JAMF Pro Integration
Follow these steps to create your client ID and secret on JAMF Pro, link your JAMF Pro account to your Juniper Mist™ organization, and verify the integration.
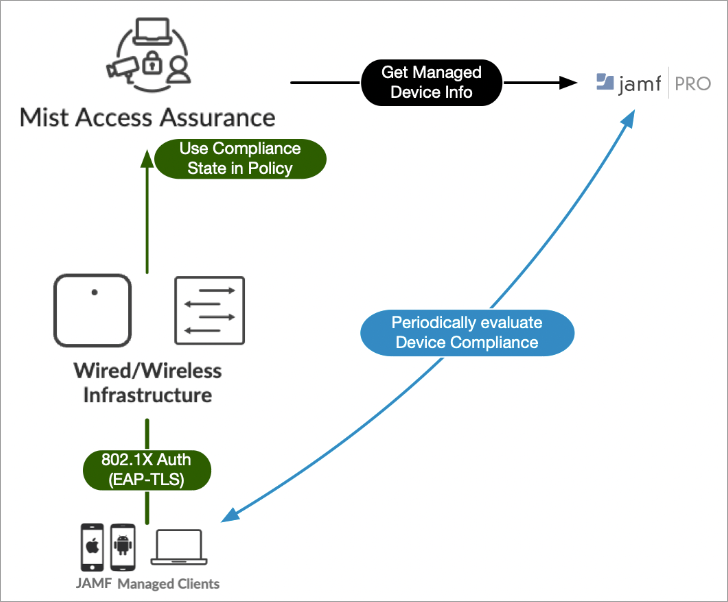
Mist Access Assurance allows you to integrate natively into JAMF Pro Endpoint Management platform for checking managed endpoint compliance state.
JAMF evaluates JAMF managed devices (MacBook, iPad, iPhone and other iOS devices) for compliance. Evaluation is done using Smart Computer Groups for MACbooks and Smart Device Groups for iPads and iOS devices for presence of antivirus, firewall status, software version, and so on. Mist Access Assurance obtains the compliance state of the devices and leverages that state in authentication policy rules to perform posture assessment.
JAMF Device Data Retrieval
Mist Access Assurance retrieves JAMF managed device data in the following manner:
-
Access Assurance uses API-based polling mechanism toward JAMF every two hours for every managed client that has been previously authenticated. Compliance states information is cached for fast retrieval.
-
Information retrieval is performed out-of-band, that is, after the authentication process to avoid any additional delays. After initial device onboarding, information is updated every two hours.
-
In case device compliance status changes, then Mist Access Assurance automatically trigger a Change Of Authorization to re-run the policy and apply respective action.
-
Juniper Mist access points (APs), which connect JAMF managed devices to the wireless network, must have firmware version 0.14 or higher.
Mist Access Assurance uses the following information during client authentication to match a client with a device record in JAMF:
- Non-randomized MAC address—This method can be used with EAP-TTLS or
EAP-TLS authentication. Client MAC device is matched with a device MAC present
in JAMF. For wireless profile, make sure MAC randomization or rotation is
disabled. Note:
iOS devices do not have native Ethernet NIC, so this method is only useful with iOS devices that are connected through wireless.
- JAMF Device UDID encoded in SAN:DNS certificate attribute. Figure 2 shows location
of UDID in configuration profile.Figure 2: Locating Unique Device ID
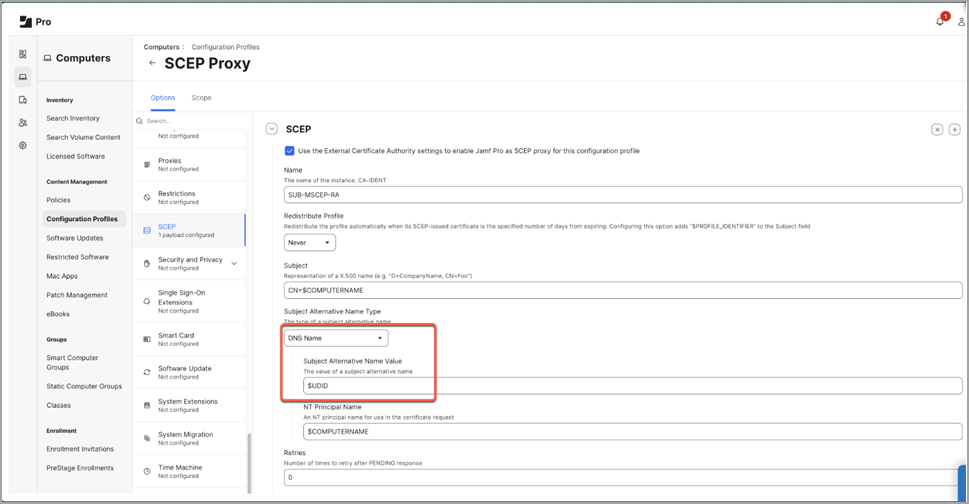
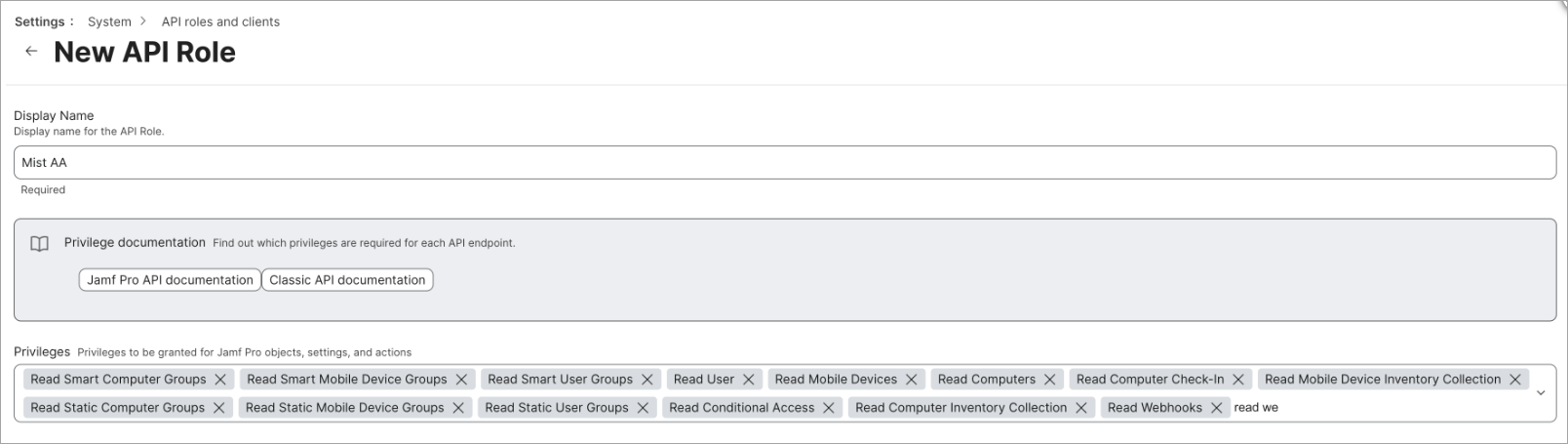
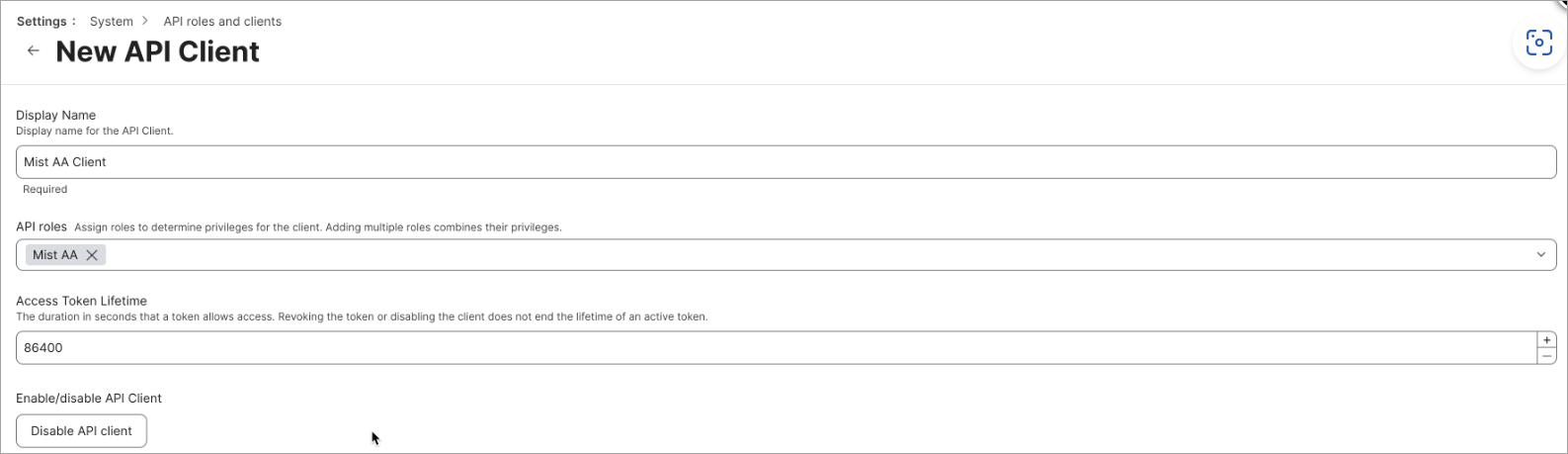
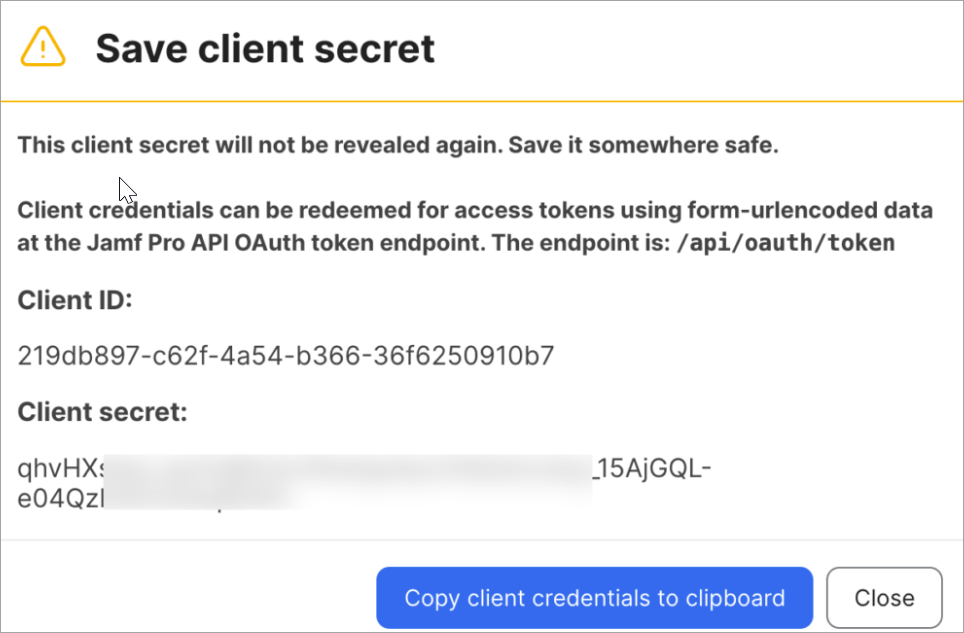
Create Client ID and Secret on the JAMF Pro
The screenshots from third-party applications are correct at the time of publishing. We have no way to know when or if the screenshots will be accurate at any future time. Please refer to the third-party website for guidance about changes to these screens or the workflows involved.
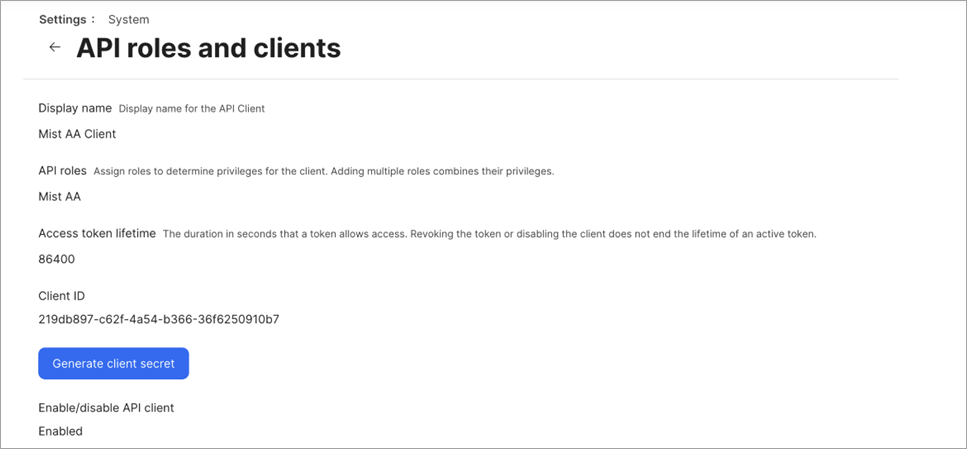
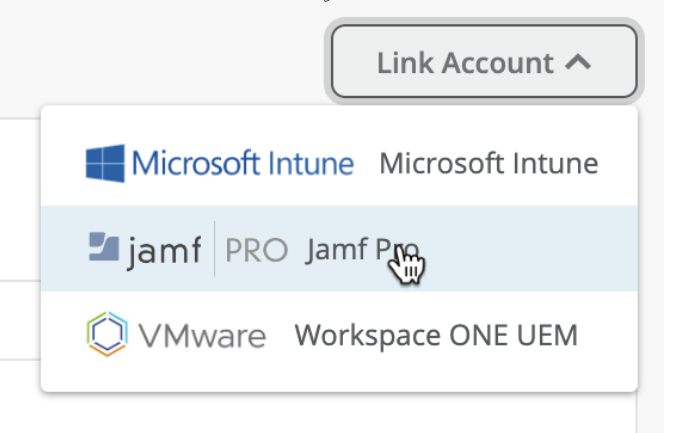
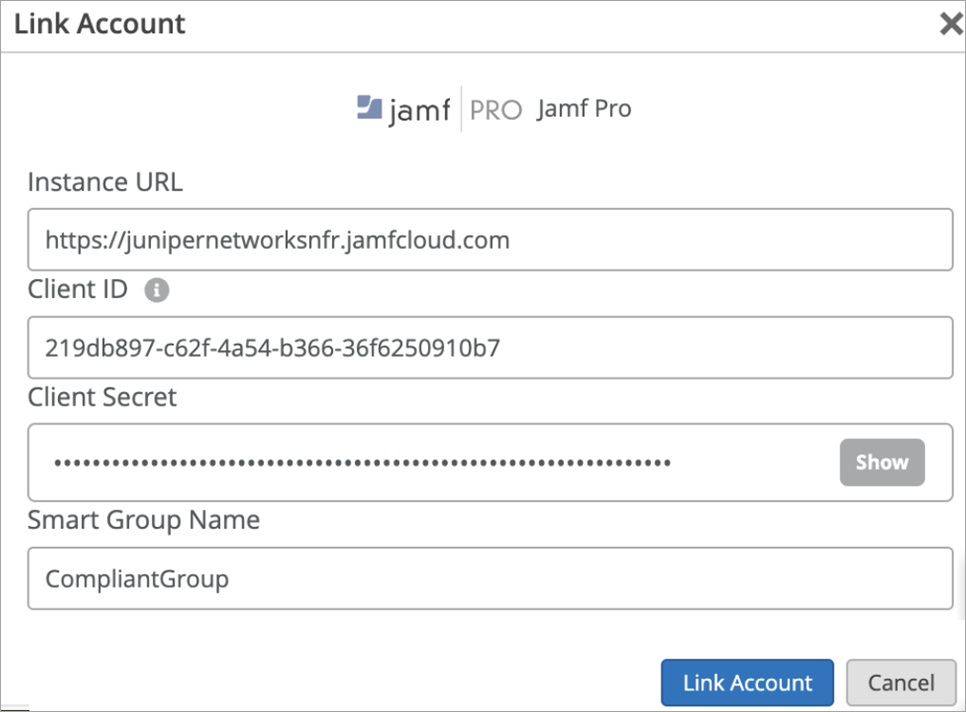
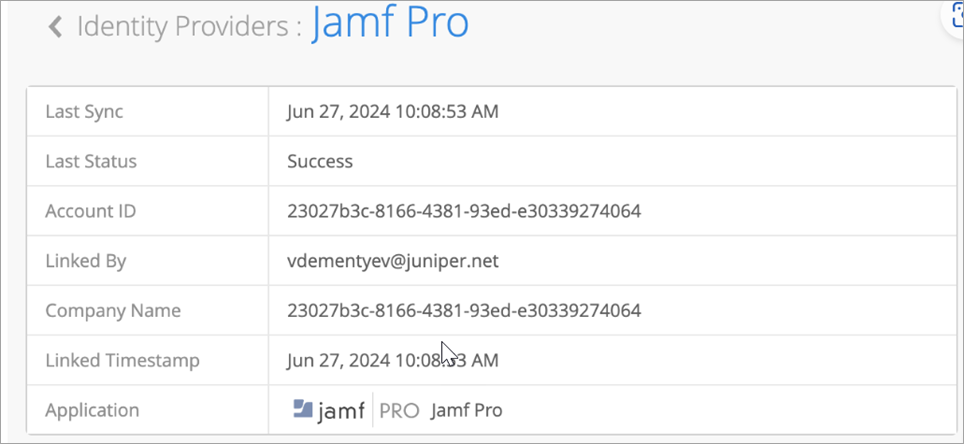
Link JAMF Pro Account to Mist Access Assurance
After linking is complete, you can see last sync status and time as shown in Figure 9.
Verification
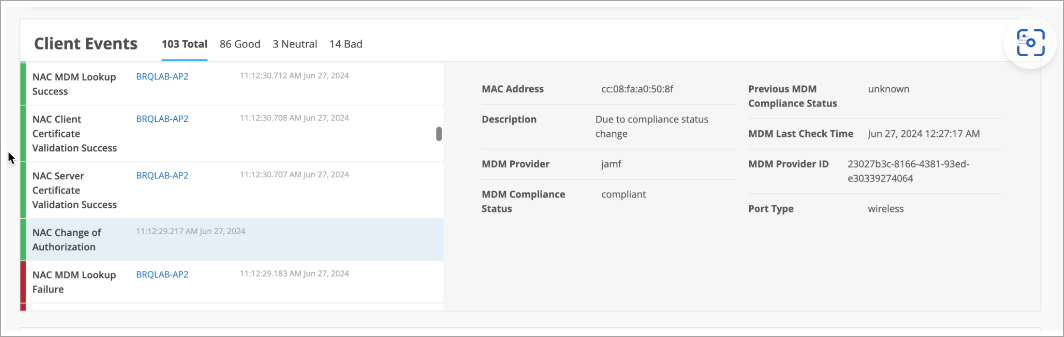
On the Juniper Mist portal, navigate to Monitoring > Insights > Client Events to see the information. Under Client Insights, you can see MDM lookups are performed for iOS managed devices as shown in Figure 10.
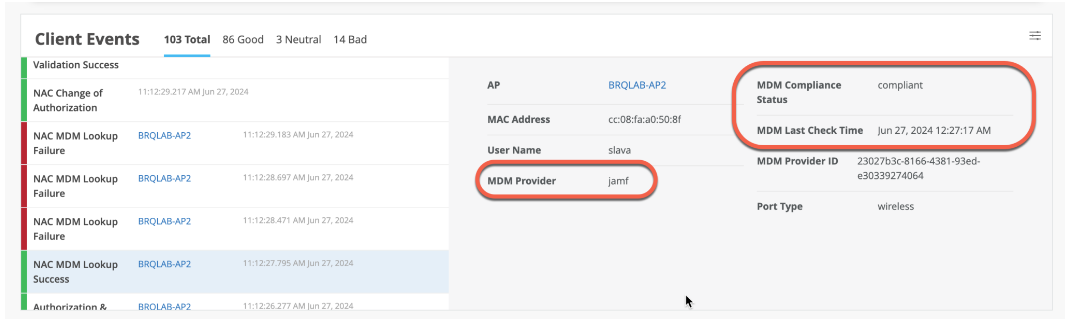
Note that during initial MDM lookup for a new client, lookup is performed post initial authentication. After MDM state changes, Mist Access Assurance initiates CoA to re-authenticate the client and apply the correct policy. Upon subsequent authentications, NAC uses MDM cache which is updated periodically to reflect any changes for every 2 hours. Figure 11 shows a sample of compliance status change.