.122.1/30 set interfaces lo0 unit 0 family inet address 10.1.255.12/32 set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set routing-options router-id 10.1.255.12 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65012 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.12.1 peer-as 65001 set protocols bgp group underlay neighbor 10.1.22.1 peer-as 65002 set protocols bgp group underlay neighbor 10.1.121.2 peer-as 65111 set protocols bgp group underlay neighbor 10.1.122.2 peer-as 65112
Núcleo 1
set system host-name core-1 set interfaces xe-0/2/0 unit 0 family inet address 10.1.11.1/30 set interfaces xe-0/2/1 unit 0 family inet address 10.1.12.1/30 set interfaces irb unit 101 virtual-gateway-accept-data set interfaces irb unit 101 family inet address 10.1.101.1/24 virtual-gateway-address 10.1.101.254 set interfaces irb unit 102 virtual-gateway-accept-data set interfaces irb unit 102 family inet address 10.1.102.1/24 virtual-gateway-address 10.1.102.254 set interfaces irb unit 103 virtual-gateway-accept-data set interfaces irb unit 103 family inet address 10.1.103.1/24 virtual-gateway-address 10.1.103.254 set interfaces lo0 unit 0 family inet address 10.1.255.1/32 set policy-options policy-statement VS_VLAN101_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN101_IMP term ESI then accept set policy-options policy-statement VS_VLAN101_IMP term VS_VLAN101 from community comm-VS_VLAN101 set policy-options policy-statement VS_VLAN101_IMP term VS_VLAN101 then accept set policy-options policy-statement VS_VLAN102_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN102_IMP term ESI then accept set policy-options policy-statement VS_VLAN102_IMP term VS_VLAN102 from community comm-VS_VLAN102 set policy-options policy-statement VS_VLAN102_IMP term VS_VLAN102 then accept set policy-options policy-statement VS_VLAN103_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN103_IMP term ESI then accept set policy-options policy-statement VS_VLAN103_IMP term VS_VLAN103 from community comm-VS_VLAN103 set policy-options policy-statement VS_VLAN103_IMP term VS_VLAN103 then accept set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set policy-options community comm-VS_VLAN101 members target:65000:101 set policy-options community comm-VS_VLAN102 members target:65000:102 set policy-options community comm-VS_VLAN103 members target:65000:103 set policy-options community comm-leaf members target:65000:1 set routing-instances VRF_Tenant_A instance-type vrf set routing-instances VRF_Tenant_A interface irb.101 set routing-instances VRF_Tenant_A route-distinguisher 10.1.255.1:1010 set routing-instances VRF_Tenant_A vrf-target target:65000:101 set routing-instances VRF_Tenant_B instance-type vrf set routing-instances VRF_Tenant_B interface irb.102 set routing-instances VRF_Tenant_B route-distinguisher 10.1.255.1:1020 set routing-instances VRF_Tenant_B vrf-target target:65000:102 set routing-instances VRF_Tenant_C instance-type vrf set routing-instances VRF_Tenant_C interface irb.103 set routing-instances VRF_Tenant_C route-distinguisher 10.1.255.1:1030 set routing-instances VRF_Tenant_C vrf-target target:65000:103 set routing-instances VS_VLAN101 instance-type virtual-switch set routing-instances VS_VLAN101 protocols evpn encapsulation vxlan set routing-instances VS_VLAN101 protocols evpn extended-vni-list 101 set routing-instances VS_VLAN101 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN101 vtep-source-interface lo0.0 set routing-instances VS_VLAN101 bridge-domains bd101 vlan-id 101 set routing-instances VS_VLAN101 bridge-domains bd101 routing-interface irb.101 set routing-instances VS_VLAN101 bridge-domains bd101 vxlan vni 101 set routing-instances VS_VLAN101 route-distinguisher 10.1.255.1:101 set routing-instances VS_VLAN101 vrf-import VS_VLAN101_IMP set routing-instances VS_VLAN101 vrf-target target:65000:101 set routing-instances VS_VLAN102 instance-type virtual-switch set routing-instances VS_VLAN102 protocols evpn encapsulation vxlan set routing-instances VS_VLAN102 protocols evpn extended-vni-list 102 set routing-instances VS_VLAN102 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN102 vtep-source-interface lo0.0 set routing-instances VS_VLAN102 bridge-domains bd102 vlan-id 102 set routing-instances VS_VLAN102 bridge-domains bd102 routing-interface irb.102 set routing-instances VS_VLAN102 bridge-domains bd102 vxlan vni 102 set routing-instances VS_VLAN102 route-distinguisher 10.1.255.1:102 set routing-instances VS_VLAN102 vrf-import VS_VLAN102_IMP set routing-instances VS_VLAN102 vrf-target target:65000:102 set routing-instances VS_VLAN103 instance-type virtual-switch set routing-instances VS_VLAN103 protocols evpn encapsulation vxlan set routing-instances VS_VLAN103 protocols evpn extended-vni-list 103 set routing-instances VS_VLAN103 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN103 vtep-source-interface lo0.0 set routing-instances VS_VLAN103 bridge-domains bd103 vlan-id 103 set routing-instances VS_VLAN103 bridge-domains bd103 routing-interface irb.103 set routing-instances VS_VLAN103 bridge-domains bd103 vxlan vni 103 set routing-instances VS_VLAN103 route-distinguisher 10.1.255.1:103 set routing-instances VS_VLAN103 vrf-import VS_VLAN103_IMP set routing-instances VS_VLAN103 vrf-target target:65000:103 set routing-options router-id 10.1.255.1 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65001 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.11.2 peer-as 65011 set protocols bgp group underlay neighbor 10.1.12.2 peer-as 65012 set protocols bgp group EVPN_VXLAN type internal set protocols bgp group EVPN_VXLAN local-address 10.1.255.1 set protocols bgp group EVPN_VXLAN family evpn signaling set protocols bgp group EVPN_VXLAN cluster 10.1.1.1 set protocols bgp group EVPN_VXLAN multipath set protocols bgp group EVPN_VXLAN neighbor 10.1.255.111 set protocols bgp group EVPN_VXLAN neighbor 10.1.255.112 set protocols bgp group EVPN_VXLAN neighbor 10.1.255.2
Núcleo 2
set system host-name core-2 set interfaces xe-0/2/0 unit 0 family inet address 10.1.21.1/30 set interfaces xe-0/2/1 unit 0 family inet address 10.1.22.1/30 set interfaces irb unit 101 virtual-gateway-accept-data set interfaces irb unit 101 family inet address 10.1.101.2/24 virtual-gateway-address 10.1.101.254 set interfaces irb unit 102 virtual-gateway-accept-data set interfaces irb unit 102 family inet address 10.1.102.2/24 virtual-gateway-address 10.1.102.254 set interfaces irb unit 103 virtual-gateway-accept-data set interfaces irb unit 103 family inet address 10.1.103.2/24 virtual-gateway-address 10.1.103.254 set interfaces lo0 unit 0 family inet address 10.1.255.2/32 set policy-options policy-statement VS_VLAN101_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN101_IMP term ESI then accept set policy-options policy-statement VS_VLAN101_IMP term VS_VLAN101 from community comm-VS_VLAN101 set policy-options policy-statement VS_VLAN101_IMP term VS_VLAN101 then accept set policy-options policy-statement VS_VLAN102_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN102_IMP term ESI then accept set policy-options policy-statement VS_VLAN102_IMP term VS_VLAN102 from community comm-VS_VLAN102 set policy-options policy-statement VS_VLAN102_IMP term VS_VLAN102 then accept set policy-options policy-statement VS_VLAN103_IMP term ESI from community comm-leaf set policy-options policy-statement VS_VLAN103_IMP term ESI then accept set policy-options policy-statement VS_VLAN103_IMP term VS_VLAN103 from community comm-VS_VLAN103 set policy-options policy-statement VS_VLAN103_IMP term VS_VLAN103 then accept set policy-options policy-statement lo0 from family inet set policy-options policy-statement lo0 from protocol direct set policy-options policy-statement lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement lo0 then accept set policy-options policy-statement load-balance term 1 then load-balance per-packet set policy-options community comm-VS_VLAN101 members target:65000:101 set policy-options community comm-VS_VLAN102 members target:65000:102 set policy-options community comm-VS_VLAN103 members target:65000:103 set policy-options community comm-leaf members target:65000:1 set routing-instances VRF_Tenant_A instance-type vrf set routing-instances VRF_Tenant_A interface irb.101 set routing-instances VRF_Tenant_A route-distinguisher 10.1.255.2:1010 set routing-instances VRF_Tenant_A vrf-target target:65000:101 set routing-instances VRF_Tenant_B instance-type vrf set routing-instances VRF_Tenant_B interface irb.102 set routing-instances VRF_Tenant_B route-distinguisher 10.1.255.2:1020 set routing-instances VRF_Tenant_B vrf-target target:65000:102 set routing-instances VRF_Tenant_C instance-type vrf set routing-instances VRF_Tenant_C interface irb.103 set routing-instances VRF_Tenant_C route-distinguisher 10.1.255.2:1030 set routing-instances VRF_Tenant_C vrf-target target:65000:103 set routing-instances VS_VLAN101 instance-type virtual-switch set routing-instances VS_VLAN101 protocols evpn encapsulation vxlan set routing-instances VS_VLAN101 protocols evpn extended-vni-list 101 set routing-instances VS_VLAN101 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN101 vtep-source-interface lo0.0 set routing-instances VS_VLAN101 bridge-domains bd101 vlan-id 101 set routing-instances VS_VLAN101 bridge-domains bd101 routing-interface irb.101 set routing-instances VS_VLAN101 bridge-domains bd101 vxlan vni 101 set routing-instances VS_VLAN101 route-distinguisher 10.1.255.2:101 set routing-instances VS_VLAN101 vrf-import VS_VLAN101_IMP set routing-instances VS_VLAN101 vrf-target target:65000:101 set routing-instances VS_VLAN102 instance-type virtual-switch set routing-instances VS_VLAN102 protocols evpn encapsulation vxlan set routing-instances VS_VLAN102 protocols evpn extended-vni-list 102 set routing-instances VS_VLAN102 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN102 vtep-source-interface lo0.0 set routing-instances VS_VLAN102 bridge-domains bd102 vlan-id 102 set routing-instances VS_VLAN102 bridge-domains bd102 routing-interface irb.102 set routing-instances VS_VLAN102 bridge-domains bd102 vxlan vni 102 set routing-instances VS_VLAN102 route-distinguisher 10.1.255.2:102 set routing-instances VS_VLAN102 vrf-import VS_VLAN102_IMP set routing-instances VS_VLAN102 vrf-target target:65000:102 set routing-instances VS_VLAN103 instance-type virtual-switch set routing-instances VS_VLAN103 protocols evpn encapsulation vxlan set routing-instances VS_VLAN103 protocols evpn extended-vni-list 103 set routing-instances VS_VLAN103 protocols evpn multicast-mode ingress-replication set routing-instances VS_VLAN103 vtep-source-interface lo0.0 set routing-instances VS_VLAN103 bridge-domains bd103 vlan-id 103 set routing-instances VS_VLAN103 bridge-domains bd103 routing-interface irb.103 set routing-instances VS_VLAN103 bridge-domains bd103 vxlan vni 103 set routing-instances VS_VLAN103 route-distinguisher 10.1.255.2:103 set routing-instances VS_VLAN103 vrf-import VS_VLAN103_IMP set routing-instances VS_VLAN103 vrf-target target:65000:103 set routing-options router-id 10.1.255.2 set routing-options autonomous-system 65000 set routing-options forwarding-table export load-balance set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group underlay type external set protocols bgp group underlay export lo0 set protocols bgp group underlay local-as 65002 set protocols bgp group underlay multipath multiple-as set protocols bgp group underlay neighbor 10.1.21.2 peer-as 65011 set protocols bgp group underlay neighbor 10.1.22.2 peer-as 65012 set protocols bgp group EVPN_VXLAN type internal set protocols bgp group EVPN_VXLAN local-address 10.1.255.2 set protocols bgp group EVPN_VXLAN family evpn signaling set protocols bgp group EVPN_VXLAN cluster 10.2.2.2 set protocols bgp group EVPN_VXLAN multipath set protocols bgp group EVPN_VXLAN neighbor 10.1.255.111 set protocols bgp group EVPN_VXLAN neighbor 10.1.255.112 set protocols bgp group EVPN_VXLAN neighbor 10.1.255.1
Configuração do EX9200
Nos switches EX9200, a vlans declaração é usada em vez de bridge-domains, e a l3-interface declaração é usada em vez de routing-interface.
O exemplo a seguir mostra como configurar essas declarações. Todas as outras configurações mostradas para roteadores da Série MX neste exemplo também se aplicam aos switches EX9200.
set routing-instances VS_VLAN300 vlans vlan1300 vlan-id 300 set routing-instances VS_VLAN300 vlans vlan1300 l3-inteface irb.1300
Neste exemplo, onde quer bridge-domains que ou routing-interface as declarações sejam usadas, para configurar switches EX9200, usar vlans e l3-interface , em vez disso.
Configuração do Leaf-1
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter informações sobre como navegar na CLI, consulte Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
As etapas para configurar o Leaf-2 são semelhantes ao Leaf-1 e, portanto, só mostraremos os procedimentos passo a passo para o Leaf-1.
Para configurar o Leaf-1:
-
Definir o nome de host do sistema.
[edit] user@leaf-1# set system host-name leaf-1
-
Configure opções de roteamento. A load-balance política de exportação está configurada na próxima etapa.
[edit] user@leaf-1# set routing-options router-id 10.1.255.111 user@leaf-1# set routing-options autonomous-system 65000 user@leaf-1# set routing-options forwarding-table export load-balance user@leaf-1# set routing-options forwarding-table ecmp-fast-reroute
-
Configure a política de balanceamento de carga.
[edit policy-options policy-statement load-balance] user@leaf-1# set term 1 then load-balance per-packet
-
Configure o EBGP underlay para os dispositivos spine. A lo0 política de exportação está configurada na próxima etapa.
[edit] user@leaf-1# set protocols bgp group underlay type external user@leaf-1# set protocols bgp group underlay export lo0 user@leaf-1# set protocols bgp group underlay local-as 65111 user@leaf-1# set protocols bgp group underlay multipath multiple-as user@leaf-1# set protocols bgp group underlay neighbor 10.1.111.1 peer-as 65011 user@leaf-1# set protocols bgp group underlay neighbor 10.1.121.1 peer-as 65012
-
Configure uma política para anunciar o endereço de loopback no underlay. Neste exemplo, você escreve uma política portátil que é agnóstica de endereço de loopback, combinando apenas rotas diretas com um comprimento de prefixo de /32. O resultado é uma política que combina com qualquer endereço de loopback e é reutilizável em todos os dispositivos da topologia.
[edit policy-options policy-statement lo0] user@leaf-1# set from family inet user@leaf-1# set from protocol direct user@leaf-1# set from route-filter 0.0.0.0/0 prefix-length-range /32-/32 user@leaf-1# set then accept
-
Configure opções de switch A interface de endpoint de túnel virtual é lo0.0, que deve ser acessível por meio do protocolo de roteamento underlay. O diferencial de rota deve ser único em todos os switches da rede para garantir que todos os anúncios de rota dentro do overlay MP-BGP sejam únicos globalmente. A meta da tabela VRF no switch da Série QFX é, no mínimo, a comunidade que o switch envia anexa a todas as rotas de ESI (Tipo-1). A
vrf-import vrf-impdeclaração define a lista da comunidade-alvo, que é importada para a instância adefault-switch.evpn.0bgp.evpn.0partir da tabela.[edit] user@leaf-1# set switch-options vtep-source-interface lo0.0 user@leaf-1# set switch-options route-distinguisher 10.1.255.111:1 user@leaf-1# set switch-options vrf-import vrf-imp user@leaf-1# set switch-options vrf-target target:65000:1
-
Configure a política de importação da tabela VRF.
[edit] user@leaf-1# set policy-options policy-statement vrf-imp term t1 from community com101 user@leaf-1# set policy-options policy-statement vrf-imp term t1 then accept user@leaf-1# set policy-options policy-statement vrf-imp term t2 from community com102 user@leaf-1# set policy-options policy-statement vrf-imp term t2 then accept user@leaf-1# set policy-options policy-statement vrf-imp term t3 from community com103 user@leaf-1# set policy-options policy-statement vrf-imp term t3 then accept user@leaf-1# set policy-options policy-statement vrf-imp term t5 then reject
-
Configure as comunidades relacionadas.
[edit] user@leaf-1# set policy-options community com101 members target:65000:101 user@leaf-1# set policy-options community com102 members target:65000:102 user@leaf-1# set policy-options community com103 members target:65000:103
-
Configure a lista de identificadores de rede virtual (VNI) estendidos para estabelecer as VNIs que você deseja fazer parte do domínio EVPN. Você também configura a replicação de entrada; na replicação de entrada EVPN-VXLAN é usada para lidar com multicast sem exigir uma subcamada multicast capaz. Diferentes alvos de rota são especificados para cada instância de identificador de rede VXLAN em
vni-routing-options.[edit] user@leaf-1# set protocols evpn encapsulation vxlan user@leaf-1# set protocols evpn multicast-mode ingress-replication user@leaf-1# set protocols evpn vni-options vni 101 vrf-target target:65000:101 user@leaf-1# set protocols evpn vni-options vni 102 vrf-target target:65000:102 user@leaf-1# set protocols evpn extended-vni-list 101 user@leaf-1# set protocols evpn extended-vni-list 102
-
Mapeie IDs VLAN localmente significativos para identificadores de rede VXLAN globalmente significativos.
[edit] user@leaf-1# set vlans v101 vlan-id 101 user@leaf-1# set vlans v101 vxlan vni 101 user@leaf-1# set vlans v102 vlan-id 102 user@leaf-1# set vlans v102 vxlan vni 102
-
Configure as sessões de overlay de IBGP capazes de EVPN.
[edit] user@leaf-1# set protocols bgp group EVPN_VXLAN_CORE type internal user@leaf-1# set protocols bgp group EVPN_VXLAN_CORE local-address 10.1.255.111 user@leaf-1# set protocols bgp group EVPN_VXLAN_CORE family evpn signaling user@leaf-1# set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.1 user@leaf-1# set protocols bgp group EVPN_VXLAN_CORE neighbor 10.1.255.2
Nota:Algumas malhas de IP usam um overlay EVPN-VXLAN baseado em EBGP. Para um exemplo de uma malha de IP que usa o EBGP tanto para underlay quanto para overlay, veja Exemplo: configurando uma malha de ponte com roteamento de borda EVPN-VXLAN com um gateway Anycast. Observe que a escolha do EBGP vs. IBGP para overlay não afeta a arquitetura da malha. Os designs de ponte com roteamento de borda (ERB) e CRB oferecem suporte a qualquer tipo de overlay.
-
Configure as interfaces de malha.
[edit] user@leaf-1# set interfaces xe-0/0/0 unit 0 family inet address 10.1.111.2/30 user@leaf-1# set interfaces xe-0/0/1 unit 0 family inet address 10.1.121.2/30
-
Configure as interfaces de acesso. Observe novamente que demonstramos uma mistura de interfaces de acesso e tronco para o anexo do servidor.
[edit] user@leaf-1# set interfaces xe-0/0/2 ether-options 802.3ad ae0 user@leaf-1# set interfaces xe-0/0/3 unit 0 family ethernet-switching interface-mode trunk user@leaf-1# set interfaces xe-0/0/3 unit 0 family ethernet-switching vlan members v101
-
Configure a interface LAG habilitada para LACP. O valor da ESI é globalmente único em todo o domínio EVPN. A
all-activedeclaração de configuração garante que todos os roteadores PE aos quais este locatário multihomed está conectado podem encaminhar o tráfego do dispositivo CE, de modo que todos os links CE sejam usados ativamente.[edit] user@leaf-1# set interfaces ae0 esi 00:01:01:01:01:01:01:01:01:01 user@leaf-1# set interfaces ae0 esi all-active user@leaf-1# set interfaces ae0 aggregated-ether-options lacp active user@leaf-1# set interfaces ae0 aggregated-ether-options lacp system-id 00:00:00:01:01:01 user@leaf-1# set interfaces ae0 unit 0 family ethernet-switching interface-mode access user@leaf-1# set interfaces ae0 unit 0 family ethernet-switching vlan members v102
-
Configure o endereço da interface de loopback.
[edit] user@leaf-1# set interfaces lo0 unit 0 family inet address 10.1.255.111/32
Configuração do Spine-1
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter informações sobre como navegar na CLI, consulte Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
As etapas para configurar o Spine-2 são semelhantes à Spine-1 e, portanto, só mostraremos os procedimentos passo a passo para o Spine-1.
Para configurar o Spine-1:
-
Definir o nome de host do sistema.
[edit] user@spine-1# set system host-name spine-1
-
Configure as opções de roteamento.
[edit] user@spine-1# set routing-options router-id 10.1.255.11 user@spine-1# set routing-options autonomous-system 65000 user@spine-1# set routing-options forwarding-table export load-balance user@spine-1# set routing-options forwarding-table ecmp-fast-reroute
-
Configure uma política de balanceamento de carga.
[edit policy-options policy-statement load-balance] user@spine-1# set term 1 then load-balance per-packet
-
Configure a underlay do EBGP com peering para dispositivos leaf e núcleo. A lo0 política que anuncia o endereço lo0 é aplicada nesta etapa; a configuração da política em si é mostrada na próxima etapa.
[edit] user@spine-1# set protocols bgp group underlay type external user@spine-1# set protocols bgp group underlay export lo0 user@spine-1# set protocols bgp group underlay local-as 65011 user@spine-1# set protocols bgp group underlay multipath multiple-as user@spine-1# set protocols bgp group underlay neighbor 10.1.11.1 peer-as 65001 user@spine-1# set protocols bgp group underlay neighbor 10.1.21.1 peer-as 65002 user@spine-1# set protocols bgp group underlay neighbor 10.1.111.2 peer-as 65111 user@spine-1# set protocols bgp group underlay neighbor 10.1.112.2 peer-as 65112
-
Configure uma política nomeada lo0 para anunciar /32 rotas. A política é igual ao endereço de loopback, sem especificar nenhum IP específico. Dessa forma, a mesma política é reutilizável em qualquer dispositivo de malha.
[edit policy-options policy-statement lo0] user@spine-1# set from family inet user@spine-1# set from protocol direct user@spine-1# set from route-filter 0.0.0.0/0 prefix-length-range /32-/32 user@spine-1# set then accept
Configuração do Núcleo 1
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter informações sobre como navegar na CLI, consulte Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
As etapas para configurar o Core-2 são semelhantes ao Core-1 e, portanto, só mostraremos os procedimentos passo a passo para o Core-1.
Para configurar o Core-1:
-
Definir o nome de host do sistema.
[edit] user@core-1# set system host-name core-1
-
Configure as opções de roteamento. A load-balance política é aplicada durante esta etapa. Você cria a política na próxima etapa
[edit] user@core-1# set routing-options router-id 10.1.255.1 user@core-1# set routing-options autonomous-system 65000 user@core-1# set routing-options forwarding-table export load-balance user@core-1# set routing-options forwarding-table ecmp-fast-reroute
-
Configure uma política de balanceamento de carga nomeada load-balance.
[edit policy-options policy-statement load-balance] user@core-1# set term 1 then load-balance per-packet
-
Configure o peering underlay do BGP. A lo0 política que anuncia o endereço de loopback é aplicada durante esta etapa. Você configura essa política na próxima etapa.
[edit] user@core-1# set protocols bgp group underlay type external user@core-1# set protocols bgp group underlay export lo0 user@core-1# set protocols bgp group underlay local-as 65001 user@core-1# set protocols bgp group underlay multipath multiple-as user@core-1# set protocols bgp group underlay neighbor 10.1.11.2 peer-as 65011 user@core-1# set protocols bgp group underlay neighbor 10.1.12.2 peer-as 65012
-
Configure uma política nomeada
lo0para anunciar rotas de loopback.[edit policy-options policy-statement lo0] user@core-1# set from family inet user@core-1# set from protocol direct user@core-1# set lo0 from route-filter 0.0.0.0/0 prefix-length-range /32-/32 user@core-1# set lo0 then accept
-
Uma grande parte da configuração do Core-1 ocorre na
[routing-instance]hierarquia. Configure os roteadores virtuais e configure uma política única de importação de tabela VRF para cada switch virtual.[edit] user@core-1# set routing-instances VRF_Tenant_A instance-type vrf user@core-1# set routing-instances VRF_Tenant_A interface irb.101 user@core-1# set routing-instances VRF_Tenant_A route-distinguisher 10.1.255.1:1010 user@core-1# set routing-instances VRF_Tenant_A vrf-target target:65000:101 user@core-1# set routing-instances VRF_Tenant_B instance-type vrf user@core-1# set routing-instances VRF_Tenant_B interface irb.102 user@core-1# set routing-instances VRF_Tenant_B route-distinguisher 10.1.255.1:1020 user@core-1# set routing-instances VRF_Tenant_B vrf-target target:65000:102 user@core-1# set routing-instances VRF_Tenant_C instance-type vrf user@core-1# set routing-instances VRF_Tenant_C interface irb.103 user@core-1# set routing-instances VRF_Tenant_C route-distinguisher 10.1.255.1:1030 user@core-1# set routing-instances VRF_Tenant_C vrf-target target:65000:103 user@core-1# set routing-instances VS_VLAN101 instance-type virtual-switch user@core-1# set routing-instances VS_VLAN101 protocols evpn encapsulation vxlan user@core-1# set routing-instances VS_VLAN101 protocols evpn extended-vni-list 101 user@core-1# set routing-instances VS_VLAN101 protocols evpn multicast-mode ingress-replication user@core-1# set routing-instances VS_VLAN101 vtep-source-interface lo0.0 user@core-1# set routing-instances VS_VLAN101 bridge-domains bd101 vlan-id 101 user@core-1# set routing-instances VS_VLAN101 bridge-domains bd101 routing-interface irb.101 user@core-1# set routing-instances VS_VLAN101 bridge-domains bd101 vxlan vni 101 user@core-1# set routing-instances VS_VLAN101 route-distinguisher 10.1.255.1:101 user@core-1# set routing-instances VS_VLAN101 vrf-import VS_VLAN101_IMP user@core-1# set routing-instances VS_VLAN101 vrf-target target:65000:101 user@core-1# set routing-instances VS_VLAN102 instance-type virtual-switch user@core-1# set routing-instances VS_VLAN102 protocols evpn encapsulation vxlan user@core-1# set routing-instances VS_VLAN102 protocols evpn extended-vni-list 102 user@core-1# set routing-instances VS_VLAN102 protocols evpn multicast-mode ingress-replication user@core-1# set routing-instances VS_VLAN102 vtep-source-interface lo0.0 user@core-1# set routing-instances VS_VLAN102 bridge-domains bd102 vlan-id 102 user@core-1# set routing-instances VS_VLAN102 bridge-domains bd102 routing-interface irb.102 user@core-1# set routing-instances VS_VLAN102 bridge-domains bd102 vxlan vni 102 user@core-1# set routing-instances VS_VLAN102 route-distinguisher 10.1.255.1:102 user@core-1# set routing-instances VS_VLAN102 vrf-import VS_VLAN102_IMP user@core-1# set routing-instances VS_VLAN102 vrf-target target:65000:102 user@core-1# set routing-instances VS_VLAN103 instance-type virtual-switch user@core-1# set routing-instances VS_VLAN103 protocols evpn encapsulation vxlan user@core-1# set routing-instances VS_VLAN103 protocols evpn extended-vni-list 103 user@core-1# set routing-instances VS_VLAN103 protocols evpn multicast-mode ingress-replication user@core-1# set routing-instances VS_VLAN103 vtep-source-interface lo0.0 user@core-1# set routing-instances VS_VLAN103 bridge-domains bd103 vlan-id 103 user@core-1# set routing-instances VS_VLAN103 bridge-domains bd103 routing-interface irb.103 user@core-1# set routing-instances VS_VLAN103 bridge-domains bd103 vxlan vni 103 user@core-1# set routing-instances VS_VLAN103 route-distinguisher 10.1.255.1:103 user@core-1# set routing-instances VS_VLAN103 vrf-import VS_VLAN103_IMP user@core-1# set routing-instances VS_VLAN103 vrf-target target:65000:103
-
Configure a política para cada instância de roteamento.
[edit policy-options] user@core-1# set policy-statement VS_VLAN101_IMP term ESI from community comm-leaf user@core-1# set policy-statement VS_VLAN101_IMP term ESI then accept user@core-1# set policy-statement VS_VLAN101_IMP term VS_VLAN101 from community comm-VS_VLAN101 user@core-1# set policy-statement VS_VLAN101_IMP term VS_VLAN101 then accept user@core-1# set policy-statement VS_VLAN102_IMP term ESI from community comm-leaf user@core-1# set policy-statement VS_VLAN102_IMP term ESI then accept user@core-1# set policy-statement VS_VLAN102_IMP term VS_VLAN102 from community comm-VS_VLAN102 user@core-1# set policy-statement VS_VLAN102_IMP term VS_VLAN102 then accept user@core-1# set policy-statement VS_VLAN103_IMP term ESI from community comm-leaf user@core-1# set policy-statement VS_VLAN103_IMP term ESI then accept user@core-1# set policy-statement VS_VLAN103_IMP term VS_VLAN103 from community comm-VS_VLAN103 user@core-1# set policy-statement VS_VLAN103_IMP term VS_VLAN103 then accept
-
Configure as comunidades. Certifique-se de que a comm-leaf política aceite rotas marcadas com o alvo 65000:1. Isso garante que todos os switches virtuais importem as rotas ESI tipo 1 de todos os leafs.
[edit] user@core-1# set policy-options community comm-VS_VLAN101 members target:65000:101 user@core-1# set policy-options community comm-VS_VLAN102 members target:65000:102 user@core-1# set policy-options community comm-VS_VLAN103 members target:65000:103 user@core-1# set policy-options community comm-leaf members target:65000:1
-
Configure as interfaces IRB. Cada IRB tem um endereço de gateway virtual, que é um endereço MAC compartilhado e endereço IP em Core-1 e Core-2.
[edit interfaces irb] user@core-1# set unit 101 virtual-gateway-accept-data user@core-1# set unit 101 family inet address 10.1.101.1/24 virtual-gateway-address 10.1.101.254 user@core-1# set unit 102 virtual-gateway-accept-data user@core-1# set unit 102 family inet address 10.1.102.1/24 virtual-gateway-address 10.1.102.254 user@core-1# set unit 103 virtual-gateway-accept-data user@core-1# set unit 103 family inet address 10.1.103.1/24 virtual-gateway-address 10.1.103.254
-
Configure as sessões de overlay do IBGP em direção ao Leaf-1 e Leaf-2. Incluímos um peering entre os dispositivos Core para o compartilhamento de rotas entre dispositivos Core.
[edit] user@core-1# set protocols bgp group EVPN_VXLAN type internal user@core-1# set protocols bgp group EVPN_VXLAN local-address 10.1.255.1 user@core-1# set protocols bgp group EVPN_VXLAN family evpn signaling user@core-1# set protocols bgp group EVPN_VXLAN cluster 10.1.1.1 user@core-1# set protocols bgp group EVPN_VXLAN multipath user@core-1# set protocols bgp group EVPN_VXLAN neighbor 10.1.255.111 user@core-1# set protocols bgp group EVPN_VXLAN neighbor 10.1.255.112 user@core-1# set protocols bgp group EVPN_VXLAN neighbor 10.1.255.2
Verificação
- Verificando a acessibilidade mac a um dispositivo CE de casa única (Leaf-1)
- Verificando a acessibilidade mac a um dispositivo CE de casa única (Tipo 2)
- Verificação de rotas importadas
- Verificando a cópia do daemon de aprendizado de endereço da Camada 2
- Verificando a tabela de encaminhamento no nível do Kernel
- Verificando a acessibilidade mac a um dispositivo CE multihomed
- Verificando a EVPN, o daemon de aprendizado de endereços de Camada 2 e as tabelas de encaminhamento de kernel para dispositivos multihomed CE
Verificando a acessibilidade mac a um dispositivo CE de casa única (Leaf-1)
Propósito
Verifique a capacidade de alcance do MAC para Tenant_A. Este usuário é um único lar do Leaf-1. Primeiro, verifique se o endereço MAC é aprendido localmente no Leaf-1. O Leaf-1 gera a rota EVPN tipo 2 somente depois de aprender o endereço MAC.
Ação
Verifique se o endereço MAC é aprendido localmente no Leaf-1.
lab@leaf-1> show ethernet-switching table vlan-id 101
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 4 entries, 4 learned
Routing instance : default-switch
Vlan MAC MAC Logical SVLBNH/ Active
name address flags interface VENH Index source
v101 00:00:5e:00:01:01 DRP esi.1749 05:00:00:fd:e8:00:00:00:65:00
v101 2c:6b:f5:54:95:f0 DR vtep.32770 10.1.255.2
v101 2c:6b:f5:ef:73:f0 DR vtep.32769 10.1.255.1
v101 56:04:15:00:bb:02 D xe-0/0/3.0
Significado
A saída mostra que o MAC 56:04:15:00:bb:02 é aprendido com sucesso com o dispositivo Tenant_A CE, que é o Servidor A na interface xe-0/3.0.
Verificando a acessibilidade mac a um dispositivo CE de casa única (Tipo 2)
Propósito
Verifique a acessibilidade mac a um dispositivo CE de casa única (Tipo 2)
Ação
Verifique a geração da rota Tipo 2 para o Core-1.
lab@leaf-1> show route advertising-protocol bgp 10.1.255.1 evpn-mac-address 56:04:15:00:bb:02 bgp.evpn.0: 50 destinations, 91 routes (50 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 2:10.1.255.111:1::101::56:04:15:00:bb:02/304 MAC/IP * Self 100 I 2:10.1.255.111:1::101::56:04:15:00:bb:02::10.1.101.101/304 MAC/IP * Self 100 I default-switch.evpn.0: 47 destinations, 87 routes (47 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 2:10.1.255.111:1::101::56:04:15:00:bb:02/304 MAC/IP * Self 100 I 2:10.1.255.111:1::101::56:04:15:00:bb:02::10.1.101.101/304 MAC/IP * Self 100 I __default_evpn__.evpn.0: 3 destinations, 4 routes (3 active, 0 holddown, 0 hidden)
Significado
A saída mostra que o MAC e o MAC/IP estão sendo anunciados.
No Core-1, a rota EVPN Type-2 é recebida bgp.evpn.0.
lab@core-1> show route receive-protocol bgp 10.1.255.111 evpn-mac-address 56:04:15:00:bb:02 extensive table bgp.evpn.0
bgp.evpn.0: 52 destinations, 68 routes (52 active, 0 holddown, 0 hidden)
* 2:10.1.255.111:1::101::56:04:15:00:bb:02/304 MAC/IP (2 entries, 1 announced)
Import Accepted
Route Distinguisher: 10.1.255.111:1
Route Label: 101
ESI: 00:00:00:00:00:00:00:00:00:00
Nexthop: 10.1.255.111
Localpref: 100
AS path: I
Communities: target:65000:101 encapsulation:vxlan(0x8)
* 2:10.1.255.111:1::101::56:04:15:00:bb:02::10.1.101.101/304 MAC/IP (2 entries, 1 announced)
Import Accepted
Route Distinguisher: 10.1.255.111:1
Route Label: 101
ESI: 00:00:00:00:00:00:00:00:00:00
Nexthop: 10.1.255.111
Localpref: 100
AS path: I
Communities: target:65000:101 encapsulation:vxlan(0x8)
A saída mostra as rotas Tipo 2 para 56:04:15:00:bb:02. O diferencial de rota é do Leaf-1 e está definido para 10.1.255.111:1.
Verificação de rotas importadas
Propósito
Verifique se a rota EVPN Tipo 2 é importada.
Ação
No Core-1, verifique se as rotas EVPN Type-2 são importadas com sucesso da bgp.evpn.0 tabela para a instância de switch EVPN.
Significado
A saída mostra que, no switch virtual da Tenant_A, a rota EVPN Type-2 é anunciada com o alvo correto, target:1:101. Use a opção extensive para revisar a rota Tipo 2 com mais detalhes.
lab@core-1> show route table VS_VLAN101.evpn.0 evpn-mac-address 56:04:15:00:bb:02
VS_VLAN101.evpn.0: 18 destinations, 25 routes (18 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
2:10.1.255.111:1::101::56:04:15:00:bb:02/304 MAC/IP
*[BGP/170] 1w1d 20:50:01, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
[BGP/170] 3d 02:56:43, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
2:10.1.255.111:1::101::56:04:15:00:bb:02::10.1.101.101/304 MAC/IP
*[BGP/170] 1w1d 20:50:01, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
[BGP/170] 3d 02:56:43, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
A saída mostra que o Core-1 recebe duas cópias. O primeiro é o anúncio da Leaf-1 (Fonte: 10.1.255.111). O segundo é o anúncio do Core-2 (Fonte: 10.1.255.2).
Verificando a cópia do daemon de aprendizado de endereço da Camada 2
Propósito
Verifique a cópia do daemon de aprendizado de endereço da Camada 2.
Ação
Verifique a cópia do daemon de aprendizado de endereço de Camada 2 inserindo o show bridge-mac table comando.
Significado
A saída mostra que 56:04:15:00:bb:02 é acessível através da interface lógica vtep.32771 para Leaf-1.
lab@core-1> show bridge mac-table instance VS_VLAN101
MAC flags (S -static MAC, D -dynamic MAC, L -locally learned, C -Control MAC
O -OVSDB MAC, SE -Statistics enabled, NM -Non configured MAC, R -Remote PE MAC, P -Pinned MAC, FU - Fast Update)
Routing instance : VS_VLAN101
Bridging domain : bd101, VLAN : 101
MAC MAC Logical Active
address flags interface source
00:00:5e:00:01:01 DRP esi.722 05:00:00:fd:e8:00:00:00:65:00
2c:6b:f5:54:95:f0 DR vtep.32779 10.1.255.2
56:04:15:00:bb:02 DR vtep.32771 10.1.255.111
Nos switches EX9200, o show ethernet-switching table-instance instance-name comando corresponde ao show bridge mac-table instance instance-name comando usado aqui para roteadores da Série MX
Verificando a tabela de encaminhamento no nível do Kernel
Propósito
Verifique a tabela de encaminhamento no nível do kernel, o identificador de próximo salto e a tabela e o hardware MAC de Camada 2.
Ação
Consulte a tabela de encaminhamento no nível do kernel, correlacione o identificador de próximo salto do índice com o identificador de rede virtual correto e analise a tabela MAC e o hardware da Camada 2.
Significado
O MAC da Tenant_A, 56:04:15:00:bb:02, é acessível pelo índice 687.
lab@core-1> show route forwarding-table family bridge vpn VS_VLAN101
Routing table: VS_VLAN101.evpn-vxlan
VPLS:
Destination Type RtRef Next hop Type Index NhRef Netif
default perm 0 dscd 664 1
vtep.32771 intf 0 comp 687 7
vtep.32774 intf 0 comp 691 4
vtep.32779 intf 0 comp 716 7
Routing table: VS_VLAN101.evpn-vxlan
Bridging domain: bd101.evpn-vxlan
VPLS:
Enabled protocols: Bridging, ACKed by all peers, EVPN VXLAN,
Destination Type RtRef Next hop Type Index NhRef Netif
00:00:5e:00:01:01/48 user 0 indr 1048579 2
comp 722 2
2c:6b:f5:54:95:f0/48 user 0 comp 716 7
56:04:15:00:bb:02/48 user 0 comp 687 7
0x30003/51 user 0 comp 705 2
Correlacione o índice 687 (NH-Id) com o identificador de rede virtual 101 e o VTEP-ID remoto de 10,1.255,111.
lab@core-1> show l2-learning vxlan-tunnel-end-point remote
Logical System Name Id SVTEP-IP IFL L3-Idx SVTEP-Mode ELP-SVTEP-IP
<default> 0 10.1.255.1 lo0.0 0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.2 VS_VLAN101 377 vtep.32779 716 RNVE
VNID MC-Group-IP
101 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.111 VS_VLAN101 369 vtep.32771 687 RNVE
VNID MC-Group-IP
101 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.112 VS_VLAN101 372 vtep.32774 691 RNVE
10.1.255.2 VS_VLAN102 376 vtep.32778 715 RNVE
VNID MC-Group-IP
102 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.111 VS_VLAN102 370 vtep.32772 688 RNVE
VNID MC-Group-IP
102 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.112 VS_VLAN102 373 vtep.32775 695 RNVE
VNID MC-Group-IP
102 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.2 VS_VLAN103 375 vtep.32777 714 RNVE
VNID MC-Group-IP
103 0.0.0.0
RVTEP-IP L2-RTT IFL-Idx Interface NH-Id RVTEP-Mode ELP-IP Flags
10.1.255.111 VS_VLAN103 371 vtep.32773 689 RNVE
10.1.255.112 VS_VLAN103 374 vtep.32776 692 RNVE
VNID MC-Group-IP
103 0.0.0.0
Nos switches EX9200, o show ethernet-switching comando corresponde ao show l2-learning show de comando aqui para roteadores da Série MX.
Verificando a acessibilidade mac a um dispositivo CE multihomed
Propósito
Verifique a acessibilidade mac do dispositivo Tenant_B CE multihomed no Leaf-1 e Leaf-2.
Ação
Verifique se o Leaf-1 e o Leaf-2 estão anunciando a acessibilidade do Tipo 1 e Do Tipo 2 em direção ao dispositivo CE multihomed.
lab@leaf-1> show ethernet-switching table vlan-id 102
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 4 entries, 4 learned
Routing instance : default-switch
Vlan MAC MAC Logical SVLBNH/ Active
name address flags interface VENH Index source
v102 00:00:5e:00:01:01 DR esi.1748 05:00:00:fd:e8:00:00:00:66:00
v102 2c:6b:f5:43:12:c0 DL ae0.0
v102 2c:6b:f5:54:95:f0 D vtep.32770 10.1.255.2
v102 2c:6b:f5:ef:73:f0 D vtep.32769 10.1.255.1
lab@leaf-2> show ethernet-switching table vlan-id 102
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 4 entries, 4 learned
Routing instance : default-switch
Vlan MAC MAC Logical SVLBNH/ Active
name address flags interface VENH Index source
v102 00:00:5e:00:01:01 DR esi.1749 05:00:00:fd:e8:00:00:00:66:00
v102 2c:6b:f5:43:12:c0 DR ae0.0
v102 2c:6b:f5:54:95:f0 D vtep.32769 10.1.255.2
v102 2c:6b:f5:ef:73:f0 D vtep.32770 10.1.255.1
Significado
A saída mostra que 2c:6b:f5:43:12:c0 representa o MAC do Tenant_B anexado ao Leaf-1 e Leaf-2.
Verificando a EVPN, o daemon de aprendizado de endereços de Camada 2 e as tabelas de encaminhamento de kernel para dispositivos multihomed CE
Propósito
Verifique a tabela de EVPN do locatário B e a tabela de daemon de aprendizado de endereços de Camada 2 do Core-1 e a tabela de encaminhamento do kernel.
Ação
No Core-1, exibir a tabela EVPN do Locatário B.
lab@core-1> show route table VS_VLAN102.evpn.0
VS_VLAN102.evpn.0: 20 destinations, 29 routes (20 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
1:10.1.255.2:0::050000fde80000006600::FFFF:FFFF/192 AD/ESI
*[BGP/170] 2d 23:43:32, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
1:10.1.255.111:0::010101010101010101::FFFF:FFFF/192 AD/ESI
*[BGP/170] 00:14:59, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:14:58, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
1:10.1.255.111:1::010101010101010101::0/192 AD/EVI
*[BGP/170] 00:15:00, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:14:59, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
1:10.1.255.112:0::010101010101010101::FFFF:FFFF/192 AD/ESI
*[BGP/170] 00:10:13, localpref 100, from 10.1.255.112
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:10:13, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
1:10.1.255.112:1::010101010101010101::0/192 AD/EVI
*[BGP/170] 00:10:14, localpref 100, from 10.1.255.112
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:10:14, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.1:102::102::00:00:5e:00:01:01/304 MAC/IP
*[EVPN/170] 2d 23:44:03
Indirect
2:10.1.255.1:102::102::2c:6b:f5:ef:73:f0/304 MAC/IP
*[EVPN/170] 2d 23:44:03
Indirect
2:10.1.255.2:102::102::00:00:5e:00:01:01/304 MAC/IP
*[BGP/170] 2d 23:43:32, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.2:102::102::2c:6b:f5:54:95:f0/304 MAC/IP
*[BGP/170] 2d 23:43:32, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.111:1::102::2c:6b:f5:43:12:c0/304 MAC/IP
*[BGP/170] 00:14:49, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:14:49, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
to 10.1.11.2 via xe-0/2/0.0
> to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.112:1::102::2c:6b:f5:43:12:c0/304 MAC/IP
*[BGP/170] 00:09:24, localpref 100, from 10.1.255.112
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:09:24, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.1:102::102::00:00:5e:00:01:01::10.1.102.254/304 MAC/IP
*[EVPN/170] 2d 23:44:03
Indirect
2:10.1.255.1:102::102::2c:6b:f5:ef:73:f0::10.1.102.1/304 MAC/IP
*[EVPN/170] 2d 23:44:03
Indirect
2:10.1.255.2:102::102::00:00:5e:00:01:01::10.1.102.254/304 MAC/IP
*[BGP/170] 2d 23:43:32, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.2:102::102::2c:6b:f5:54:95:f0::10.1.102.2/304 MAC/IP
*[BGP/170] 2d 23:43:32, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
2:10.1.255.112:1::102::2c:6b:f5:43:12:c0::10.1.102.101/304 MAC/IP
*[BGP/170] 00:06:19, localpref 100, from 10.1.255.112
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:06:18, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
3:10.1.255.1:102::102::10.1.255.1/248 IM
*[EVPN/170] 2d 23:45:49
Indirect
3:10.1.255.2:102::102::10.1.255.2/248 IM
*[BGP/170] 2d 23:44:03, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
3:10.1.255.111:1::102::10.1.255.111/248 IM
*[BGP/170] 00:14:58, localpref 100, from 10.1.255.111
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:14:58, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
3:10.1.255.112:1::102::10.1.255.112/248 IM
*[BGP/170] 00:10:17, localpref 100, from 10.1.255.112
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
[BGP/170] 00:10:17, localpref 100, from 10.1.255.2
AS path: I, validation-state: unverified
> to 10.1.11.2 via xe-0/2/0.0
to 10.1.12.2 via xe-0/2/1.0
Exibir a tabela de daemon de aprendizado de endereços de Camada 1 do Core-1.
lab@core-1> show bridge mac-table instance VS_VLAN102
MAC flags (S -static MAC, D -dynamic MAC, L -locally learned, C -Control MAC
O -OVSDB MAC, SE -Statistics enabled, NM -Non configured MAC, R -Remote PE MAC, P -Pinned MAC, FU - Fast Update)
Routing instance : VS_VLAN102
Bridging domain : bd102, VLAN : 102
MAC MAC Logical Active
address flags interface source
00:00:5e:00:01:01 DRP esi.708 05:00:00:fd:e8:00:00:00:66:00
2c:6b:f5:43:12:c0 DR esi.719 00:01:01:01:01:01:01:01:01:01
2c:6b:f5:54:95:f0 DR vtep.32772 10.1.255.2
Nos switches EX9200, o show ethernet-switching table-instance instance-name comando corresponde ao show bridge mac-table instance instance-name show de comando aqui para roteadores da Série MX
Exibir a tabela de encaminhamento do kernel do Core-1.
lab@core-1> show route forwarding-table vpn VS_VLAN102
Routing table: VS_VLAN102.evpn-vxlan
VPLS:
Destination Type RtRef Next hop Type Index NhRef Netif
default perm 0 dscd 544 1
vtep.32772 intf 0 comp 688 7
vtep.32775 intf 0 comp 716 5
vtep.32778 intf 0 comp 722 5
Routing table: VS_VLAN102.evpn-vxlan
Bridging domain: bd102.evpn-vxlan
VPLS:
Enabled protocols: Bridging, ACKed by all peers, EVPN VXLAN,
Destination Type RtRef Next hop Type Index NhRef Netif
00:00:5e:00:01:01/48 user 0 indr 1048574 2
comp 708 2
2c:6b:f5:43:12:c0/48 user 0 indr 1048578 3
comp 719 2
2c:6b:f5:54:95:f0/48 user 0 comp 688 7
0x30004/51 user 0 comp 702 2
Significado
Para o dispositivo Tenant_B CE, quatro rotas diferentes estão listadas para ESI 00:01:01:01:01:01:01:01:01:01:01:
-
1:10.1.255.111:0:010101010101010101:FFFF:FFFF/192 AD/ESI
Essa rota A-D Tipo-1 EVPN por segmento de Ethernet teve origem no Leaf-1. O diferencial de rota é obtido de nível
routing-optionsglobal. O Core-1 recebe essa rota Tipo 1, originária do Leaf-1, tanto do Leaf-1 quanto do Leaf-2. -
1:10.1.255.111:1:010101010101010101:0/192 AD/EVI
Esta é a rota EVPN por EVI A-D Tipo-1. O diferencial de rota é obtido da instância de roteamento, ou no caso de QFX5100, o
switch-options. O Core-1 recebe essa rota Tipo 1, originária do Leaf-1, tanto do Leaf-1 quanto do Leaf-2. -
1:10.1.255.112:0:010101010101010101:FFFF:FFFF/192 AD/ESI
Esta é a rota EVPN por segmento de Ethernet A-D Tipo-1 originada do Leaf-2. O diferencial de rota é obtido de nível
routing-optionsglobal. O Core-1 recebe essa rota Tipo 1, originária do Leaf-2, tanto do Leaf-2 quanto do Leaf-1. -
1:10.1.255.112:1:010101010101010101:0/192 AD/EVI
Esta é a rota EVPN por EVI A-D Tipo-1. O diferencial de rota é obtido da instância de roteamento, ou no caso de QFX5100,
switch-options. O Core-1 recebe essa rota Tipo 1, originária do Leaf-2, tanto do Leaf-2 quanto do Leaf-1.
As rotas Tipo 2 para o MAC físico e um virtual associados ao Tenant_B dispositivo CE multihomed são originadas como esperado.
A partir da saída ainda não podemos determinar quais VTEPs são usados para encaminhamento à ESI 00:01:01:01:01:01:01:01:01:01:01. Para determinar o VTEPS, exibir os ESIs de endpoint do túnel VXLAN.
lab@core-1> show l2-learning vxlan-tunnel-end-point esi
ESI RTT VLNBH INH ESI-IFL LOC-IFL #RVTEPs
00:01:01:01:01:01:01:01:01:01 VS_VLAN101 718 1048577 esi.718 2 Aliasing
RVTEP-IP RVTEP-IFL VENH MASK-ID FLAGS MAC-COUNT
10.1.255.112 vtep.32779 723 1 2 0
10.1.255.111 vtep.32774 714 0 2 0
...
Nos switches EX9200, o show ethernet-switching comando corresponde ao show l2-learning show de comando aqui para roteadores da Série MX.
A saída mostra balanceamento ativo de carga nas interfaces VTEP para Leaf-1 e Leaf-2 para os endereços MAC neste ESI, que valida a configuração totalmente ativa no Leaf-1 e Leaf-2.
