Change of Authorization (CoA)
Explore the benefits of adding a Change of Authorization (CoA) server to your WLAN.
With Change of Authorization (CoA), you can modify authorized RADIUS sessions after initial authentication to meet changing access requirements. For example, CoA can enable use cases such as administrator-initiated session resets to terminate sessions. CoA also can be used to grant updated access to users after they successfully complete guest registration.
Benefits of Change of Authorization (CoA) in RADIUS
Benefits of Change of Authorization (CoA) in RADIUS:
-
Enhances control over active user sessions: By allowing the RADIUS server to send unsolicited messages to the NAS, CoA gives you the ability to modify session characteristics after initial authentication. This enhanced control can be used to terminate or re-authorize user sessions as required.
-
Overcomes limitations of standard RADIUS protocol: The standard RADIUS protocol only allows messages to be initiated by the NAS. CoA extends this functionality, providing a more flexible and dynamic approach to session management.
-
Streamlines Network Administration: The Disconnect Message feature of CoA allows for efficient session resets. This not only saves time and resources, but also simplifies administrative duties.
-
Facilitates Guest Access Management: The CoA Re-Auth Message feature can be utilized to grant full network access after a guest user registers through a captive portal, making the process of managing guest access smoother and more effective.
-
Supports Vendor-Specific Attributes: CoA's compatibility with vendor-specific attributes enables effective interoperation between the RADIUS server and NAS devices when sending CoA messages. This contributes to a seamless and efficient network operation.
Enabling CoA in the WLAN Settings
In the WLAN settings, go to the CoA/DM Server section to enable this feature. Enter the IP Address and Shared Secret. You can keep the default Port value or specify a port.
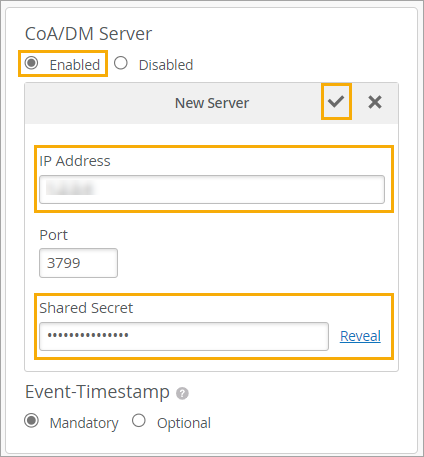
For more help with WLAN settings, see Configure a WLAN Template and WLAN Options.
How CoA Works
When you implement the Change of Authorization (CoA) feature in your RADIUS environment, you empower the RADIUS server to actively send unsolicited messages to the Network Access Server (NAS) to modify session characteristics after the initial authentication process. This proactive approach addresses the limitations of the standard RADIUS protocol, which traditionally permits only the NAS to initiate messages.
In the CoA functionality, there are two primary message types that you can leverage:
-
Disconnect Message: This message type is designed to terminate user sessions by incorporating the
Acct-Terminate-Causeattribute in the message. A key application of this feature is when you need to reset sessions for various reasons. -
CoA Re-Auth Message: This message type prompts the NAS to re-authorize a session. In scenarios like Guest Access, this is particularly useful when a guest user completes registration through a captive portal, and consequently, the network grants them full access. To convey the re-authorize command effectively, the message employs vendor-specific attributes.
To ensure seamless interoperability between the RADIUS server and NAS devices, you might need to enable support for specific vendor attributes. By doing so, you facilitate the smooth functioning of CoA messages within your network infrastructure.
In summary, by incorporating the CoA feature in your RADIUS environment, you can achieve the following:
-
Enable RADIUS servers to actively modify sessions after authentication, overcoming the constraints of the standard protocol.
-
Utilize two key message types (Disconnect and CoA Re-Auth) to manage different session scenarios effectively.
-
Address various use cases, such as administrator-initiated session resets and granting full network access to guest users post-registration.
-
Leverage vendor-specific attributes to ensure optimal compatibility and functionality of CoA across different network devices.
By adopting this approach, you can create a more dynamic and responsive network environment, capable of handling diverse session management requirements and providing a robust, secure experience for your users.
Message Flow
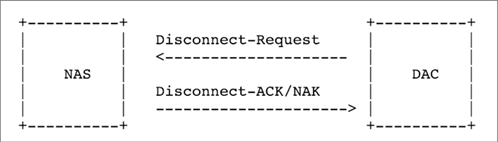
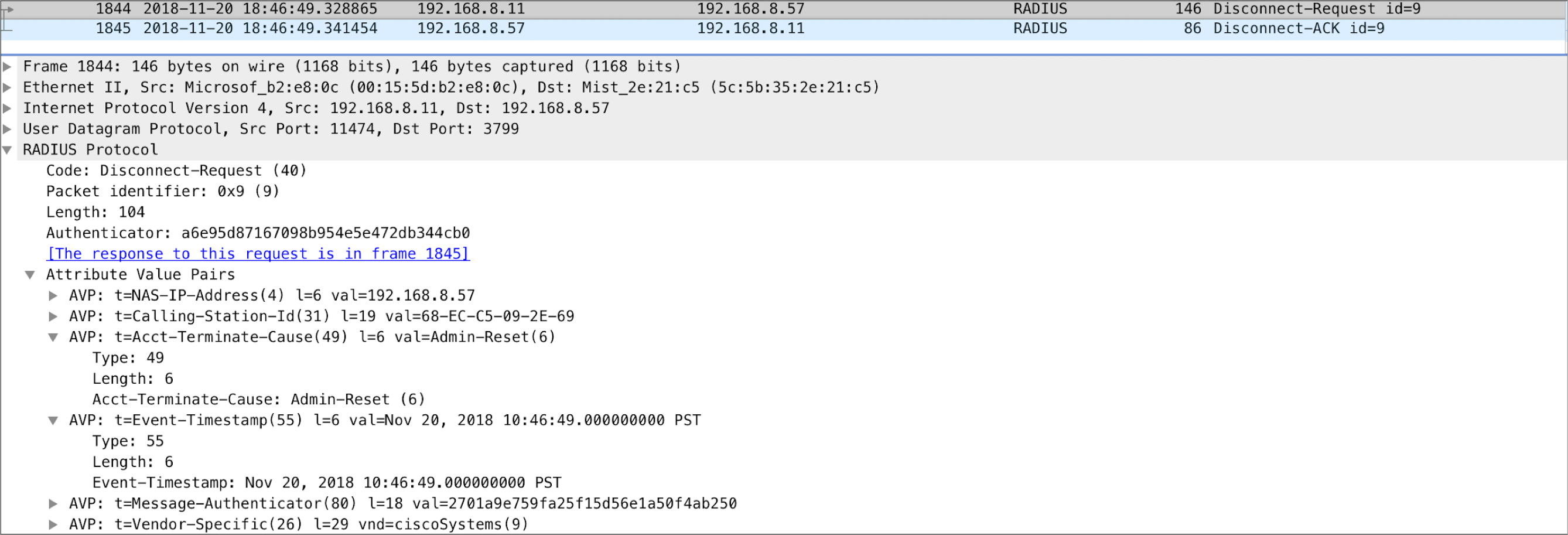
Disconnect Message: Session Termination
-
AVP: Acct-Terminate-Cuase
-
Value: Admin-Reset
-
CoA: Session Re-authentication
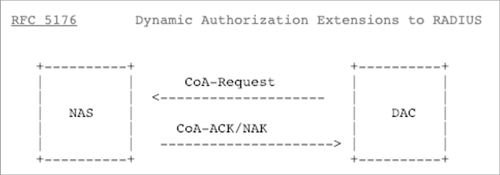
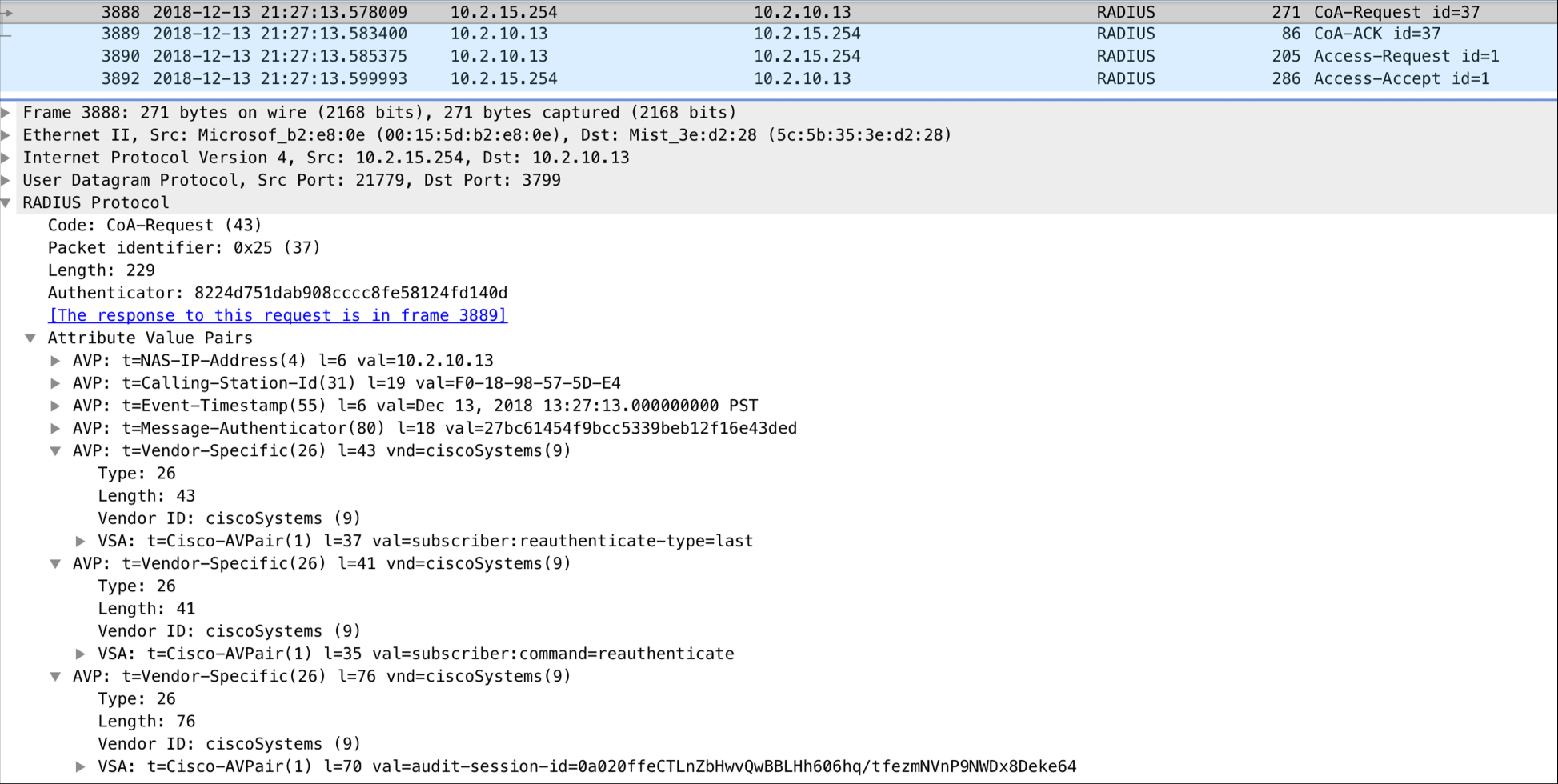
-
AVP: Vendor Specific (Cisco-AVP)
-
Value: Reauthenticate
CoA Messages that are not applicable to Juniper Mist:
-
Session termination with Port-Shut
-
Session termination with Port-Bounce
-
