ON THIS PAGE
NAT Protocol Translation
Configuring NAT-PT
To configure the translation type as basic-nat-pt, you must configure the DNS ALG application, the NAT pools and rules,
a service set with a service interface, and trace options. Configuring
NAT-PT is not supported if you are using MS-MPCs or MS-MICs. This
topic includes the following tasks:
- Configuring the DNS ALG Application
- Configuring the NAT Pool and NAT Rule
- Configuring the Service Set for NAT
- Configuring Trace Options
Configuring the DNS ALG Application
To configure the DNS ALG application:
Configuring the NAT Pool and NAT Rule
To configure the NAT pool and NAT rule:
Configuring the Service Set for NAT
To configure the service set for NAT:
Configuring Trace Options
To configure the trace options:
The following example configures the translation type as basic-nat-pt.
[edit]
user@host# show services
service-set ss_dns {
nat-rules rule-basic-nat-pt;
interface-service {
service-interface sp-1/2/0;
}
}
nat {
pool p1 {
address 10.10.10.2/32;
}
pool src_pool0 {
address 20.1.1.1/32;
}
pool dst_pool0 {
address 50.1.1.2/32;
}
rule rule-basic-nat-pt {
match-direction input;
term t1 {
from {
source-address {
2000::2/128;
}
destination-address {
4000::2/128;
}
applications dns_alg;
}
then {
translated {
source-pool src_pool0;
destination-pool dst_pool0;
dns-alg-prefix 2001:db8:10::0/96;
translation-type {
basic-nat-pt;
}
}
}
}
term t2 {
from {
source-address {
2000::2/128;
}
destination-address {
2001:db8:10::0/96;
}
}
then {
translated {
source-prefix 19.19.19.1/32;
translation-type {
basic-nat-pt;
}
}
}
}
}
}
adaptive-services-pics {
traceoptions {
flag all;
}
}Example: Configuring NAT-PT
A Domain Name System application-level gateway (DNS ALG) is used with Network Address Translation-Protocol Translation (NAT-PT) to facilitate name-to-address mapping. You can configure the DNS ALG to map addresses returned in the DNS response to an IPv6 address. Configuring NAT-PT is not supported if you are using MS-MPCs or MS-MICs.
When you configure NAT-PT with DNS ALG support, you must configure two NAT rules or one rule with two terms. In this example, you configure two rules. The first NAT rule ensures that the DNS query and response packets are translated correctly. For this rule to work, you must configure a DNS ALG application and reference it in the rule. The second rule is required to ensure that NAT sessions are destined to the address mapped by the DNS ALG.
Then, you must configure a service set, and then apply the service set to the interfaces.
This example describes how to configure NAT-PT with DNS ALG:
Requirements
This example uses the following hardware and software components:
Junos OS Release 11.2
A multiservices interface (ms-)
Overview and Topology
The following scenario shows the process of NAT-PT with DNS ALG when a laptop in an IPv6-only domain requests access to a server in an IPv4-only domain.
Topology
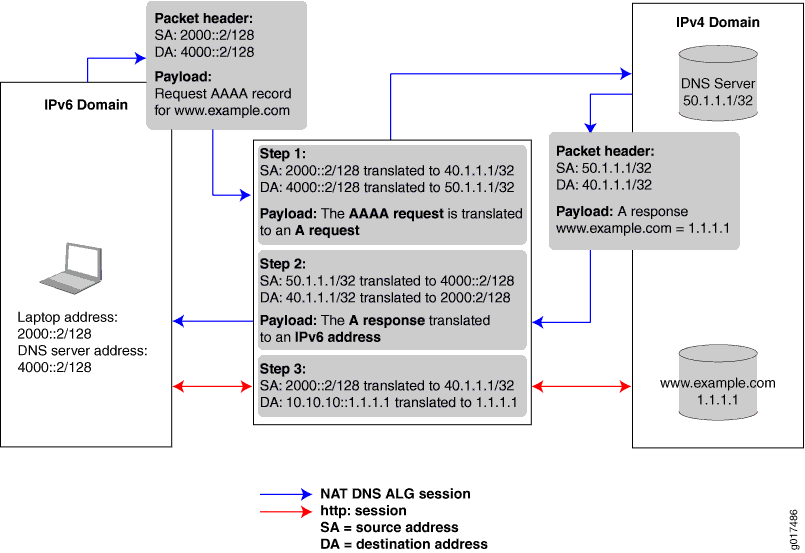
The Juniper Networks router in the center of the illustration performs address translation in two steps. When the laptop requests a session with the www.example.com server that is in an IPv4-only domain, the Juniper Networks router performs the following:
Translates the IPv6 laptop and DNS server addresses into IPv4 addresses.
Translates the AAAA request from the laptop into an A request so that the DNS server can provide the IPv4 address.
When the DNS server responds with the A request, the Juniper Networks router performs the following:
Translates the IPv4 DNS server address back into an IPv6 address.
Translates the A request back into a AAAA request so that the laptop now has the 96-bit IPv6 address of the www.example.com server.
After the laptop receives the IPv6 version of the www.example.com server address, the laptop initiates a second session using the 96-bit IPv6 address to access that server. The Juniper Networks router performs the following:
Translates the laptop IPv4 address directly into its IPv4 address.
Translates the 96-bit IPv6 www.example.com server address into its IPv4 address.
Configuration of NAT-PT with DNS ALGs
To configure NAT-PT with DNS ALG , perform the following tasks:
- Configuring the Application-Level Gateway
- Configuring the NAT Pools
- Configuring the DNS Server Session: First NAT Rule
- Configuring the HTTP Session: Second NAT Rule
- Configuring the Service Set
- Configuring the Stateful Firewall Rule
- Configuring Interfaces
Configuring the Application-Level Gateway
Step-by-Step Procedure
Configure the DNS application as the ALG to which the DNS traffic is destined. The DNS application protocol closes the DNS flow as soon as the DNS response is received. When you configure the DNS application protocol, you must specify the UDP protocol as the network protocol to match in the application definition.
To configure the DNS application:
In configuration mode, go to the
[edit applications]hierarchy level.user@host# edit applications
Define the application name and specify the application protocol to use in match conditions in the first NAT rule.
[edit applications] user@host# set application application-name application-protocol protocol-name
For example:
[edit applications] user@host# set application dns_alg application-protocol dns
Specify the protocol to match, in this case UDP.
[edit applications] user@host# set application application-name protocol type
For example:
[edit applications] user@host# set application dns_alg protocol udp
Define the UDP destination port for additional packet matching, in this case the domain port.
[edit applications] user@host# set application application-name destination-port value
For example:
[edit applications] user@host# set application dns_alg destination-port 53
Results
[edit applications]
user@host# show
application dns_alg {
application-protocol dns;
protocol udp;
destination-port 53;
}Configuring the NAT Pools
Step-by-Step Procedure
In this configuration, you configure two pools that define the addresses (or prefixes) used for NAT. These pools define the IPv4 addresses that are translated into IPv6 addresses. The first pool includes the IPv4 address of the source. The second pool defines the IPv4 address of the DNS server. To configure NAT pools:
In configuration mode, go to the
[edit services nat]hierarchy level.user@host# edit services nat
Specify the name of the first pool and the IPv4 source address (laptop).
[edit services nat] user@host# set pool nat-pool-name address ip-prefix
For example:
[edit services nat] user@host# set pool pool1 address 40.1.1.1/32
Specify the name of the second pool and the IPv4 address of the DNS server.
[edit services nat] user@host# set pool nat-pool-name address ip-prefix
For example:
[edit services nat] user@host# set pool pool2 address 50.1.1.1/32
Results
The following sample output shows the configuration of NAT pools.
[edit services nat]
user@host# show
pool pool1 {
address 40.1.1.1/32;
}
pool pool2 {
address 50.1.1.1/32;
}Configuring the DNS Server Session: First NAT Rule
Step-by-Step Procedure
The first NAT rule is applied to DNS traffic going to the DNS server. This rule ensures that the DNS query and response packets are translated correctly. For this rule to work, you must configure a DNS ALG application and reference it in the rule. The DNS application was configured in Configuring NAT-PT. In addition, you must specify the direction in which traffic is matched, the source address of the laptop, the destination address of the DNS server, and the actions to take when the match conditions are met.
To configure the first NAT rule:
In configuration mode, go to the
[edit services nat]hierarchy level.user@host# edit services nat
Specify the name of the NAT rule.
[edit services nat] user@host# edit rule rule-name
For example:
[edit services nat] user@host# edit rule rule1
Specify the name of the NAT term.
[edit services nat rule rule-name] user@host# edit term term-name
For example:
[edit services nat rule rule1] user@host# edit term term1
Define the match conditions for this rule.
Specify the IPv6 source address of the device (laptop) attempting to access an IPv4 address.
[edit services nat rule rule-name term term-name] user@host# set from source-address source-address
For example:
[edit services nat rule rule1 term term1] user@host# set from source-address 2000::2/128
Specify the IPv6 destination address of the DNS server.
[edit services nat rule rule-name term term-name] user@host# set from destination-address prefix
For example:
[edit services nat rule rule1 term term1] user@host# set from destination-address 4000::2/128
Reference the DNS application to which the DNS traffic destined for port 53 is applied.
[edit services nat rule rule1 term term1] user@host# set from applications application-name
In this example, the application name configured in the Configuring the DNS Application step is dns_alg:
[edit services nat rule rule1 term term1] user@host# set from applications dns_alg
Define the actions to take when the match conditions are met. The source and destination pools you configured in Configuring the NAT Pools are applied here.
Apply the NAT pool configured for source translation.
[edit services nat rule rule-name term term-name] user@host# set then translated source-pool nat-pool-name
For example:
[edit services nat rule rule1 term term1] user@host# set then translated source-pool pool1
Apply the NAT pool configured for destination translation.
[edit services nat rule rule-name term term-name] user@host# set then translated destination-pool nat-pool-name
For example:
[edit services nat rule rule1 term term1] user@host# set then translated source-pool pool2
Define the DNS ALG 96-bit prefix for IPv4-to-IPv6 address mapping.
[edit services nat rule rule-name term term-name] user@host# set then translated dns-alg-prefix dns-alg-prefix
For example:
[edit services nat rule rule1 term term1] user@host# set then translated dns-alg-prefix 10:10:10::0/96
Specify the type of NAT used for source and destination traffic.
[edit services nat rule rule-name term term-name] user@host# set then translated translation-type basic-nat-pt
For example:
[edit services nat rule rule1 term term1] user@host# set then translated translation-type basic-nat-pt
Note:In this example, since NAT is achieved using address-only translation, the basic-nat-pt translation type is used. To achieve NAT using address and port translation (NAPT), use the napt-pt translation type.
Specify the direction in which to match traffic that meets the rule conditions.
[edit services nat rule rule-name] user@host# set match-direction (input | output)
For example:
[edit services nat rule rule1] user@host# set match-direction input
Configure system logging to record information from the services interface to the /var/log directory.
[edit services nat rule rule-name term term-name] user@host# set then syslog
For example:
[edit services nat rule rule1 term term1] user@host# set then syslog
Results
The following sample output shows the configuration of the first NAT rule that goes to the DNS server.
[edit services nat]
user@host# show
rule rule1 {
match-direction input;
term term1 {
from {
source-address {
2000::2/128;
}
destination-address {
4000::2/128;
}
applications dns_alg;
}
then {
translated {
source-pool pool1;
destination-pool pool2;
dns-alg-prefix 10:10:10::0/96;
translation-type {
basic-nat-pt;
}
}
syslog;
}
}
}
Configuring the HTTP Session: Second NAT Rule
Step-by-Step Procedure
The second NAT rule is applied to destination traffic going to the IPv4 server (www.example.com). This rule ensures that NAT sessions are destined to the address mapped by the DNS ALG. For this rule to work, you must configure the DNS ALG address map that correlates the DNS query or response processing done by the first rule with the actual data sessions processed by the second rule. In addition, you must specify the direction in which traffic is matched: the IPv4 address for the IPv6 source address (laptop), the 96-bit prefix to prepend to the IPv4 destination address (www.example.com), and the translation type.
To configure the second NAT rule:
In configuration mode, go to the following hierarchy level.
user@host# edit services nat
Specify the name of the NAT rule and term.
[edit services nat] user@host# edit rule rule-name term term-name
For example:
[edit services nat] user@host# edit rule rule2 term term1
Define the match conditions for this rule:
Specify the IPv6 address of the device attempting to access the IPv4 server.
[edit services nat rule rule-name term term-name] user@host# set from source-address source-address
For example:
[edit services nat rule rule2 term term1] user@host# set from source-address 2000::2/128
Specify the 96-bit IPv6 prefix to prepend to the IPv4 server address.
[edit services nat rule rule-name term term-name] user@host# set from destination-address prefix
For example:
[edit services nat rule rule2 term term1] user@host# set from destination-address 10:10:10::c0a8:108/128
Define the actions to take when the match conditions are met.
Specify the prefix for the translation of the IPv6 source address.
[edit services nat rule rule-name term term-name] user@host# set then translated source-prefix source-prefix
For example:
[edit services nat rule rule2 term term1] user@host# set then translated source-prefix 19.19.19.1/32
Specify the type of NAT used for source and destination traffic.
[edit services nat rule rule-name term term-name] user@host# set then translated translation-type basic-nat-pt
For example:
[edit services nat rule rule2 term term1] user@host# set then translated translation-type basic-nat-pt
Note:In this example, since NAT is achieved using address-only translation, the basic-nat-pt translation type is used. To achieve NAT using address and port translation (NAPT), you must use the napt-pt translation type.
Specify the direction in which to match traffic that meets the conditions in the rule.
[edit services nat rule rule-name] user@host# set match-direction (input | output)
For example:
[edit services nat rule rule2] user@host# set match-direction input
Results
The following sample output shows the configuration of the second NAT rule.
[edit services nat]
user@host# show
rule rule2 {
match-direction input;
term term1 {
from {
source-address {
2000::2/128;
}
destination-address {
10:10:10::c0a8:108/128;
}
}
then {
translated {
source-prefix 19.19.19.1/32;
translation-type {
basic-nat-pt;
}
}
}
}
}
Configuring the Service Set
Step-by-Step Procedure
This service set is an interface service set used as an action modifier across the entire services (ms-) interface. Stateful firewall and NAT rule sets are applied to traffic processed by the services interface.
To configure the service set:
In configuration mode, go to the
[edit services]hierarchy level.user@host# edit services
Define a service set.
[edit services] user@host# edit service-set service-set-name
For example:
[edit services] user@host# edit service-set ss
Specify properties that control how system log messages are generated for the service set.
[edit services service-set ss] user@host# set syslog host local services severity-level
The example below includes all severity levels.
[edit services service-set ss] user@host# set syslog host local services any
Specify the stateful firewall rule included in this service set.
[edit services service-set ss] user@host# set stateful-firewall-rules rule1 severity-level
The example below references the stateful firewall rule defined in Configuring the Stateful Firewall Rule.
[edit services service-set ss] user@host# set stateful-firewall-rules rule1
Define the NAT rules included in this service set.
[edit services service-set ss] user@host# set nat-rules rule-name
The example below references the two rules defined in this configuration example.
[edit services service-set ss user@host# set nat-rules rule1 user@host# set nat-rules rule2
Configure an adaptive services interface on which the service is to be performed.
[edit services service-set ss] user@host# set interface-service service-interface interface-name
For example:
[edit services service-set ss user@host# interface-service service-interface ms-2/0/0
Only the device name is needed, because the router software manages logical unit numbers automatically. The services interface must be an adaptive services interface for which you have configured unit 0 family inet at the
[edit interfaces interface-name]hierarchy level in Configuring Interfaces.
Results
The following sample output shows the configuration of the service set.
[edit services]
user@host# show
service-set ss {
syslog {
host local {
services any;
}
}
stateful-firewall-rules rule1;
nat-rules rule1;
nat-rules rule2;
interface-service {
service-interface ms-2/0/0;
}
}
Configuring the Stateful Firewall Rule
Step-by-Step Procedure
This example uses a stateful firewall to inspect packets for state information derived from past communications and other applications. The NAT-PT router checks the traffic flow matching the direction specified by the rule, in this case both input and output. When a packet is sent to the services (ms-) interface, direction information is carried along with it.
To configure the stateful firewall rule:
In configuration mode, go to the
[edit services stateful firewall]hierarchy level.user@host# edit services stateful firewall
Specify the name of the stateful firewall rule.
[edit services stateful-firewall] user@host# edit rule rule-name
For example:
[edit services stateful-firewall] user@host# edit rule rule1
Specify the direction in which traffic is to be matched.
[edit services stateful-firewall rule rule-name] user@host# set match-direction (input | input-output | output)
For example:
[edit services stateful-firewall rule rule1] user@host# set match-direction input-output
Specify the name of the stateful firewall term.
[edit services stateful-firewall rule rule-name] user@host# edit term term-name
For example:
[edit services stateful-firewall rule rule1] user@host# edit term term1
Define the terms that make up this rule.
[edit services stateful-firewall rule rule-name term term-name] user@host# set then accept
For example:
[edit services stateful-firewall rule rule1 term term1] user@host# set then accept
Results
The following sample output shows the configuration of the services stateful firewall.
[edit services]
user@host# show
stateful-firewall {
rule rule1 {
match-direction input-output;
term term1 {
then {
accept;
}
}
}
}
Configuring Interfaces
Step-by-Step Procedure
After you have defined the service set, you must apply services to one or more interfaces installed on the router. In this example, you configure one interface on which you apply the service set for input and output traffic. When you apply the service set to an interface, it automatically ensures that packets are directed to the services (ms-) interface.
To configure the interfaces:
In configuration mode, go to the
[edit interfaces]hierarchy level.user@host# edit interfaces
Configure the interface on which the service set is applied to automatically ensure that packets are directed to the services (ms-) interface.
For IPv4 traffic, specify the IPv4 address.
[edit interfaces] user@host# set ge-1/0/9 unit 0 family inet address 30.1.1.1/24
Apply the service set defined in Configuring Interfaces.
[edit interfaces] user@host# set ge-1/0/9 unit 0 family inet6 service input service-set ss user@host# set ge-1/0/9 unit 0 family inet6 service output service-set ss
For IPv6 traffic, specify the IPv6 address.
[edit interfaces] user@host# set ge-1/0/9 unit 0 family inet6 address 2000::1/64
Specify the interface properties for the services interface that performs the service.
[edit interfaces] user@host# set ms-2/0/0 services-options syslog host local services any user@host# set ms-2/0/0 unit 0 family inet user@host# set ms-2/0/0 unit 0 family inet6
Results
The following sample output shows the configuration of the interfaces for this example.
[edit interfaces]
user@host# show
ge-1/0/9 {
unit 0 {
family inet {
address 30.1.1.1/24;
}
family inet6 {
service {
input {
service-set ss;
}
output {
service-set ss;
}
}
address 2000::1/64;
}
}
}
ms-2/0/0 {
services-options {
syslog {
host local {
services any;
}
}
}
unit 0 {
family inet;
family inet6;
}
}
