Integrate Google Workspace as an Identity Provider
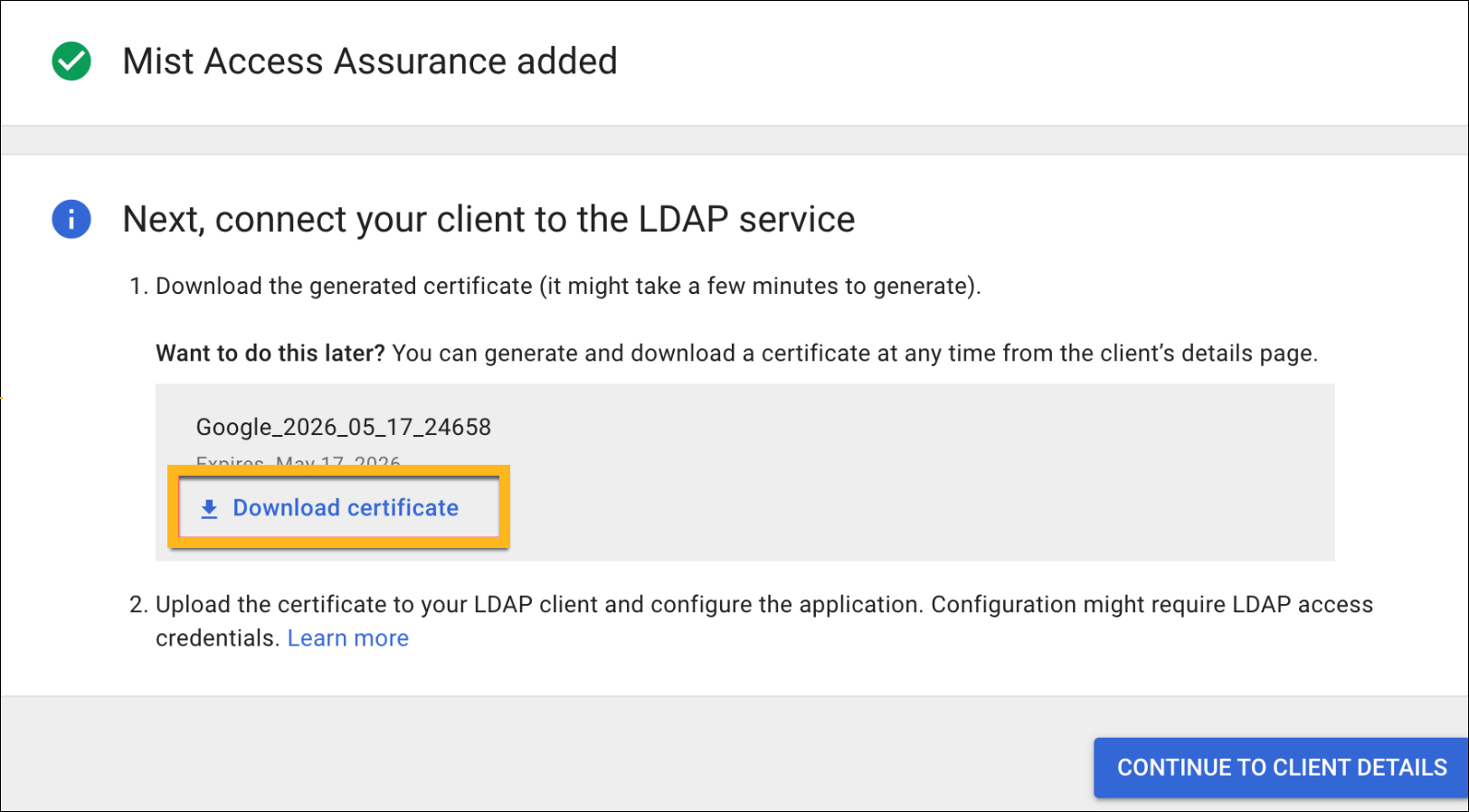
Follow these steps to add Mist as a client in your Google Workspace portal, download your certificate, and add your Identity Provider to your Juniper Mist organization.
Juniper Mist Access Assurance allows you to integrate with Google Workspace as Identity Provider (IdP) to leverage secure Lightweight Directory Access Protocol over SSL (LDAPS) connector for the following use cases:
- For certificate-based (EAP-TLS or
EAP-TTLS)
authorization:
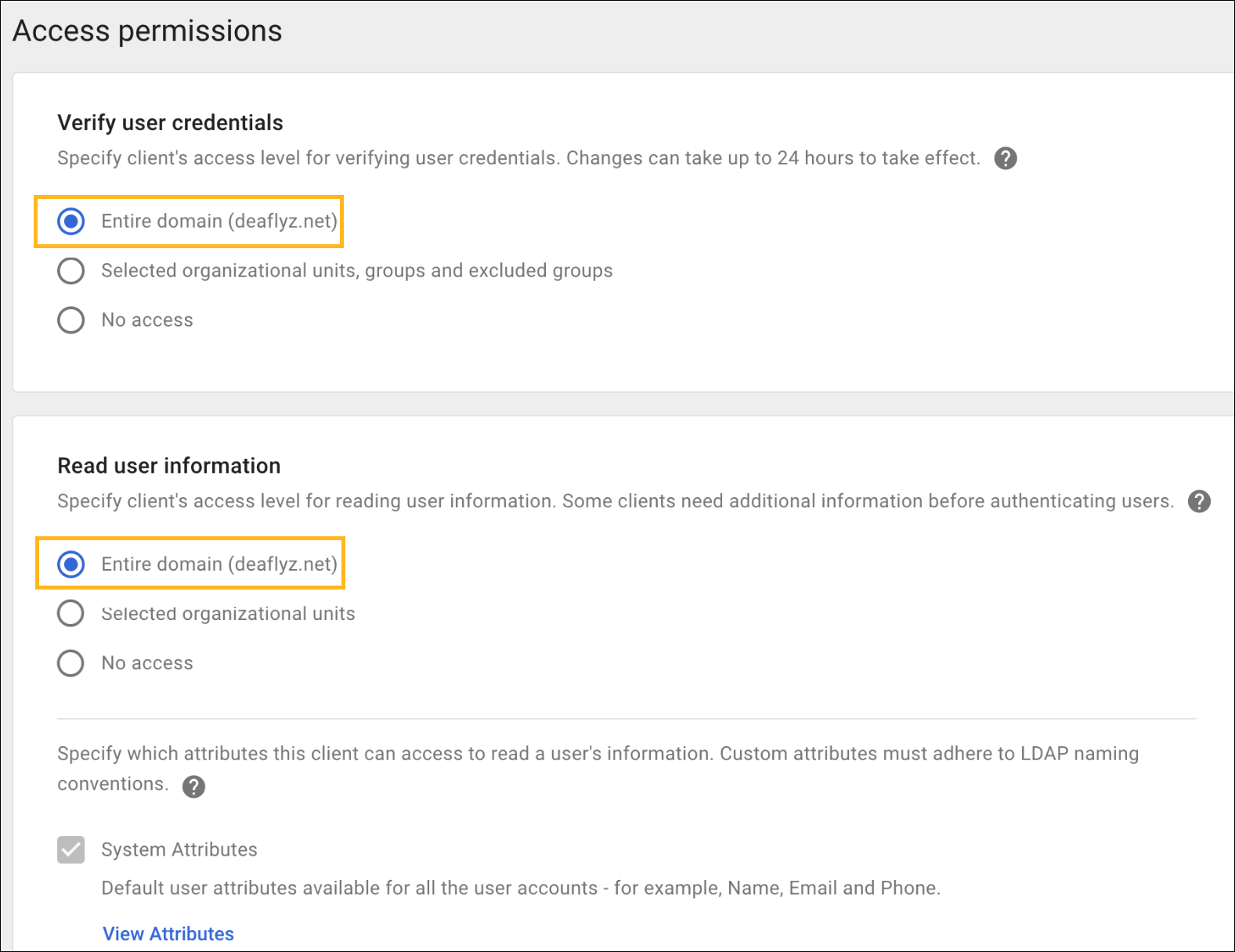
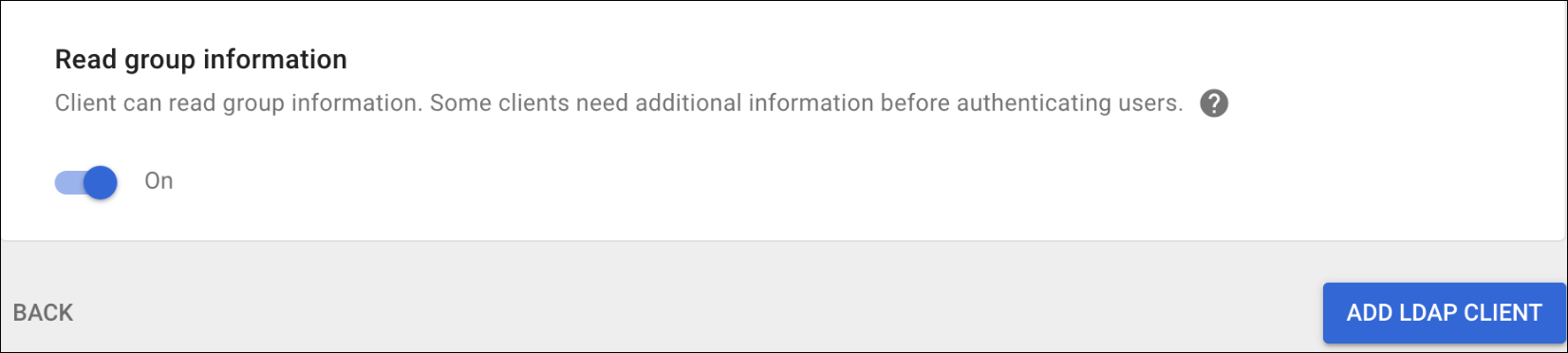
- Retrieves user group membership information to support authentication policies based on this user identity
- Gets the status—active or suspended—of an user account
-
EAP-TTLS with PAP
- Checks the username and password for authentication with Google’s Identity Provider
Some of the screenshots included in this document are sourced from third-party applications. Be aware that these screenshots may change over time and may not always match the current version of the applications.
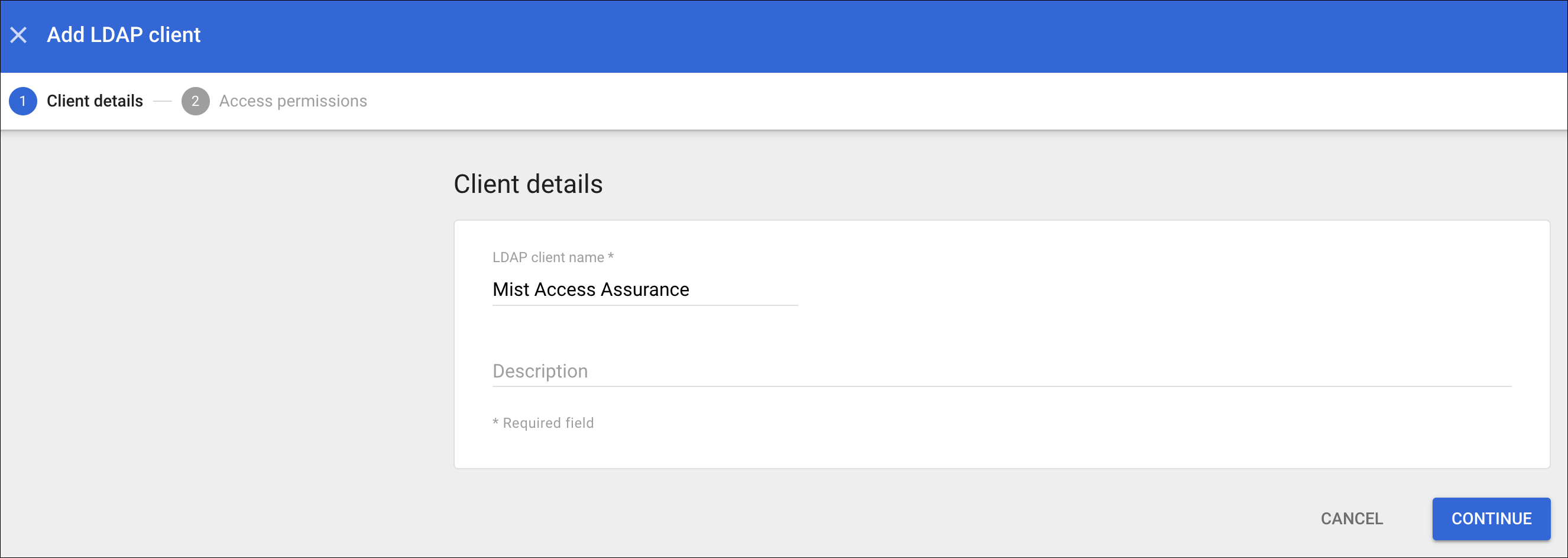
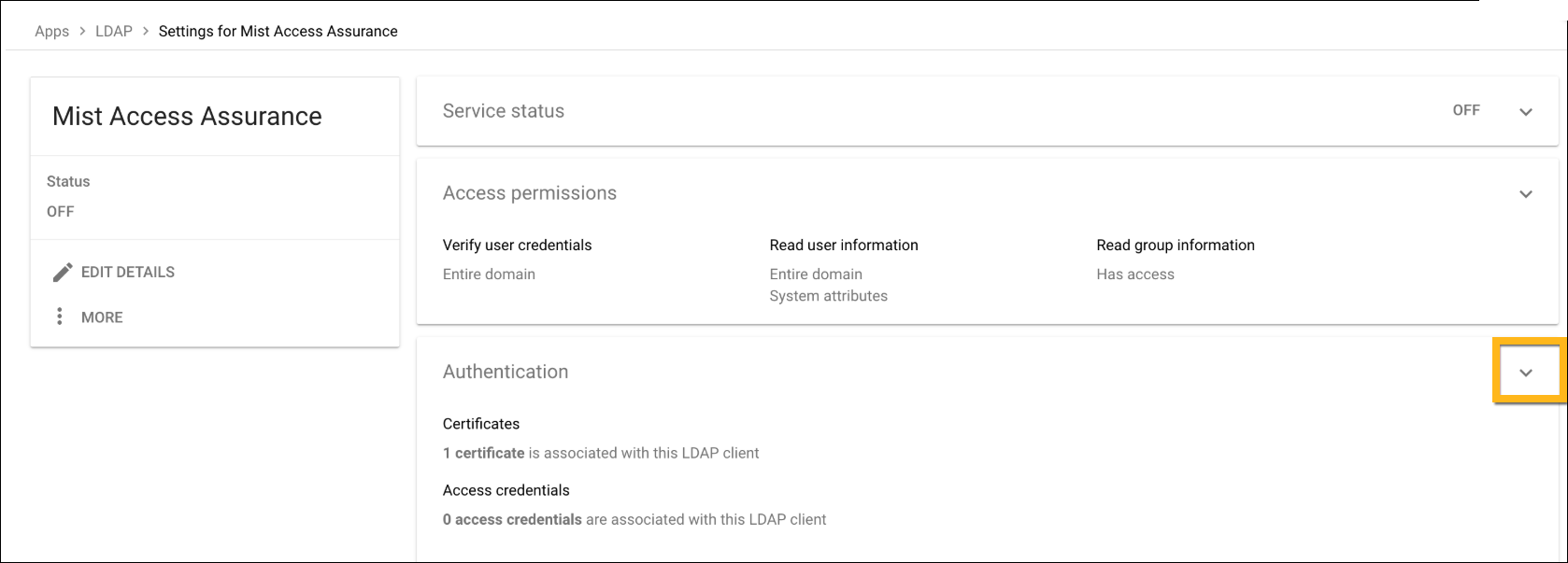
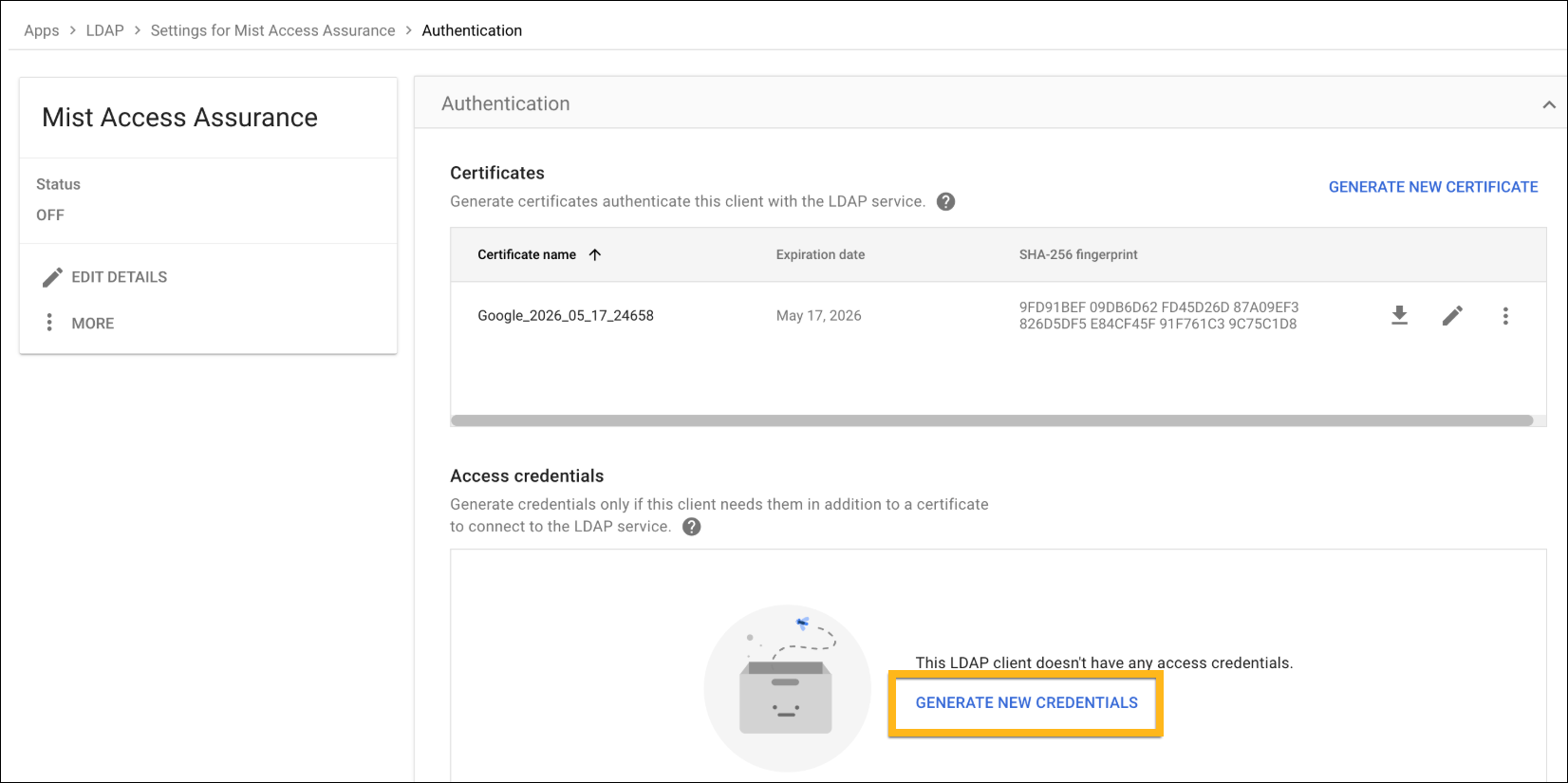
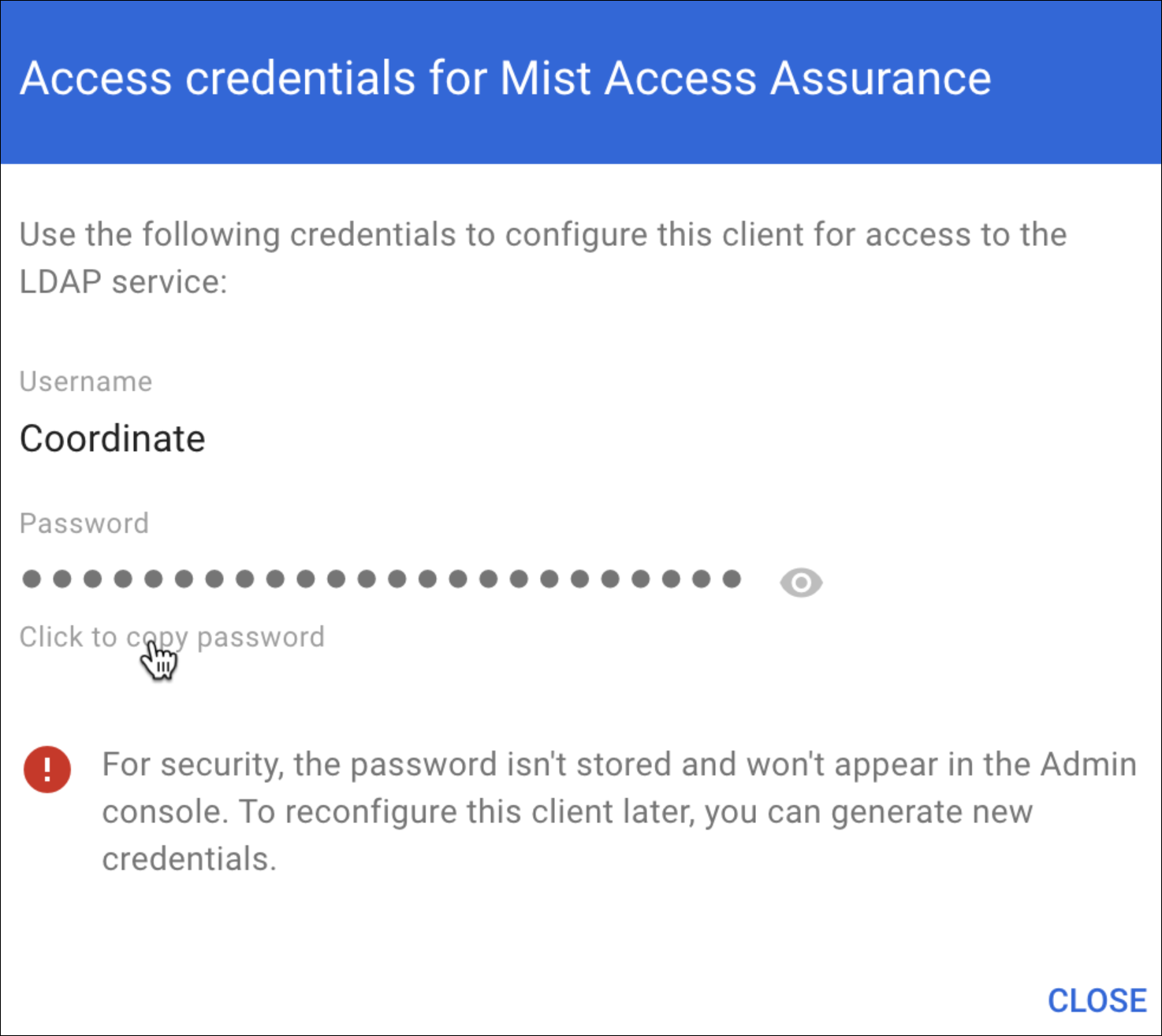
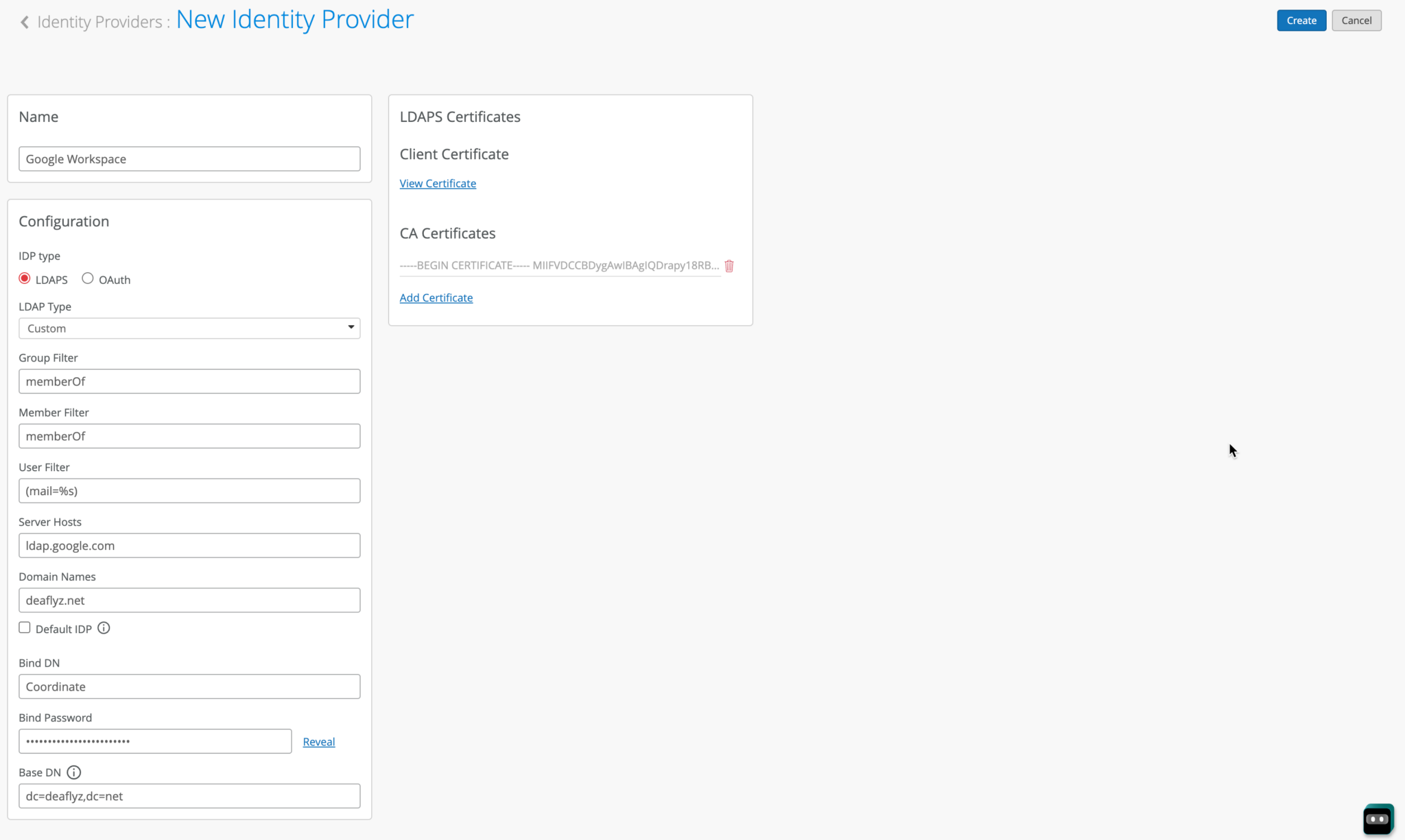
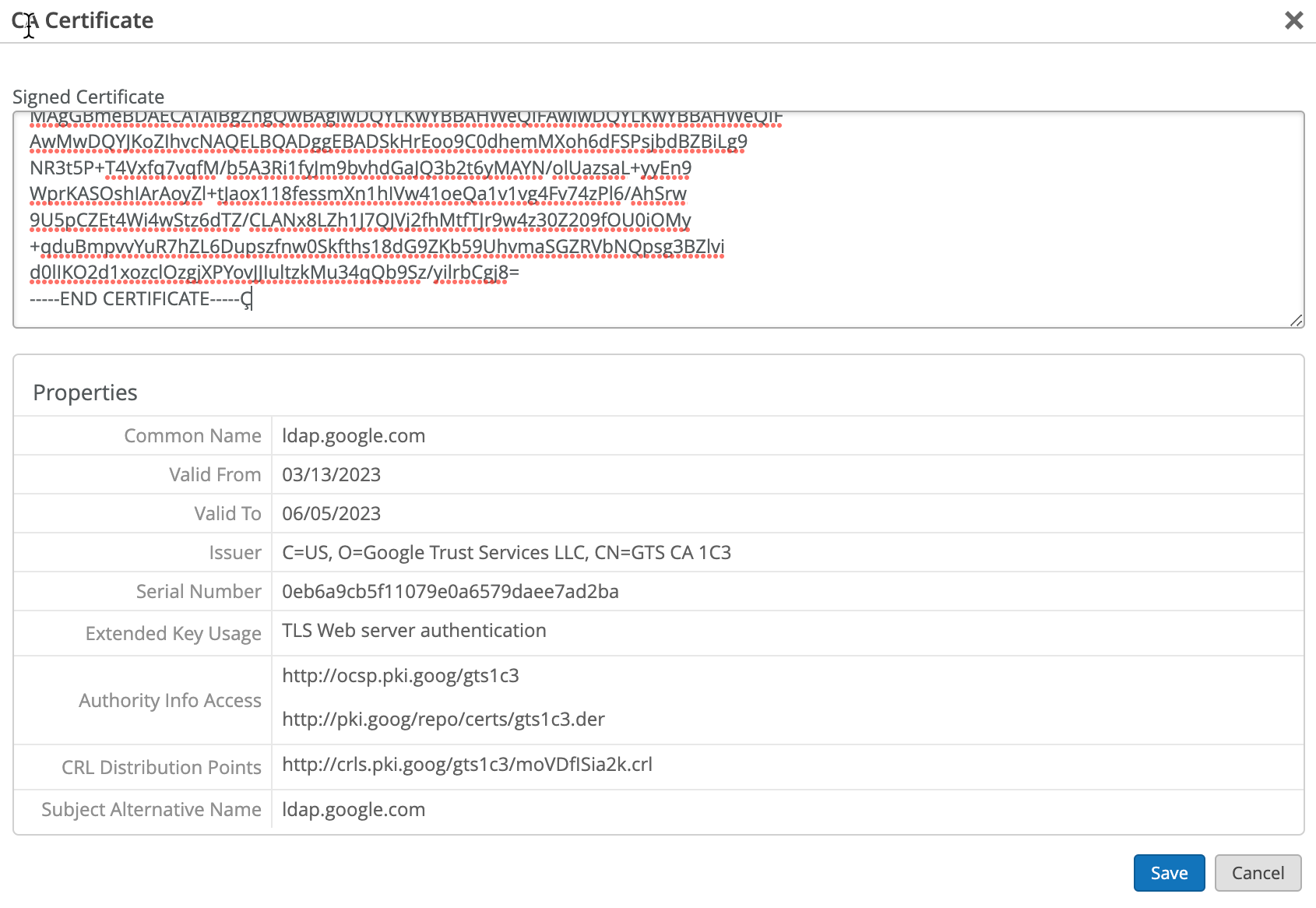
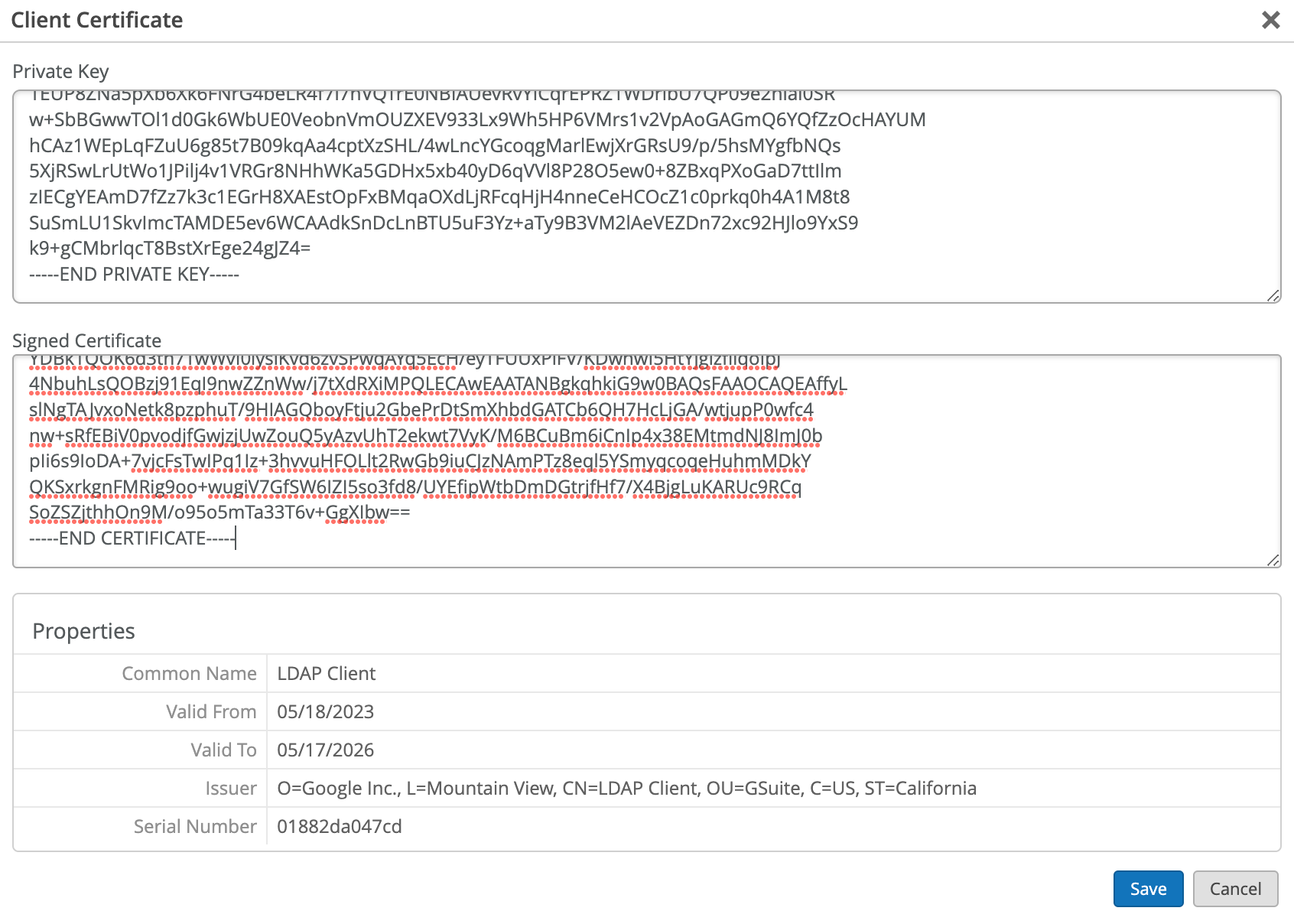
Configuration on Google Workspace
The following procedure shows you how to configure Google Workspace as an identity provider (IdP) with Juniper Mist.
The screenshots from third-party applications are correct at the time of publishing. We have no way to know when or if the screenshots will be accurate at any future time. Please refer to the third-party website for guidance about changes to these screens or the workflows involved.
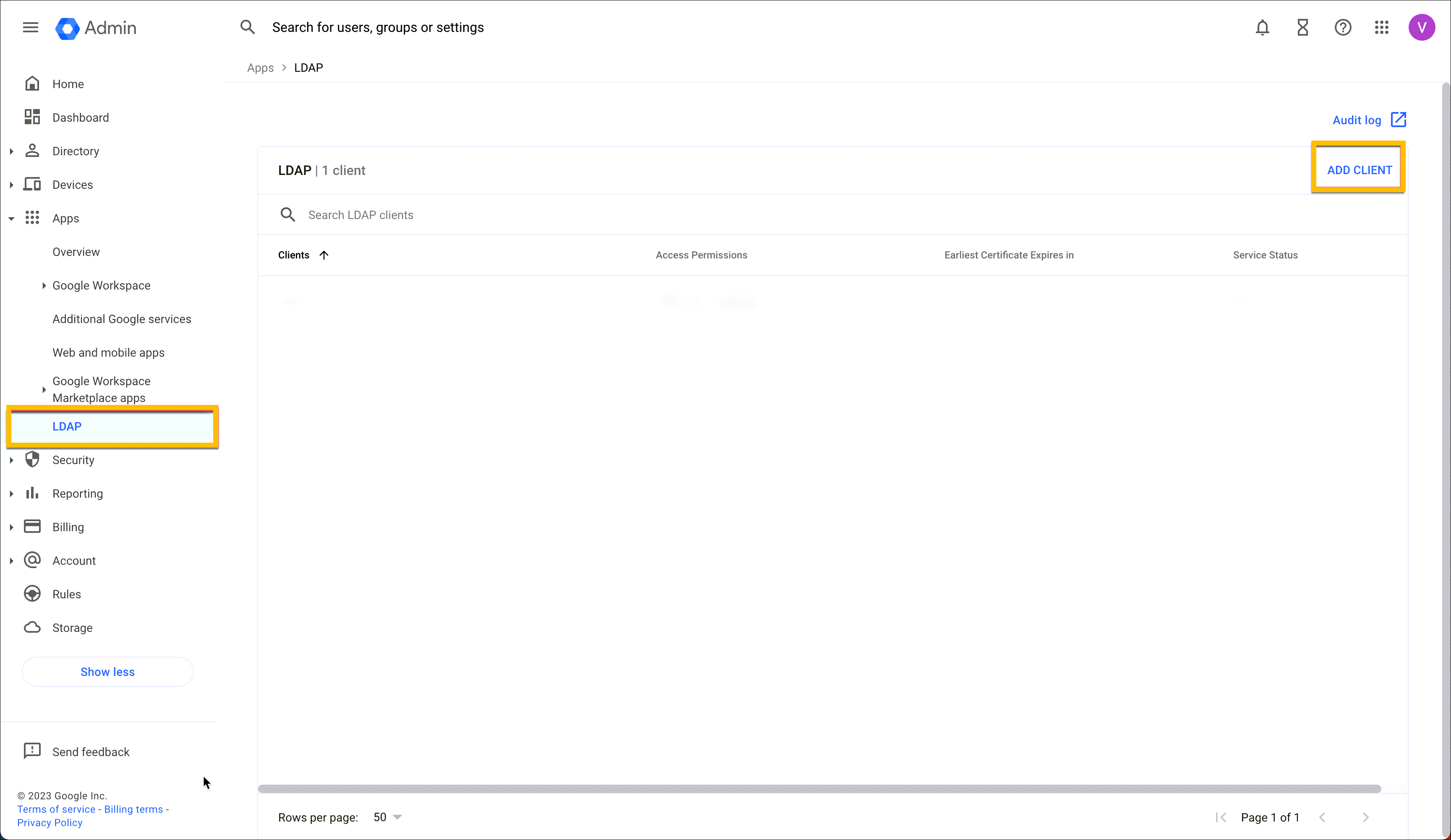
Configuration on Juniper Mist Dashboard
On the Juniper Mist portal, go to Monitoring > Insights > Client Events.
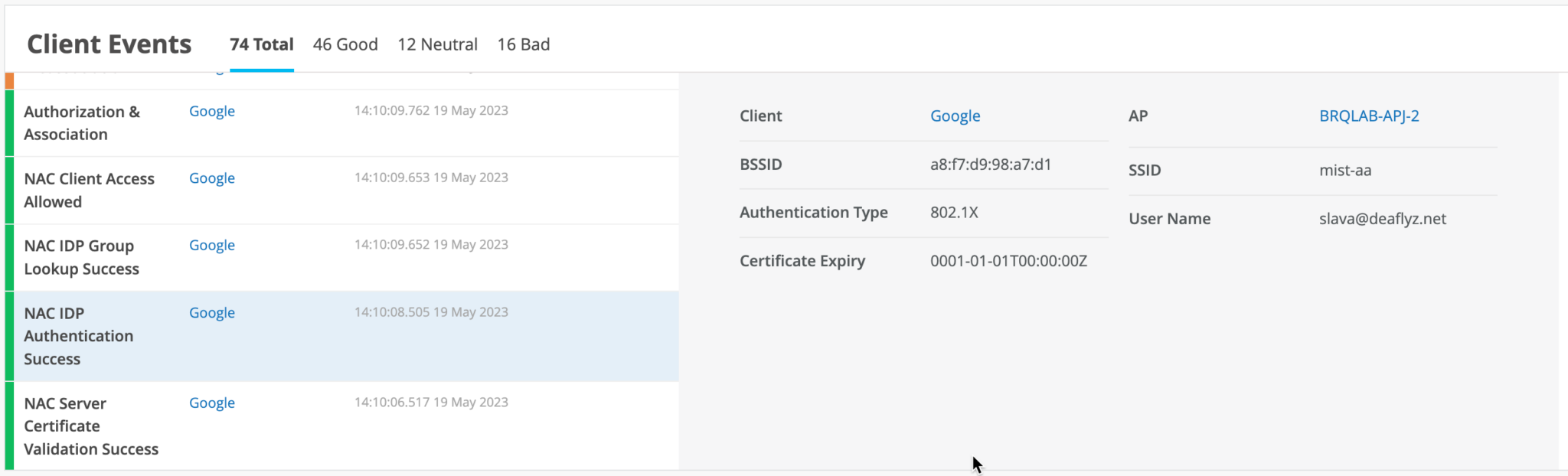
When a user authenticates using EAP-TTLS , you can see the NAC IDP Authentication Success and NAC IDP Group Lookup Success events that fetch user group membership information.
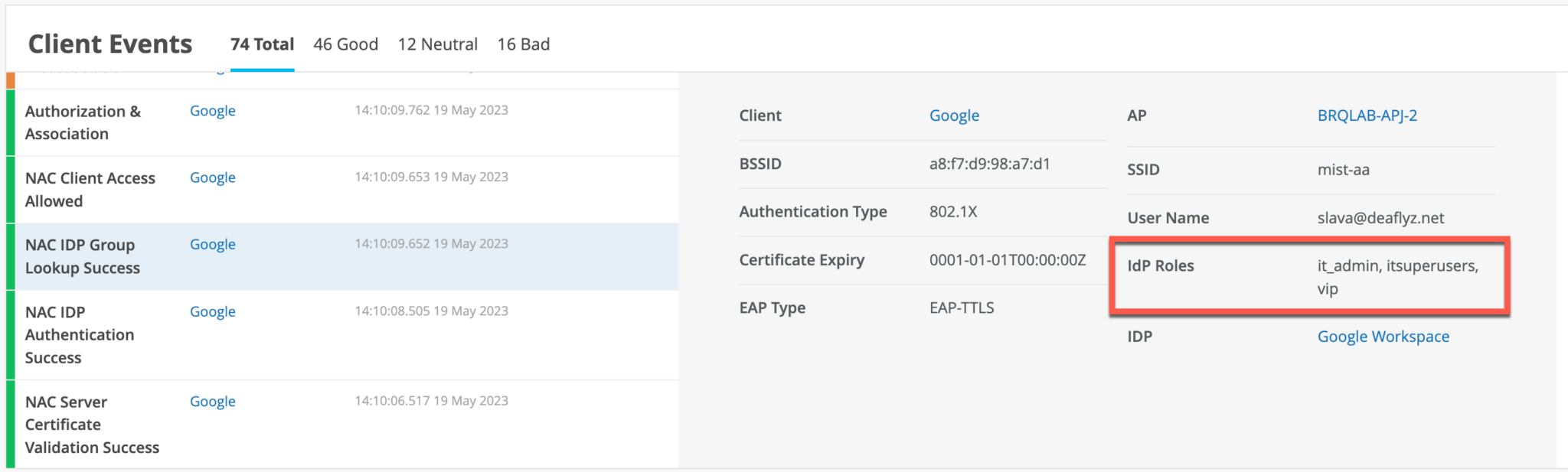
In case of EAP-TTLS authentication, you can see the NAC IDP Authentication Success event. This event indicates that Google Workspace has validated user credentials.
You may leverage IDP Roles from Google Workspace in your Auth policy rules to perform network segmentation based on user roles.
About EAP-TTLS and Azure AD using ROPC
Extensible Authentication Protocol–Tunneled TLS (EAP-TTLS) leverages LDAPS OAuth flow with Azure AD to perform user authentication. This implies the use of legacy authentication, which involves the use of a username and password without MFA. There are several factors to consider when employing this method:
- Configure client devices with the correct Wi-Fi profile, either from GPO or MDM. Providing only username and password at the login prompt does not work for some operating systems.
- Users must use Google Email ID (username@domain) username format for entering the username.
- Configure clients to trust server certificate. See Use Digital Certificates.