Group VPNv2
Read this topic to learn about Group VPNv2 in Junos OS.
Group VPNv2 introduces the concept of a trusted group to eliminate point-to-point tunnels and their associated overlay routing. All group members share a common security association (SA), also known as a group SA.
Group VPNv2 Overview
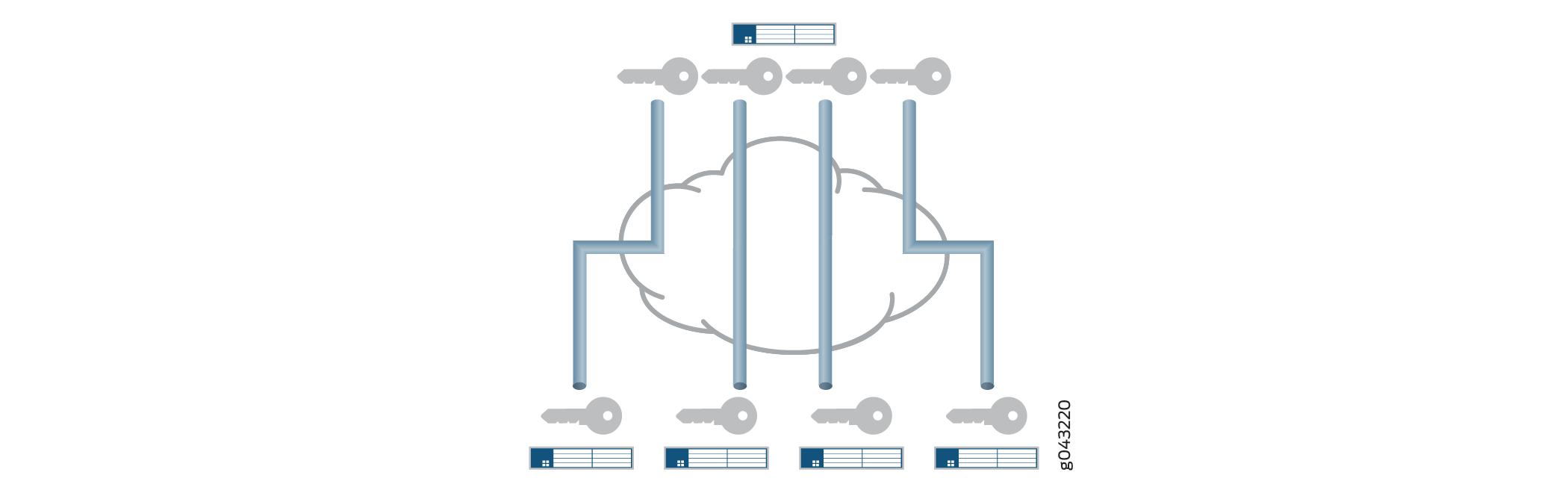
An IPsec security association (SA) is a unidirectional agreement between virtual private network (VPN) participants that defines the rules to use for authentication and encryption algorithms, key exchange mechanisms, and secure communications. With many VPN implementations, the SA is a point-to-point tunnel between two security devices (see Figure 1).
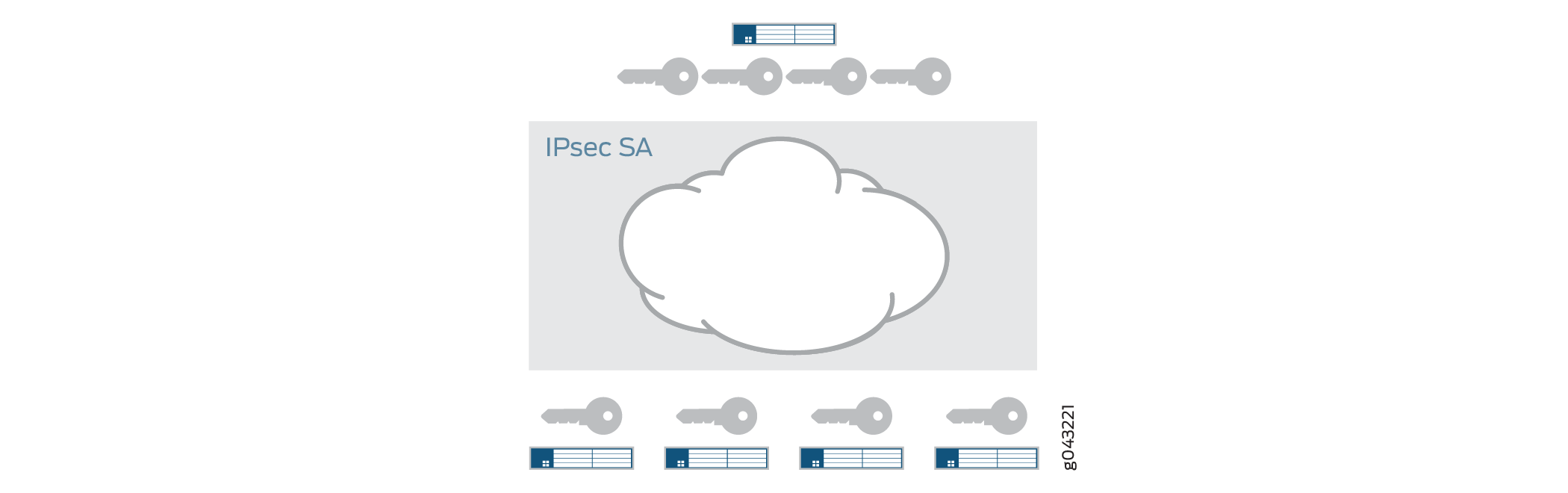
Group VPNv2 extends IPsec architecture to support SAs that are shared by a group of security devices (see Figure 2). With Group VPNv2, any-to-any connectivity is achieved by preserving the original source and destination IP addresses in the outer header.
Group VPNv2 is an enhanced version of the group VPN feature introduced in an earlier Junos OS release for SRX Series Firewalls. Group VPNv2 on Juniper devices support RFC 6407, The Group Domain of Interpretation (GDOI), and interoperate with other devices that comply with RFC 6407.
- Understanding the GDOI Protocol for Group VPNv2
- Understanding Group VPNv2 Servers and Members
- Understanding Group VPNv2 Limitations
- Understanding Group VPNv2 Server-Member Communication
- Understanding Group VPNv2 Key Operations
Understanding the GDOI Protocol for Group VPNv2
Group VPNv2 is based on RFC 6407, The Group Domain of Interpretation (GDOI). This RFC describes the protocol between group members and group servers to establish SAs among group members. GDOI messages create, maintain, or delete SAs for a group of devices.
The GDOI protocol runs on UDP port 848. The Internet Security Association and Key Management Protocol (ISAKMP) defines two negotiation phases to establish SAs for an IKE IPsec tunnel. Phase 1 allows two devices to establish an ISAKMP SA for other security protocols, such as GDOI.
With Group VPNv2, Phase 1 ISAKMP SA negotiation is performed between a group server and a group member. The server and member must use the same ISAKMP policy. GDOI exchanges between the server and member establish the SAs that are shared with other group members. A group member does not need to negotiate IPsec with other group members. GDOI exchanges must be protected by ISAKMP Phase 1 SAs.
There are two types of GDOI exchanges:
-
The
groupkey-pullexchange allows a member to request SAs and keys shared by the group from the server. Group members must register with a group server through agroupkey-pullexchange. -
The
groupkey-pushexchange is a single rekey message that allows the server to send group SAs and keys to members before existing group SAs expire. Rekey messages are unsolicited messages sent from the server to members.
Understanding Group VPNv2 Servers and Members
The center of Group VPNv2 is the group controller/key server (GCKS). A server cluster can be used to provide GCKS redundancy.
The GCKS or group server performs the following tasks:
-
Controls group membership.
-
Generates encryption keys.
-
Sends new group SAs and keys to members. Group members encrypt traffic based on the group SAs and keys provided by the group server.
A group server can service multiple groups. A single security device can be a member of multiple groups.
Each group is represented by a group identifier, which is a number between 1 and 4,294,967,295. The group server and group members are linked together by the group identifier. There can be only one group identifier per group, and multiple groups cannot use the same group identifier.
The following is a high-level view of Group VPNv2 server and member actions:
-
The group server listens on UDP port 848 for members to register.
-
To register with the group server, the member first establishes an IKE SA with the server. A member device must provide correct IKE Phase 1 authentication to join the group. Preshared key authentication on a per-member basis is supported.
-
Upon successful authentication and registration, the member device retrieves group SAs and keys for the specified group identifier from the server with a GDOI
groupkey-pullexchange. -
The server adds the member to the membership for the group.
-
Group members exchange packets encrypted with group SA keys.
The server sends SA and key refreshes to group members with
rekey (GDOI groupkey-push) messages. The server sends rekey
messages before SAs expire to ensure that valid keys are available
for encrypting traffic between group members.
A rekey message sent by the server requires an acknowledgement
(ack) message from each group member. If the server does not receive
an ack message from the member, the rekey message is retransmitted
at the configured retransmission-period (the default is
10 seconds). If there is no reply from the member after the configured number-of-retransmission (the default is 2 times), the member
is removed from the server’s registered members. The IKE SA
between the server and member is also removed.
The server also sends rekey messages to provide new keys to members when the group SA has changed.
Understanding Group VPNv2 Limitations
Group VPNv2 servers only operate with Group VPNv2 members that support RFC 6407, The Group Domain of Interpretation (GDOI).
The following are not supported in Group VPNv2:
-
SNMP.
-
Deny policy from Cisco GET VPN server.
-
PKI support for Phase 1 IKE authentication.
-
Colocation of group server and member, where server and member functions coexist in the same physical device.
-
Group members configured as chassis clusters.
-
J-Web interface for configuration and monitoring.
-
Multicast data traffic.
Group VPNv2 is not supported in deployments where IP addresses cannot be preserved—for example, across the Internet where NAT is used.
Understanding Group VPNv2 Server-Member Communication
Server-member
communication allows the server to send GDOI groupkey-push (rekey)
messages to members. If server-member communication is not configured for the group,
members can send GDOI groupkey-pull messages to register and
reregister with the server, but the server is not able to send
groupkey-push messages to members.
Server-member communication is configured for the group by using
the server-member-communication
configuration
statement at the [edit security group-vpn server] hierarchy. The following options can be defined:
-
Authentication algorithm (sha-256 or sha-384) used to authenticate the member to the server. There is no default algorithm.
-
Encryption algorithm used for communications between the server and member. You can specify aes-128-cbc, aes-192-cbc, or aes-256-cbc. There is no default algorithm.
-
Unicast communication type for rekey messages sent to group members.
-
Lifetime for the key encryption key (KEK). The default is 3600 seconds.
-
Number of times the group server retransmits
groupkey-pushmessages to a group member without a response (the default is 2 times) and the period of time between retransmissions (the default is 10 seconds).
If server-member communication for a group is not configured,
the membership list displayed by the show security group-vpn
server registered-members command shows group members who have
registered with the server; members can be active or not. When server-member
communication for a group is configured, the group membership list
is cleared. For unicast communication type, the show security
group-vpn server registered-members command shows only active
members.
Understanding Group VPNv2 Key Operations
This topic contains the following sections:
Group Keys
The group server maintains a database to track the relationship among VPN groups, group members, and group keys. There are two kinds of group keys that the server downloads to members:
-
Key Encryption Key (KEK)—Used to encrypt SA rekey (GDOI
groupkey-push) exchanges. One KEK is supported per group. -
Traffic Encryption Key (TEK)—Used to encrypt and decrypt IPsec data traffic between group members.
The key associated with an SA is accepted by a group member only if there is a matching policy configured on the member. An accepted key is installed for the group, whereas a rejected key is discarded.
Rekey Messages
If the group is configured for server-member communications,
the server sends SA and key refreshes to group members with rekey
(GDOI groupkey-push) messages. Rekey messages are sent
before SAs expire; this ensures that valid keys are available for
encrypting traffic between group members.
The server also sends rekey messages to provide new keys to members when there is a change in group membership or the group SA has changed (for example, a group policy is added or deleted).
Server-member communications options must be configured on the server to allow the server to send rekey messages to group members.
The group server sends one copy of the unicast rekey message to each group member. Upon receipt of the rekey message, members must send an acknowledgment (ACK) to the server. If the server does not receive an ACK from a member (including retransmission of rekey messages), the server considers the member to be inactive and removes it from the membership list. The server stops sending rekey messages to the member.
The number-of-retransmission and retransmission-period configuration statements for server-member communications control
the resending of rekey messages by the server when no ACK is received
from a member.
The interval at which the server sends rekey messages is based
on the value of the lifetime-seconds configuration statement
at the [edit security group-vpn server group group-name
] hierarchy. New keys are generated before the expiration of
the KEK and TEK keys.
The lifetime-seconds for the KEK is configured as
part of the server-member communications; the default is 3600 seconds.
The lifetime-seconds for the TEK is configured for the
IPsec proposal; the default is 3600 seconds.
Member Registration
If a group member does not receive a new SA key from the server
before the current key expires, the member must reregister with the
server and obtain updated keys with a GDOI groupkey-pull exchange.
Group VPNv2 Configuration Overview
This topic describes the main tasks for configuring Group VPNv2.
The group controller/key server (GCKS) manages Group VPNv2 security associations (SAs), and generates encryption keys and distributes them to group members. You can use a Group VPNv2 server cluster to provide GCKS redundancy. See Understanding Group VPNv2 Server Clusters.
On the group server(s), configure the following:
- IKE Phase 1 SA. See Understanding IKE Phase 1 Configuration for Group VPNv2 .
- IPsec SA. See Understanding IPsec SA Configuration for Group VPNv2.
- VPN group information, including the group identifier, IKE gateways for group members, the maximum number of members in the group, and server-member communications. Group configuration includes a group policy that defines the traffic to which the SA and keys apply. Server cluster and antireplay time window can optionally be configured. See Group VPNv2 Configuration Overview and Understanding Group VPNv2 Traffic Steering.
On the group member, configure the following:
IKE Phase 1 SA. See Understanding IKE Phase 1 Configuration for Group VPNv2 .
IPsec SA. See Understanding IPsec SA Configuration for Group VPNv2.
IPsec policy that defines the incoming zone (usually a protected LAN), outgoing zone (usually a WAN) and the VPN group to which the policy applies. Exclude or fail-open rules can also be specified. See Understanding Group VPNv2 Traffic Steering.
Security policy to allow group VPN traffic between the zones specified in the IPsec policy.
Group VPNv2 operation requires a working routing topology that allows client devices to reach their intended sites throughout the network.
The group is configured on the server with the group configuration statement at the [edit security group-vpn server] hierarchy.
The group information consists of the following information:
Group identifier—A value that identifies the VPN group. The same group identifier must be configured on the group member.
Each group member is configured with the
ike-gatewayconfiguration statement. There can be multiple instances of this configuration statement, one for each member of the group.Group policies—Policies that are to be downloaded to members. Group policies describe the traffic to which the SA and keys apply. See Understanding Group VPNv2 Traffic Steering.
Member threshold—The maximum number of members in the group. After the member threshold for a group is reached, a server stops responding to
groupkey-pullinitiations from new members. See Understanding Group VPNv2 Server Clusters.Server-member communication—Optional configuration that allows the server to send
groupkey-pushrekey messages to members.Server cluster—Optional configuration that supports group controller/key server (GCKS) redundancy. See Understanding Group VPNv2 Server Clusters.
Antireplay—Optional configuration that detects packet interception and replay. See Understanding Group VPNv2 Antireplay.
Understanding IKE Phase 1 Configuration for Group VPNv2
An IKE Phase 1 SA between a group server and a group member establishes a secure channel in which to negotiate IPsec SAs that are shared by a group. For standard IPsec VPNs on Juniper Networks security devices, Phase 1 SA configuration consists of specifying an IKE proposal, policy, and gateway.
For Group VPNv2, the IKE Phase 1 SA configuration is similar to the configuration for standard
IPsec VPNs, but is performed at the [edit security
group-vpn server ike] and [edit
security group-vpn member ike] hierarchies.
In the IKE proposal configuration, you set the authentication method and the authentication and encryption algorithms that will be used to open a secure channel between participants. In the IKE policy configuration, you set the mode in which the Phase 1 channel will be negotiated, specify the type of key exchange to be used, and reference the Phase 1 proposal. In the IKE gateway configuration, you reference the Phase 1 policy.
The IKE proposal and policy configuration on the group server must match the IKE proposal and policy configuration on group members. On a group server, an IKE gateway is configured for each group member. On a group member, up to four server addresses can be specified in the IKE gateway configuration.
Understanding IPsec SA Configuration for Group VPNv2
After the server and member have established a secure and authenticated channel in Phase 1 negotiation, they proceed to establish the IPsec SAs that are shared by group members to secure data that is transmitted among members. While the IPsec SA configuration for Group VPNv2 is similar to the configuration for standard VPNs, a group member does not need to negotiate the SA with other group members.
IPsec configuration for Group VPNv2 consists of the following information:
On the group server, an IPsec proposal is configured for the security protocol, authentication, and encryption algorithm to be used for the SA. The IPsec SA proposal is configured on the group server with the
proposalconfiguration statement at the [edit security group-vpn server ipsec] hierarchy.On the group member, an Autokey IKE is configured that references the group identifier, the group server (configured with the
ike-gatewayconfiguration statement), and the interface used by the member to connect to group peers. The Autokey IKE is configured on the member with thevpnconfiguration statement at the [edit security group-vpn member ipsec] hierarchy.
See Also
Understanding Group VPNv2 Traffic Steering
The group server distributes IPsec security associations (SAs) and keys to members of a specified group. All members that belong to the same group share the same set of IPsec SAs. The SA that is installed on a specific group member is determined by the policy associated with the group SA and the IPsec policy that is configured on the group member.
- Group Policies Configured on Group Servers
- IPsec Policies Configured on Group Members
- Fail-Close
- Exclude and Fail-Open Rules
- Priorities of IPsec Policies and Rules
Group Policies Configured on Group Servers
In a VPN group, each group SA and key that the server pushes
to a member are associated with a group policy. The group policy describes
the traffic on which the key should be used, including protocol, source
address, source port, destination address, and destination port. On
the server, the group policy is configured with the match-policy policy-name options at the [edit security group-vpn
server group name ipsec-sa name] hierarchy level.
Group policies that are identical (configured with the same source address, destination address, source port, destination port, and protocol values) cannot exist for a single group. An error is returned if you attempt to commit a configuration that contains identical group policies for a group. If this occurs, you must delete one of the identical group policies before you can commit the configuration.
IPsec Policies Configured on Group Members
On the group member, an IPsec policy consists of the following information:
Incoming zone (
from-zone) for group traffic.Outgoing zone (
to-zone) for group traffic.The name of the group to which the IPsec policy applies. Only one Group VPNv2 name can be referenced by a specific from-zone/to-zone pair.
The interface that is used by the group member to connect to
the Group VPNv2 must belong to the outgoing zone. This interface is
specified with the group-vpn-external-interface statement
at the [edit security group-vpn member ipsec vpn vpn-name] hierarchy level.
On the group member, the IPsec policy is configured at the [edit security ipsec-policy] hierarchy level. Traffic that matches
the IPsec policy is further checked against exclude and fail-open
rules that are configured for the group.
Fail-Close
By default, traffic that does not match exclude or fail-open rules or group policies received from the group server is blocked; this is known as fail-close.
Exclude and Fail-Open Rules
On group members, the following types of rules can be configured for each group:
Traffic that is excluded from VPN encryption. Examples of this type of traffic can include BGP or OSPF routing protocols. To exclude traffic from a group, use the
set security group-vpn member ipsec vpn vpn-name exclude ruleconfiguration. A maximum of 10 exclude rules can be configured.Traffic that is critical to the customer’s operation and must be sent in cleartext (unencrypted) if the group member has not received a valid traffic encryption key (TEK) for the IPsec SA. Fail-open rules allow this traffic flow while all other traffic is blocked. Enable fail-open with the
set security group-vpn member ipsec vpn vpn-name fail-open ruleconfiguration. A maximum of 10 fail-open rules can be configured.
Priorities of IPsec Policies and Rules
IPsec policies and rules have the following priorities on the group member:
Exclude rules that define traffic to be excluded from VPN encryption.
Group policies that are downloaded from the group server.
Fail-open rules that define traffic that is sent in cleartext if there is no valid TEK for the SA.
Fail-close policy that blocks traffic. This is the default if traffic does not match exclude or fail-open rules or group policies.
See Also
Understanding the Group VPNv2 Recovery Probe Process
Two situations could indicate that a group member is out of synchronization with the group server and other group members:
The group member receives an Encapsulating Security Payload (ESP) packet with an unrecognized Security Parameter Index (SPI).
There is outgoing IPsec traffic but no incoming IPsec traffic on the group member.
When either situation is detected, a recovery probe process
can be triggered on the group member. The recovery probe process initiates
GDOI groupkey-pull exchanges at specific intervals to update
the member’s SA from the group server. If there is a DoS attack
of bad SPI packets or if the sender itself is out of synchronization,
the out-of-synchronization indication on the group member might be
a false alarm. To avoid overloading the system, the groupkey-pull initiation is retried at intervals of 10, 20, 40, 80, 160, and 320
seconds.
The recovery probe process is disabled by default. To enable
the recovery probe process, configure recovery-probe at
the [edit security group-vpn member ipsec vpn vpn-name] hierarchy level.
Understanding Group VPNv2 Antireplay
Antireplay is an IPsec feature that can detect when a packet is intercepted and then replayed by attackers. Antireplay is disabled by default for a group.
Each IPsec packet contains a timestamp. The group member checks
whether the packet’s timestamp falls within the configured anti-replay-time-window value.
A packet is dropped if the timestamp exceeds the value.
We recommend that NTP be configured on all devices that support Group VPNv2 antireplay.
Group members that are running on vSRX Virtual Firewall instances on a host machine where the
hypervisor is running under a heavy load can experience issues that can be corrected by
reconfiguring the anti-replay-time-window value. If data that matches
the IPsec policy on the group member is not being transferred, check the show
security group-vpn member ipsec statistics output for D3P errors. Make sure
that NTP is operating correctly. If there are errors, adjust the
anti-replay-time-window value.
See Also
Example: Configuring a Group VPNv2 Server and Members
This example shows how to configure a Group VPNv2 server to provide group controller/key server (GCKS) support to Group VPNv2 group members.
Requirements
The example uses the following hardware and software components:
A supported SRX Series Firewall or vSRX Virtual Firewall instance running Junos OS Release 15.1X49-D30 or later that supports Group VPNv2. This SRX Series Firewall or vSRX Virtual Firewall instance operates as a Group VPNv2 server.
Two supported SRX Series Firewalls or vSRX Virtual Firewall instances running Junos OS Release 15.1X49-D30 or later that support Group VPNv2. These devices or instances operate as Group VPNv2 group members.
Two supported MX Series devices running Junos OS Release 15.1R2 or later that support Group VPNv2. These devices operate as Group VPNv2 group members.
A hostname, a root administrator password, and management access must be configured on each device. We recommend that NTP also be configured on each device.
Group VPNv2 operation requires a working routing topology that allows client devices to reach their intended sites throughout the network. This examples focuses on the Group VPNv2 configuration; the routing configuration is not described.
Overview
In this example, the Group VPNv2 network consists of a server and four members. Two of the members are SRX Series Firewalls or vSRX Virtual Firewall instances while the other two members are MX Series devices. The shared group VPN SAs secure traffic between group members.
The group VPN SAs must be protected by a Phase 1 SA. Therefore, the group VPN configuration must include configuring IKE Phase 1 negotiations on both the group server and the group members.
The same group identifier must be configured on both the group server and the group members. In this example, the group name is GROUP_ID-0001 and the group identifier is 1. The group policy configured on the server specifies that the SA and key are applied to traffic between subnetworks in the 172.16.0.0/12 range.
On SRX Series Firewall or vSRX Virtual Firewall group members, an IPsec policy is configured for the group with the LAN zone as the from-zone (incoming traffic) and the WAN zone as the to-zone (outgoing traffic). A security policy is also needed to allow traffic between the LAN and WAN zones.
Topology
Figure 3 shows the Juniper Networks devices to be configured for this example.
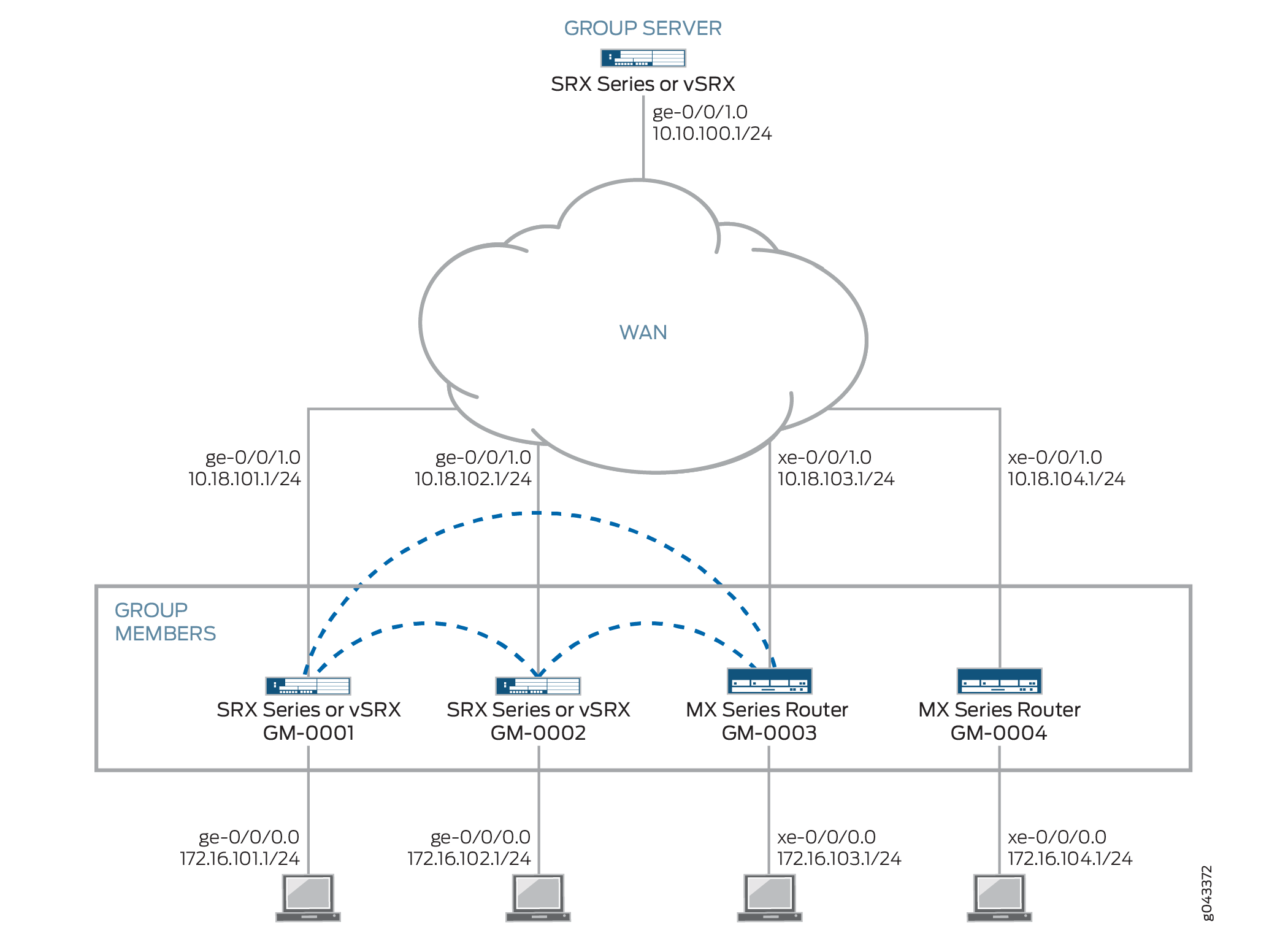
Configuration
- Configuring the Group Server
- Configuring Group Member GM-0001 (SRX Series Firewall or vSRX Virtual Firewall Instance)
- Configuring Group Member GM-0002 (SRX Series Firewall or vSRX Virtual Firewall Instance)
- Configuring Group Member GM-0003 (MX Series Device)
- Configuring Group Member GM-0004 (MX Series Device)
Configuring the Group Server
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/1 unit 0 family inet address 10.10.100.1/24 set security policies global policy 1000 match source-address any set security policies global policy 1000 match destination-address any set security policies global policy 1000 match application any set security policies global policy 1000 match from-zone any set security policies global policy 1000 match to-zone any set security policies global policy 1000 then reject set security policies global policy 1000 then log session-init set security policies global policy 1000 then count set security policies default-policy deny-all set security zones security-zone GROUPVPN host-inbound-traffic system-services ike set security zones security-zone GROUPVPN host-inbound-traffic system-services ssh set security zones security-zone GROUPVPN host-inbound-traffic system-services ping set security zones security-zone GROUPVPN interfaces ge-0/0/1.0 set routing-options static route 10.18.101.0/24 next-hop 10.10.100.254 set routing-options static route 10.18.102.0/24 next-hop 10.10.100.254 set routing-options static route 10.18.103.0/24 next-hop 10.10.100.254 set routing-options static route 10.18.104.0/24 next-hop 10.10.100.254 set security group-vpn server ike proposal PSK-SHA256-DH14-AES256 authentication-method pre-shared-keys set security group-vpn server ike proposal PSK-SHA256-DH14-AES256 authentication-algorithm sha-256 set security group-vpn server ike proposal PSK-SHA256-DH14-AES256 dh-group group14 set security group-vpn server ike proposal PSK-SHA256-DH14-AES256 encryption-algorithm aes-256-cbc set security group-vpn server ike policy GMs mode main set security group-vpn server ike policy GMs proposals PSK-SHA256-DH14-AES256 set security group-vpn server ike policy GMs pre-shared-key ascii-text "$ABC123" set security group-vpn server ike gateway GM-0001 ike-policy GMs set security group-vpn server ike gateway GM-0001 address 10.18.101.1 set security group-vpn server ike gateway GM-0001 local-address 10.10.100.1 set security group-vpn server ike gateway GM-0002 ike-policy GMs set security group-vpn server ike gateway GM-0002 address 10.18.102.1 set security group-vpn server ike gateway GM-0002 local-address 10.10.100.1 set security group-vpn server ike gateway GM-0003 ike-policy GMs set security group-vpn server ike gateway GM-0003 address 10.18.103.1 set security group-vpn server ike gateway GM-0003 local-address 10.10.100.1 set security group-vpn server ike gateway GM-0004 ike-policy GMs set security group-vpn server ike gateway GM-0004 address 10.18.104.1 set security group-vpn server ike gateway GM-0004 local-address 10.10.100.1 set security group-vpn server ipsec proposal AES256-SHA256-L3600 authentication-algorithm hmac-sha-256-128 set security group-vpn server ipsec proposal AES256-SHA256-L3600 encryption-algorithm aes-256-cbc set security group-vpn server ipsec proposal AES256-SHA256-L3600 lifetime-seconds 3600 set security group-vpn server group GROUP_ID-0001 group-id 1 set security group-vpn server group GROUP_ID-0001 member-threshold 2000 set security group-vpn server group GROUP_ID-0001 ike-gateway GM-0001 set security group-vpn server group GROUP_ID-0001 ike-gateway GM-0002 set security group-vpn server group GROUP_ID-0001 ike-gateway GM-0003 set security group-vpn server group GROUP_ID-0001 ike-gateway GM-0004 set security group-vpn server group GROUP_ID-0001 ike-gateway GM-0005 set security group-vpn server group GROUP_ID-0001 anti-replay-time-window 1000 set security group-vpn server group GROUP_ID-0001 server-member-communication communication-type unicast set security group-vpn server group GROUP_ID-0001 server-member-communication encryption-algorithm aes-256-cbc set security group-vpn server group GROUP_ID-0001 server-member-communication lifetime-seconds 7200 set security group-vpn server group GROUP_ID-0001 server-member-communication sig-hash-algorithm sha-256 set security group-vpn server group GROUP_ID-0001 ipsec-sa GROUP_ID-0001 proposal AES256-SHA256-L3600 set security group-vpn server group GROUP_ID-0001 ipsec-sa GROUP_ID-0001 match-policy 1 source 172.16.0.0/12 set security group-vpn server group GROUP_ID-0001 ipsec-sa GROUP_ID-0001 match-policy 1 destination 172.16.0.0/12 set security group-vpn server group GROUP_ID-0001 ipsec-sa GROUP_ID-0001 match-policy 1 protocol 0
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure the Group VPNv2 server:
Configure interfaces, security zones, and security policies.
[edit interfaces] user@host# set ge-0/0/1 unit 0 family inet address 10.10.100.1/24 [edit security zones security-zone GROUPVPN] user@host# set host-inbound-traffic system-services ike user@host# set host-inbound-traffic system-services ssh user@host# set host-inbound-traffic system-services ping user@host# set interfaces ge-0/0/1.0 [edit security policies] user@host# set global policy 1000 match source-address any user@host# set global policy 1000 match destination-address any user@host# set global policy 1000 match application any user@host# set global policy 1000 match from-zone any user@host# set global policy 1000 match to-zone any user@host# set global policy 1000 then reject user@host# set global policy 1000 then log session-init user@host# set global policy 1000 then count user@host# set default-policy deny-all
Configure the static routes.
[edit routing-options] user@host# set static route 10.18.101.0/24 next-hop 10.10.100.254 user@host# set static route 10.18.102.0/24 next-hop 10.10.100.254 user@host# set static route 10.18.103.0/24 next-hop 10.10.100.254 user@host# set static route 10.18.104.0/24 next-hop 10.10.100.254
Configure the IKE proposal, policy, and gateways.
[edit security group-vpn server ike proposal PSK-SHA256-DH14-AES256] user@host# set authentication-method pre-shared-keys user@host# set authentication-algorithm sha-256 user@host# set dh-group group14 user@host# set encryption-algorithm aes-256-cbc [edit security group-vpn server ike policy GMs] user@host# set mode main user@host# set proposals PSK-SHA256-DH14-AES256 user@host# set pre-shared-key ascii-text "$ABC123" [edit security group-vpn server ike gateway GM-0001] user@host# set ike-policy GMs user@host# set address 10.18.101.1 user@host# set local-address 10.10.100.1 [edit security group-vpn server ike gateway GM-0002] user@host# set ike-policy GMs user@host# set address 10.18.102.1 user@host# set local-address 10.10.100.1 [edit security group-vpn server ike gateway GM-0003] user@host# set ike-policy GMs user@host# set address 10.18.103.1 user@host# set local-address 10.10.100.1 [edit security group-vpn server ike gateway GM-0004] user@host# set ike-policy GMs user@host# set address 10.18.104.1 user@host# set local-address 10.10.100.1
Configure the IPsec proposal.
[edit security group-vpn server ipsec proposal AES256-SHA256-L3600] user@host# set authentication-algorithm hmac-sha-256-128 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 3600 VPN Group
Configure the group.
[edit security group-vpn server group GROUP_ID-0001] user@host# set group-id 1 user@host# set member-threshold 2000 user@host# set ike-gateway GM-0001 user@host# set ike-gateway GM-0002 user@host# set ike-gateway GM-0003 user@host# set ike-gateway GM-0004 user@host# set anti-replay-time-window 1000
Configure server-to-member communications.
[edit security group-vpn server group GROUP_ID-0001 server-member-communication] user@host# set communication-type unicast user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 7200 user@host# set sig-hash-algorithm sha-256
Configure the group policy to be downloaded to the group members.
[edit security group-vpn server group GROUP_ID-0001 ipsec-sa GROUP_ID-0001] user@host# set proposal AES256-SHA256-L3600 user@host# set match-policy 1 source 172.16.0.0/12 user@host# set match-policy 1 destination 172.16.0.0/12 user@host# set match-policy 1 protocol 0
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, and show security commands. If the output does not display
the intended configuration, repeat the instructions in this example
to correct the configuration.
[edit]
user@host# show interfaces
ge-0/0/1 {
unit 0 {
family inet {
address 10.10.100.1/24;
}
}
}
[edit]
user@host# show routing-options
static {
route 10.18.101.0/24 next-hop 10.10.100.254;
route 10.18.102.0/24 next-hop 10.10.100.254;
route 10.18.103.0/24 next-hop 10.10.100.254;
route 10.18.104.0/24 next-hop 10.10.100.254;
}
[edit]
user@host# show security
group-vpn {
server {
ike {
proposal PSK-SHA256-DH14-AES256 {
authentication-method pre-shared-keys;
authentication-algorithm sha-256;
dh-group group14;
encryption-algorithm aes-256-cbc;
}
policy GMs {
mode main;
proposals PSK-SHA256-DH14-AES256;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway GM-0001 {
ike-policy GMs;
address 10.18.101.1;
local-address 10.10.100.1;
}
gateway GM-0002 {
ike-policy GMs;
address 10.18.102.1;
local-address 10.10.100.1;
}
gateway GM-0003 {
ike-policy GMs;
address 10.18.103.1;
local-address 10.10.100.1;
}
gateway GM-0004 {
ike-policy GMs;
address 10.18.104.1;
local-address 10.10.100.1;
}
}
ipsec {
proposal AES256-SHA256-L3600 {
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
}
group GROUP_ID-0001 {
group-id 1;
member-threshold 2000;
ike-gateway GM-0001;
ike-gateway GM-0002;
ike-gateway GM-0003;
ike-gateway GM-0004;
anti-replay-time-window 1000;
server-member-communication {
communication-type unicast;
lifetime-seconds 7200;
encryption-algorithm aes-256-cbc;
sig-hash-algorithm sha-256;
}
ipsec-sa GROUP_ID-0001 {
proposal AES256-SHA256-L3600;
match-policy 1 {
source 172.16.0.0/12;
destination 172.16.0.0/12;
protocol 0;
}
}
}
}
}
policies {
global {
policy 1000 {
match {
source-address any;
destination-address any;
application any;
from-zone any;
to-zone any;
}
then {
reject;
log {
session-init;
}
count;
}
}
}
default-policy {
deny-all;
}
}
zones {
security-zone GROUPVPN {
host-inbound-traffic {
system-services {
ike;
ssh;
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Configuring Group Member GM-0001 (SRX Series Firewall or vSRX Virtual Firewall Instance)
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/0 unit 0 description To_LAN set interfaces ge-0/0/0 unit 0 family inet address 172.16.101.1/24 set interfaces ge-0/0/1 unit 0 description To_KeySrv set interfaces ge-0/0/1 unit 0 family inet address 10.18.101.1/24 set security zones security-zone LAN host-inbound-traffic system-services ike set security zones security-zone LAN host-inbound-traffic system-services ssh set security zones security-zone LAN host-inbound-traffic system-services ping set security zones security-zone LAN interfaces ge-0/0/0.0 set security zones security-zone WAN host-inbound-traffic system-services ike set security zones security-zone WAN host-inbound-traffic system-services ssh set security zones security-zone WAN host-inbound-traffic system-services ping set security zones security-zone WAN interfaces ge-0/0/1.0 set security address-book global address 172.16.0.0/12 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match source-address 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match destination-address 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match application any set security policies from-zone LAN to-zone WAN policy 1 then permit set security policies from-zone LAN to-zone WAN policy 1 then log session-init set security policies from-zone WAN to-zone LAN policy 1 match source-address 172.16.0.0/12 set security policies from-zone WAN to-zone LAN policy 1 match destination-address 172.16.0.0/12 set security policies from-zone WAN to-zone LAN policy 1 match application any set security policies from-zone WAN to-zone LAN policy 1 then permit set security policies from-zone WAN to-zone LAN policy 1 then log session-init set security policies global policy 1000 match source-address any set security policies global policy 1000 match destination-address any set security policies global policy 1000 match application any set security policies global policy 1000 match from-zone any set security policies global policy 1000 match to-zone any set security policies global policy 1000 then reject set security policies global policy 1000 then log session-init set security policies global policy 1000 then count set security policies default-policy deny-all set routing-options static route 10.18.102.0/24 next-hop 10.18.101.254 set routing-options static route 10.18.103.0/24 next-hop 10.18.101.254 set routing-options static route 10.18.104.0/24 next-hop 10.18.101.254 set routing-options static route 172.16.101.0/24 next-hop 10.18.101.254 set routing-options static route 172.16.102.0/24 next-hop 10.18.101.254 set routing-options static route 172.16.103.0/24 next-hop 10.18.101.254 set routing-options static route 172.16.104.0/24 next-hop 10.18.101.254 set routing-options static route 10.10.100.0/24 next-hop 10.18.101.254 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-method pre-shared-keys set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 dh-group group14 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-algorithm sha-256 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 encryption-algorithm aes-256-cbc set security group-vpn member ike policy KeySrv mode main set security group-vpn member ike policy KeySrv proposals PSK-SHA256-DH14-AES256 set security group-vpn member ike policy KeySrv pre-shared-key ascii-text "$ABC123" set security group-vpn member ike gateway KeySrv ike-policy KeySrv set security group-vpn member ike gateway KeySrv server-address 10.10.100.1 set security group-vpn member ike gateway KeySrv local-address 10.18.101.1 set security group-vpn member ipsec vpn GROUP_ID-0001 ike-gateway KeySrv set security group-vpn member ipsec vpn GROUP_ID-0001 group-vpn-external-interface ge-0/0/1.0 set security group-vpn member ipsec vpn GROUP_ID-0001 group 1 set security group-vpn member ipsec vpn GROUP_ID-0001 recovery-probe set security ipsec-policy from-zone LAN to-zone WAN ipsec-group-vpn GROUP_ID-0001
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure the Group VPNv2 member:
Configure interfaces, security zones, and security policies.
[edit interfaces] user@host# set ge-0/0/0 unit 0 description To_LAN user@host# set ge-0/0/0 unit 0 family inet address 172.16.101.1/24 user@host# set ge-0/0/1 unit 0 description To_KeySrv user@host# set ge-0/0/1 unit 0 family inet address 10.18.101.1/24 [edit security zones security-zone LAN] user@host# set host-inbound-traffic system-services ike user@host# set host-inbound-traffic system-services ssh user@host# set host-inbound-traffic system-services ping user@host# set interfaces ge-0/0/0.0 [edit security] user@host# set address-book global address 172.16.0.0/12 172.16.0.0/12 [edit security zones security-zone WAN] user@host# set host-inbound-traffic system-services ike user@host# set host-inbound-traffic system-services ssh user@host# set host-inbound-traffic system-services ping user@host# set interfaces ge-0/0/1.0 [edit security policies from-zone LAN to-zone WAN] user@host# set policy 1 match source-address 172.16.0.0/12 user@host# set policy 1 match destination-address 172.16.0.0/12 user@host# set policy 1 match application any user@host# set policy 1 then permit user@host# set then log session-init [edit security policies from-zone WAN to-zone LAN user@host# set policy 1 match source-address 172.16.0.0/12 user@host# set policy 1 match destination-address 172.16.0.0/12 user@host# set policy 1 match application any user@host# set policy 1 then permit user@host# set then log session-init [edit security policies] user@host# set global policy 1000 match source-address any user@host# set global policy 1000 match destination-address any user@host# set global policy 1000 match application any user@host# set global policy 1000 match from-zone any user@host# set global policy 1000 match to-zone any user@host# set global policy 1000 match then reject user@host# set global policy 1000 match then log session-init user@host# set global policy 1000 match then count user@host# set default-policy deny-all
Configure the static routes.
[edit routing-options] user@host# set static route 10.18.102.0/24 next-hop 10.18.101.254 user@host# set static route 10.18.103.0/24 next-hop 10.18.101.254 user@host# set static route 10.18.104.0/24 next-hop 10.18.101.254 user@host# set static route 172.16.101.0/24 next-hop 10.18.101.254 user@host# set static route 172.16.102.0/24 next-hop 10.18.101.254 user@host# set static route 172.16.103.0/24 next-hop 10.18.101.254 user@host# set static route 172.16.104.0/24 next-hop 10.18.101.254 user@host# set static route 10.10.100.0/24 next-hop 10.18.101.254
Configure the IKE proposal, policy, and gateway.
[edit security group-vpn member ike proposal PSK-SHA256-DH14-AES256] user@host# set authentication-method pre-shared-keys user@host# set authentication-algorithm sha-256 user@host# set dh-group group14 user@host# set encryption-algorithm aes-256-cbc [edit security group-vpn member ike policy KeySrv ] user@host# set mode main user@host# set proposals PSK-SHA256-DH14-AES256 user@host# set pre-shared-key ascii-text "$ABC123" [edit security group-vpn member ike gateway KeySrv] user@host# set ike-policy KeySrv user@host# set server-address 10.10.100.1 user@host# set local-address 10.18.101.1
Configure the IPsec SA.
[edit security group-vpn member ipsec vpn GROUP_ID-0001] user@host# set ike-gateway KeySrv user@host# set group-vpn-external-interface ge-0/0/1.0 user@host# set group 1 user@host# set recovery-probe
Configure the IPsec policy.
[edit security ipsec-policy from-zone LAN to-zone WAN] user@host# set ipsec-group-vpn GROUP_ID-0001
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, and show security commands. If the output does not display
the intended configuration, repeat the instructions in this example
to correct the configuration.
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
description To_LAN;
family inet {
address 172.16.101.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description To_KeySrv;
family inet {
address 10.18.101.1/24;
}
}
}
[edit]
user@host# show routing-options
static {
route 10.18.102.0/24 next-hop 10.18.101.254;
route 10.18.103.0/24 next-hop 10.18.101.254;
route 10.18.104.0/24 next-hop 10.18.101.254;
route 172.16.101.0/24 next-hop 10.18.101.254;
route 172.16.102.0/24 next-hop 10.18.101.254;
route 172.16.103.0/24 next-hop 10.18.101.254;
route 172.16.104.0/24 next-hop 10.18.101.254;
route 10.10.100.0/24 next-hop 10.18.101.254;
}
[edit]
user@host# show security
address-book {
global {
address 172.16.0.0/12 172.16.0.0/12;
}
}
group-vpn {
member {
ike {
proposal PSK-SHA256-DH14-AES256 {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
}
policy KeySrv {
mode main;
proposals PSK-SHA256-DH14-AES256;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway KeySrv {
ike-policy KeySrv;
server-address 10.10.100.1;
local-address 10.18.101.1;
}
}
ipsec {
vpn GROUP_ID-0001 {
ike-gateway KeySrv;
group-vpn-external-interface ge-0/0/1.0;
group 1;
recovery-probe;
}
}
}
}
ipsec-policy {
from-zone LAN to-zone WAN {
ipsec-group-vpn GROUP_ID-0001;
}
}
policies {
from-zone LAN to-zone WAN {
policy 1 {
match {
source-address 172.16.0.0/12;
destination-address 172.16.0.0/12;
application any;
}
then {
permit;
log {
session-init;
}
}
}
}
from-zone WAN to-zone LAN {
policy 1 {
match {
source-address 172.16.0.0/12;
destination-address 172.16.0.0/12;
application any;
}
then {
permit;
log {
session-init;
}
}
}
}
global {
policy 1000 {
match {
source-address any;
destination-address any;
application any;
from-zone any;
to-zone any;
}
then {
reject;
log {
session-init;
}
count;
}
}
}
default-policy {
deny-all;
}
}
zones {
security-zone LAN {
host-inbound-traffic {
system-services {
ike;
ssh;
ping;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone WAN {
host-inbound-traffic {
system-services {
ike;
ssh;
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Configuring Group Member GM-0002 (SRX Series Firewall or vSRX Virtual Firewall Instance)
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/0 unit 0 description To_LAN set interfaces ge-0/0/0 unit 0 family inet address 172.16.102.1/24 set interfaces ge-0/0/1 unit 0 description To_KeySrv set interfaces ge-0/0/1 unit 0 family inet address 10.18.102.1/24 set security zones security-zone LAN host-inbound-traffic system-services ike set security zones security-zone LAN host-inbound-traffic system-services ssh set security zones security-zone LAN host-inbound-traffic system-services ping set security zones security-zone LAN interfaces ge-0/0/0.0 set security zones security-zone WAN host-inbound-traffic system-services ike set security zones security-zone WAN host-inbound-traffic system-services ssh set security zones security-zone WAN host-inbound-traffic system-services ping set security zones security-zone WAN interfaces ge-0/0/1.0 set security address-book global address 172.16.0.0/12 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match source-address 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match destination-address 172.16.0.0/12 set security policies from-zone LAN to-zone WAN policy 1 match application any set security policies from-zone LAN to-zone WAN policy 1 then permit set security policies from-zone LAN to-zone WAN policy 1 then log session-init set security policies from-zone WAN to-zone LAN policy 1 match source-address 172.16.0.0/12 set security policies from-zone WAN to-zone LAN policy 1 match destination-address 172.16.0.0/12 set security policies from-zone WAN to-zone LAN policy 1 match application any set security policies from-zone WAN to-zone LAN policy 1 then permit set security policies from-zone WAN to-zone LAN policy 1 then log session-init set security policies global policy 1000 match source-address any set security policies global policy 1000 match destination-address any set security policies global policy 1000 match application any set security policies global policy 1000 match from-zone any set security policies global policy 1000 match to-zone any set security policies global policy 1000 then reject set security policies global policy 1000 then log session-init set security policies global policy 1000 then count set security policies default-policy deny-all set routing-options static route 10.18.101.0/24 next-hop 10.18.102.254 set routing-options static route 10.18.103.0/24 next-hop 10.18.102.254 set routing-options static route 10.18.104.0/24 next-hop 10.18.102.254 set routing-options static route 172.16.101.0/24 next-hop 10.18.102.254 set routing-options static route 172.16.102.0/24 next-hop 10.18.102.254 set routing-options static route 172.16.103.0/24 next-hop 10.18.102.254 set routing-options static route 172.16.104.0/24 next-hop 10.18.102.254 set routing-options static route 10.10.100.0/24 next-hop 10.18.102.254 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-method pre-shared-keys set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 dh-group group14 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-algorithm sha-256 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 encryption-algorithm aes-256-cbc set security group-vpn member ike policy KeySrv mode main set security group-vpn member ike policy KeySrv proposals PSK-SHA256-DH14-AES256 set security group-vpn member ike policy KeySrv pre-shared-key ascii-text "$ABC123" set security group-vpn member ike gateway KeySrv ike-policy KeySrv set security group-vpn member ike gateway KeySrv server-address 10.10.100.1 set security group-vpn member ike gateway KeySrv local-address 10.18.102.1 set security group-vpn member ipsec vpn GROUP_ID-0001 ike-gateway KeySrv set security group-vpn member ipsec vpn GROUP_ID-0001 group-vpn-external-interface ge-0/0/1.0 set security group-vpn member ipsec vpn GROUP_ID-0001 group 1 set security group-vpn member ipsec vpn GROUP_ID-0001 recovery-probe set security ipsec-policy from-zone LAN to-zone WAN ipsec-group-vpn GROUP_ID-0001
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure the Group VPNv2 member:
Configure interfaces, security zones, and security policies.
[edit interfaces] user@host# set ge-0/0/0 unit 0 description To_LAN user@host# set ge-0/0/0 unit 0 family inet address 172.16.102.1/24 user@host# set ge-0/0/1 unit 0 description To_KeySrv user@host# set ge-0/0/1 unit 0 family inet address 10.18.101.1/24 [edit security zones security-zone LAN] user@host# set host-inbound-traffic system-services ike user@host# set host-inbound-traffic system-services ssh user@host# set host-inbound-traffic system-services ping user@host# set interfaces ge-0/0/0.0 [edit security zones security-zone WAN] user@host# set host-inbound-traffic system-services ike user@host# set host-inbound-traffic system-services ssh user@host# set host-inbound-traffic system-services ping user@host# set interfaces ge-0/0/1.0 [edit security] user@host# set address-book global address 172.16.0.0/12 172.16.0.0/12 [edit security policies from-zone LAN to-zone WAN] user@host# set policy 1 match source-address 172.16.0.0/12 user@host# set policy 1 match destination-address 172.16.0.0/12 user@host# set policy 1 match application any user@host# set policy 1 then permit user@host# set then log session-init [edit security policies from-zone WAN to-zone LAN user@host# set policy 1 match source-address 172.16.0.0/12 user@host# set policy 1 match destination-address 172.16.0.0/12 user@host# set policy 1 match application any user@host# set policy 1 then permit user@host# set then log session-init [edit security policies] user@host# set global policy 1000 match source-address any user@host# set global policy 1000 match destination-address any user@host# set global policy 1000 match application any user@host# set global policy 1000 match from-zone any user@host# set global policy 1000 match to-zone any user@host# set global policy 1000 match then reject user@host# set global policy 1000 match then log session-init user@host# set global policy 1000 match then count user@host# set default-policy deny-all
Configure the static routes.
[edit routing-options] user@host# set static route 10.18.101.0/24 next-hop 10.18.102.254 user@host# set static route 10.18.103.0/24 next-hop 10.18.102.254 user@host# set static route 10.18.104.0/24 next-hop 10.18.102.254 user@host# set static route 172.16.101.0/24 next-hop 10.18.102.254 user@host# set static route 172.16.102.0/24 next-hop 10.18.102.254 user@host# set static route 172.16.103.0/24 next-hop 10.18.102.254 user@host# set static route 172.16.104.0/24 next-hop 10.18.102.254 user@host# set static route 10.10.100.0/24 next-hop 10.18.102.254
Configure the IKE proposal, policy, and gateway.
[edit security group-vpn member ike proposal PSK-SHA256-DH14-AES256] user@host# set authentication-method pre-shared-keys user@host# set authentication-algorithm sha-256 user@host# set dh-group group14 user@host# set encryption-algorithm aes-256-cbc [edit security group-vpn member ike policy KeySrv ] user@host# set mode main user@host# set proposals PSK-SHA256-DH14-AES256 user@host# set pre-shared-key ascii-text "$ABC123" [edit security group-vpn member ike gateway KeySrv] user@host# set ike-policy KeySrv user@host# set server-address 10.10.100.1 user@host# set local-address 10.18.102.1
Configure the IPsec SA.
[edit security group-vpn member ipsec vpn GROUP_ID-0001] user@host# set ike-gateway KeySrv user@host# set group-vpn-external-interface ge-0/0/1.0 user@host# set group 1 user@host# set recovery-probe
Configure the IPsec policy.
[edit security ipsec-policy from-zone LAN to-zone WAN] user@host# set ipsec-group-vpn GROUP_ID-0001
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, and show security commands. If the output does not display
the intended configuration, repeat the instructions in this example
to correct the configuration.
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
description To_LAN;
family inet {
address 172.16.102.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description To_KeySrv;
family inet {
address 10.18.102.1/24;
}
}
}
[edit]
user@host# show routing-options
static {
route 10.18.101.0/24 next-hop 10.18.102.254;
route 10.18.103.0/24 next-hop 10.18.102.254;
route 10.18.104.0/24 next-hop 10.18.102.254;
route 172.16.101.0/24 next-hop 10.18.102.254;
route 172.16.102.0/24 next-hop 10.18.102.254;
route 172.16.103.0/24 next-hop 10.18.102.254;
route 172.16.104.0/24 next-hop 10.18.102.254;
route 10.10.100.0/24 next-hop 10.18.102.254;
}
[edit]
user@host# show security
address-book {
global {
address 172.16.0.0/12 172.16.0.0/12;
}
}
group-vpn {
member {
ike {
proposal PSK-SHA256-DH14-AES256 {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
}
policy KeySrv {
mode main;
proposals PSK-SHA256-DH14-AES256;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway KeySrv {
ike-policy KeySrv;
server-address 10.10.100.1;
local-address 10.18.102.1;
}
}
ipsec {
vpn GROUP_ID-0001 {
ike-gateway KeySrv;
group-vpn-external-interface ge-0/0/1.0;
group 1;
recovery-probe;
}
}
}
}
policies {
from-zone LAN to-zone WAN {
policy 1 {
match {
source-address 172.16.0.0/12;
destination-address 172.16.0.0/12;
application any;
}
then {
permit;
log {
session-init;
}
}
}
}
from-zone WAN to-zone LAN {
policy 1 {
match {
source-address 172.16.0.0/12;
destination-address 172.16.0.0/12;
application any;
}
then {
permit;
log {
session-init;
}
}
}
}
global {
policy 1000 {
match {
source-address any;
destination-address any;
application any;
from-zone any;
to-zone any;
}
then {
reject;
log {
session-init;
}
count;
}
}
}
default-policy {
deny-all;
}
}
zones {
security-zone LAN {
host-inbound-traffic {
system-services {
ike;
ssh;
ping;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone WAN {
host-inbound-traffic {
system-services {
ike;
ssh;
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Configuring Group Member GM-0003 (MX Series Device)
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces xe-0/0/1 unit 0 family inet service input service-set GROUP_ID-0001 service-filter GroupVPN-KS set interfaces xe-0/0/1 unit 0 family inet service output service-set GROUP_ID-0001 service-filter GroupVPN-KS set interfaces xe-0/0/1 unit 0 family inet address 10.18.103.1/24 set interfaces xe-0/0/2 unit 0 family inet address 172.16.103.1/24 set interfaces ms-0/2/0 unit 0 family inet set routing-options static route 10.18.101.0/24 next-hop 10.18.103.254 set routing-options static route 10.18.102.0/24 next-hop 10.18.103.254 set routing-options static route 10.18.104.0/24 next-hop 10.18.103.254 set routing-options static route 172.16.101.0/24 next-hop 10.18.103.254 set routing-options static route 172.16.102.0/24 next-hop 10.18.103.254 set routing-options static route 172.16.103.0/24 next-hop 10.18.103.254 set routing-options static route 172.16.104.0/24 next-hop 10.18.103.254 set routing-options static route 10.10.100.0/24 next-hop 10.18.103.254 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-method pre-shared-keys set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 dh-group group14 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-algorithm sha-256 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 encryption-algorithm aes-256-cbc set security group-vpn member ike policy KeySrv mode main set security group-vpn member ike policy KeySrv proposals PSK-SHA256-DH14-AES256 set security group-vpn member ike policy KeySrv pre-shared-key ascii-text "$ABC123" set security group-vpn member ike gateway KeySrv ike-policy KeySrv set security group-vpn member ike gateway KeySrv server-address 10.10.100.1 set security group-vpn member ike gateway KeySrv local-address 10.18.103.1 set security group-vpn member ipsec vpn GROUP_ID-0001 ike-gateway KeySrv set security group-vpn member ipsec vpn GROUP_ID-0001 group 1 set security group-vpn member ipsec vpn GROUP_ID-0001 match-direction output set security group-vpn member ipsec vpn GROUP_ID-0001 tunnel-mtu 1400 set security group-vpn member ipsec vpn GROUP_ID-0001 df-bit clear set services service-set GROUP_ID-0001 interface-service service-interface ms-0/2/0.0 set services service-set GROUP_ID-0001 ipsec-group-vpn GROUP_ID-0001 set firewall family inet service-filter GroupVPN-KS term inbound-ks from destination-address 10.10.100.1/32 set firewall family inet service-filter GroupVPN-KS term inbound-ks from source-address 10.10.100.1/32 set firewall family inet service-filter GroupVPN-KS term inbound-ks then skip set firewall family inet service-filter GroupVPN-KS term outbound-ks from destination-address 10.10.100.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks then skip set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 from source-address 172.16.0.0/12 set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 from destination-address 172.16.0.0/12 set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 then service
Step-by-Step Procedure
To configure the Group VPNv2 member:
Configure the interfaces.
[edit interfaces] user@host# set xe-0/0/1 unit 0 family inet service input service-set GROUP_ID-0001 service-filter GroupVPN-KS user@host# set xe-0/0/1 unit 0 family inet service output service-set GROUP_ID-0001 service-filter GroupVPN-KS user@host# set xe-0/0/1 unit 0 family inet address 10.18.103.1/24 user@host# set xe-0/0/2 unit 0 family inet address 172.16.103.1/24 user@host# set ms-0/2/0 unit 0 family inet
Configure routing.
[edit routing-options] user@host# set static route 10.18.101.0/24 next-hop 10.18.103.254 user@host# set static route 10.18.102.0/24 next-hop 10.18.103.254 user@host# set static route 10.18.104.0/24 next-hop 10.18.103.254 user@host# set static route 172.16.101.0/24 next-hop 10.18.103.254 user@host# set static route 172.16.102.0/24 next-hop 10.18.103.254 user@host# set static route 172.16.103.0/24 next-hop 10.18.103.254 user@host# set static route 172.16.104.0/24 next-hop 10.18.103.254 user@host# set static route 10.10.100.0/24 next-hop 10.18.103.254
Configure IKE proposal, policy, and gateway.
[edit security group-vpn member ike proposal PSK-SHA256-DH14-AES256 ] user@host# set authentication-method pre-shared-keys user@host# set group group14 user@host# set authentication-algorithm sha-256 user@host# set encryption-algorithm aes-256-cbc [edit security group-vpn member ike policy KeySrv ] user@host# set mode main user@host# set proposals PSK-SHA256-DH14-AES256 user@host# set pre-shared-key ascii-text "$ABC123" [edit security group-vpn member ike gateway KeySrv] user@host# set ike-policy KeySrv user@host# set server-address 10.10.100.1 user@host# set local-address 10.18.103.1
Configure the IPsec SA.
[edit security group-vpn member ipsec vpn GROUP_ID-0001] user@host# set ike-gateway KeySrv user@host# set group 1 user@host# set match-direction output user@host# set tunnel-mtu 1400 user@host# set df-bit clear
Configure the service filter.
[edit firewall family inet service-filter GroupVPN-KS] user@host# set term inbound-ks from destination-address 10.10.100.1/32 user@host# set term inbound-ks from source-address 10.10.100.1/32 user@host# set term inbound-ks then skip user@host# set term outbound-ks from destination-address 10.10.100.1/32 user@host# set term outbound-ks then skip user@host# set term GROUP_ID-0001 from source-address 172.16.0.0/12 user@host# set term GROUP_ID-0001 from destination-address 172.16.0.0/12 user@host# set term GROUP_ID-0001 then service
Configure the service set.
[edit services service-set GROUP_ID-0001] user@host# set interface-service service-interface ms-0/2/0.0 user@host# set ipsec-group-vpn GROUP_ID-0001
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, show security, show services, and show
firewall commands. If the output does not display the intended
configuration, repeat the instructions in this example to correct
the configuration.
[edit]
user@host# show interfaces
xe-0/0/1 {
unit 0 {
family inet {
service {
input {
service-set GROUP_ID-0001 service-filter GroupVPN-KS;
}
output {
service-set GROUP_ID-0001 service-filter GroupVPN-KS;
}
}
address 10.18.103.1/24;
}
}
}
xe-0/0/2 {
unit 0 {
family inet {
address 172.16.103.1/24;
}
}
}
ms-0/2/0 {
unit 0 {
family inet;
}
}
[edit]
user@host# show routing-options
static {
route 10.18.101.0/24 next-hop 10.18.103.254;
route 10.18.102.0/24 next-hop 10.18.103.254;
route 10.18.104.0/24 next-hop 10.18.103.254;
route 172.16.101.0/24 next-hop 10.18.103.254;
route 172.16.102.0/24 next-hop 10.18.103.254;
route 172.16.103.0/24 next-hop 10.18.103.254;
route 172.16.104.0/24 next-hop 10.18.103.254;
}
[edit]
user@host# show security
group-vpn {
member {
ike {
proposal PSK-SHA256-DH14-AES256 {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
}
policy KeySrv {
mode main;
proposals PSK-SHA256-DH14-AES256;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway KeySrv {
ike-policy KeySrv;
local-address 10.18.103.1;
server-address 10.10.101.1;
}
}
ipsec {
vpn GROUP_ID-0001 {
ike-gateway KeySrv
group 1;
match-direction output;
tunnel-mtu 1400;
df-bit clear;
}
}
}
}
[edit]
user@host# show services
service-set GROUP_ID-0001 {
interface-service {
service-interface ms-0/2/0.0;
}
ipsec-group-vpn GROUP_ID-0001;
}
[edit]
user@host# show firewall
family inet {
service-filter GroupVPN-KS {
term inbound-ks {
from {
destination-address {
10.10.100.1/32;
}
source-address {
10.10.100.1/32;
}
}
then skip;
}
term outbound-ks {
from {
destination-address {
10.10.100.1/32;
}
}
then skip;
}
term GROUP_ID-0001 {
from {
source-address {
172.16.0.0/12;
}
destination-address {
172.16.0.0/12;
}
}
then service;
}
}
}
Configuring Group Member GM-0004 (MX Series Device)
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces xe-0/0/1 unit 0 family inet service input service-set GROUP_ID-0001 service-filter GroupVPN-KS set interfaces xe-0/0/1 unit 0 family inet service output service-set GROUP_ID-0001 service-filter GroupVPN-KS set interfaces xe-0/0/1 unit 0 family inet address 10.18.104.1/24 set interfaces xe-0/0/2 unit 0 family inet address 172.16.104.1/24 set interfaces ms-0/2/0 unit 0 family inet set routing-options static route 10.18.101.0/24 next-hop 10.18.104.254 set routing-options static route 10.18.102.0/24 next-hop 10.18.104.254 set routing-options static route 10.18.103.0/24 next-hop 10.18.104.254 set routing-options static route 172.16.101.0/24 next-hop 10.18.104.254 set routing-options static route 172.16.102.0/24 next-hop 10.18.104.254 set routing-options static route 172.16.103.0/24 next-hop 10.18.104.254 set routing-options static route 172.16.104.0/24 next-hop 10.18.104.254 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-method pre-shared-keys set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 dh-group group14 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 authentication-algorithm sha-256 set security group-vpn member ike proposal PSK-SHA256-DH14-AES256 encryption-algorithm aes-256-cbc set security group-vpn member ike policy SubSrv mode main set security group-vpn member ike policy SubSrv proposals PSK-SHA256-DH14-AES256 set security group-vpn member ike policy SubSrv pre-shared-key ascii-text "$ABC123" set security group-vpn member ike gateway SubSrv ike-policy SubSrv set security group-vpn member ike gateway SubSrv server-address 10.17.101.1 set security group-vpn member ike gateway SubSrv server-address 10.17.102.1 set security group-vpn member ike gateway SubSrv server-address 10.17.103.1 set security group-vpn member ike gateway SubSrv server-address 10.17.104.1 set security group-vpn member ike gateway SubSrv local-address 10.18.104.1 set security group-vpn member ipsec vpn GROUP_ID-0001 ike-gateway SubSrv set security group-vpn member ipsec vpn GROUP_ID-0001 group 1 set security group-vpn member ipsec vpn GROUP_ID-0001 match-direction output set security group-vpn member ipsec vpn GROUP_ID-0001 tunnel-mtu 1400 set security group-vpn member ipsec vpn GROUP_ID-0001 df-bit clear set services service-set GROUP_ID-0001 interface-service service-interface ms-0/2/0.0 set services service-set GROUP_ID-0001 ipsec-group-vpn GROUP_ID-0001 set firewall family inet service-filter GroupVPN-KS term inbound-ks from destination-address 10.10.100.1/32 set firewall family inet service-filter GroupVPN-KS term inbound-ks from source-address 10.10.100.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks from destination-address 10.17.101.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks from destination-address 10.17.102.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks from destination-address 10.17.103.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks from destination-address 10.17.104.1/32 set firewall family inet service-filter GroupVPN-KS term outbound-ks then skip set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 from source-address 172.16.0.0/12 set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 from destination-address 172.16.0.0/12 set firewall family inet service-filter GroupVPN-KS term GROUP_ID-0001 then service
Step-by-Step Procedure
To configure the Group VPNv2 member:
Configure the interfaces.
[edit interfaces] user@host# set xe-0/0/1 unit 0 family inet service input service-set GROUP_ID-0001 service-filter GroupVPN-KS user@host# set xe-0/0/1 unit 0 family inet service output service-set GROUP_ID-0001 service-filter GroupVPN-KS user@host# set xe-0/0/1 unit 0 family inet address 10.18.104.1/24 user@host# set xe-0/0/2 unit 0 family inet address 172.16.104.1/24 user@host# set ms-0/2/0 unit 0 family inet
Configure routing.
[edit routing-options] user@host# set static route 10.18.101.0/24 next-hop 10.18.104.254 user@host# set static route 10.18.102.0/24 next-hop 10.18.104.254 user@host# set static route 10.18.103.0/24 next-hop 10.18.104.254 user@host# set static route 172.16.101.0/24 next-hop 10.18.104.254 user@host# set static route 172.16.102.0/24 next-hop 10.18.104.254 user@host# set static route 172.16.103.0/24 next-hop 10.18.104.254 user@host# set static route 172.16.104.0/24 next-hop 10.18.104.254
Configure IKE proposal, policy, and gateway.
[edit security group-vpn member ike proposal PSK-SHA256-DH14-AES256 ] user@host# set authentication-method pre-shared-keys user@host# set group group14 user@host# set authentication-algorithm sha-256 user@host# set encryption-algorithm aes-256-cbc [edit security group-vpn member ike policy KeySrv ] user@host# set mode main user@host# set proposals PSK-SHA256-DH14-AES256 user@host# set pre-shared-key ascii-text "$ABC123" [edit security group-vpn member ike gateway KeySrv] user@host# set ike-policy KeySrv user@host# set server-address 10.10.100.1 user@host# set local-address 10.18.104.1
Configure the IPsec SA.
[edit security group-vpn member ipsec vpn GROUP_ID-0001] user@host# set ike-gateway KeySrv user@host# set group 1 user@host# set match-direction output user@host# set tunnel-mtu 1400 user@host# set df-bit clear
Configure the service filter.
[edit firewall family inet service-filter GroupVPN-KS] user@host# set term inbound-ks from destination-address 10.10.101.1/32 user@host# set term inbound-ks from source-address 10.10.101.1/32 user@host# set term inbound-ks then skip user@host# set term outbound-ks from destination-address 10.17.101.1/32 user@host# set term outbound-ks from destination-address 10.17.102.1/32 user@host# set term outbound-ks from destination-address 10.17.103.1/32 user@host# set term outbound-ks from destination-address 10.17.104.1/32 user@host# set term outbound-ks then skip user@host# set term GROUP_ID-0001 from source-address 172.16.0.0/12 user@host# set term GROUP_ID-0001 from destination-address 172.16.0.0/12 user@host# set term GROUP_ID-0001 then service
Configure the service set.
[edit services service-set GROUP_ID-0001] user@host# set interface-service service-interface ms-0/2/0.0 user@host# set ipsec-group-vpn GROUP_ID-0001
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show routing-options, show security, show services, and show
firewall commands. If the output does not display the intended
configuration, repeat the instructions in this example to correct
the configuration.
[edit]
user@host# show interfaces
xe-0/0/1 {
unit 0 {
family inet {
service {
input {
service-set GROUP_ID-0001 service-filter GroupVPN-KS;
}
output {
service-set GROUP_ID-0001 service-filter GroupVPN-KS;
}
}
address 10.18.104.1/24;
}
}
}
xe-0/0/2 {
unit 0 {
family inet {
address 172.16.104.1/24;
}
}
}
ms-0/2/0 {
unit 0 {
family inet;
}
}
[edit]
user@host# show routing-options
static {
route 10.18.101.0/24 next-hop 10.18.104.254;
route 10.18.102.0/24 next-hop 10.18.104.254;
route 10.18.103.0/24 next-hop 10.18.104.254;
route 172.16.101.0/24 next-hop 10.18.104.254;
route 172.16.102.0/24 next-hop 10.18.104.254;
route 172.16.103.0/24 next-hop 10.18.104.254;
route 172.16.104.0/24 next-hop 10.18.104.254;
}
[edit]
user@host# show security
group-vpn {
member {
ike {
proposal PSK-SHA256-DH14-AES256 {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
}
policy KeySrv {
mode main;
proposals PSK-SHA256-DH14-AES256;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway KeySrv {
ike-policy KeySrv;
local-address 10.18.104.1;
server-address 10.17.101.1;
}
}
ipsec {
vpn GROUP_ID-0001 {
ike-gateway KeySrv
group 1;
match-direction output;
tunnel-mtu 1400;
df-bit clear;
}
}
}
}
[edit]
user@host# show services
service-set GROUP_ID-0001 {
interface-service {
service-interface ms-0/2/0.0;
}
ipsec-group-vpn GROUP_ID-0001;
}
[edit]
user@host# show firewall
family inet {
service-filter GroupVPN-KS {
term inbound-ks {
from {
destination-address {
10.10.100.1/32;
}
source-address {
10.10.100.1/32;
}
}
then skip;
}
term outbound-ks {
from {
destination-address {
10.17.101.1/32;
10.17.102.1/32;
10.17.103.1/32;
10.17.104.1/32;
}
}
then skip;
}
term GROUP_ID-0001 {
from {
source-address {
172.16.0.0/12;
}
destination-address {
172.16.0.0/12;
}
}
then service;
}
}
}
Verification
Confirm that the configuration is working properly.
- Verifying Group Member Registration
- Verifying That Group Keys Are Distributed
- Verifying Group VPN SAs on the Group Server
- Verifying Group VPN SAs on Group Members
- Verifying IPsec SAs on the Group Server
- Verifying IPsec SAs on the Group Members
- Verifying Group Policies (SRX Series Firewall or vSRX Virtual Firewall Group Members Only)
Verifying Group Member Registration
Purpose
Verify that group members are registered on the server.
Action
From operational mode, enter the show security
group-vpn server registered-members and show security group-vpn
server registered-members detail commands on the server.
user@host> show security group-vpn server registered-members Group: GROUP_ID-0001, Group Id: 1 Total number of registered members: 2 Member Gateway Member IP Last Update Vsys GM-0001 10.18.101.1 Thu Nov 19 2015 16:31:09 root GM-0003 10.18.103.1 Thu Nov 19 2015 16:29:47 root
user@host> show security group-vpn server registered-members detail
GGroup: GROUP_ID-0001, Group Id: 1
Total number of registered members: 2
Member gateway: GM-0001, Member IP: 10.18.101.1, Vsys: root
Last Update: Thu Nov 19 2015 16:31:09
Stats:
Pull Succeeded : 2
Pull Failed : 0
Push Sent : 0
Push Acknowledged : 0
Push Unacknowledged : 0
Member gateway: GM-0003, Member IP: 10.18.103.1, Vsys: root
Last Update: Thu Nov 19 2015 16:29:47
Stats:
Pull Succeeded : 1
Pull Failed : 0
Push Sent : 0
Push Acknowledged : 0
Push Unacknowledged : 0
Verifying That Group Keys Are Distributed
Purpose
Verify that group keys are distributed to members.
Action
From operational mode, enter the show security
group-vpn server statistics command on the group server.
user@host> show security group-vpn server statistics
Group: GROUP_ID-0001, Group Id: 1
Stats:
Pull Succeeded : 4
Pull Failed : 0
Pull Exceed Member Threshold : 0
Push Sent : 0
Push Acknowledged : 0
Push Unacknowledged : 0
Verifying Group VPN SAs on the Group Server
Purpose
Verify Group VPN SAs on the group server.
Action
From operational mode, enter the show security
group-vpn server kek security-associations and show security
group-vpn server kek security-associations detail commands on
the group server.
user@host> show security group-vpn server kek security-associations Index Life:sec Initiator cookie Responder cookie GroupId 738879 1206 a471513492db1e13 24045792a4b3dd64 1
user@host> show security group-vpn server kek security-associations detail Index 738879, Group Name: GROUP_ID-0001, Group Id: 1 Initiator cookie: a471513492db1e13, Responder cookie: 24045792a4b3dd64 Authentication method: RSA Lifetime: Expires in 1204 seconds, Activated Rekey in 694 seconds Algorithms: Sig-hash : sha256 Encryption : aes256-cbc Traffic statistics: Input bytes : 0 Output bytes : 0 Input packets: 0 Output packets: 0 Server Member Communication: Unicast Retransmission Period: 10, Number of Retransmissions: 2 Group Key Push sequence number: 0 PUSH negotiations in progress: 0
Verifying Group VPN SAs on Group Members
Purpose
Verify Group VPN SAs on the group members.
Action
From operational mode, enter the show security group-vpn member kek
security-associations and show security group-vpn
member kek security-associations detail commands on the SRX
Series Firewall or vSRX Virtual Firewall group member.
user@host> show security group-vpn member kek security-associations Index Server Address Life:sec Initiator cookie Responder cookie GroupId 5455810 10.10.100.1 1093 a471513492db1e13 24045792a4b3dd64 1
user@host> show security group-vpn member kek security-associations detail
Index 5455810, Group Id: 1
Group VPN Name: GROUP_ID-0001
Local Gateway: 10.18.101.1, GDOI Server: 10.10.100.1
Initiator cookie: a471513492db1e13, Responder cookie: 24045792a4b3dd64
Lifetime: Expires in 1090 seconds
Group Key Push Sequence number: 0
Algorithms:
Sig-hash : hmac-sha256-128
Encryption : aes256-cbc
Traffic statistics:
Input bytes : 0
Output bytes : 0
Input packets: 0
Output packets: 0
Stats:
Push received : 0
Delete received : 0
From operational mode, enter the show security group-vpn
member kek security-associations and show security group-vpn
member kek security-associations detail commands on the MX Series
group member.
user@host> show security group-vpn member kek security-associations Index Server Address Life:sec Initiator cookie Responder cookie GroupId 488598 10.10.100.1 963 a471513492db1e13 24045792a4b3dd64 1
user@host> show security group-vpn member kek security-associations detail
Index 488598, Group Id: 1
Group VPN Name: GROUP_ID-0001
Local Gateway: 10.18.103.1, GDOI Server: 10.10.100.1
Initiator cookie: a471513492db1e13, Responder cookie: 24045792a4b3dd64
Lifetime: Expires in 961 seconds
Group Key Push Sequence number: 0
Algorithms:
Sig-hash : hmac-sha256-128
Encryption : aes256-cbc
Traffic statistics:
Input bytes : 0
Output bytes : 0
Input packets: 0
Output packets: 0
Stats:
Push received : 0
Delete received : 0
Verifying IPsec SAs on the Group Server
Purpose
Verify IPsec SAs on the group server.
Action
From operational mode, enter the show security
group-vpn server ipsec security-associations and show security
group-vpn server ipsec security-associations detail commands
on the group server.
user@host> show security group-vpn server ipsec security-associations Group: GROUP_ID-0001, Group Id: 1 Total IPsec SAs: 1 IPsec SA Algorithm SPI Lifetime GROUP_ID-0001 ESP:aes-256/sha256 1c548e4e 1156
user@host> show security group-vpn server ipsec security-associations detail
Group: GROUP_ID-0001, Group Id: 1
Total IPsec SAs: 1
IPsec SA: GROUP_ID-0001
Protocol: ESP, Authentication: sha256, Encryption: aes-256
Anti-replay: D3P enabled
SPI: 1c548e4e
Lifetime: Expires in 1152 seconds, Activated
Rekey in 642 seconds
Policy Name: 1
Source: 172.16.0.0/12
Destination: 172.16.0.0/12
Source Port: 0
Destination Port: 0
Protocol: 0
Verifying IPsec SAs on the Group Members
Purpose
Verify IPsec SAs on the group members.
Action
From operational mode, enter the show security group-vpn member ipsec
security-associations and show security group-vpn
member ipsec security-associations detail commands on the SRX
Series Firewall or vSRX Virtual Firewall group member.
user@host> show security group-vpn member ipsec security-associations Total active tunnels: 1 ID Server Port Algorithm SPI Life:sec/kb GId lsys <>49152 10.10.100.1 848 ESP:aes-256/sha256-128 1c548e4e 1073/ unlim 1 root
user@host> show security group-vpn member ipsec security-associations detail
Virtual-system: root Group VPN Name: GROUP_ID-0001
Local Gateway: 10.18.101.1, GDOI Server: 10.10.100.1
Group Id: 1
Routing Instance: default
Recovery Probe: Enabled
DF-bit: clear
Stats:
Pull Succeeded : 4
Pull Failed : 3
Pull Timeout : 3
Pull Aborted : 0
Push Succeeded : 6
Push Failed : 0
Server Failover : 0
Delete Received : 0
Exceed Maximum Keys(4) : 0
Exceed Maximum Policies(10): 0
Unsupported Algo : 0
Flags:
Rekey Needed: no
List of policies received from server:
Tunnel-id: 49152
Source IP: ipv4_subnet(any:0,[0..7]=172.16.0.0/12)
Destination IP: ipv4_subnet(any:0,[0..7]=172.16.0.0/12)
Direction: bi-directional, SPI: 1c548e4e
Protocol: ESP, Authentication: sha256-128, Encryption: aes-256
Hard lifetime: Expires in 1070 seconds, Activated
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 931 seconds
Mode: Tunnel, Type: Group VPN, State: installed
Anti-replay service: D3P enabled
From operational mode, enter the show security group-vpn
member ipsec security-associations and show security group-vpn
member ipsec security-associations detail commands on the MX
Series group member.
user@host> show security group-vpn member ipsec security-associations Total active tunnels: 1 ID Server Port Algorithm SPI Life:sec/kb GId lsys <>10001 10.10.100.1 848 ESP:aes-256/sha256-128 1c548e4e 947/ unlim 1 root
user@host> show security group-vpn member ipsec security-associations detail
Virtual-system: root Group VPN Name: GROUP_ID-0001
Local Gateway: 10.18.103.1, GDOI Server: 10.10.100.1
Group Id: 1
Rule Match Direction: output, Tunnel-MTU: 1400
Routing Instance: default
DF-bit: clear
Stats:
Pull Succeeded : 2
Pull Failed : 0
Pull Timeout : 1
Pull Aborted : 0
Push Succeeded : 2
Push Failed : 0
Server Failover : 0
Delete Received : 0
Exceed Maximum Keys(4) : 0
Exceed Maximum Policies(1): 0
Unsupported Algo : 0
Flags:
Rekey Needed: no
List of policies received from server:
Tunnel-id: 10001
Source IP: ipv4_subnet(any:0,[0..7]=172.16.0.0/12)
Destination IP: ipv4_subnet(any:0,[0..7]=172.16.0.0/12)
Direction: bi-directional, SPI: 1c548e4e
Protocol: ESP, Authentication: sha256-128, Encryption: aes-256
Hard lifetime: Expires in 945 seconds, Activated
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 840 seconds
Mode: Tunnel, Type: Group VPN, State: installed
Anti-replay service: D3P enabled
Verifying Group Policies (SRX Series Firewall or vSRX Virtual Firewall Group Members Only)
Purpose
Verify group policies on SRX Series Firewall or vSRX Virtual Firewall group members.
Action
From operational mode, enter the show security
group-vpn member policy command on the group member.
user@host> show security group-vpn member policy Group VPN Name: GROUP_ID-0001, Group Id: 1 From-zone: LAN, To-zone: WAN Tunnel-id: 49152, Policy type: Secure Source : IP <172.16.0.0 - 172.31.255.255>, Port <0 - 65535>, Protocol <0> Destination : IP <172.16.0.0 - 172.31.255.255>, Port <0 - 65535>, Protocol <0> Tunnel-id: 63488, Policy type: Fail-close Source : IP <0.0.0.0 - 255.255.255.255>, Port <0 - 65535>, Protocol <0> Destination : IP <0.0.0.0 - 255.255.255.255>, Port <0 - 65535>, Protocol <0>
Example: Configuring Group VPNv2 Server-Member Communication for Unicast Rekey Messages
This example shows how to enable the server to send unicast rekey messages to group members to ensure that valid keys are available for encrypting traffic between group members.
Requirements
Before you begin:
Configure the group server and members for IKE Phase 1 negotiation.
Configure the group server and members for IPsec SA.
Configure the group
g1on the group server.
Overview
In this example, you specify the following server-member communication
parameters for group g1:
The server sends unicast rekey messages to group members.
aes-128-cbc is used to encrypt traffic between the server and members.
sha-256 is used for member authentication.
Default values are used for KEK lifetime and retransmissions.
Configuration
Procedure
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode.
To configure server-member communication:
Set the communications type.
[edit security group-vpn server group g1 server-member-communication] user@host# set communications-type unicast
Set the encryption algorithm.
[edit security group-vpn server group g1 server-member-communication] user@host# set encryption-algorithm aes-128-cbc
Set the member authentication.
[edit security group-vpn server group g1 server-member-communication] user@host# set sig-hash-algorithm sha-256
Verification
To verify the configuration is working properly,
enter the show security group-vpn server group g1 server-member-communication command.
