Help us improve your experience.
Let us know what you think.
Do you have time for a two-minute survey?

Help us improve your experience.
Let us know what you think.
Do you have time for a two-minute survey?
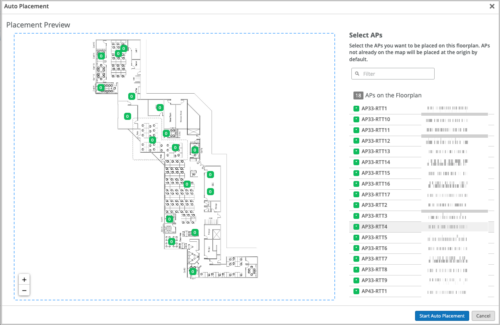
Mist now supports auto placement of access points (APs) on your floorplan. This location service feature automates and simplifies the Mist AP deployment and administration.
In a greenfield deployment (where APs are installed and claimed but not yet placed), you can use this feature to automatically configure the x, y coordinates to place your APs on the floorplan. In this case, you will need to manually configure the positions of the reference APs (or anchor APs) suggested by Mist. The positions of the reference APs are used to calculate the positions of the remaining APs. In a brownfield deployment (where APs are installed, claimed, and placed already), this feature helps you verify and correct the positions of the APs that are already on the floorplan.
When you initiate the auto placement operation, Mist calculates the new AP positions and lets you compare them with the current positions. You can then choose to accept or reject the placement suggestions.
You can perform automatic placement of APs from the Location > Live View > floorplan page.
We recommend that you plan for a maintenance window to run this process, because your wireless operations may be impacted while auto-placement is in progress. The automatic placement duration could vary depending on the number of APs on the floor plan. See the table below for a few examples:
|
Number of APs on the floor plan |
Automatic placement duration (in minutes) |
|
10 |
4 |
|
50 |
20 |
|
100 |
40 |
Note that the APs must have the firmware version 0.14.x or newer to support the auto placement feature. Autoplacement is not supported on Wi-Fi 5 APs (AP21,AP41,AP61).
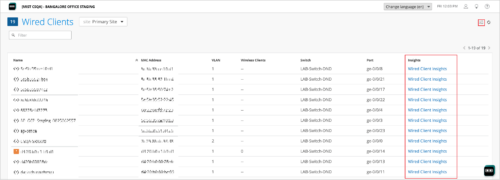
You can now access the insights view of your sites, devices, and clients from their list pages. This option is helpful for Mist admins who need to frequently access the insights data for troubleshooting purposes. Previously, for device and site insights, you had to navigate to the device and site details pages.
The following are the list pages that now provide the option to access the insights view: Access Points, Switches, WAN Edges, Cellular Edges, Mist Edges, Wired Clients, WiFi Clients, and Sites (Organization > Site Configurations). These pages display hyperlinks to access the insights view, in the Insights column.
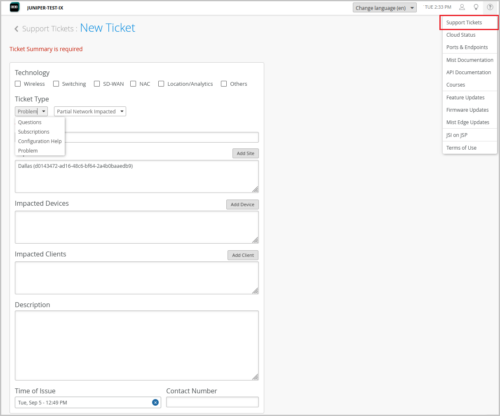
To streamline our customer support process, we have revamped the Support Tickets creation UI on the Mist portal. The new UI lets you submit issues or questions with more specific details, helping you reach the right support team quicker. You can group your issues under specific technology types that include Wireless, Switching, SD-WAN, NAC, Location/Analytics, and Others. The new UI supports the following ticket types:
Questions: Submit your questions.
Subscriptions: Request support for a subscription order. You need to provide a ticket summary along with the subscription order ID.
Configuration Help: Request support for your configuration.
Problem: Submit a problem. You can specify whether the problem impacts the network fully or partially, or it affects only specific devices or sites. You can also raise RMA requests from here.
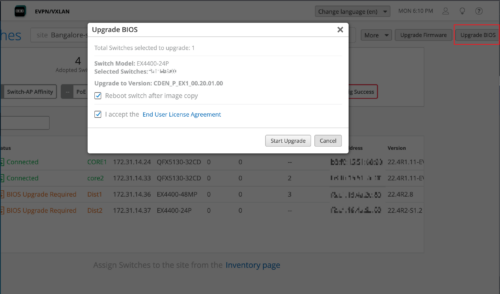
You can now upgrade the BIOS on the EX4400 switches to the latest version, using the Upgrade BIOS option on the Switches page. The existing BIOS version running on these devices is CDEN_P_EX1_00.15.01.00. You can now upgrade it to CDEN_P_EX1_00.20.01.00. We recommend that you upgrade the BIOS version of those EX4400 switches that display the status BIOS Upgrade Required on the Switches page. Without the latest BIOS version, the EX4400 switches might unexpectedly reboot, impacting your services.
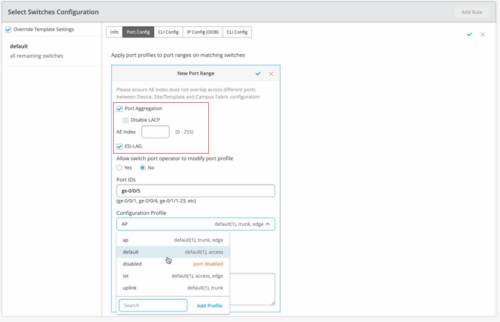
You can configure ESI Link Aggregation Groups (ESI-LAGs) on the aggregated Ethernet (AE) interfaces on a switch participating in Campus Fabric (EVPN/VXLAN). This functionality is an extension of ESI-LAG option available on the switch detail page (switch dashboard) to the site and organization level now.
Mist supports ESI-LAG only on the AE ports that are configured with Link Aggregation Control Protocol (LACP). You can now configure ESI-LAG at the device, site template, and organization template levels, using the options on the following pages:
Device Level: On the Port Configuration tile on the Switches > switch name page.
Site level: On the Port Config tab in the Select Switches Configuration section on the Site > Switch Configuration > switch configuration name page.
Organization level: On the Port Config tab in the Select Switches Configuration section on the Organization > Switch Templates > template name page.
ESI link aggregation groups (ESI-LAGs) enable one or more client devices to form a logical link aggregation group (LAG) interface with the peers.
Note: To be able to apply the ESI-LAG configuration, you need to have the switch included in a campus fabric configuration.
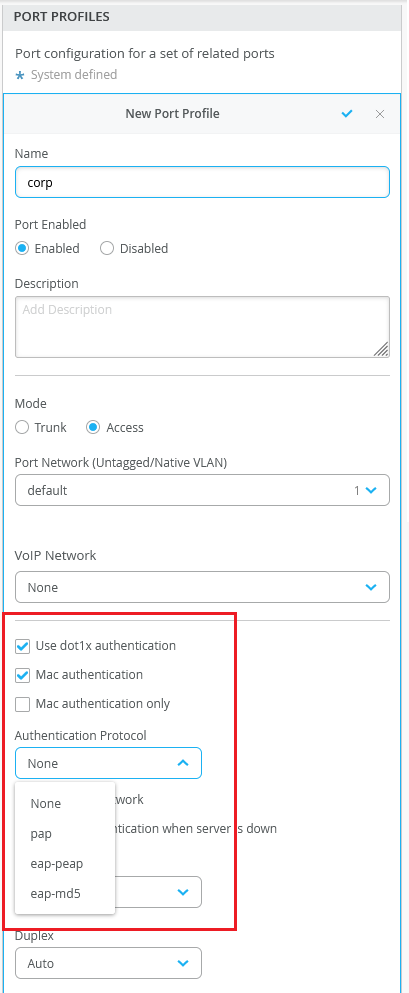
You can configure authentication protocols on the port profiles that use dot1x authentication with the MAC authentication option. Junos supports the following protocols: Protected Extensible Authentication Protocol (eap-peap), Password Authentication Protocol (pap), and eap-md5. These protocols are used by a supplicant to provide authentication credentials for MAC RADIUS authentication. You can configure these protocols from the Port Profiles tile on the switch dashboard (Switches > switch name), site template (Sites > Switch Configuration > switch configuration name), and organization template (Organization > Switch Templates > template name) pages.
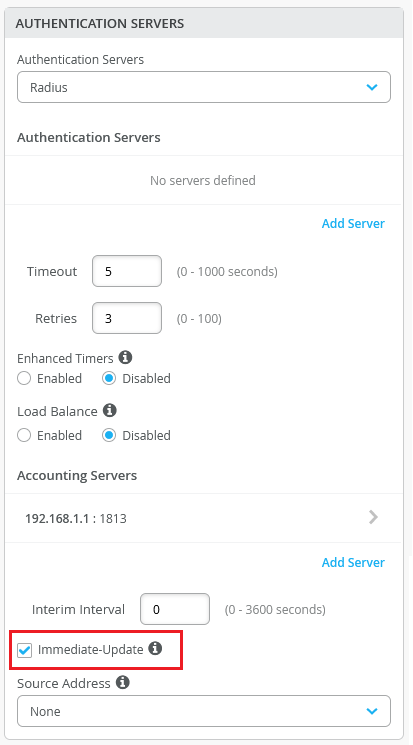
You can configure your switch to send an Acct-Update message to the RADIUS accounting server immediately following a change of authorization (CoA) operation, IPv4 address allocation, or de-allocation. To do this, select the Immediate-Update check box on the Authentication Servers tile on the switch configuration page (organization template, site template, or the switch dashboard). This option is available only if you have configured a RADIUS accounting server.
Dynamic Port Configuration mainly involves two steps – defining dynamic port profile assignment rules (or dynamic port configuration) and then enabling the rules on the ports to be set as dynamic ports. If you do not enable any port to function as a dynamic port after defining a dynamic port configuration set, the switch dashboard displays a message suggesting that you set a port to function as a dynamic port.
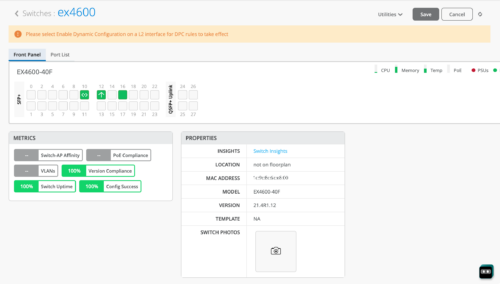
Similarly, if you enable a port to function as dynamic port but forgot to define the dynamic port profile assignment rules, the switch dashboard displays a message suggesting that you define the dynamic port configuration.
You can create dynamic port configuration from the switch template or from the switch detail page (switch dashboard).
The Switch Insights page now provides the following indicators in the new Table Capacity section:
MAC Address Table: Displays the percentage of the MAC address table capacity used. The MAC address table contains MAC Address-interface bindings associated with each VLAN.
ARP Table: Displays the percentage of Address Resolution Protocol (ARP) table capacity used. The ARP table contains the learned MAC Address-IP bindings of the devices connected to the network.
Route Summary: Displays the percentage of routing table capacity used.
You can hover over each of these indicators to view the number of entries in each table.
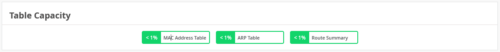
The color of these indicators changes depending on the percentage of the table capacity used, as shown below.
|
Color of the indicator |
Percentage of the table capacity used |
|---|---|
|
Green |
0 to 80 |
|
Orange |
81 to 90 |
|
Red |
91 to 100 |
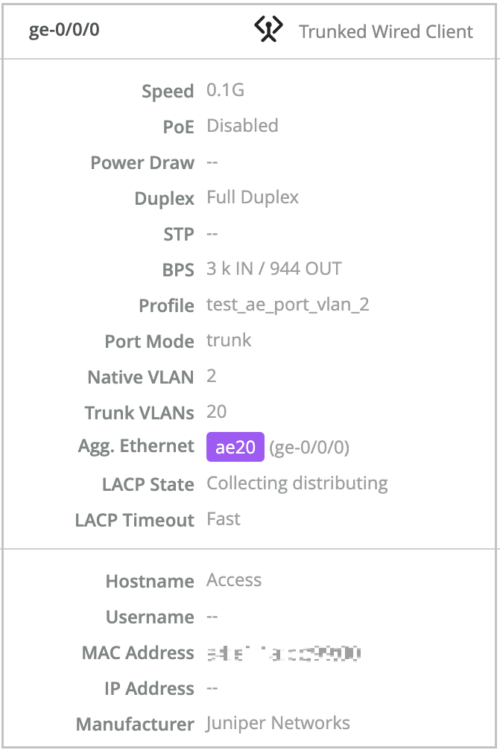
You can now view the Link Aggregation Control Protocol (LACP) states (or Mux states) of the aggregated Ethernet (AE) interfaces on your switch. The following LACP states are supported: Attached, Detached, and Collecting distributing. You can also see the LACP timeout information. The timeout values supported are fast and slow. If a port doesn’t have the aggregated Ethernet configuration, the LACP status is not available for that port.
To view the LACP status of a port, navigate to the switch dashboard (Switches > switch name) and hover over the port on the Front Panel tab. You can also click the port to view this information.
The Switch Events section on the Switch Insights page displays an event when an aggregated Ethernet interface included in a Link Aggregation Control Protocol (LACP) bundle does not receive the LACP stats despite the bundle being up.
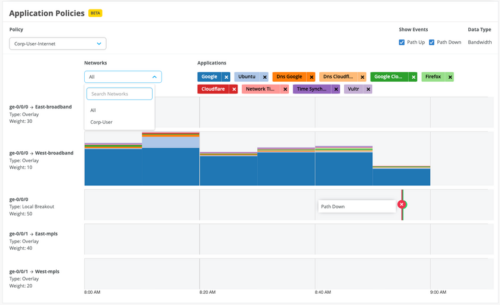
We have added an Application Policies dashboard to the WAN Edge Insights page. This dashboard shows the paths the application traffic takes to traverse through the network. The information displayed also includes the WAN links and the details of any events that impacted those paths. You can view this information for each policy. If your policy contains a lot of source networks and users, you can apply filters to view the source network or users that you are interested in.
Note: For the traffic sent by an SSR device via Juniper Secure Edge Connectors, the Application Policies section displays only the traffic data. It doesn’t display an Application Routing Visibility chart.
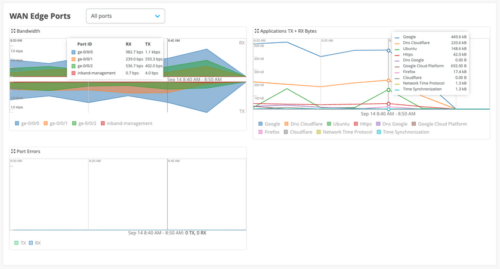
We have enhanced the WAN Edge Port insights section with an Application TX+ RX Bytes dashboard. The dashboard provides a default view of the top 10 applications on the WAN links of a given WAN Edge device based on traffic. You can choose to view the data per interface or for all interfaces together.
Mist now supports traffic steering based on the application detected through deep packet inspection (DPI). Application steering for DPI-detected traffic works for custom and built-in applications.
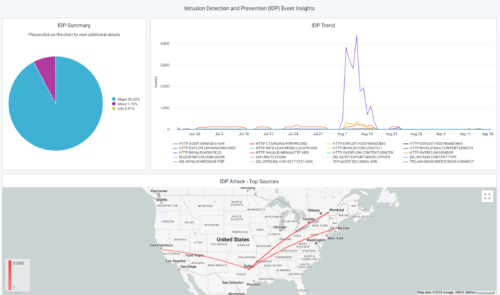
We have added a new Intrusion Detection and Prevention (IDP) profile to the application policy configuration for SRX devices. The new profile, called Critical Only – SRX, detects critical attack signatures and takes the recommended action. You can select the new profile from the IDP drop down menu on the application policy configuration page (Organization > Application Policy).
The IDP policies enable you to selectively enforce various attack detection and prevention techniques on the network traffic passing through an IDP-enabled device.
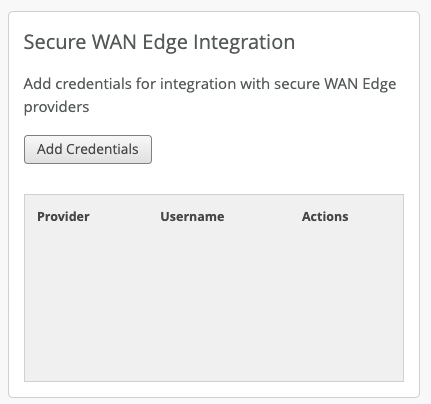
To further simplify the cloud-to-cloud integration with Zscaler, Mist now supports automatic provisioning of Zscaler tunnels. This process involves the following two steps:
Providing credentials required to integrate Mist cloud with the secure WAN edge provider (Zscaler). You can add credentials from the Secure WAN Edge Integration tile on the Organization > Settings page. The information includes the user’s email address, password, Juniper partner key, and the cloud name.
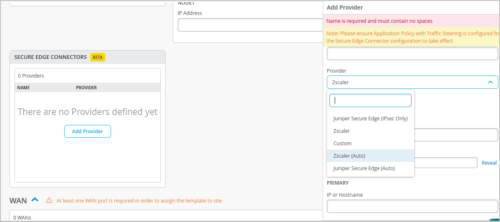
When you assign a template enabled with the Zscaler (Auto) option to a site, the following operations take place:
An associated Zscaler site (location object) is automatically created.
The details required for tunnel creation are exchanged between Mist and Zscaler.
Tunnels are brought up from the device to the closest network point of presence (POP).
The WAN Edge Insights page now displays some additional client details based on DHCP events. The details displayed include hostnames of some clients which were previously listed as anonymous devices. This information is displayed on the clients list launched from the Number of clients column in the Applications section on the WAN Edge Insights page.
Mist now supports the following Cradlepoint devices:
R1900 router
AER2200 router
CBA850 LTE adapter and its sub models
You can view the inventory details for the Cradlepoint devices onboarded to the Mist cloud from the Organization > Inventory > Cellular Edges page. You can also assign these devices to a site by clicking More > Assign to Site.
See Release 6.1.5-14.
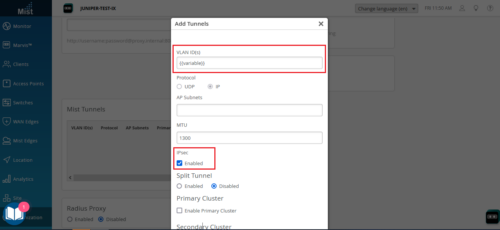
We have made the following changes to the site-level Mist Tunnels (Organization > Site Configuration > site name > Mist Tunnels):
Support for configuring VLAN IDs through site variables. Site variables provide a way to use tags (example: “VLAN_VAR”) to represent real values (example: 11) so that the value can vary according to the context where you use the variable. This means the same variable can configure different VLAN IDs in different sites.
IPsec support for site-level Mist Tunnels. This feature enables you to use IPsec protocols for the tunnels from APs to site-level Mist Edges.
To capture the insights and historic trends in WAN security events, we have introduced a new Premium Analytics dashboard called WAN Security Insights – SSR. This dashboard provides crucial insights derived from the URL filtering events and intrusion detection and prevention system (IDS or IPS) events generated by an SSR device with Advanced Security Pack. For more information about the SSR Advanced Security Pack, see Juniper Session Smart Networking Advanced Security Pack Datasheet.