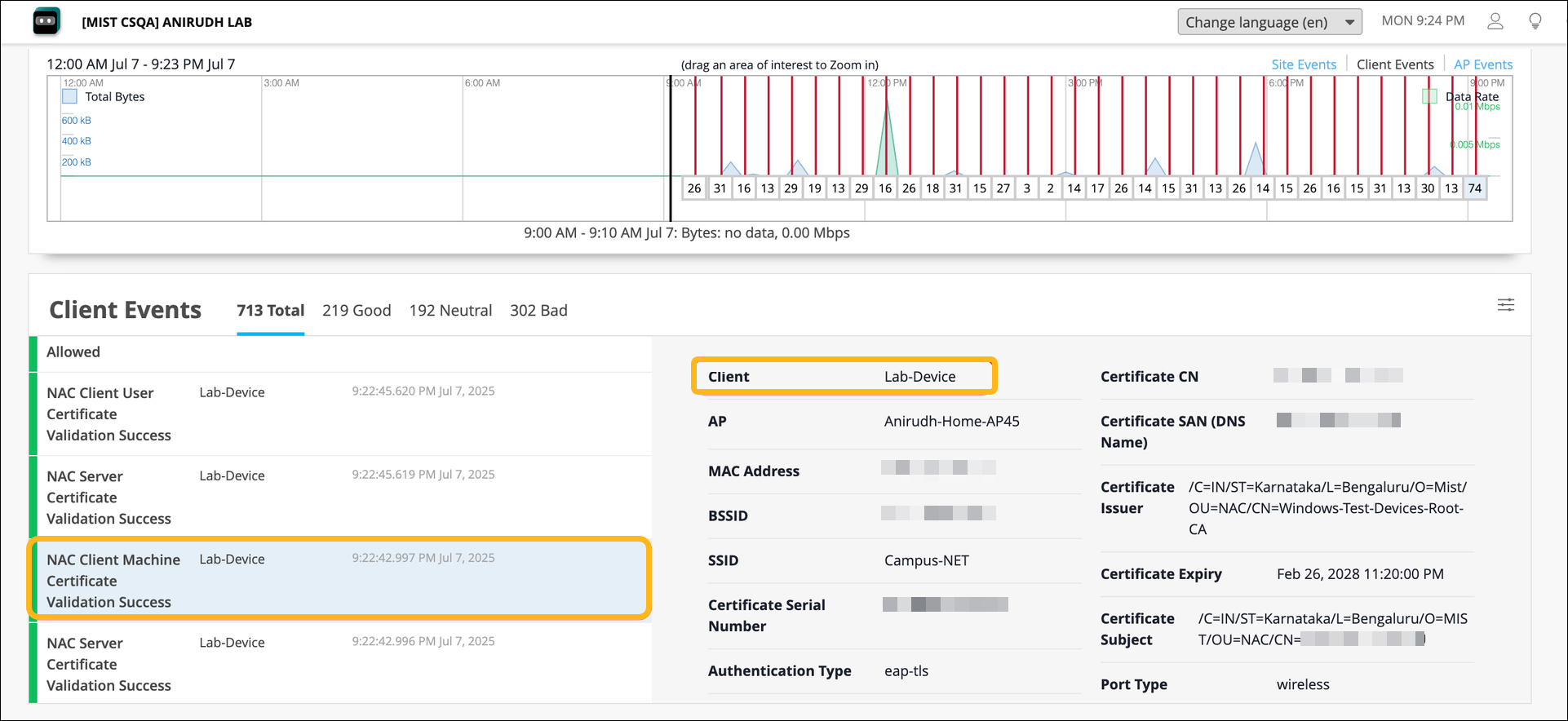
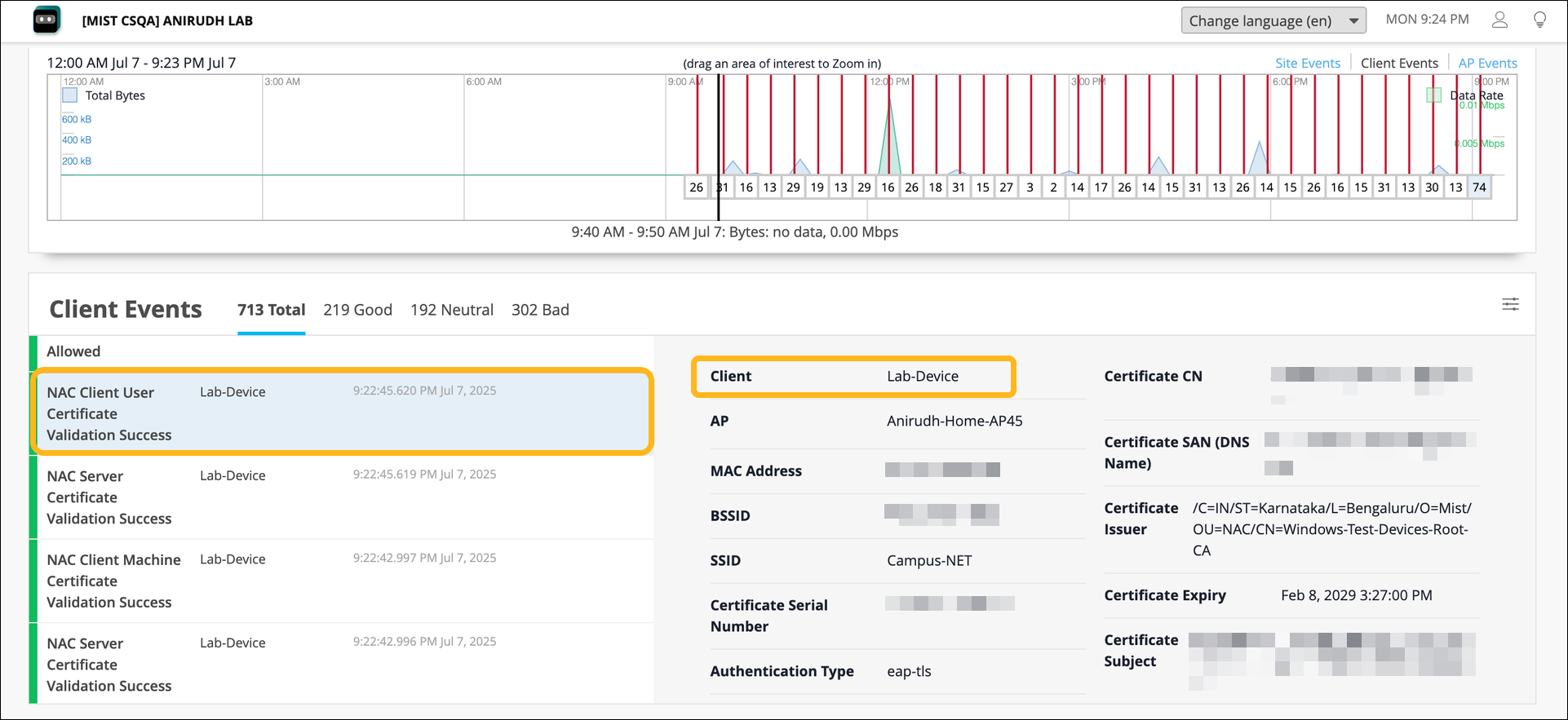
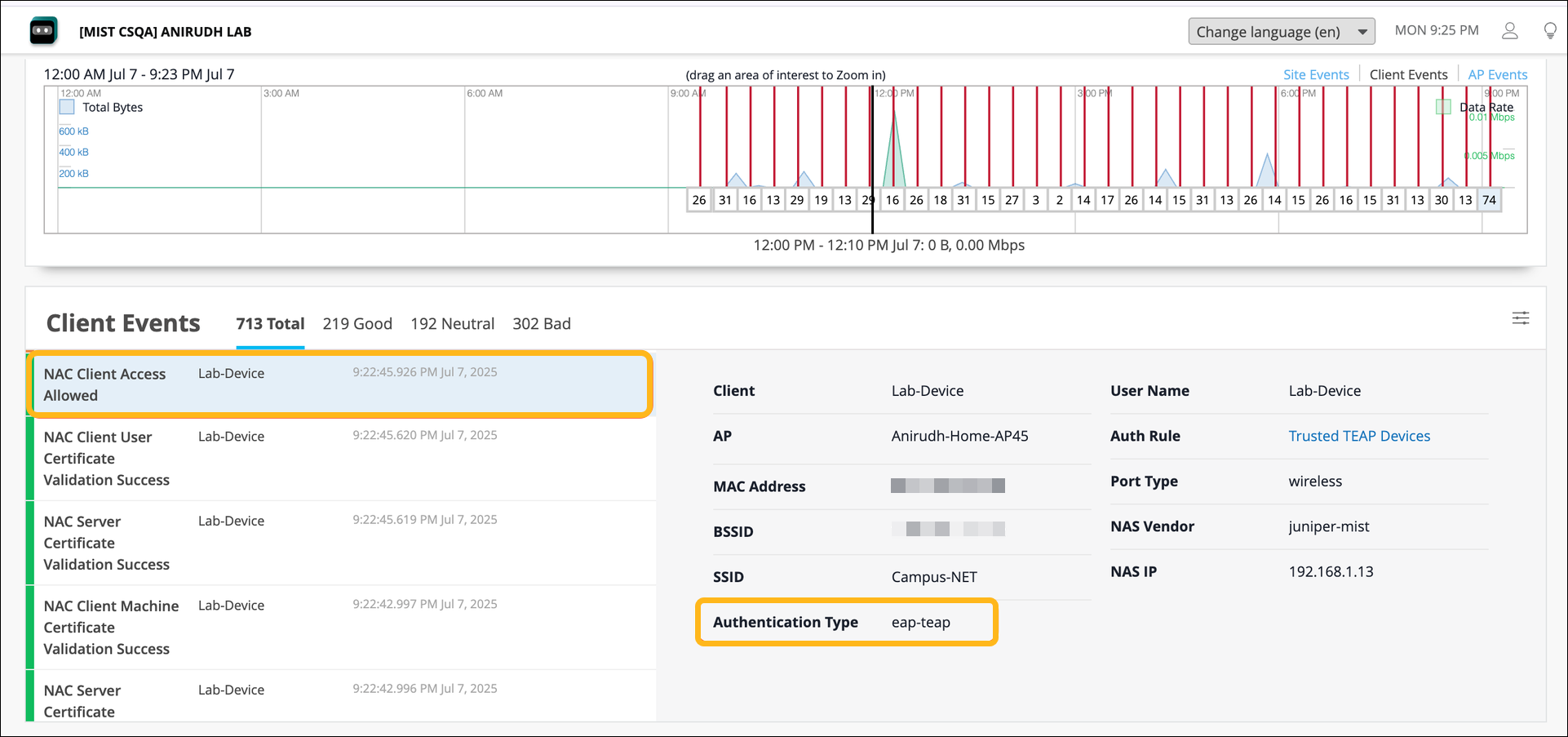
Configure EAP-TEAP Authentication for a Windows Device
To secure your network, follow these steps to configure a client device for EAP-TEAP (Tunneled Extensible Authentication Protocol) authentication.
Tunneled Extensible Authentication Protocol (TEAP) is a tunnel-based EAP method that enables secure communication between a peer and a server by using the Transport Layer Security (TLS) protocol to establish a mutually authenticated tunnel. Within the tunnel, TLV objects are used to convey authentication-related data between the EAP peer and the EAP server. (RFC 7170 - Tunnel Extensible Authentication Protocol )
Currently TEAP support is available for Windows 10 Version and above.
As of now, you can configure wireless and wired profile with TEAP manually or through scripts, which can be distributed using MDM or GPO. Current MDM solutions do not provide out-of-the box support for TEAP configuration.
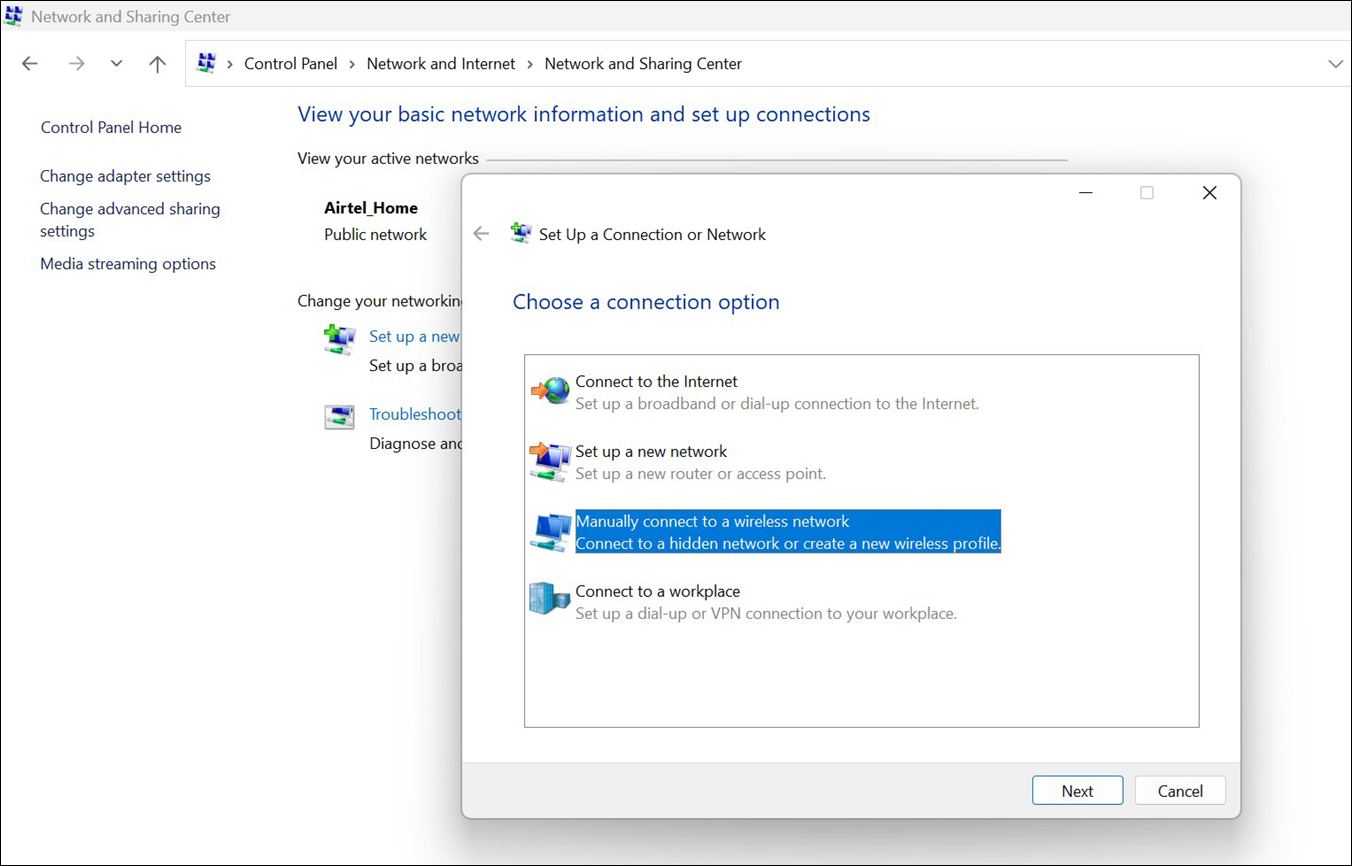
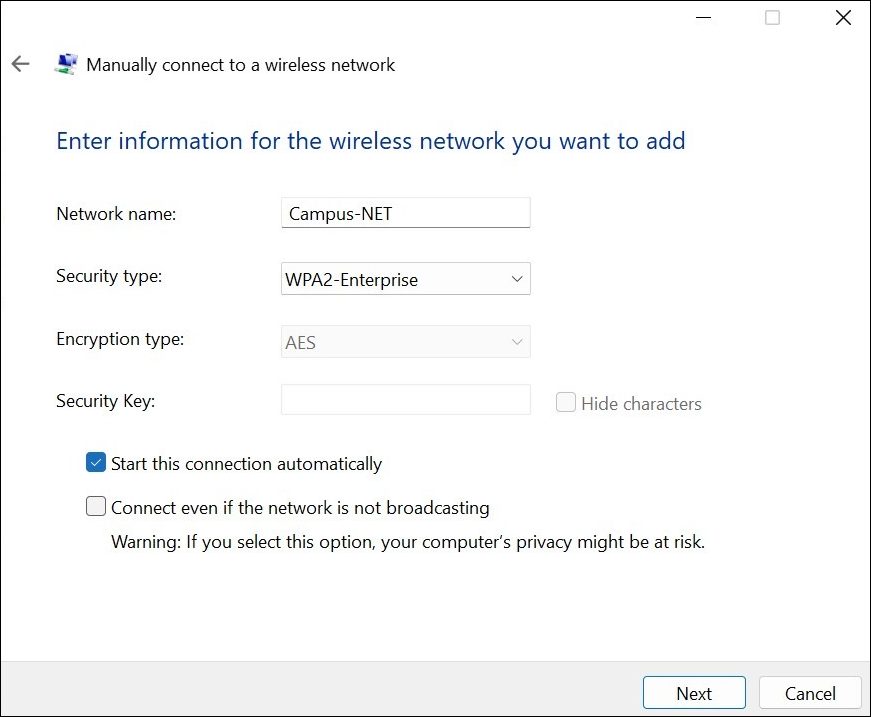
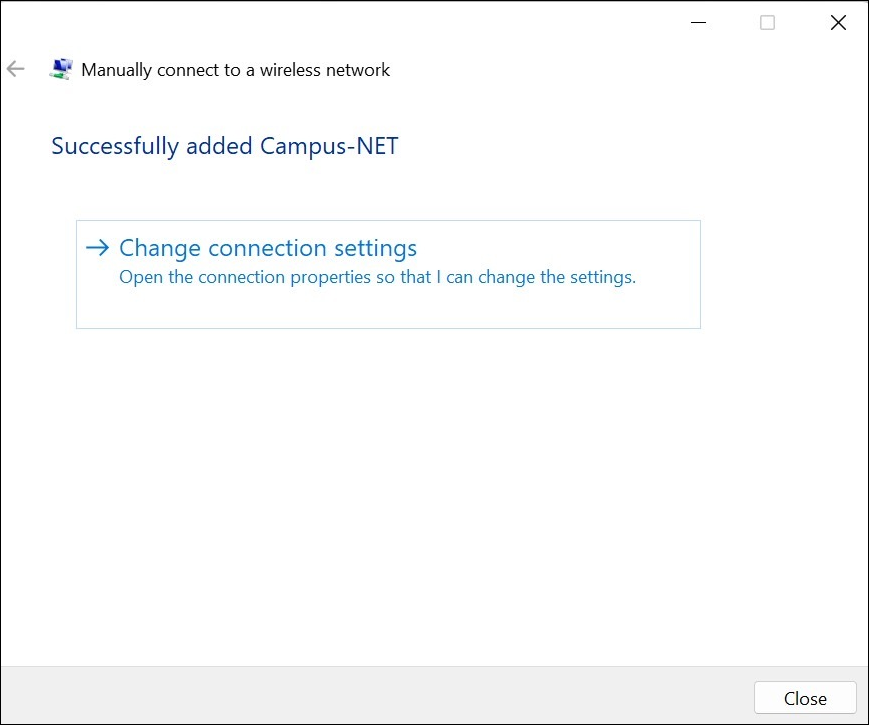
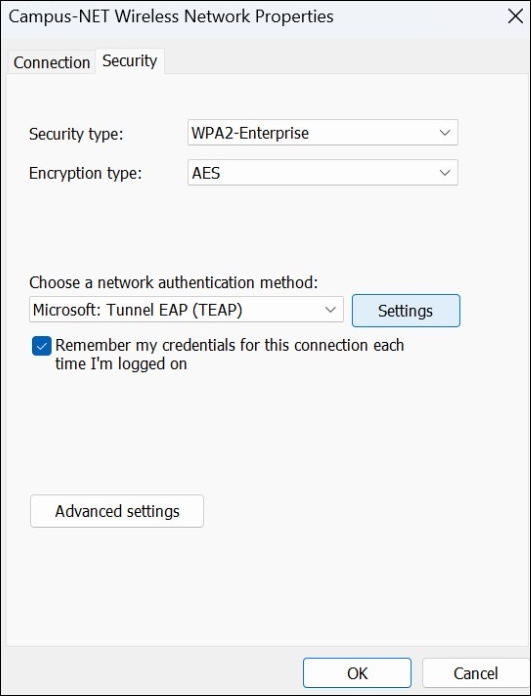
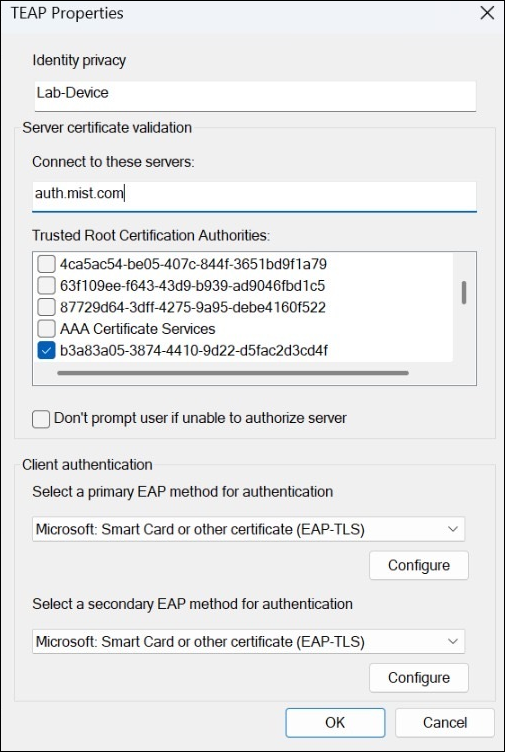
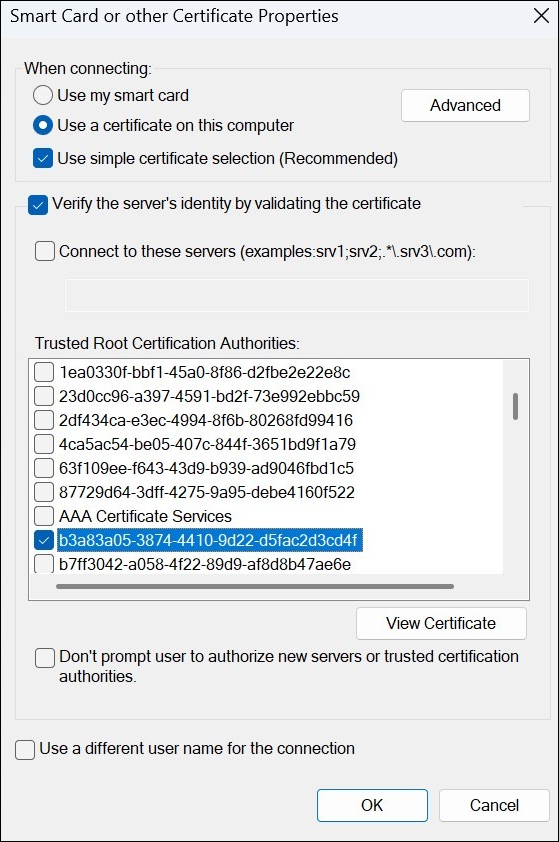
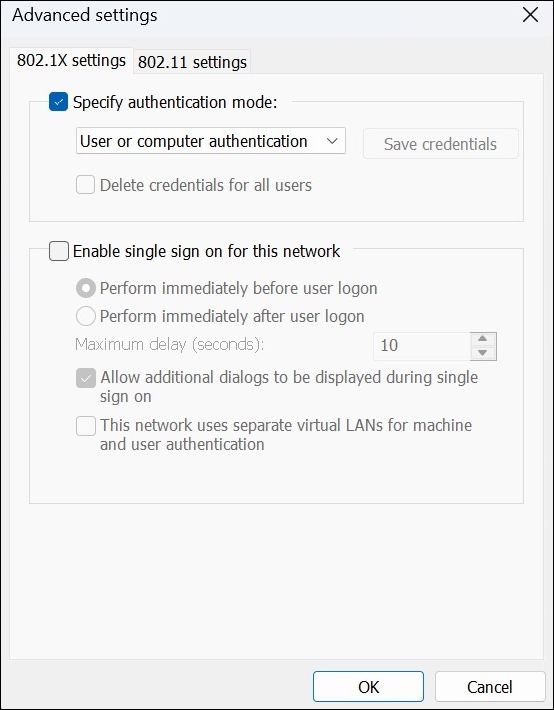
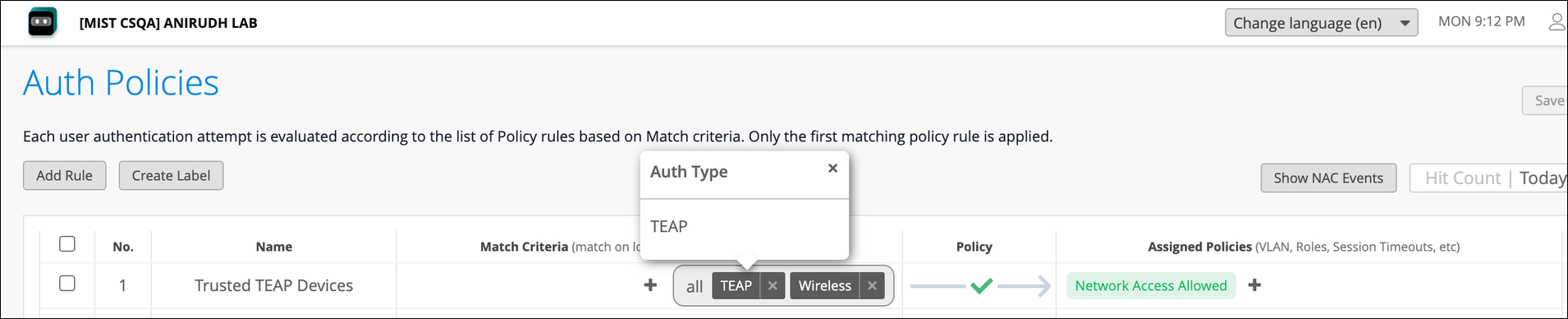
To configure EAP-TEAP on a Windows device: