ON THIS PAGE
Understanding BPDU Protection for Spanning-Tree Instance Interfaces
Configuring BPDU Protection for Individual Spanning-Tree Instance Interfaces
Understanding BPDUs Used for Exchanging Information Among Bridges
Configuring Interface for BPDU Protection With Port Shutdown Mode
Configuring Interface for BPDU Protection With BPDU Drop Mode
BPDU Protection for Spanning-Tree Protocols
Understanding BPDU Protection for Spanning-Tree Instance Interfaces
ACX Series routers, MX Series routers, PTX Series routers, EX Series switches, and QFX Series switches support spanning-tree protocols that prevent loops in a network by creating a tree topology (spanning-tree) of the entire bridged network. All spanning-tree protocols use a special type of frame called bridge protocol data units (BPDUs) to communicate with each other.
The Spanning Tree Protocol (STP) family is designed to break possible loops in a Layer 2 bridged network. Loop prevention avoids damaging broadcast storms that can potentially render the network useless. STP processes on bridges exchange BPDUs to determine the LAN topology, decide the root bridge, stop forwarding on some ports, and so on. However, a misbehaving user application or device can interfere with the operation of the STP protocols and cause network problems.
BPDU-block is a feature that defends the STP topology from a misbehaving user application or device or a threat. You must enable BPDU guard on the interfaces that are not supposed to receive any BPDUs.
If an interface is configured to be edge port, it will transition directly to the Forwarding state. Such ports are connected to end devices and are not expected to receive BPDU. Therefore, to avoid loops, you must protect edge ports by enabling bpdu-block-on-edge.
On the routers and switches that support STP, you can configure BPDU protection to ignore BPDUs received on interfaces where none should be expected (for example, a LAN interface on a network edge with no other bridges present). If a BPDU is received on a protected interface, the interface is disabled and stops forwarding frames. By default, all BPDUs are accepted and processed on all interfaces.
You can achieve BPDU protection in several ways. By default, if bpdu-block is enabled on the interface, on receiving BPDU, the interface will be disabled and all traffic forwarding will stop on the interface. However, if you do not want to disable the interface and do not want that interface to take part in the STP calculation, you can configure action drop. If you configure action drop, the interface remains up and running and traffic continues to flow; however, BPDUs are dropped.
The edge ports do not support action drop. BPDU-block-on-edge disables the interface if the edge ports receive BPDUs. You must clear the error to bring the interface back up.
You can configure BPDU protection on interfaces with the following encapsulation types:
-
ethernet-bridge
-
ethernet-vpls
-
extended-vlan-bridge
-
vlan-vpls
-
vlan-bridge
-
extended-vlan-vpls
You can configure BPDU protection on individual interfaces or on all the edge ports of the bridge.
Enable BPDU protection on interfaces that are configured as edge ports by using the
bpdu-block-on-edge command under the set protocols
(mstp|rstp|vstp) hierarchy. If you have not configured a port as an edge
port, you can still configure BPDU protection on the interface by using the
bpdu-block command under the set protocols
layer2-control hierarchy. You can also use the bpdu-block
command to configure BPDU protection on interfaces configured for a spanning-tree.
See Also
Understanding BPDU Protection for STP, RSTP, and MSTP
Networks frequently use multiple protocols simultaneously to achieve different goals and in some cases those protocols might conflict with each other. One such case is when spanning-tree protocols are active on the network, where a special type of switching frame called a bridge protocol data unit (BPDU) can conflict with BPDUs generated on other devices such as PCs. The different kinds of BPDUs are not compatible, but they can still be recognized by other devices that use BPDUs and cause network outages. You need to protect any device that recognizes BPDUs from picking up incompatible BPDUs.
Different Types of BPDUs
Spanning-tree protocols such as Spanning Tree Protocol (STP), Rapid Spanning Tree Protocol (RSTP), VLAN Spanning Tree Protocol (VSTP), and Multiple Spanning Tree Protocol (MSTP) generate their own BPDUs. These peer STP applications use their BPDUs to communicate, and ultimately, the exchange of BPDUs determines which interfaces block traffic and which interfaces become root ports. The root ports and designated ports forward traffic; the alternate and back up ports block the traffic.
Configuring BPDU Protection for Individual Spanning-Tree Instance Interfaces
To configure BPDU protection on one or more spanning-tree
instance interfaces, include the bpdu-block statement:
bpdu-block { interface interface-name; disable-timeout seconds; }
If you also include the optional disable-timeout seconds
statement, protected interfaces are automatically cleared after the specified
time interval unless the interval is 0.
Understanding BPDUs Used for Exchanging Information Among Bridges
In a Layer 2 bridge environment, spanning-tree protocols use data frames called Bridge Protocol Data Units (BPDUs) to exchange information among bridges.
Spanning-tree protocols on peer systems exchange BPDUs, which contain information about port roles, bridge IDs, and root path costs. On each router or switch, the spanning-tree protocol uses this information to elect a root bridge, identify root ports for each switch, identify designated ports for each physical LAN segment, and prune specific redundant links to create a loop-free tree topology. The resulting tree topology provides a single active Layer 2 data path between any two end stations.
In discussions of spanning-tree protocols, the terms bridge and switch are often used interchangeably.
The transmission of BPDUs is controlled by the Layer 2 Control Protocol process (l2cpd) on MX Series 5G Universal Routing Platforms.
The transmission of periodic packets on behalf of the l2cpd process is carried out by periodic packet management (PPM), which, by default, is configured to run on the Packet Forwarding Engine. The ppmd process on the Packet Forwarding Engine ensures that the BPDUs are transmitted even when the l2cpd is unavailable, and keeps the remote adjacencies alive during a unified in-service software upgrade (unified ISSU). However, if you want the distributed PPM (ppmd) process to run on the Routing Engine instead of the Packet Forwarding Engine, you can disable the ppmd process on the Packet Forwarding Engine.
On routers and switches with redundant Routing Engines (two Routing Engines that are installed in the same router), you can configure nonstop bridging. Nonstop bridging enables the router to switch from a primary Routing Engine to a backup Routing Engine without losing Layer 2 Control Protocol (L2CP) information. Nonstop bridging uses the same infrastructure as graceful Routing Engine switchover (GRES) to preserve interface and kernel information. However, nonstop bridging also saves L2CP information by running the l2cpd process on the backup Routing Engine.
To use nonstop bridging, you must first enable GRES.
Nonstop bridging is supported for the following Layer 2 control protocols:
Spanning-Tree Protocol (STP)
Rapid Spanning-Tree Protocol (RSTP)
Multiple Spanning-Tree Protocol (MSTP)
Understanding BPDU Protection for EVPN-VXLAN
EVPN-VXLAN data center fabrics have a number of built-in Ethernet loop prevention mechanisms, such as split-horizon and designated forwarder and non-designated forwarder election. In some existing data center environments where a new IP EVPN fabric is being deployed, you might need to configure BPDU protection at the leaf-to-server interface in order to avoid network outages due to xSTP miscalculations. Incorrect cabling between the server and leaf interfaces, or any back-door layer 2 link between two or more ESI-LAG interfaces, might cause miscalculations and then result in Ethernet loops. Without BPDU protection, BPDUs might not be recognized and will be flooded as unknown Layer 2 packets on the VXLAN interfaces. With BPDU protection, when a BPDU is received on an edge port in an EVPN-VXLAN environment, the edge port is disabled and stops forwarding all traffic. You can also configure BPDU protection to drop BPDU traffic but have all other traffic forwarded on the interfaces without having to configure a spanning-tree protocol.
Configuring Interface for BPDU Protection With Port Shutdown Mode
To configure BPDU protection on an edge interface of a switch:
Ensure that the switch is connected to an end device.
Configuring Interface for BPDU Protection With BPDU Drop Mode
For certain access switches, you might want interfaces on the switch not to shutdown on encountering incompatible BPDU packets; instead, only drop incompatible BPDU packets while allowing the remaining traffic to pass through. Such an interface must not have a spanning-tree protocol configured on it, so that packets that pass through the interface will not cause STP misconfiguration and consequent network outages.
To configure BPDU protection for an interface to only drop incompatible BPDU packets and to allow the remaining traffic to pass through, while retaining the interface status as up:
Ensure that the switch on which you are configuring BPDU protection is connected to a peer device.
Configuring BPDU Protection for Edge Interfaces
In a spanning-tree topology, if a switch is an access switch then interfaces on that switch will be connected to end devices such as PCs, servers, routers, or hubs, that are not connected to other switches. You configure these interfaces as edge interfaces because they directly connect to end devices.
Interfaces that are configured as edge interfaces can transition to a forwarding state
immediately because they cannot create network loops. A switch detects edge ports by
noting the absence of communication from the end stations. As edge ports are
connected to end devices, it is imperative that you configure BPDU protection on
edge ports to avoid loops. If BPDU protection is enabled on an edge interface, the
interface shuts down on encountering ae BPDU thereby preventing any traffic from
passing through the interface. You can re-enable the interface by issuing the
clear error bpdu interface
interface-name operational mode command. The
clear error bpdu interface
interface-name command will only re-enable an
interface but the BPDU configuration for the interface will continue to exist unless
you explicitly remove the BPDU configuration.
To configure BPDU protection on an edge interface of a switch:
Ensure that the switch is connected to an end device.
Example: Blocking BPDUs on an Interface for 600 Seconds
The following example, when used with a full bridge configuration with aggregated Ethernet, blocks BPDUs on interface ae0 for 10 minutes (600 seconds) before enabling the interface again:
[edit protocols layer2-control]
bpdu-block {
interface ae0;
disable-timeout 600;
}
See Also
Example: Configuring BPDU Protection on Interfaces
This example uses Junos OS for EX Series switches without support for the Enhanced Layer 2 Software (ELS) configuration style. For ELS details, see Using the Enhanced Layer 2 Software CLI.
When BPDU protection is enabled, an interface shuts down or drops BPDU packets when any incompatible BPDU is encountered, thereby preventing the BPDUs generated by spanning-tree protocols from reaching the switch. When an interface is configured to drop BPDU packets, all traffic except the incompatible BPDUs can pass through the interface.
The BPDU drop feature can be specified only on interfaces on which no spanning-tree protocol is configured.
This example configures BPDU protection on STP switch downstream interfaces that connect to two PCs:
Requirements
This example uses the following hardware and software components:
-
One EX Series switch in an RSTP topology
-
One EX Series switch that is not in any spanning-tree topology
-
Junos OS Release 9.1 or later for EX Series switches
Before you configure the interfaces on Switch 2 for BPDU protection, be sure you have:
-
Ensured that RSTP is operating on Switch 1.
-
Disabled or enabled RSTP on Switch 2 (depending on the configuration that you plan to implement.)
If you want to enable the BPDU shutdown feature, then it is optional to disable spanning-tree protocols on the interface.
By default, RSTP is enabled on all EX Series switches.
Overview and Topology
This example explains how to configure BPDU protection on an interface.
Figure 1 shows the topology for this example. Switch 1 and Switch 2 are connected through a trunk interface. Switch 1 is configured for RSTP while Switch 2 has a spanning-tree protocol configured on it for the first scenario, and does not have a spanning-tree protocol configured on it for the second scenario.
In the first scenario, this example configures downstream BPDU protection on Switch 2
interfaces ge-0/0/5.0 and ge-0/0/6.0
when the default spanning-tree protocol (RSTP) is not disabled on these interfaces.
When BPDU protection is enabled, the shutdown statement is enabled
by default, and the switch interfaces will shut down if BPDUs generated by the
laptops attempt to access Switch 2.
In the second scenario, this example configures downstream BPDU protection on Switch
2 interfaces ge-0/0/5.0 and ge-0/0/6.0
when there is no spanning-tree protocol configured on these interfaces. When BPDU
protection is enabled with the drop statement, the switch
interfaces drop only the BPDUs while allowing remaining traffic to pass through and
retaining their status as up if BPDUs generated by the laptops attempt to access
Switch 2.
When configuring BPDU protection on an interface without spanning trees connected to a switch with spanning trees, be careful that you do not configure BPDU protection on all interfaces. Doing so could prevent BPDUs being received on switch interfaces (such as a trunk interface) that you intended to have receive BPDUs from a switch with spanning trees.
Topology
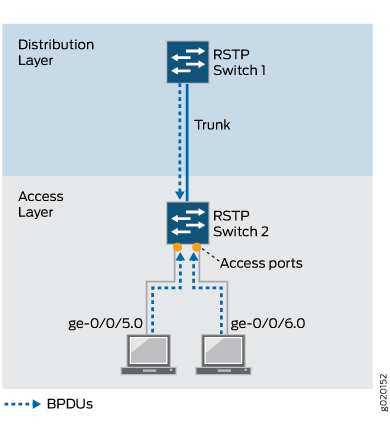
Table 1 shows the components that will be configured for BPDU protection.
|
Property |
Settings |
|---|---|
|
Switch 1 (Distribution Layer) |
Switch 1 is connected to Switch 2 through a trunk interface. Switch 1 is configured for RSTP. |
|
Switch 2 (Access Layer) |
Switch 2 has two downstream access ports connected to laptops:
|
Configuration
To configure BPDU protection on the interfaces:
Procedure
CLI Quick Configuration
This is the first scenario that explains configuration for the default BPDU
block (action: shutdown). To quickly configure BPDU
protection on Switch 2, copy the following commands and paste them into the
switch terminal window:
[edit] user@switch# set protocols layer2-control bpdu-block interface ge-0/0/5 [edit] user@switch# set protocols layer2-control bpdu-block interface ge-0/0/6
Step-by-Step Procedure
To configure BPDU protection for the shutdown statement:
-
Configure the BPDU block (action:
shutdown) on the downstream interface ge-0/0/5 on Switch 2:[edit protocols] user@switch# set layer2-control bpdu-block interface ge-0/0/5
-
Configure the BPDU block (action:
shutdown) on the downstream interface ge-0/0/6 on Switch 2:[edit protocols] user@switch# set layer2-control bpdu-block interface ge-0/0/6
Results
Check the results of the configuration:
user@switch> show protocols layer2-control
bpdu-block {
interface ge-0/0/5;
interface ge-0/0/6;
}
Procedure
CLI Quick Configuration
This is the second scenario that explains configuration for the
drop statement. To quickly configure BPDU protection on
Switch 2 for the drop statement, copy the following
commands and paste them into the switch terminal window:
[edit] user@switch# set protocols layer2-control bpdu-block interface ge-0/0/5 drop user@switch# set protocols layer2-control bpdu-block interface ge-0/0/6 drop
If xSTP is enabled on the interface, you must disable it before
configuring BPDU drop action: block. You can disable RSTP globally by
using the delete protocols rstp, the set
protocols rstp disable, or the set protocols rstp
interface all disable command.
Step-by-Step Procedure
To configure BPDU protection for the drop statement:
-
Configure the BPDU
dropstatement on the downstream interface ge-0/0/5 on Switch 2:[edit protocols layer2-control] user@switch# set bpdu-block interface ge-0/0/50 drop
-
Configure the BPDU
dropstatement on the downstream interface ge-0/0/6 on Switch 2:[edit protocols layer2-control] user@switch# set bpdu-block interface ge-0/0/6 drop
Results
Check the results of the configuration:
user@switch> show configuration protocols layer2-control
bpdu-block {
interface ge-0/0/5;
interface ge-0/0/6;
}
