Group-Based Policies in VXLAN Environments
Overview
Integrating Group-Based Policy (GBP) with Virtual Extensible LAN (VXLAN) architecture facilitates advanced microsegmentation within your networking environment. This functionality empowers you to enforce tag-based policies where policies are driven by business-centric tags rather than traditional network topology constraints.
By configuring source tag and destination tag match options, you gain granular control over network access, allowing for sophisticated traffic management. The system leverages reserved fields in the VXLAN header to apply policies across network segments, ensuring flexible traffic isolation and enhanced access control through Endpoint Groups (EPGs). You can manage group tags using various identifiers like MAC addresses, VLANs, RADIUS server assignments, or controllers, offering adaptable tag management.
SRX Series support tag-based match conditions in security policies to enforce micro-segmentation. GBP tag assignment is not supported in SRX Series firewalls.
Juniper switches have supported the group-based policy model ( (EVPN-VXLAN Group-Based Policies) and micro-segmentations, and now the SRX Series Firewall extend this functionality by incorporating GBP into its security policies. We recommend you to read Micro and Macro Segmentation using Group Based Policy in a VXLAN before you proceed with this topic.
For the complete list of supported features and platforms, see EVPN-VXLAN group-based policies in Feature Explorer.
Key Features
-
Endpoint Grouping: Devices and users are categorized into logical groups based on their roles, functions, or security requirements, regardless of their physical location in the VXLAN fabric.
-
Policy Definition: Security policies are defined between these groups, specifying allowed interactions, which are then enforced across the VXLAN overlay.
-
Consistent Policy Application: Policies are consistently applied regardless of the physical location of devices within the network, a key benefit in VXLAN's location-independent architecture.
-
Scalability: As new devices are added to a group, they automatically inherit the group's security policies, aligning well with VXLAN's ability to scale across large data center networks
- Benefits of Integrating GBP with VXLAN
- Introduction
- What is Microsegmentation with GBP?
- Group Tag Assignment
- VXLAN Header for GBP
- Group Tag Transfer in Inter-VXLAN Networks
- Inter-Site or External Communication
- Configuration of Group Based Policies
Benefits of Integrating GBP with VXLAN
-
Improve operational efficiency by simplifying the configuration process by allowing you to implement consistent security policies across enterprise network domains.
-
Enhance network security by allowing granular control over access based on business-centric tags, reducing the risk associated with unauthorized access.
-
Facilitate efficient traffic management by enabling microsegmentation, which isolates network segments and controls interactions between distinct EPGs.
-
Support dynamic policy adjustments, making it easier to adapt to changing business requirements without needing to redesign network topology.
-
Provide flexibility in tag management through various identifiers, allowing seamless integration with existing infrastructure and simplifying the implementation of policies.
Introduction
In the context of EVPN VXLAN, especially when implementing microsegmentation, the following terms are fundamental to understanding how traffic is classified, controlled, and segmented across the network.
- Endpoint Group (EPG) is a logical grouping of endpoints (like VMs, containers, or bare-metal hosts) that share common policy requirements. These groups are used to define which endpoints can communicate with each other. based on attributes like IP subnet, VLAN, VXLAN VNID, or tags. These groups are used to apply consistent security policies across dynamic workloads.
- Group-Based Policy (GBP) is a policy model that defines how traffic flows between different EPGs. These policies can control communication between endpoint groups based on identity, not just IP or port.
- Scalable Group Tags (SGTs) are 16-bit metadata identifiers assigned to endpoints—such as virtual machines, containers, or hosts—to indicate their group membership. The term GBP tag is a broader reference to the use of these identifiers for enforcing group-based policies across the network. In this document, we use the term GBP tags to refer to these identifiers
What is Microsegmentation with GBP?
Microsegmentation allocates users, servers, VMs, and devices to endpoint groups and defines group-based policies between endpoint groups to manage traffic control between endpoints.
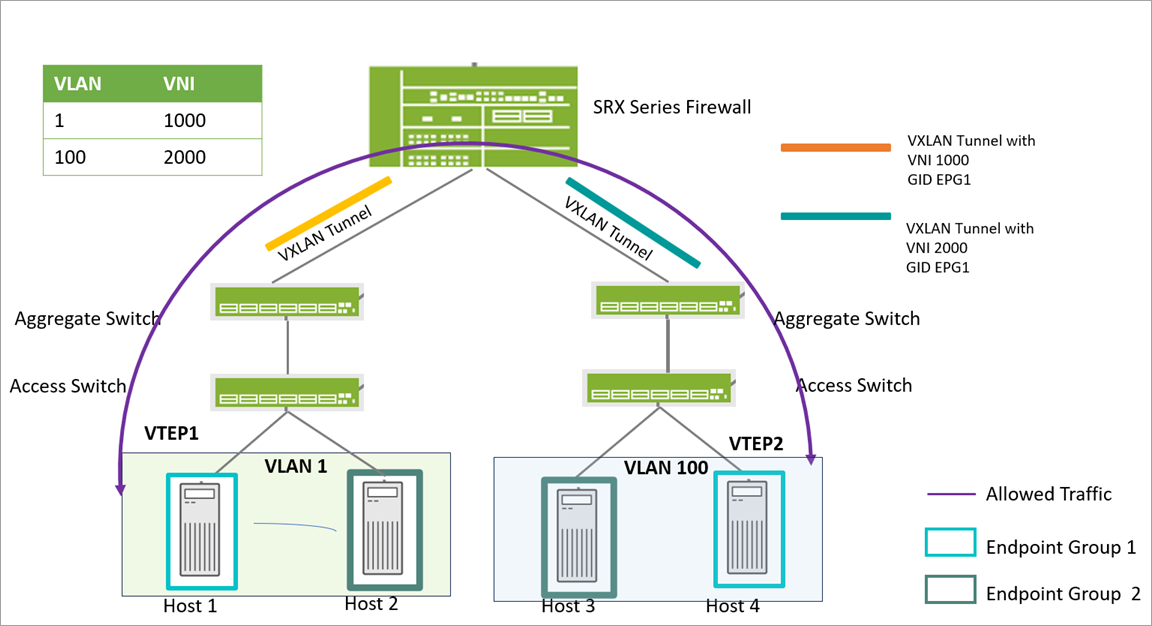
Following image shows a portion of VXLAN topology.

In this illustration, SRX Firewall at the spine layer acts as centralized security and policy enforcement. Four Hosts (Host1, Host2, Host3, Host4) connected to the access switches. These four hosts belongs to the same VLAN/subnet. For example, assume that the requirements are as follows:
- Host1 and Host4 can communicate,
- Host2 and Host3 can communicate.
- Host1 and Host4 must not communicate with Host2 and Host3.
To address this requirement, hosts grouped into endpoint groups (EPG1 and EPG2) as follows:
- Host1 (on Switch1) and Host4 (on Switch2) are added to endpoint group 1(EPG1).
- Host2 (on Switch 1) and Host3 (on Switch2) are added to endpoint group 2(EPG2).
Once the endpoints are grouped, intra group access and isolation or inter group access or isolation can be defined. That is, both the access switches are configured with a policy that if source group is EPG1 and destination group is EPG2, deny the traffic and vice-a-versa. Similarly, another set of policies are created that if source group and destination group are same, allow the traffic. As a result:
- Communication between Host2 and Host3 is allowed as both are part of EPG2.
- Communication between Host1 and Host4 is allowed as both are part of EPG1.
- Communication between Host1 and Host2/Host 4 is not allowed as hosts are in different EPGs.
- Communication between Host3 and Host4/Host 2 is not allowed as hosts are in different EPGs..
Group Tag Assignment
GBP uses tags to mark traffic and to enforce policy. The assignment process involves mapping each endpoint to a specific tag based on its business function, which is then utilized in the policy lookup process to enforce the desired communication patterns. In campus networks, tags can be assigned to endpoints in one of the following methods.
-
GBP tags—Tags based on various matches on the ingress interface including:
- MAC address
- Port
- VLAN
- Port, VLAN
- Subnet/IP Address
- RADIUS server assigned tags—Network environments using RADIUS servers for network access control. Endpoints are placed in VLANs based on the type of endpoint or the user authorization and device fingerprinting. RADIUS server send the group tag in Juniper VSA. The ingress access switch can associate the group tag sent by the RADIUS server to all traffic generated by that MAC address.
- Controller assigned tags—Network environments managed by a controller like Juniper Apstra Fabric Conductor, tags are assigned to switch ports or endpoints connected to switch ports. Switch can associate the tag to all traffic from these endpoints.
How GBP Tags Work?
- Each endpoint—such as a VM, container, or host—is dynamically assigned a GBP tag based on its role or function (e.g., web server, database server, admin workstation).
- The GBP tag is propagated along with the traffic, either embedded in the VXLAN header or carried as metadata, ensuring that group identity travels with the packet.
- SRX Series Firewalls, or other policy enforcement points inspect the GBP tag to determine how traffic should be handled according to defined group-based policies.
- Security policies are applied by matching source GBP tags and destination GBP tags, allowing enforcement decisions to be made based on group relationships rather than IP addresses or network topology
This approach enables organizations to enforce policies that reflect business logic and organizational structure, rather than being constrained by static network constructs like VLANs or subnets.
VXLAN Header for GBP
VXLAN-GBP leverages reserved fields in the VXLAN header to carry the GBP tags assigned to the frame. Following figure is an example of 16-bit Group Policy ID field .
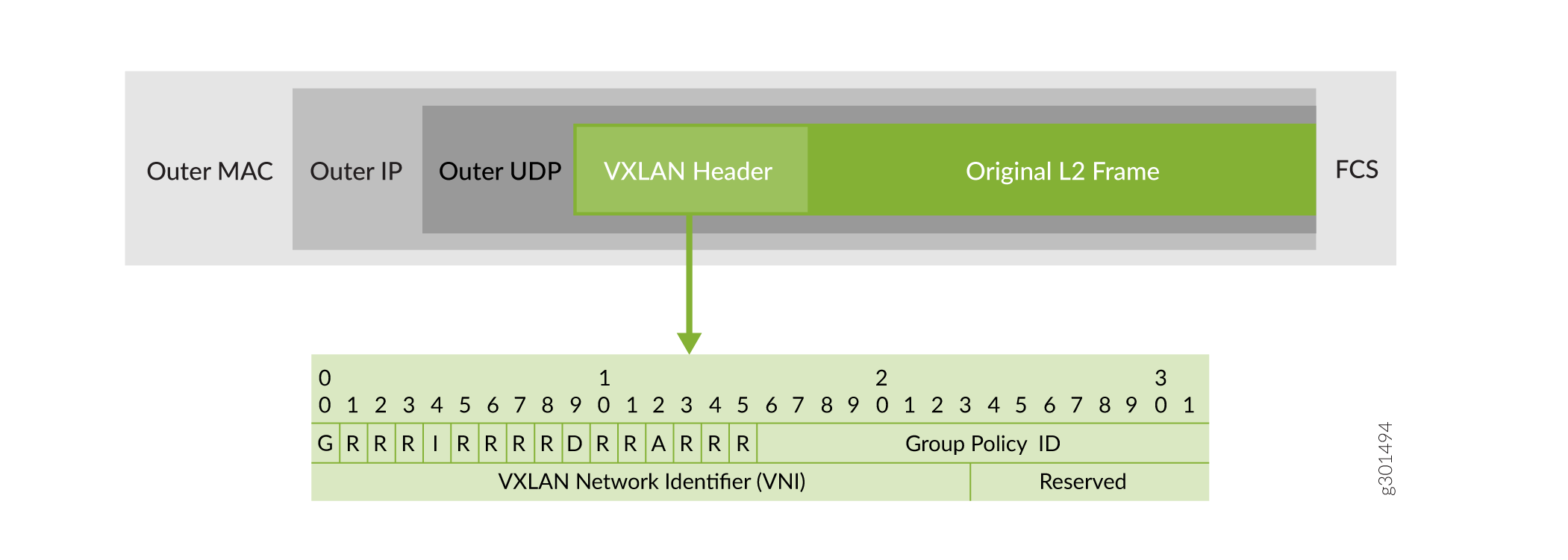
Enforcement Challenges
When a packet is encapsulated at the source VTEP, it includes the GBP tag of the source endpoint in the VXLAN header. This allows downstream devices to know who sent the traffic. The GBP tag of the destination endpoint is typically not included in the VXLAN header. It’s only known at the destination VTEP, which has local knowledge of the endpoint it serves.
If a firewall or policy engine (like SRX) is sitting in the middle of the fabric, it may only see the source tag and not the destination tag, making it hard to apply GBP rules that depend on both. In this case, to enforce policies based on both source and destination GBP tags, the best place is the egress VTEP—the switch that knows the destination endpoint and its group tag. This ensures accurate policy enforcement.
To enable tag-based filtering at ingress or gateway devices, the network must support a mechanism to share group tag information for all endpoints across the fabric. Example: EVPN Type 5 routes (IP Prefix routes) can carry BGP communities that include GBP tags metadata. This setting allows every device in the overlay (including SRX firewalls) to learn the GBP tags of all endpoints, not just the ones locally connected.
Group Tag Transfer in Inter-VXLAN Networks
In a VXLAN (Virtual Extensible LAN) environment, traffic flow between different VXLANs (often referred to as VNIs or Virtual Network Identifiers) requires special handling because VXLAN is designed to extend Layer 2 networks across Layer 3 infrastructure. In such cases, the source group ID must be preserved across VXLAN tunnels to ensure that any policies or security measures associated with the group are maintained throughout the traffic flow.
Following illustration shows the process involved in routing traffic between different VXLAN segments (VNIs) using a Layer 3 gateway that can handle VXLAN encapsulated traffic.
Scenario overview:
- Need to establish communication between Host1 and Host4.
- Host1 is located in a VXLAN identified by VNI 1000.
- Host4 is located in a different VXLAN identified by VNI 2000.
- Host1 and Host4 are part of same endpoint group (EPG2).
Traffic flow and inter-VXLAN routing for source group tag preservation:
- Host1 sends a packet destined for Host4. VTEP1 (VXLAN Tunnel Endpoint 1),
which is associated with Host1's VNI (1000), receives this packet. Since
Host4 is in a different VXLAN (VNI 2000), VTEP1 forwards the packet to the
default gateway for VNI 1000, which is L3 Gateway (SRX Series Firewall in
this example). Here, the SRX Series Firewall can act as VTEP device to
perform encapsulation and de-encapsulation. Note: Although SRX Series devices can terminate and re-originate VXLAN tunnels, they do not insert GBP source tags. GBP tag insertion is performed only by leaf devices. SRX devices can read and evaluate GBP tags in policies, but they cannot generate or assign them, and the micro‑segmentation filters required for GBP tag insertion are not supported on SRX. As a result, while SRX can participate in GBP processing, it cannot function as a leaf device for GBP tag assignment.
- VTEP1 encapsulates the packet with VXLAN headers, including the EPG1 (Endpoint Group) group ID, which is a metadata identifier used for policy enforcement. The encapsulated packet is sent to the Layer 3 Gateway.
- The Layer 3 gateway receives the VXLAN-encapsulated packet. It decapsulates the packet to examine the inner payload and source group ID. The gateway is responsible for routing the packet between different VNIs, in this case, from VNI 1000 to VNI 2000.
- Layer 3 gateway re-encapsulates the packet with VXLAN headers for forwarding to VTEP2 (associated with Host4's VNI, 2000). It ensures that the original source group ID (EPG1) is preserved in the VXLAN header during this re-encapsulation process.
- VTEP2 receives the encapsulated packet from Layer 3 Gateway. It decapsulates the packet and delivers it to Host4 in VNI 2000.
To effectively manage inter-VXLAN traffic with group tag preservation, you must configure gateway routers to handle encapsulation and decapsulation processes across VXLAN tunnel endpoints (VTEPs). This configuration is required to preserve source group tags during transit, allowing consistent policy enforcement across different network segments.
Inter-Site or External Communication
Following image shows spine-and-leaf EVPN-VXLAN topology for comminication between two datacenters.
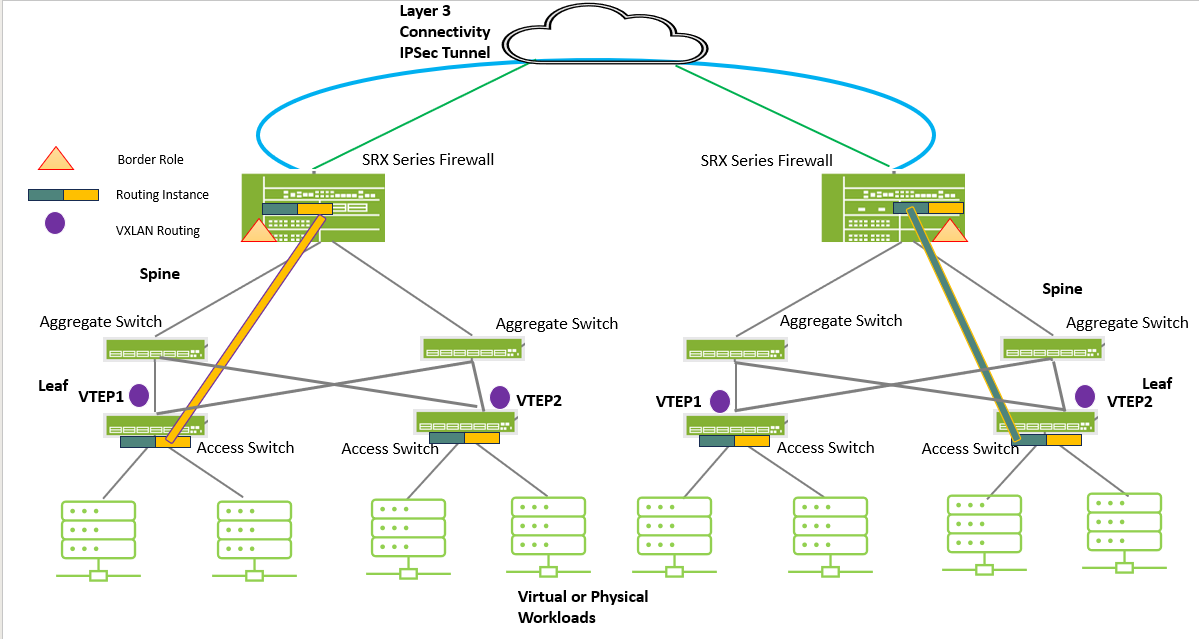
In this topology, SRX Series Firewall acts as a Layer 3 gateway for traffic between VXLAN segments (that is, between different subnets or VNIs). It establishes IPsec tunnels for inter-DC traffic ensuring encrypted communication between sites or external networks.
When host traffic traverses the spine-leaf topology, the system first encapsulates the packet with VXLAN headers. Then, it determines if additional encapsulation (like IPSec) is needed. If so, the SRX prepares the packet for the next tunnel stage, ensuring secure and policy-compliant delivery.
For additional information on GBPs, see Micro and Macro Segmentation using Group Based Policy in a VXLAN. For configuration on SRX Series Firewalls in EVPN-VXLAN, see Tunnel Inspection for EVPN-VXLAN by SRX Series Devices.
Configuration of Group Based Policies
To effectively implement VXLAN group-based policy, understand the process of configuration sequence and options. This section provides configuration sequence and samples related to group-based policies in EVPN-VXLAN deployments. Ensure that the EVPN-VXLAN baseline, including both underlay and overlay configurations, is properly set up and operational.
Configuration Sequences
To implement GBP effectively, you must:
- Define GBP tags:
Assign GBP tags, which are numeric identifiers, to endpoints to classify them into logical security groups. These tags help enforce identity-based policies across the network.
- Static Assignment: Configure GBP tags directly on switch ports.
- Dynamic Assignment: Use RADIUS and 802.1X authentication on switches to assign GBP tags based on user/device identity during login. See Assigning SGTs Using 802.1X in Micro and Macro Segmentation using Group Based Policy in a VXLAN.
The maximum number of GBP tags that can be configured for both source and destination is 128.
- Create GBP Tag Assignment Filters: Set up filters on switches to assign GBP tags to incoming traffic. These filters can be based on Interface (port), MAC address, or user authentication results (e.g., RADIUS attributes). This ensures that traffic entering the VXLAN fabric is correctly tagged with its group identity for policy enforcement downstream.
Configure GBP Policy Enforcement Filters: Develop policies that enforce security measures on traffic based on the assigned GBP tags, controlling which traffic is permitted or blocked to achieve segmentation.
Enable VXLAN-GBP Encapsulation: Configure VXLAN to incorporate the GBP tag within the VXLAN header's Group Policy ID field, facilitating tag propagation across the VXLAN fabric.
Apply GBP Policies at Enforcement Points: By default, enforcement occurs at the egress switch where both source and destination GBP tags are available. Juniper also supports optional ingress enforcement, requiring destination tag propagation to the ingress point.
Verify and Monitor: Utilize operational commands to ensure GBP tag assignment, policy enforcement, and VXLAN encapsulation are functioning correctly, confirming that policies are applied as intended.
Configuration Samples
GBP configuration differs depending on whether you're running on a Centrally Routed and Bridging (CRB) overlay or an Edge Routed and Bridging overlay. For details, see Micro and Macro Segmentation using Group Based Policy in a VXLAN.
On Access or Aggregate Switch
Configure a firewall filter named "TEST-1" with micro-segmentation capabilities. Specify a condition for term "t1" within the filter. It matches IPv4 traffic and IPv6 traffic originating from the subnet 20.20.20.0/24 and 2000::/64 respectively. Next define the action for traffic that matches the conditions specified in term "t1". In this case, a "gbp-tag" (group-based policy tag) with a value of 200 is applied to the matched traffic.
[edit] user@host# set firewall family any filter TEST-1 micro-segmentation user@host# set firewall family any filter TEST-1 term t1 from ip-version ipv4 address 20.20.20.0/24 user@host# set firewall family any filter TEST-1 term t1 from ip-version ipv6 address 2000::/64 user@host# set firewall family any filter TEST-1 term t1 then gbp-tag 200
Configure GBP policy enforcement. Packets with GBP source tag 100 and GBP destination tag 200 will match on term t100-200 and be accepted. Packets with GBP source tag 100 and GBP destination tag 300 will match on term t100-300 and be discarded.
[edit] user@host# set firewall family any filter gbp-policy term t100-200 from gbp-src-tag 100 user@host# set firewall family any filter gbp-policy term t100-200 from gbp-dst-tag 200 user@host# set firewall family any filter gbp-policy term t100-200 then accept user@host# set firewall family any filter gbp-policy term t100-300 from gbp-src-tag 100 user@host# set firewall family any filter gbp-policy term t100-300 from gbp-dst-tag 300 user@host# set firewall family any filter gbp-policy term t100-300 then discard
- Enable the following statement to perform the policy enforcement at the
ingress node.
[edit] user@host# set forwarding-options evpn-vxlan gbp ingress-enforcement
Ingress enforcement saves network bandwidth by discarding tagged packets at the ingress that would otherwise be discarded at the egress. To support policy enforcement at or closer to the ingress, we propagate the MAC and IP-MAC based tags across the network using extended BGP communities within EVPN Type 2 and Type 5 routes. For more details, see Policy Enforcement at the Ingress and Tag Propagation section in Micro and Macro Segmentation using Group Based Policy in a VXLAN.
Associate the GBP filter to a routing instance. Within the routing instance, configure the EVPN-VXLAN GBP ingress source tag to use the
TEST-1filter.[edit] user@host# set routing-instances R1 forwarding-options evpn-vxlan gbp ingress-src-tag filter TEST-1
On interface
ge-0/0/1, unit 0, the filter chainTEST-1is applied, which ensures that the source GBP tag is pushed into the packet header.[edit] user@host# set interfaces ge-0/0/1 unit 0 filter chain TEST-1
On SRX Series Firewall
A security policy
zone-pol1is established from thetrustzone to theuntrustzone.The policy matches traffic with the many criteria including Source GBP tag:
200. If the traffic matches all these criteria, the policy permits the flow:[edit] user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match source-address any user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match destination-address any user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match application any user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match dynamic-application any user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match gbp-src-tag 200 user@host# set security policies from-zone trust to-zone untrust policy zone-pol1 match gbp-dst-tag 400 user@host# set security policies from-zone trust to-zone untrust policy zone-pol1then permit
- Verify policy details on the firewall:
usr@hhost# show security policiesDefault policy: permit-all Default policy log Profile ID: 0 Pre ID default policy: permit-all Default HTTP Mux policy: permit-all From zone: trust, To zone: untrust Policy: zone-pol1, State: enabled, Index: 4, Scope Policy: 0, Sequence number: 1, Log Profile ID: 0 Source vrf group: any Destination vrf group: any Source addresses: any Destination addresses: any Applications: any Dynamic Applications: any Source identity feeds: any Destination identity feeds: any Gbp source tags: 200 Gbp destination tag: 400 Action: permit, log
