Central Web Authentication
Web authentication provides access to network for users by redirecting the client’s Web browser to a central Web authentication server (CWA server), which handles the complete login process. Web authentication can also be used as a fallback authentication method for regular network users who have 802.1X-enabled devices, but fail authentication because of other issues, such as expired network credentials.
Understanding Central Web Authentication
Web authentication redirects Web browser requests to a login page that requires the user to input a username and password. Upon successful authentication, the user is allowed access to the network. Web authentication is useful for providing network access to temporary users, such as visitors to a corporate site, who try to access the network using devices that are not 802.1X-enabled. Web authentication can also be used as a fallback authentication method for regular network users who have 802.1X-enabled devices, but fail authentication because of other issues, such as expired network credentials.
Web authentication can be done locally on the switch using captive portal, but this requires that the Web portal pages be configured on each switch used as a network access device. Central Web authentication (CWA) provides efficiency and scaling benefits by redirecting the client’s Web browser to a central Web authentication server (CWA server), which handles the complete login process.
CWA is supported with MAC RADIUS authentication only. CWA is not supported with 802.1X authentication.
- Central Web Authentication Process
- Dynamic Firewall Filters for Central Web Authentication
- Redirect URL for Central Web Authentication
Central Web Authentication Process
Central Web authentication is invoked after a host has failed MAC RADIUS authentication. The host can attempt authentication using 802.1X authentication first, but must then attempt MAC RADIUS authentication before attempting central Web authentication. The switch, operating as the authenticator, exchanges RADIUS messages with the authentication, authorization, and accounting (AAA) server. After MAC RADIUS authentication fails, the switch receives an Access-Accept message from the AAA server. This message includes a dynamic firewall filter and a redirect URL for central Web authentication. The switch applies the filter, which allows the host to receive an IP address, and uses the URL to redirect the host to the Web authentication page.
The host is prompted for login credentials and might also be asked to agree to an acceptable use policy. If Web authentication is successful, the AAA server sends a Change of Authorization (CoA) message, which updates the terms of the authorized session in progress. This enables the authenticator to update the filter or VLAN assignment applied to the controlled port, to allow the host to access the LAN.
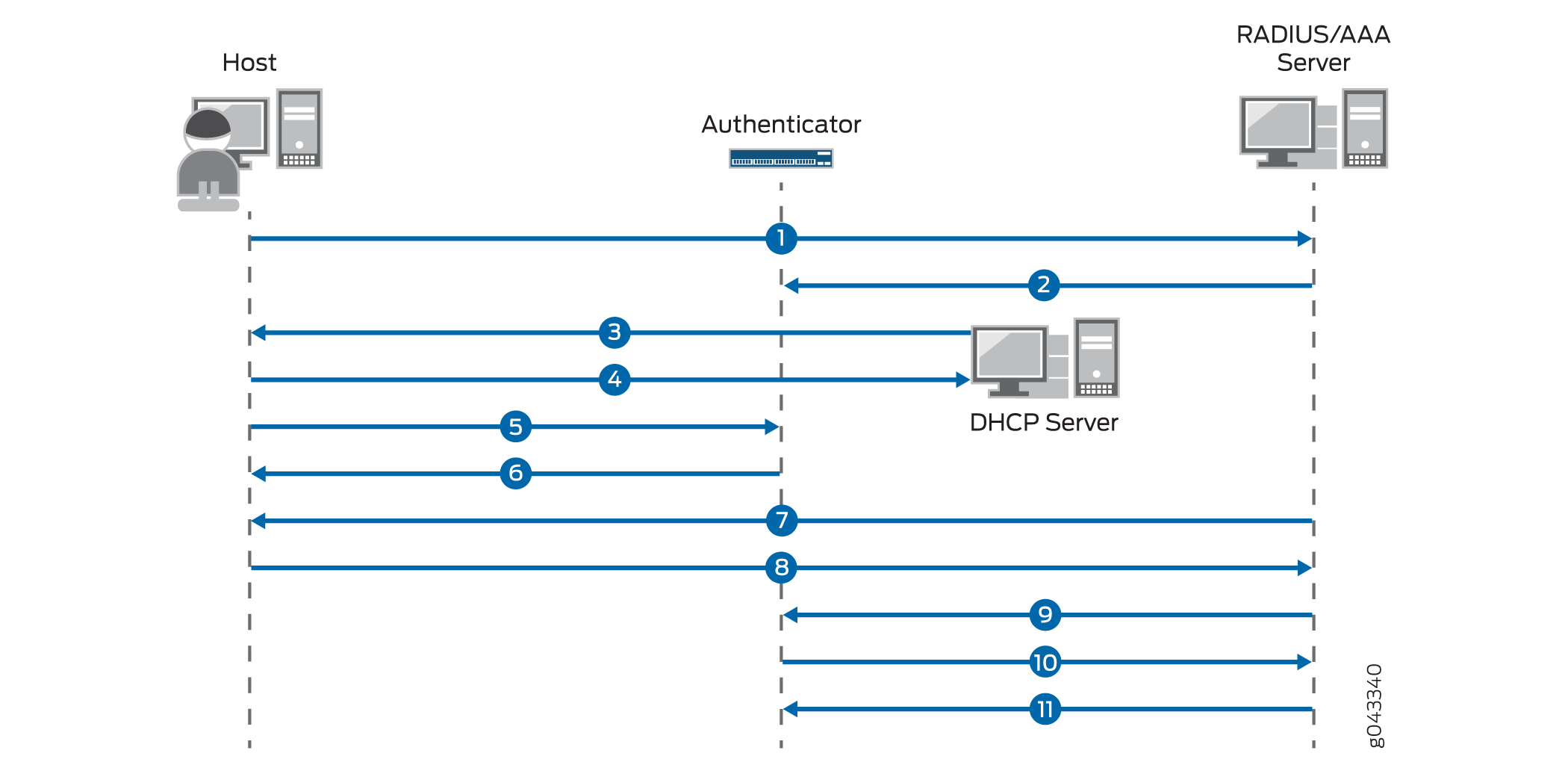
The sequence of events in central Web authentication is as follows (see Figure 1):
-
A host connected to the switch (authenticator) initiates MAC RADIUS authentication.
-
MAC RADIUS authentication fails. Instead of sending an Access-Reject message to the switch, the AAA server sends an Access-Accept message that includes a dynamic firewall filter and a CWA redirect URL.
-
The host is allowed by the terms of the filter to send DHCP requests.
-
The host receives an IP address and DNS information from the DHCP server. The AAA server initiates a new session that has a unique session ID.
-
The host opens a Web browser.
-
The authenticator sends the CWA redirect URL to the host.
-
The host is redirected to the CWA server and is prompted for login credentials.
-
The host provides the username and password.
-
After successful Web authentication, the AAA server sends a CoA message to udpate the filter or VLAN assignment applied on the controlled port, allowing the host to access the LAN.
-
The authenticator responds with a CoA-ACK message and sends a MAC RADIUS authentication request to the AAA server.
-
The AAA server matches the session ID to the appropriate access policy and sends an Access-Accept message to authenticate the host.
Dynamic Firewall Filters for Central Web Authentication
Central Web authentication uses dynamic firewall filters, which are centrally defined on the AAA server and dynamically applied to supplicants that request authentication through that server. The filter allows the host to get an IP address dynamically using DHCP. You define the filters by using RADIUS attributes, which are included in the Access-Accept messages sent from the server. Filters can be defined using either the Juniper-Switching-Filter attribute, which is a vendor-specific attribute (VSA), or the Filter-ID attribute, which is an IETF RADIUS attribute.
To use the Juniper-Switching-Filter VSA for central Web authentication, you must configure the filter with the correct terms that allow the destination IP address of the CWA server. This configuration is done directly on the AAA server. To use the Filter-ID attribute for central web authentication, enter the value as JNPR_RSVD_FILTER_CWA on the AAA server. The filter terms for this attribute are internally defined for central Web authentication, because of which no additional configuration is required. For more information about configuring dynamic firewall filters for central web authentication, see Configuring Central Web Authentication.
Redirect URL for Central Web Authentication
In central Web authentication, the authenticator redirects the host’s Web browser request to the CWA server by using a redirect URL. After redirection, the CWA server completes the login process. The redirect URL for central web authentication can be configured on the AAA server or on the authenticator. The redirect URL, along with the dynamic firewall filter, must be present to trigger the central web authentication process after the failure of MAC RADIUS authentication.
The redirect URL can be centrally defined on the AAA server by using the
Juniper-CWA-Redirect VSA, which is attribute number 50 in the Juniper RADIUS
dictionary. The URL is forwarded from the AAA server to the switch in the same
RADIUS Access-Accept message that contains the dynamic firewall filter. You can also
configure the redirect URL locally on the host interface by using the CLI statement
redirect-url at the [edit protocols dot1x authenticator
interface interface-name
] hierarchy level. For more
information about configuring the redirect URL, see Configuring Central Web Authentication.
See Also
Configuring Central Web Authentication
Central Web authentication is a fallback method of authentication in which the host’s Web browser is redirected to a central Web authentication (CWA) server. The CWA server provides a web portal where the user can enter a username and password. If these credentials are validated by the CWA server, the user is authenticated and is allowed access to the network.
Central Web authentication is invoked after a host has failed MAC RADIUS authentication. The switch, operating as the authenticator, receives a RADIUS Access-Accept message from the AAA server that includes a dynamic firewall filter and a redirect URL for central Web authentication. The dynamic firewall filter and the redirect URL must both be present for the central Web authentication process to be triggered.
- Configuring Dynamic Firewall Filters for Central Web Authentication
- Configuring the Redirect URL for Central Web Authentication
- Guidelines for Configuring Central Web Authentication
Configuring Dynamic Firewall Filters for Central Web Authentication
Dynamic firewall filters are used in central Web authentication to enable the host to get an IP address from a DHCP server, which allows the host to access the network. The filters are defined on the AAA server using RADIUS attributes, which are sent to the authenticator in an Access-Accept message. You can define the filter using either the Juniper-Switching-Filter attribute, which is a vendor-specific attribute (VSA), or the Filter-ID attribute, which is an IETF RADIUS attribute.
To use the Juniper-Switching-Filter VSA for central Web authentication, you must configure the filter terms directly on the AAA server. The filter must include a term to match the destination IP address of the CWA server with the action
allow.For example:
001122334455 Auth-Type := EAP, Cleartext-Password :="001122334455" Session-Timeout = "300", Juniper-CWA-Redirect-URL = "https://10.10.10.10", Juniper-Switching-Filter = "Match Destination-ip 10.10.10.10 Action allow, Match ip-protocol 17 Action allow, Match Destination-mac 00:01:02:33:44:55 Action deny"Note:The switch does not resolve the DNS queries for the redirect URL. You must configure the Juniper-Switching-Filter attribute to allow the destination IP address of the CWA server.
To use the Filter-ID attribute for central Web authentication, enter JNPR_RSVD_FILTER_CWA as the value for the attribute on the AAA server. The filter terms for this attribute are internally defined for central Web authentication, because of which no additional configuration is required.
For example:
001122334455 Auth-Type := EAP, Cleartext-Password :="001122334455" Session-Timeout = "300", Juniper-CWA-Redirect-URL = "https://10.10.10.10", Filter-Id = "JNPR_RSVD_FILTER_CWA",
For more information about configuring dynamic firewall filters on the AAA server, see the documentation for your AAA server.
Configuring the Redirect URL for Central Web Authentication
In central Web authentication, the authenticator redirects the host’s Web browser request to the CWA server by using a redirect URL. The redirect URL for central Web authentication can be configured on the AAA server or locally on the host interface.
To configure the redirect URL on the AAA server, use the Juniper-CWA-Redirect VSA, which is attribute number 50 in the Juniper RADIUS dictionary. The URL is forwarded from the AAA server to the switch in the same RADIUS Access-Accept message that contains the dynamic firewall filter.
For example:
001122334455 Auth-Type := EAP, Cleartext-Password :="001122334455" Session-Timeout = "300", Juniper-CWA-Redirect-URL = "https://10.10.10.10", Filter-Id = "JNPR_RSVD_FILTER_CWA",Note:When the special Filter-ID attribute JNPR_RSVD_FILTER_CWA is used for the dynamic firewall filter, the redirect URL must include the IP address of the AAA server, for example, https://10.10.10.10.
To configure the redirect URL locally on the host interface, use the following CLI statement:
[edit] user@switch# set protocols dot1x authenticator interface interface-name redirect-url
For example:
user@switch# show protocols dot1x authenticator { authentication-name-profile auth1; interface { ge-0/0/1.0 { supplicant single; mac-radius; redirect-url https://10.10.10.10; } } }
Guidelines for Configuring Central Web Authentication
Central Web authentication is triggered after the failure of MAC RADIUS authentication when the redirect URL and dynamic firewall filter are both present. The redirect URL and dynamic firewall filter can be configured in any of the following combinations:
The AAA server sends both the CWA redirect URL and dynamic firewall filter to the authenticator. The redirect URL is configured on the AAA server by using the Juniper-CWA-Redirect VSA and the dynamic firewall filter is configured on the AAA server by using the Juniper-Switching-Filter VSA. The filter must be configured to allow the destination IP address of the CWA server in this case.
The AAA server sends the dynamic firewall filter to the authenticator and the redirect URL is configured locally on the host port. The redirect URL is configured on the authenticator by using the
redirect-urlCLI statement and the dynamic firewall filter is configured on the AAA server by using the Juniper-Switching-Filter VSA. The filter must be configured to allow the destination IP address of the CWA server in this case.The AAA server sends both the CWA redirect URL and dynamic firewall filter to the authenticator. The redirect URL is configured on the AAA server by using the Juniper-CWA-Redirect VSA and the dynamic firewall filter is configured on the AAA server by using the Filter-ID attribute with the value JNPR_RSVD_FILTER_CWA. The redirect URL must contain the IP address of the CWA server in this case.
-
The AAA server sends the dynamic firewall filter to the authenticator and the redirect URL is configured locally on the host port. The redirect URL is configured on the authenticator by using the
redirect-urlCLI statement and the dynamic firewall filter is configured on the AAA server by using the Filter-ID attribute with the value JNPR_RSVD_FILTER_CWA. The redirect URL must contain the IP address of the CWA server in this case.Note:The
redirect-urlcommand statement is required in the CLI only if the RADIUS server is not sending the redirect URL in the "Juniper-CWA-Redirect" VSA.
