CLI Overview
CLI is a tool that helps you to debug and troubleshoot issues that you might encounter on Juniper Security Director. You can run the commands to complete tasks such as examining details about the system and network, viewing logs, and verifying the current status of different services.
Get Started with the CLI
This topic shows you how to start the CLI and view the command hierarchy.
To access the CLI:
Install and configure Open Virtual Appliance (OVA) in your VM. For more information, see Juniper Security Director Installation and Upgrade Guide.
Please note that only CLI Administrator (cliadmin) can access the CLI.
Enter the username ssh cliadmin@<VM IP address> and the password you created during the OVA configuration.
Once you have entered the credentials, the terminal appears as shown below.
user@user-mbp ~ % ssh cliadmin@10.1.23.0 cliadmin@10.1.23.0's password: Starting Security Director CLI.. ******************************************** * * * Juniper Security Director CLI * * * ******************************************** $
Once you are logged in, you can run the operational commands for debugging.
If you forgot your password, you can reset it using the pass-key.
To reset the password for the cliadmin user:
Login to vSphere Client.
In the vSphere client, right-click the VM and select .
Click Yes to confirm and power off the VM.
Once the VM is powered off, right-click the VM again and select . During the boot process, wait for a pass-key or token to be displayed in the CLI. This might take a few minutes. Copy this passkey or token and keep it securely.
Note: You don't need to power on the VM if you have already saved the passkey or token from a previous boot process.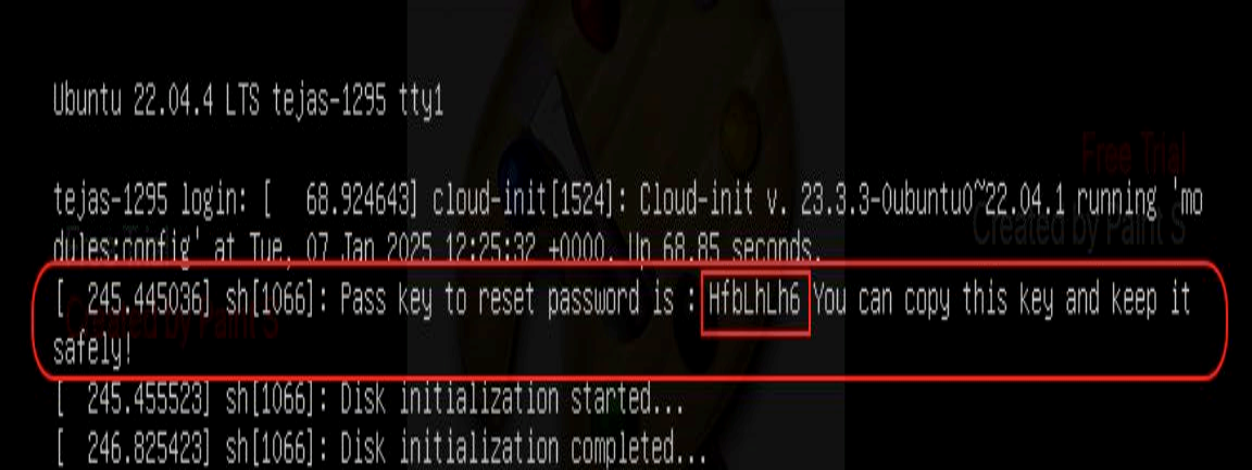
In the vSphere client, right-click the VM and select .
Click Yes to confirm and power off the VM.
Right-click the VM, select .
Select the following properties and select SET VALUE:
PasswordResetKey—Set the value of this property to the passkey or token that you copied during the VM reboot.
CLI_PASSWORD—Set the value of this property to your new desired password. Enter the password that meets the following requirements:
The password should be at least 8 characters long and not more than 32 characters.
The password must include at least three of the following:
Numbers (0-9)
Uppercase letters (A-Z)
Lowercase letters (a-z)
Special characters (~!@#$%^&*()_-+={}[];:"'<,>.?/|\)
Click OK.
Right-click the VM, select .
The password will be reset to the new password only if the value of PasswordResetKey property matches the pass-key or token.
Categories of CLI Commands
CLI commands are categorized into four main types:
-
Global Commands—Global commands are key system commands. For example,
networkstatcommand shows the network-related and diagnostic information, andlistcommand shows the files in a directory. -
Service Commands—Service commands display the status and logs of a service, and can also restart a service. For example,
service configdb logcommand shows the logs of configdb service andservice configdb restartcommand restarts the configdb service. -
Set Commands—Set commands update the VM configuration, such as IP address, Domain Name System (DNS), Network Time Protocol (NTP) and enable or disable CLI settings like the timestamp. For example,
set ipaddress changecommand changes the IP address of the host VM. -
Show Commands—Show commands provide detailed information about a service or file that helps in debugging. For example,
show loadbalancer configcommand shows the configuration of the loadbalancer service.
Key Features of the CLI
The CLI commands and statements follow a hierarchical organization and have a regular syntax. The CLI provides following features to simplify CLI use:
- Consistent command names—Commands that provide the same type of function have the same
name. For example, all
showcommands display software or services information and statistics. -
Lists and short descriptions of available commands—The CLI provides information about available commands at each level of the command hierarchy. If you type a question mark (
?) at any level, you see a list of the available commands along with a short description of each. For example, to view all the available commands for loadbalancer service, typeservice loadbalancer ?.$ service loadbalancer ? config Configure the loadbalancer service log Display the logs of loadbalancer service restart Restart the loadbalancer service status Check the loadbalancer service status <cr>
-
Command completion—Command completion for command names (keywords) and for command options is available at each level of the hierarchy. To complete a command or option that you have partially typed, press the Tab key or the Spacebar. If the partially typed letters begin a string that uniquely identifies a command, the complete command name appears. Otherwise, a beep indicates that you have entered an ambiguous command, and the CLI displays possible completions. Completion also applies to other strings, such as filenames, interface names, usernames, and configuration statements. If you enter an incomplete or a wrong command in the CLI, the following error messages are displayed.
$ tail Syntax error: Incompleted command
$ tail /var/log/onpremcli/cli-audit.log 5 hghfdg Syntax error: Illegal command line
$ tail abc: Syntax error: Illegal parameter 🡪 Here the command is expecting Filepath as input but abc: is not a valid filepath(: is not accepted as part of Filepath here)
CLI Command Hierarchy
CLI commands are organized in a hierarchy. Commands that perform a similar function are
grouped under the same level of the hierarchy. For example, all commands that display
information about the services are under the show <service name>
command.
To execute a command, enter the full command name, starting at the top level of the
hierarchy. For example, to display the status of loadbalancer service, use the command
show loadbalancer status.
$ show loadbalancer status 2024-12-19 15:02:56 UTC VIP Address Service L2-advertisment UI Virtual IP Address 10.157.76.41 ambassador yes Device Connection Virtual IP Address 10.157.76.42 dcs-central yes Log Collector Virtual IP Address 10.157.76.44 scss-central yes
Use Keyboard Sequences to Navigate and Edit the CLI
You can use keyboard sequences in the CLI to navigate and edit the command line. You can also use keyboard sequences to scroll through a list of recently executed commands. The following table lists some of the CLI keyboard sequences.
|
Keyboard Sequence |
Action |
|---|---|
|
Ctrl+a |
Move the cursor to the beginning of the command line. |
|
Ctrl+e |
Move the cursor to the end of the command line. |
|
Ctrl+h or Backspace |
Delete the character before the cursor. |
|
Ctrl+d |
Delete the character at the cursor. |
|
Ctrl+k |
Delete the all characters from the cursor to the end of the command line. |
|
Ctrl+u |
Delete the all characters from the command line. |
|
Ctrl+w |
Delete the word before the cursor. |
|
Ctrl+y |
Insert the most recently deleted text at the cursor. |
|
Up arrow |
Scroll backward through the list of recently executed commands. |
|
Down arrow |
Scroll forward through the list of recently executed commands. |
Key Services
You can run the CLI commands for the following services:
-
Bootservice—Bootservice is the first host service to run in the Juniper Security Director and runs only once during the boot process. The service performs the following tasks:
-
Checks the resources and determines the size of the VM.
-
Configures the disk layout to create partitions and logical volumes.
-
Configures services like clusterdb before it starts.
See service bootservice.
-
-
Clusterdb (etcd)—Cluster database contains data about the entire deployment which is utilized by the cluster manager. The database includes distributed locks to handle image upgrades, topology changes, and system fault generation. In the Juniper Security Director, etcd is used as clusterdb. etcd is an open-source distributed key-value store that contains the critical information needed for the distributed systems to keep running.
-
Cluster-manager—Cluster manager is a service responsible for performing following tasks:
-
Image installation and upgrades
-
Manages topology changes like IP address modifications and node status (offline/online).
-
Checks the cluster database for any resource configuration changes every three minutes. If a resource configuration change is detected, the service triggers the Tdeployer module to take the necessary action after acquiring the cluster manager locks.
-
-
Configdb (database)—Configdb is a database service used by the applications and services.
See service configdb (Database) and show configdb (database).
-
Documentdb (Opensearch)—Documentdb service is used for log analytics and insights. The service is used by the global search to cache policy objects and stores documents in the location /log_analytics/opensearch. In the Juniper Security Director, OpenSearch engine is used as the documentdb. OpenSearch is an open-source search and analytics engine used for log analytics and real-time application monitoring.
See service documentdb (OpenSearch) and show documentdb (opensearch).
-
Healthmonitor—Healthmonitor is a service that assesses the health of the system to detect any issues. The service generates system faults to inform users about these issues. The system faults are displayed in the UI and the CLI under the show health commands. The service runs as a background process, assessing the system health every five minutes.
See show health and service healthmonitor.
-
IPtables—IPtables is a service used to manage network traffic rules, which can be configured to limit communication to the host VM.
See service iptable and show iptable.
-
Keystore (Redis)—Keystore service is used by the application to store temporary information as key values. In the Juniper Security Director, Redis is used as the keystore. Redis is a key-value database that stores data in memory instead of on a disk or solid-state drive (SSD)
-
Kubernetes—Kubernetes is a platform designed to automate the management, deployment, and scaling of applications. Kubernetes is installed as part of the software bundle. All the application and infrastructure services will only function properly after Kubernetes has been installed.
See service kubernetes and show kubernetes.
-
Loadbalancer (metallb)—Loadbalancer service assigns the IP addresses to the services and responds to Address Resolution Protocol (ARP) requests for these IPs. In the Juniper Security Director, MetalLB is used as the loadbalancer to push the virtual IPs configured for the UI, device connectivity, and device logs. IP addresses are sent to the loadbalancer through the Tdeployer module as part of the topology changes.
See service loadbalancer and show loadbalancer.
-
Messagebus (Kafka)—In the Juniper Security Director, Kafka is used by the applications as the messaging queue or bus. Kafka service is used to build real-time streaming data pipelines and applications that combines messaging, storage, and stream processing capabilities. In the Juniper Security Director, the following two message buses are used:
-
Config messagebus—Config messagebus is used by the services for the configuration of the devices.
-
Logging messagebus—Logging messagebus is used by the services for the device logs.
-
-
Repository—Repository service is responsible for following tasks:
-
Unpacks and stores the Helm or repository charts and Docker images for microservices.
-
Manages host-based (.deb) packages.
-
Ensures third-party repository services are running efficiently.
-
Unpacks the software contents of a Juniper Security Director software bundle.
-
Verifies the authenticity of the software bundle.
See service repository and show repository.
-
-
System Logs—System logs help you to identify and troubleshoot issues that you might encounter on Juniper Security Director.
See About the System Logs Page, set systemlogs and system logs.
