IPsec Tunnel Traffic Configuration
IPsec Tunnel Traffic Configuration Overview
Traffic configuration defines the traffic that must flow through the IPsec tunnel. You configure outbound and inbound firewall filters, which identify and direct traffic to be encrypted and confirm that decrypted traffic parameters match those defined for the given tunnel. The outbound filter is applied to the LAN or WAN interface for the incoming traffic you want to encrypt off of that LAN or WAN. The inbound filter is applied to the ES PIC to check the policy for traffic coming in from the remote host. Because of the complexity of configuring a router to forward packets, no automatic checking is done to ensure that the configuration is correct. Make sure that you configure the router very carefully.
The valid firewall filters statements for IPsec are destination-port, source-port, protocol, destination-address, and source-address.
In Figure 1, Gateway A protects the network 10.1.1.0/24, and Gateway B protects the network 10.2.2.0/24. The gateways are connected by an IPsec tunnel.
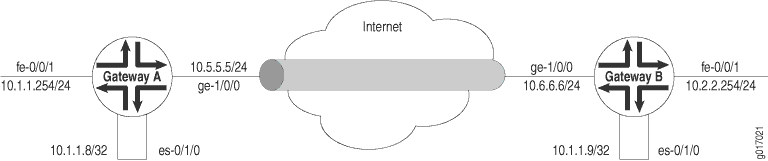
The SA and ES interfaces for Gateway A are configured as follows:
[edit security ipsec]
security-association manual-sa1 {
manual {
direction bidirectional {
protocol esp;
spi 2312;
authentication {
algorithm hmac-md5-96;
key ascii-text 1234123412341234;
}
encryption {
algorithm 3des-cbc;
key ascii-text 123456789009876543211234;
}
}
}
}
[edit interfaces es-0/1/0]
unit 0 {
tunnel {
source 10.5.5.5;
destination 10.6.6.6;
}
family inet {
ipsec-sa manual-sa1;
address 10.1.1.8/32 {
destination 10.1.1.9;
}
}
}
The SA and ES interfaces for Gateway B are configured as follows:
[edit security ipsec]
security-association manual-sa1 {
manual {
direction bidirectional {
protocol esp;
spi 2312;
authentication {
algorithm hmac-md5-96;
key ascii-text 1234123412341234;
}
encryption {
algorithm 3des-cbc;
key ascii-text 123456789009876543211234;
}
}
}
}
[edit interfaces es-0/1/0]
unit 0 {
tunnel {
source 10.6.6.6;
destination 10.5.5.5;
}
family inet {
ipsec-sa manual-sa1;
address 10.1.1.9/32; {
destination 10.1.1.8;
}
}
}
See Also
Example: Configuring an Outbound Traffic Filter
Firewall filters for outbound traffic direct the traffic through the desired IPsec tunnel and ensure that the tunneled traffic goes out the appropriate interface (see IPsec Tunnel Traffic Configuration Overview). Here, an outbound firewall filter is created on security Gateway A; it identifies the traffic to be encrypted and adds it to the input side of the interface that carries the internal VPN traffic:
[edit firewall]
filter ipsec-encrypt-policy-filter {
term term1 {
from {
source-address { # local network
10.1.1.0/24;
}
destination-address { # remote network
10.2.2.0/24;
}
}
then ipsec-sa manual-sa1; # apply SA name to packet
term default {
then accept;
}
The source address, port, and protocol on the outbound traffic filter must match the destination address, port, and protocol on the inbound traffic filter. The destination address, port, and protocol on the outbound traffic filter must match the source address, port, and protocol on the inbound traffic filter.
See Also
Example: Applying an Outbound Traffic Filter
After you have configured the outbound firewall filter, you apply it:
[edit interfaces]
fe-0/0/1 {
unit 0 {
family inet {
filter {
input ipsec-encrypt-policy-filter;
}
address 10.1.1.254/24;
}
}
}
The outbound filter is applied on the Fast Ethernet interface at the [edit interfaces fe-0/0/1 unit 0 family inet] hierarchy level. Any packet matching
the IPsec action term (term 1) on the input filter (ipsec-encrypt-policy-filter), configured on the Fast Ethernet interface, is directed to the ES PIC interface at the [edit interfaces es-0/1/0 unit 0 family inet] hierarchy level. If a packet arrives
from the source address 10.1.1.0/24 and goes to the destination address 10.2.2.0/24, the Packet
Forwarding Engine directs the packet to the ES PIC interface, which is configured with the manual-sa1 SA. The ES PIC receives the packet, applies the manual-sa1 SA,
and sends the packet through the tunnel.
The router must have a route to the tunnel endpoint; add a static route if necessary.
See Also
Example: Configuring an Inbound Traffic Filter for a Policy Check
Requirements
No special configuration beyond device initialization is required before configuring this example.
Overview
Here, an inbound firewall filter, which performs the final IPsec policy
check, is created on security Gateway A. This check ensures that only packets that match the
traffic configured for this tunnel are accepted. This filter is configured via the CLI interface
at the [edit firewall family inet] hierarchy level.
Configuration
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode.
To configure this example, perform the following tasks:
CLI Quick Configuration
To quickly configure this example, copy the following configuration commands
into a text file, remove any line breaks, and then paste the commands into the CLI at the [edit] hierarchy level.
[edit] set firewall family inet filter ipsec-decrypt-policy-filter term term1 from source-address 10.2.2.0/24 set firewall family inet filter ipsec-decrypt-policy-filter term term1 from destination-address 10.1.1.0/24 set firewall family inet filter ipsec-decrypt-policy-filter term term1 then accept commit
Configuring the firewall filter
Step-by-Step Procedure
To configure the firewall filter, ipsec-decrypt-policy-filter that
catches traffic from the remote 10.2.2.0/24 netowrk that is destined for the local 10.1.1.0/24 network:
Create the firewall filter:
[edit] user@host# edit firewall family inet filter ipsec-decrypt-policy-filter
Configure matching for source and destination addresses:
[edit firewall family inet filter ipsec-decrypt-policy-filter] user@host# set term term1 from source-address 10.2.2.0/24 user@host# set term term1 from destination-address 10.1.1.0/24
Configure the filter to accept the matched traffic:
[edit firewall family inet filter ipsec-decrypt-policy-filter] user@host# set term term1 then accept
Note:The accept statement within the
term term1is for this filter only. Traffic that does not match this filter term will be dropped by the default firewall action.Confirm your candidate firewall configuration by issuing the
showconfiguration command at the[edit firewall family inet]hierarchy level[edit firewall family inet] user@host# show filter ipsec-decrypt-policy-filter { term term1 { # perform policy check from { source-address { # remote network 10.2.2.0/24; } destination-address { # local network 10.1.1.0/24; } } then accept; } }If the command output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
If you are done configuring the device, commit your candidate configuration.
[edit] user@host# commit
To implement this filter, you apply it as an input filter to the
es-0/1/0logical interface of Gateway A. See Example: Applying an Inbound Traffic Filter to an ES PIC for a Policy Check for details.
Example: Applying an Inbound Traffic Filter to an ES PIC for a Policy Check
After you create the inbound firewall filter, apply it to the ES PIC. Here,
the inbound firewall filter (ipsec-decrypt-policy-filter) is applied on the decrypted
packet to perform the final policy check. The IPsec manual-sa1 SA is referenced
at the [edit interfaces es-1/2/0 unit 0 family inet] hierarchy level and decrypts
the incoming packet.
[edit interfaces]
es-1/2/0 {
unit 0 {
tunnel {
source 10.5.5.5; # tunnel source address
destination 10.6.6.6; # tunnel destination address
}
family inet {
filter {
input ipsec-decrypt-policy-filter;
}
ipsec-sa manual-sa1; # SA name applied to packet
address 10.1.1.8/32 { # local interface address inside local VPN
destination 10.2.2.254; # destination address inside remote VPN
}
}
}
The Packet Forwarding Engine directs IPsec packets to the ES PIC. It uses
the packet’s SPI, protocol, and destination address to look up the SA configured on
one of the ES interfaces. The IPsec manual-sa1 SA is referenced at the [edit
interfaces es-1/2/0 unit 0 family inet] hierarchy level and is used to decrypt the incoming
packet. When the packets are processed (decrypted, authenticated, or both), the input firewall
filter (ipsec-decrypt-policy-filter) is applied on the decrypted packet to perform
the final policy check. Term1 defines the decrypted (and verified) traffic and performs the
required policy check.
The inbound traffic filter is applied after the ES PIC has processed the packet, so the decrypted traffic is defined as any traffic that the remote gateway is encrypting and sending to this router. IKE uses this filter to determine the policy required for a tunnel. This policy is used during the negotiation with the remote gateway to find the matching SA configuration.
See Also
ES Tunnel Interface Configuration for a Layer 3 VPN
To configure an ES tunnel interface for a Layer 3 VPN, you need to configure an ES tunnel interface on the provider edge (PE) router and on the customer edge (CE) router. You also need to configure IPsec on the PE and CE routers.
