Overview of Port Security
Port Security Features
Ethernet LANs are vulnerable to attacks such as address spoofing (forging) and Layer 2 denial of service (DoS) on network devices. Port security features help protect the access ports on your device against the loss of information and productivity that such attacks can cause.
Junos OS is hardened through the separation of control forwarding and services planes, with each function running in protected memory. The control-plane CPU is protected by rate limiting, routing policy, and firewall filters to ensure switch uptime even under severe attack.
Junos OS provides features to help secure ports on a device. Ports can be categorized as either trusted or untrusted. You apply policies appropriate to each category to protect ports against various types of attacks.
Access port security features such as dynamic Address Resolution Protocol (ARP) inspection, DHCP snooping, and MAC limiting are controlled through a single Junos OS CLI command. Basic port security features are enabled in the device’s default configuration. You can configure additional features with minimal configuration steps. Depending on the particular feature, you can configure the feature either on VLANs or bridge domain interfaces.
Starting with Junos OS Release 18.4R1, DHCP snooping occurs on trusted ports for the following Juniper Series switches, EX2300, EX4600, and QFX5K. Prior to Junos OS Release 18.4R1, for these devices, this was true only for DHCPv6 snooping. In addition, DHCP snooping occurs on trusted ports for EX9200 Series switches, and Fusion Enterprises, that are running Junos OS Release 19.1R1 and later.
Juniper Networks EX Series Ethernet Switches provide the following hardware and software security features:
Console Port—Allows use of the console port to connect to the Routing Engine through an RJ-45 cable. You then use the command-line interface (CLI) to configure the switch.
Out-of-Band Management—A dedicated management Ethernet port on the rear panel allows out-of-band management.
Software Images—All Junos OS images are signed by Juniper Networks certificate authority (CA) with public key infrastructure (PKI).
User Authentication, Authorization, and Accounting (AAA)—Features include:
User and group accounts with password encryption and authentication.
Access privilege levels configurable for login classes and user templates.
RADIUS authentication, TACACS+ authentication, or both, for authenticating users who attempt to access the switch.
Auditing of configuration changes through system logging or RADIUS/TACACS+.
802.1X Authentication—Provides network access control. Supplicants (hosts) are authenticated when they initially connect to a LAN. Authenticating supplicants before they receive an IP address from a DHCP server prevents unauthorized supplicants from gaining access to the LAN. EX Series switches support Extensible Authentication Protocol (EAP) methods, including EAP-MD5, EAP-TLS, EAP-TTLS, and EAP-PEAP.
Port Security—Access Port security features supported on switching devices are::
DHCP snooping—Filters and blocks ingress Dynamic Host Configuration Protocol (DHCP) server messages on untrusted ports, and builds and maintains a database of DHCP lease information, which is called the DHCP snooping database.
Note:DHCP snooping is not enabled in the default configuration of the switching device. DHCP snooping is enabled on a VLAN or bridge domain. The details of enabling DHCP snooping depend on the particular device.
Trusted DHCP server—Configuring the DHCP server on a trusted port protects against rogue DHCP servers sending leases. You enable this feature on an interface (port). By default, access ports are untrusted, and trunk ports are trusted. (Access ports are the switch ports that connect to Ethernet endpoints such as user PCs and laptops, servers, and printers. Trunk ports are the switch ports that connect an Ethernet switch to other switches or to routers.)
DHCPv6 snooping—DHCP snooping for IPv6.
DHCP option 82—Also known as the DHCP Relay Agent Information option. This DHCPv4 feature helps protect the switching device against attacks such as spoofing of IP addresses and MAC addresses and DHCP IP address starvation. Option 82 provides information about the network location of a DHCP client, and the DHCP server uses this information to implement IP addresses or other parameters for the client.
DHCPv6 option 37—Option 37 is the remote ID option for DHCPv6 and is used to insert information about the network location of the remote host into DHCPv6 packets. You enable option 37 on a VLAN.
Note:DHCPv6 snooping with option 37 is not supported on the MX Series.
DHCPv6 option 18—Option 18 is the circuit ID option for DHCPv6 and is used to insert information about the client port into DHCPv6 packets. This option includes other details that can be optionally configured, such as the prefix and the interface description.
DHCPv6 option 16—Option 16 is the vendor ID option for DHCPv6 and is used to insert information about the vendor of the client hardware into DHCPv6 packets.
Dynamic ARP inspection (DAI)—Prevents Address Resolution Protocol (ARP) spoofing attacks. ARP requests and replies are compared against entries in the DHCP snooping database, and filtering decisions are made on the basis of the results of those comparisons. You enable DAI on a VLAN.
IPv6 neighbor discovery inspection—Prevents IPv6 address spoofing attacks. Neighbor discovery requests and replies are compared against entries in the DHCPv6 snooping database, and filtering decisions are made on the basis of the results of those comparisons. You enable neighbor discovery inspection on a VLAN.
IP source guard—Mitigates the effects of IP address spoofing attacks on the Ethernet LAN. With IP source guard enabled, the source IP address in the packet sent from an untrusted access interface is validated against the DHCP snooping database. If the packet cannot be validated, it is discarded. You enable IP source guard on a VLAN or bridge domain.
IPv6 source guard—IP source guard for IPv6.
MAC limiting—Protects against flooding of the Ethernet switching table (also known as the MAC forwarding table or Layer 2 forwarding table). You can enable MAC limiting on an interface.
MAC move limiting—Tracks MAC movement and detects MAC spoofing on access ports. You enable this feature on a VLAN or bridge domain.
Persistent MAC learning—Also known as sticky MAC. Persistent MAC learning enables interfaces to retain dynamically learned MAC addresses across switch reboots. You enable this feature on an interface.
Unrestricted proxy ARP—The switch responds to all ARP messages with its own MAC address. Hosts that are connected to the switch’s interfaces cannot communicate directly with other hosts. Instead, all communications between hosts go through the switch.
Restricted proxy ARP—The switch does not respond to an ARP request if the physical networks of the source and target of the ARP request are the same. It does not matter whether the destination host has the same IP address as the incoming interface or a different (remote) IP address. An ARP request for a broadcast address elicits no reply.
Device Security—Storm control permits the switch to monitor unknown unicast and broadcast traffic and drop packets, or shut down, or temporarily disable the interface when a specified traffic level is exceeded, thus preventing packets from proliferating and degrading the LAN. You can enable storm control on access interfaces or trunk interfaces.
Encryption Standards—Supported standards include:
128-, 192-, and 256-bit Advanced Encryption Standard (AES)
56-bit Data Encryption Standard (DES) and 168-bit 3DES
See Also
Understanding How to Protect Access Ports from Common Attacks
Port security features can protect the Juniper Networks EX Series and QFX10000 Ethernet Switches against various types of attacks. Protection methods against some common attacks are:
- Mitigation of Ethernet Switching Table Overflow Attacks
- Mitigation of Rogue DHCP Server Attacks
- Protection Against ARP Spoofing Attacks (Does not apply to QFX10000 Series Switches)
- Protection Against DHCP Snooping Database Alteration Attacks (Does not apply to QFX10000 Series Switches)
- Protection Against DHCP Starvation Attacks
Mitigation of Ethernet Switching Table Overflow Attacks
In an overflow attack on the Ethernet switching table, an intruder sends so many requests from new MAC addresses that the table cannot learn all the addresses. When the switch can no longer use information in the table to forward traffic, it is forced to broadcast messages. Traffic flow on the switch is disrupted, and packets are sent to all hosts on the network. In addition to overloading the network with traffic, the attacker might also be able to sniff that broadcast traffic.
To mitigate such attacks, configure both a MAC limit for learned MAC addresses and some specific allowed MAC addresses. Use the MAC limiting feature to control the total number of MAC addresses that can be added to the Ethernet switching table for the specified interface or interfaces. By setting the MAC addresses that are explicitly allowed, you ensure that the addresses of network devices whose network access is critical are guaranteed to be included in the Ethernet switching table. See Example: Protecting against Ethernet Switching Table Overflow Attacks.
You can also configure learned MAC addresses to persist on each interface. Used in combination with a configured MAC limit, this persistent MAC learning helps prevent traffic loss after a restart or an interface-down event and also increases port security by limiting the MAC addresses allowed on the interface.
Mitigation of Rogue DHCP Server Attacks
If an attacker sets up a rogue DHCP server to impersonate a legitimate DHCP server on the LAN, the rogue server can start issuing leases to the network's DHCP clients. The information provided to the clients by this rogue server can disrupt their network access, causing DoS. The rogue server might also assign itself as the default gateway device for the network. The attacker can then sniff the network traffic and perpetrate a man-in-the-middle attack—that is, it misdirects traffic intended for a legitimate network device to a device of its choice.
To mitigate a rogue DHCP server attack, set the interface to which that rogue server is connected as untrusted. That action will block all ingress DHCP server messages from that interface. See Example: Protecting against Rogue DHCP Server Attacks.
The switch logs all DHCP server packets that are received on untrusted ports—for example:
5 untrusted DHCPOFFER received, interface ge-0/0/0.0[65], vlan v1[10] server ip/mac 12.12.12.1/00:00:00:00:01:12 offer ip/client mac 12.12.12.253/00:AA:BB:CC:DD:01
You can use these messages to detect malicious DHCP servers on the network.
For QFX Series switches, including QFX10000, if you attach a DHCP server to an access port, you must configure the port as trusted.
Protection Against ARP Spoofing Attacks (Does not apply to QFX10000 Series Switches)
In ARP spoofing, an attacker sends faked ARP messages on the network. The attacker associates its own MAC address with the IP address of a network device connected to the switch. Any traffic sent to that IP address is instead sent to the attacker. Now the attacker can create various types of mischief, including sniffing the packets that were meant for another host and perpetrating man-in-the middle attacks. (In a man-in-the-middle attack, the attacker intercepts messages between two hosts, reads them, and perhaps alters them, all without the original hosts knowing that their communications have been compromised. )
To protect against ARP spoofing on your switch, enable both DHCP snooping and dynamic ARP inspection (DAI). DHCP snooping builds and maintains the DHCP snooping table. That table contains the MAC addresses, IP addresses, lease times, binding types, VLAN information, and interface information for the untrusted interfaces on the switch. DAI uses the information in the DHCP snooping table to validate ARP packets. Invalid ARP packets are blocked and, when they are blocked, a system log message is recorded that includes the type of ARP packet and the sender’s IP address and MAC address.
Protection Against DHCP Snooping Database Alteration Attacks (Does not apply to QFX10000 Series Switches)
In an attack designed to alter the DHCP snooping database, an intruder introduces a DHCP client on one of the switch's untrusted access interfaces that has a MAC address identical to that of a client on another untrusted port. The intruder acquires the DHCP lease, which results in changes to the entries in the DHCP snooping table. Subsequently, what would have been valid ARP requests from the legitimate client are blocked.
To protect against this type of alteration of the DHCP snooping database, configure MAC addresses that are explicitly allowed on the interface. See Example: Protecting Against DHCP Snooping Database Attacks.
Protection Against DHCP Starvation Attacks
In a DHCP starvation attack, an attacker floods an Ethernet LAN with DHCP requests from spoofed (counterfeit) MAC addresses so that the switch's trusted DHCP servers cannot keep up with requests from legitimate DHCP clients on the switch. The address space of those servers is completely used up, so they can no longer assign IP addresses and lease times to clients. DHCP requests from those clients are either dropped—that is, the result is a denial of service (DoS)—or directed to a rogue DHCP server set up by the attacker to impersonate a legitimate DHCP server on the LAN.
To protect the switch from DHCP starvation attacks, use the MAC limiting feature. Specify the maximum number of MAC addresses that the switch can learn on the access interfaces to which those clients connect. The switch's DHCP server or servers will then be able to supply the specified number of IP addresses and leases to those clients and no more. If a DHCP starvation attack occurs after the maximum number of IP addresses has been assigned, the attack will fail. See Example: Protecting against DHCP Starvation Attacks.
For additional protection on EX Series switches, you can configure learned MAC addresses on each interface to persist across restarts of the switch by enabling persistent MAC learning. This persistent MAC learning both helps to prevent traffic loss after a restart and ensures that even after a restart or an interface-down event, the persistent MAC addresses are re-entered into the forwarding database rather than the switch learning new MAC addresses.
See Also
Configuring Port Security (ELS)
The features described are supported on EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Configuring Port Security (non-ELS). For ELS details, see Using the Enhanced Layer 2 Software CLI.
Ethernet LANs are vulnerable to attacks such as address spoofing and Layer 2 denial of service (DoS) on network devices. DHCP port security features help protect the access ports on the switch against the losses of information and productivity that can result from such attacks.
The following port security features are supported for DHCPv4:
DHCP snooping
Dynamic ARP inspection (DAI)
IP source guard
DHCP option 82
The following port security features are supported for DHCPv6:
DHCPv6 snooping
IPv6 Neighbor discovery inspection
IPv6 source guard
DHCPv6 option 37, option 18 and option 16
DHCP snooping and DHCPv6 snooping are
disabled by default on any VLAN. No explicit CLI configuration is used to enable DHCP snooping
or DHCPv6 snooping. When you configure any of the port security features for a VLAN at the [edit vlans vlan-name forwarding-options dhcp-security] hierarchy
level, DHCP snooping and DHCPv6 snooping are automatically enabled on that VLAN.
Starting in Junos
OS Release 14.1X53-D47 and 15.1R6, you can enable DHCP snooping or DHCPv6 snooping on a VLAN
without configuring other port security features by configuring the dhcp-security CLI statement at the [edit vlans vlan-name forwarding-options] hierarchy level.
DAI, IPv6 neighbor discovery inspection, IP source guard, IPv6 source guard, DHCP option 82 and DHCPv6 options are configured per VLAN. You must configure a VLAN before configuring these DHCP port security features. See Configuring VLANs for EX Series Switches with ELS Support (CLI Procedure).
The DHCP port security features that you specify for the VLAN apply to all the interfaces
included within that VLAN. However, you can assign different attributes to an access interface
or a group of access interfaces within the VLAN. The access interface or interfaces must first
be configured as a group using the group statement at the [edit vlans vlan-name forwarding-options
dhcp-security] hierarchy level. A group must have at least one interface.
Configuring a group of access interfaces
on a VLAN at the [edit vlans vlan-name forwarding-options dhcp-security] hierarchy level automatically enables DHCP snooping for all interfaces in the VLAN.
Attributes that can be specified for access interfaces using the group statement
are:
Specifying that the interface have a static IP-MAC address (
static-ip or static-ipv6)Specifying an access interface to act as a trusted interface to a DHCP server (
trusted)Specifying an interface not to transmit DHCP option 82 (
no-option82) or DHCPv6 options (no-option37)
Trunk interfaces are trusted by default. However, you can override this default
behavior and set a trunk interface as untrusted.
For additional details, see:
You can override the general port security settings for the VLAN by configuring a group of access interfaces within that VLAN. For details, see:
See Also
Configuring Port Security (non-ELS)
Ethernet LANs are vulnerable to attacks such as address spoofing and Layer 2 denial of service (DoS) on network devices. Port security features such as DHCP snooping, DAI (dynamic ARP inspection), MAC limiting, MAC move limiting, and persistent MAC learning, as well as trusted DHCP server, help protect the access ports on the switch against the loss of information and productivity that such attacks can cause.
Depending on the particular feature, you can configure the port security feature either on:
VLANs—A specific VLAN or all VLANs
Interfaces—A specific interface or all interfaces
If you configure one of the port security features on all VLANs or all interfaces, the switch software enables that port security feature on all VLANs and all interfaces that are not explicitly configured with other port security features.
However, if you do explicitly configure one of the port security features on a specific VLAN or on a specific interface, you must explicitly configure any additional port security features that you want to apply to that VLAN or interface. Otherwise, the switch software automatically applies the default values for the feature.
For example, if you disable DHCP snooping on all VLANs and decide to explicitly enable IP source guard only on a specific VLAN, you must also explicitly enable DHCP snooping on that specific VLAN. Otherwise, the default value of no DHCP snooping applies to that VLAN.
To configure port security features by using the CLI:
- Enabling DHCP Snooping
- Enabling Dynamic ARP Inspection (DAI)
- Enabling IPv6 Neighbor Discovery Inspection
- Limiting Dynamic MAC Addresses on an Interface
- Enabling Persistent MAC Learning on an Interface
- Limiting MAC Address Movement
- Restricting a VoIP Client MAC Address in a VoIP VLAN
- Configuring Trusted DHCP Servers on an Interface
Enabling DHCP Snooping
You can configure DHCP snooping to enable the device to monitor DHCP messages received, ensure that hosts use only the IP addresses that are assigned to them, and allow access only to authorized DHCP servers.
To enable DHCP snooping:
On a specific VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan vlan-name examine-dhcp
On all VLANs:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan all examine-dhcp
To enable DHCPv6 snooping:
On a specific VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan vlan-name examine-dhcpv6
On all VLANs:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan all examine-dhcpv6
Enabling Dynamic ARP Inspection (DAI)
You can enable DAI to protect against ARP snooping. To enable DAI:
On a single VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan vlan-name arp-inspection
On all VLANs:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan all arp-inspection
Enabling IPv6 Neighbor Discovery Inspection
You can enable neighbor discovery inspection to protect against IPv6 address spoofing.
To enable neighbor discovery on a single VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan vlan-name neighbor-discovery-inspection
To enable neighbor discovery on all VLANs:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan all neighbor-discovery-inspection
Limiting Dynamic MAC Addresses on an Interface
Limit the number of dynamic MAC addresses allowed on an interface and specify the action to take if the limit is exceeded:
On a single interface:
[edit ethernet-switching-options secure-access-port] user@switch# set interface interface-name mac-limit limit action action
On all interfaces:
[edit ethernet-switching-options secure-access-port] user@switch# set interface all mac-limit limit action action
Enabling Persistent MAC Learning on an Interface
You can configure learned MAC addresses to persist on an interface across restarts of the switch:
[edit ethernet-switching-options secure-access-port] user@switch# set interface interface-name persistent-learning
Limiting MAC Address Movement
You can limit the number of times a MAC address can move from its original interface in 1 second:
On a single VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan vlan-name mac-move-limit limit action action
On all VLANs:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan all mac-move-limit limit action action
Restricting a VoIP Client MAC Address in a VoIP VLAN
To restrict a VoIP client MAC address from being learned in a configured VoIP VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set interfaceinterface-name voip-mac-exlusive
Any MAC address learned on that interface for the VoIP VLAN is not learned on a data VLAN with that same interface. If a MAC address has been learned on a data VLAN interface and then the MAC address is learned on a VoIP VLAN with that same interface, the MAC address is removed from the data VLAN interface.
Configuring Trusted DHCP Servers on an Interface
Configure a trusted DHCP server on an interface:
[edit ethernet-switching-options secure-access-port] user@switch# set interface interface-name dhcp-trusted
Example: Configuring Port Security (non-ELS)
You can configure DHCP snooping, dynamic ARP inspection (DAI), MAC limiting, persistent MAC learning, and MAC move limiting on the untrusted ports of switches to protect the switches and the Ethernet LAN against address spoofing and Layer 2 denial-of-service (DoS) attacks. You can also configure a trusted DHCP server and specific (allowed) MAC addresses for the switch interfaces.
The switches used in this example do not support the ELS configuration style. For information on configuring port security on ELS switches, see Configuring Port Security (ELS).
This example describes how to configure basic port security features on a switch:
Requirements
This example uses the following hardware and software components:
One EX Series or QFX Series.
Junos OS Release 11.4 or later for EX Series switches or Junos OS Release 12.1 or later for the QFX Series
A DHCP server to provide IP addresses to network devices on the switch
Before you configure basic port security features, be sure you have:
Connected the DHCP server to the switch.
Configured a VLAN on the switch. See the task for your platform:
In this example, the DHCP server and its clients are all members of a single VLAN on the switch.
Overview and Topology
Ethernet LANs are vulnerable to address spoofing and DoS attacks on network devices. To protect the devices from such attacks, you can configure:
DHCP snooping to validate DHCP server messages
DAI to protect against MAC spoofing
MAC limiting to constrain the number of MAC addresses the switch adds to its MAC address cache
MAC move limiting to help prevent MAC spoofing
Persistent MAC learning (sticky MAC) to constrain the MAC addresses that can be learned on an interface to the first ones learned, even after a reboot of the switch
Trusted DHCP server configured on a trusted port to protect against rogue DHCP servers sending leases
This example shows how to configure these security features on a switch connected to a DHCP server.
The setup for this example includes the VLAN employee-vlan on the switch. Figure 1 illustrates the topology for this example.
Topology
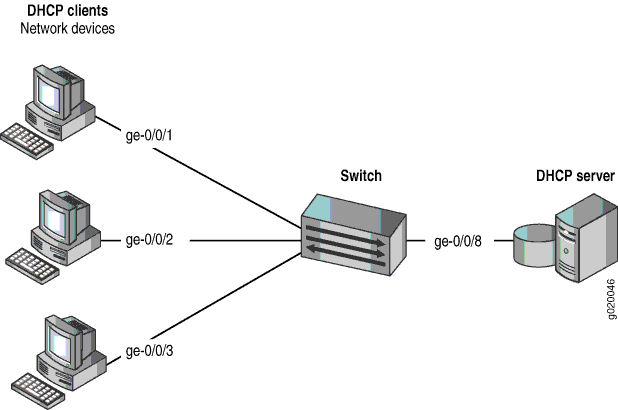
The components of the topology for this example are shown in Table 1.
| Properties | Settings |
|---|---|
Switch hardware |
One EX Series or QFX series switch |
VLAN name and ID |
employee-vlan, tag 20 |
VLAN subnets |
192.0.2.16/28 192.0.2.17 through 192.0.2.30 192.0.2.31 is subnet's broadcast address |
Interfaces in employee-vlan |
ge-0/0/1, ge-0/0/2, ge-0/0/3, ge-0/0/8 |
Interface for DHCP server |
ge-0/0/8 |
In this example, the switch is initially configured with the default port security setup. In the default switch configuration:
Secure port access is activated on the switch.
DHCP snooping and DAI are disabled on all VLANs.
All access ports are untrusted, and all trunk ports are trusted for DHCP snooping.
In the configuration tasks for this example, you set the DHCP server as trusted; you enable DHCP snooping, DAI, and MAC move limiting on a VLAN; you set a value for a MAC limit on some interfaces; you configure some specific (allowed) MAC addresses on an interface; and you configure persistent MAC learning on an interface.
Configuration
To configure basic port security on a switch whose DHCP server and client ports are in a single VLAN:
Procedure
CLI Quick Configuration
To quickly configure basic port security on the switch, copy the following commands and paste them into the switch terminal window:
[edit ethernet-switching-options secure-access-port] set interface ge-0/0/1 mac-limit 4 set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:80 set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:81 set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:83 set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:85 set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:88 set interface ge-0/0/2 mac-limit 4 set interface ge-0/0/1 persistent-learning set interface ge-0/0/8 dhcp-trusted set vlan employee-vlan arp-inspection set vlan employee-vlan examine-dhcp set vlan employee-vlan mac-move-limit 5
Step-by-Step Procedure
Configure basic port security on the switch:
Enable DHCP snooping on the VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan employee-vlan examine-dhcp
Specify the interface (port) from which DHCP responses are allowed:
[edit ethernet-switching-options secure-access-port] user@switch# set interface ge-0/0/8 dhcp-trusted
Enable dynamic ARP inspection (DAI) on the VLAN:
[edit ethernet-switching-options secure-access-port] user@switch# set vlan employee-vlan arp-inspection
Configure a MAC limit of 4 and use the default action, drop. (Packets are dropped, and the MAC address is not added to the Ethernet switching table if the MAC limit is exceeded on the interfaces):
[edit ethernet-switching-options secure-access-port] user@switch# set interface ge-0/0/1 mac-limit 4 user@switch# set interface ge-0/0/2 mac-limit 4
Allow learned MAC addresses for a particular interface to persist across restarts of the switch and interface-down events by enabling persistent MAC learning:
[edit ethernet-switching-options secure-access-port] user@switch# set interface ge-0/0/1 persistent-learning
Configure a MAC move limit of 5 and use the default action, drop. (Packets are dropped, and the MAC address is not added to the Ethernet switching table if a MAC address has exceeded the MAC move limit):
[edit ethernet-switching-options secure-access-port] user@switch# set vlan employee-vlan mac-move-limit 5
Configure allowed MAC addresses:
[edit ethernet-switching-options secure-access-port] user@switch# set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:80 user@switch# set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:81 user@switch# set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:83 user@switch# set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:85 user@switch# set interface ge-0/0/2 allowed-mac 00:05:85:3A:82:88
Results
Check the results of the configuration:
[edit ethernet-switching-options secure-access-port]
user@switch# show
interface ge-0/0/1.0 {
mac-limit 4;
persistent-learning;
}
interface ge-0/0/2.0 {
allowed-mac [ 00:05:85:3a:82:80 00:05:85:3a:82:81 00:05:85:3a:82:83 00:05:85:3a:82:85 00:05:85:3a:82:88 ];
mac-limit 4;
}
interface ge-0/0/8.0 {
dhcp-trusted;
}
vlan employee-vlan {
arp-inspection
examine-dhcp;
mac-move-limit 5;
}
Verification
To confirm that the configuration is working properly:
- Verifying That DHCP Snooping Is Working Correctly on the Switch
- Verifying That DAI Is Working Correctly on the Switch
- Verifying That MAC Limiting, MAC Move Limiting, and Persistent MAC Learning Are Working Correctly on the Switch
- Verifying That Allowed MAC Addresses Are Working Correctly on the Switch
Verifying That DHCP Snooping Is Working Correctly on the Switch
Purpose
Verify that DHCP snooping is working on the switch.
Action
Send some DHCP requests from network devices (here they are DHCP clients) connected to the switch.
Display the DHCP snooping information when the interface on which the DHCP server connects to the switch is trusted. The following output results when requests are sent from the MAC addresses and the server has provided the IP addresses and leases:
user@switch> show dhcp snooping binding DHCP Snooping Information: MAC Address IP Address Lease Type VLAN Interface ----------------- ---------- ----- ---- ---- --------- 00:05:85:3A:82:77 192.0.2.17 600 dynamic employee—vlan ge-0/0/1.0 00:05:85:3A:82:79 192.0.2.18 653 dynamic employee—vlan ge-0/0/1.0 00:05:85:3A:82:80 192.0.2.19 720 dynamic employee—vlan ge-0/0/2.0 00:05:85:3A:82:81 192.0.2.20 932 dynamic employee—vlan ge-0/0/2.0 00:05:85:3A:82:83 192.0.2.21 1230 dynamic employee—vlan ge-0/0/2.0 00:05:85:27:32:88 192.0.2.22 3200 dynamic employee—vlan ge-0/0/2.0
Meaning
When the interface on which the DHCP server connects to the switch has been set to trusted, the output (see preceding sample) shows, for each MAC address, the assigned IP address and lease time—that is, the time, in seconds, remaining before the lease expires.
If the DHCP server had been configured as untrusted, no entries would be added to the
DHCP snooping database, and nothing would be shown in the output of the show dhcp snooping
binding command.
Verifying That DAI Is Working Correctly on the Switch
Purpose
Verify that DAI is working on the switch.
Action
Send some ARP requests from network devices connected to the switch.
Display the DAI information:
user@switch> show arp inspection statistics ARP inspection statistics: Interface Packets received ARP inspection pass ARP inspection failed --------------- --------------- -------------------- --------------------- ge-0/0/1.0 7 5 2 ge-0/0/2.0 10 10 0 ge-0/0/3.0 12 12 0
Meaning
The sample output shows the number of ARP packets received and inspected per interface, with a listing of how many packets passed and how many failed the inspection on each interface. The switch compares the ARP requests and replies against the entries in the DHCP snooping database. If a MAC address or IP address in the ARP packet does not match a valid entry in the database, the packet is dropped.
Verifying That MAC Limiting, MAC Move Limiting, and Persistent MAC Learning Are Working Correctly on the Switch
Purpose
Verify that MAC limiting, MAC move limiting, and persistent MAC learning are working on the switch.
Action
Suppose that two packets have been sent from hosts on ge-0/0/1 and five packets from hosts on ge-0/0/2, with both interfaces set to a MAC limit of 4 with the default action drop and ge-0/0/1 enabled for persistent MAC learning.
Display the MAC addresses learned:
user@switch> show ethernet-switching table Ethernet-switching table: 7 entries, 4 learned, 2 persistent entries VLAN MAC address Type Age Interfaces employee-vlan * Flood - All-members employee-vlan 00:05:85:3A:82:77 Persistent 0 ge-0/0/1.0 employee-vlan 00:05:85:3A:82:79 Persistent 0 ge-0/0/1.0 employee-vlan 00:05:85:3A:82:80 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:81 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:83 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:85 Learn 0 ge-0/0/2.0
Now suppose packets have been sent from two of the hosts on ge-0/0/2 after they have been moved to other interfaces more than five times in 1 second, with employee-vlan set to a MAC move limit of 5 with the default action drop.
Display the MAC addresses in the table:
user@switch> show ethernet-switching table
Ethernet-switching table: 7 entries, 2 learned, 2 persistent entries VLAN MAC address Type Age Interfaces employee-vlan * Flood - All-members employee-vlan 00:05:85:3A:82:77 Persistent 0 ge-0/0/1.0 employee-vlan 00:05:85:3A:82:79 Persistent 0 ge-0/0/1.0 employee-vlan 00:05:85:3A:82:80 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:81 Learn 0 ge-0/0/2.0 employee-vlan * Flood - ge-0/0/2.0 employee-vlan * Flood - ge-0/0/2.0
Meaning
The first sample output shows that with a MAC limit of 4 for each interface, the fifth MAC address on ge-0/0/2 was not learned because it exceeded the MAC limit. The second sample output shows that MAC addresses for three of the hosts on ge-/0/0/2 were not learned, because the hosts had been moved back more than five times in 1 second.
Interface ge-0/0/1.0 was enabled for persistent MAC learning, so the MAC addresses associated with this interface are of the type persistent.
Verifying That Allowed MAC Addresses Are Working Correctly on the Switch
Purpose
Verify that allowed MAC addresses are working on the switch.
Action
Display the MAC cache information after five allowed MAC addresses have been configured on interface ge-0/0/2:
user@switch> show ethernet-switching table Ethernet-switching table: 5 entries, 4 learned VLAN MAC address Type Age Interfaces employee-vlan 00:05:85:3A:82:80 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:81 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:83 Learn 0 ge-0/0/2.0 employee-vlan 00:05:85:3A:82:85 Learn 0 ge-0/0/2.0 employee-vlan * Flood - ge-0/0/2.0
Meaning
Because the MAC limit value for this interface has been set to 4, only four of the five configured allowed addresses are learned.
