Security Policies for VXLAN
Configure Security Policies for VXLAN
Use this example to configure security policies for EVPN (Ethernet VPN) Virtual Extensible LAN (VXLAN) tunnel inspection.
Requirements
VXLAN support on SRX Series Firewalls provides the flexibility to bring an enterprise grade firewall to connect end points in their campus, data center, branch and public cloud environments while providing embedded security.
This example uses the following hardware and software components:
SRX4600 device
Junos OS Release 20.4R1
Before you begin:
Make sure you understand how EVPN and VXLAN works.
Overview
The EVPN solution provides large enterprises a common framework used to manage their campus and data center networks. An EVPN-VxLAN architecture supports efficient Layer 2 and Layer 3 network connectivity with scale, simplicity, and agility. Figure 1 shows an simplified VXLAN traffic flow topology.
Topology
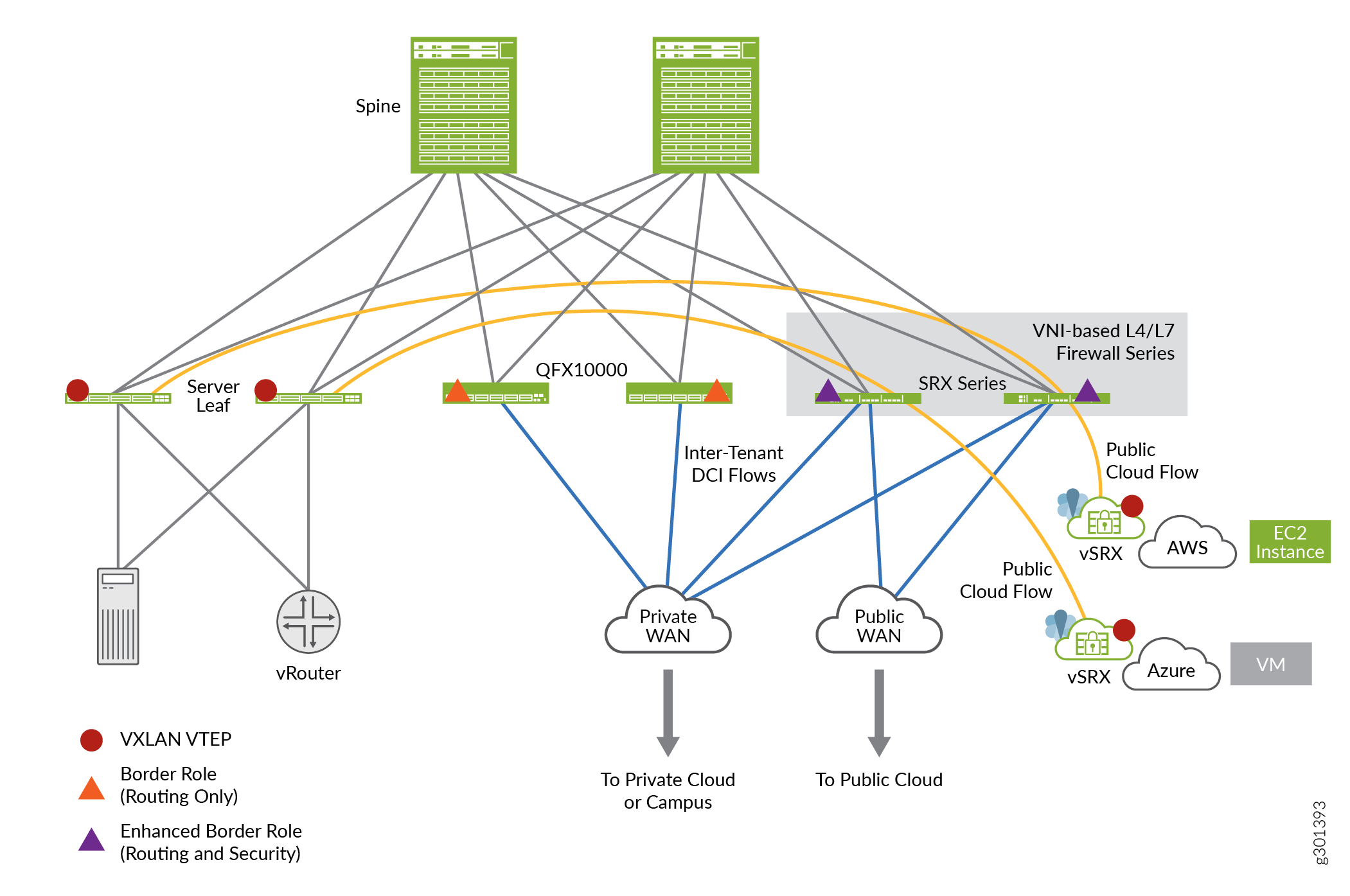
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security zones security-zone cloud-1 set security zones security-zone dc set security tunnel-inspection inspection-profile ins-pf1 vxlan vx1 vni r1 set security tunnel-inspection inspection-profile ins-pf1 vxlan vx1 vni r2 set security tunnel-inspection inspection-profile ins-pf1 vxlan vx1 vni r3 set security tunnel-inspection inspection-profile ins-pf1 vxlan vx1 vni r4 set security tunnel-inspection inspection-profile ins-pf1 vxlan vx1 policy-set pset1 set security tunnel-inspection vni r1 vni-range 160 to 200 set security tunnel-inspection vni r2 vni-id 155 set security tunnel-inspection vni r3 vni-range 300 to 399 set security tunnel-inspection vni r4 vni-range 100 to 120 set security tunnel-inspection vni v1 vni-range 1 to 100 set security policies from-zone dc to-zone cloud-1 policy p1 match source-address any set security policies from-zone dc to-zone cloud-1 policy p1 match destination-address any set security policies from-zone dc to-zone cloud-1 policy p1 match application junos-vxlan set security policies from-zone dc to-zone cloud-1 policy p1 then permit tunnel-inspection ins-pf1 set security policies from-zone cloud-1 to-zone dc policy p1 match source-address any set security policies from-zone cloud-1 to-zone dc policy p1 match destination-address any set security policies from-zone cloud-1 to-zone dc policy p1 match application junos-vxlan set security policies from-zone cloud-1 to-zone dc policy p1 then permit tunnel-inspection ins-pf1 set security policies policy-set pset1 policy pset_p1 match source-address any set security policies policy-set pset1 policy pset_p1 match destination-address any set security policies policy-set pset1 policy pset_p1 match application any set security policies policy-set pset1 policy pset_p1 then permit set security policies default-policy deny-all
Procedure
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure VXLAN:
Define Security Zones.
[edit security zones] user@host# set security-zone cloud-1 user@host# set zones security-zone dc
Define tunnel-inspection profile.
[edit security tunnel-inspection] user@host# set inspection-profile ins-pf1 vxlan vx1 vni r1 user@host# set inspection-profile ins-pf1 vxlan vx1 vni r2 user@host# set inspection-profile ins-pf1 vxlan vx1 vni r3 user@host# set inspection-profile ins-pf1 vxlan vx1 vni r4 user@host# set inspection-profile ins-pf1 vxlan vx1 policy-set pset1 user@host# set vni r1 vni-range 160 to 200 user@host# set vni r2 vni-id 155 user@host# set vni r3 vni-range 300 to 399 user@host# set vni r4 vni-range 100 to 120 user@host# set vni v1 vni-range 1 to 100
Define outer session policies.
[edit security policies] user@host# set from-zone dc to-zone cloud-1 policy p1 match source-address any user@host# set from-zone dc to-zone cloud-1 policy p1 match destination-address any user@host# set from-zone dc to-zone cloud-1 policy p1 match application junos-vxlan user@host# set from-zone dc to-zone cloud-1 policy p1 then permit tunnel-inspection profile-1 user@host# set from-zone cloud-1 to-zone dc policy p1 match source-address any user@host# set from-zone cloud-1 to-zone dc policy p1 match destination-address any user@host# set from-zone cloud-1 to-zone dc policy p1 match application junos-vxlan user@host# set from-zone cloud-1 to-zone dc policy p1 then permit tunnel-inspection ins-pf1
Define policy-set.
[edit security policies] user@host# set policy-set pset1 policy pset_p1 match source-address any user@host# set policy-set pset1 policy pset_p1 destination-address any user@host# set policy-set pset1 policy pset_p1 match application any user@host# set policy-set pset1 policy pset_p1 then permit user@host# set default-policy deny-all
Results
From configuration mode, confirm your configuration
by entering the show security policies command. If the
output does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
user@host# show security policies
from-zone dc to-zone cloud-1 {
policy p1 {
match {
source-address any;
destination-address any;
application junos-vxlan;
}
then {
permit {
tunnel-inspection {
ins-pf1;
}
}
}
}
}
from-zone cloud-1 to-zone dc {
policy p1 {
match {
source-address any;
destination-address any;
application junos-vxlan;
}
then {
permit {
tunnel-inspection {
ins-pf1;
}
}
}
}
}
policy-set pset1 {
policy pset_p1 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
default-policy {
deny-all;
}
If you are done configuring the feature on your device, enter commit from configuration mode.
Verification
Verify tunnel inspection profiles and VNI
Purpose
Verify that the tunnel inpection profile and VNI are confugured..
Action
From operational mode, enter the show security
tunnel-inspection profiles ins-pf1 and show security tunnel-inspection
vnis commands.
user@host> show security tunnel-inspection profiles ins-pf1
node0:
--------------------------------------------------------------------------
Logical system: root-logical-system
Profile count: 1
Profile: ins-pf1
Type: VXLAN
Vxlan count: 1
Vxlan name: vx1
VNI count: 4
VNI:r1, r2, r3, r4
Policy set: pset1
Inspection level: 1user@host> show security tunnel-inspection vnis
node0:
--------------------------------------------------------------------------
Logical system: root-logical-system
VNI count: 5
VNI name: r1
VNI id count: 1
[160 - 200]
VNI name: r2
VNI id count: 1
[155 - 155]
VNI name: r3
VNI id count: 1
[300 - 399]
VNI name: r4
VNI id count: 1
[100 - 120]
VNI name: v1
VNI id count: 1
[1 - 100]Meaning
The output displays that the VXLAN feature is enabled and there are no safe search redirects and safe search rewrites.
Verify Safe Search Function
Purpose
Verify that the safe search feature is enabled for Content Security Web filtering solutions.
Action
From operational mode, enter the Show security
flow tunnel-inspection statistic command to view the tunnel-inspection
statistics.
user@host> show security flow tunnel-inspection statistics
node0:
--------------------------------------------------------------------------
Flow Tunnel-inspection statistics:
Tunnel-inspection statistics of FPC4 PIC1:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 269
overlay session close: 269
underlay session active: 0
underlay session create: 566
underlay session close: 566
input packets: 349717
input bytes: 363418345
output packets: 348701
output bytes: 363226339
bypass packets: 501
bypass bytes: 50890
Tunnel-inspection statistics of FPC4 PIC2:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 270
overlay session close: 270
underlay session active: 0
underlay session create: 586
underlay session close: 586
input packets: 194151
input bytes: 200171306
output packets: 193221
output bytes: 199987258
bypass packets: 617
bypass bytes: 92902
Tunnel-inspection statistics of FPC4 PIC3:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 275
overlay session close: 275
underlay session active: 0
underlay session create: 615
underlay session close: 615
input packets: 216486
input bytes: 222875066
output packets: 213827
output bytes: 222460378
bypass packets: 2038
bypass bytes: 270480
Tunnel-inspection statistics summary:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 814
overlay session close: 814
underlay session active: 0
underlay session create: 1767
underlay session close: 1767
input packets: 760354
input bytes: 786464717
output packets: 755749
output bytes: 785673975
bypass packets: 3156
bypass bytes: 414272
node1:
--------------------------------------------------------------------------
Flow Tunnel-inspection statistics:
Tunnel-inspection statistics of FPC4 PIC1:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 269
overlay session close: 269
underlay session active: 0
underlay session create: 566
underlay session close: 566
input packets: 0
input bytes: 0
output packets: 0
output bytes: 0
bypass packets: 0
bypass bytes: 0
Tunnel-inspection statistics of FPC4 PIC2:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 270
overlay session close: 270
underlay session active: 0
underlay session create: 586
underlay session close: 586
input packets: 0
input bytes: 0
output packets: 0
output bytes: 0
bypass packets: 0
bypass bytes: 0
Tunnel-inspection statistics of FPC4 PIC3:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 275
overlay session close: 275
underlay session active: 0
underlay session create: 615
underlay session close: 615
input packets: 0
input bytes: 0
output packets: 0
output bytes: 0
bypass packets: 0
bypass bytes: 0
Tunnel-inspection statistics summary:
Tunnel-inspection type VXLAN:
overlay session active: 0
overlay session create: 814
overlay session close: 814
underlay session active: 0
underlay session create: 1767
underlay session close: 1767
input packets: 0
input bytes: 0
output packets: 0
output bytes: 0
bypass packets: 0
bypass bytes: 0 Meaning
The output displays that the VXLAN feature is enabled and there are no safe search redirects and safe search rewrites.
