Example: Configuring a Firewall Filter on a Management Interface on an EX Series Switch
You can configure a firewall filter on a management interface on an EX Series switch to filter ingress or egress traffic on the management interface on the switch. You can use utilities such as SSH or Telnet to connect to the management interface over the network and then use management protocols such as SNMP to gather statistical data from the switch.
This example discusses how to configure a firewall filter on a management interface to filter SSH packets egressing from an EX Series switch:
Requirements
This example uses the following hardware and software components:
One EX Series switch and one management PC
Junos OS Release 10.4 or later for EX Series switches
Overview and Topology
Topology
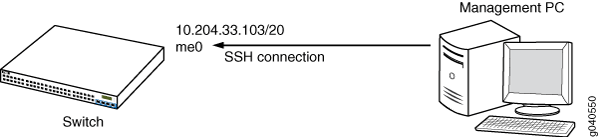
In this example, a management PC establishes an SSH connection with the management interface on a switch to remotely manage the switch. The IP address configured for the management interface is 10.204.33.103/20. A firewall filter is configured on the management interface to count the number of packets egressing from a source SSH port on the management interface. When the management PC establishes the SSH session with the management interface, the management interface returns SSH packets to the management PC to confirm that the session is established. These SSH packets are filtered based on the match condition specified in the firewall filter before they are forwarded to the management PC. As these packets are generated from the source SSH port on the management interface, they fulfill the match condition specified for the management interface. The number of matched SSH packets provides a count of the number of packets that have traversed the management interface. A system administrator can use this information to monitor the management traffic and take any action if required.
Figure 1 shows the topology for this example in which a management PC establishes an SSH connection with the switch.
Configuration
To configure a firewall filter on a management interface, perform these tasks:
CLI Quick Configuration
To quickly create and configure a firewall filter on the management interface to filter SSH packets egressing from the management interface, copy the following commands and paste them into the switch terminal window:
[edit] set firewall family inet filter mgmt_fil1 term t1 from source-port ssh set firewall family inet filter mgmt_fil1 term t1 then count c1 set firewall family inet filter mgmt_fil1 term t2 then accept set interfaces me0 unit 0 family inet filter output mgmt_fil1
Step-by-Step Procedure
To configure a firewall filter on the management interface to filter SSH packets:
Configure the firewall filter that matches SSH packets from the source port:
[edit] user@switch# set firewall family inet filter (Firewall Filters) mgmt_fil1 term t1 from source-port ssh user@switch# set firewall family inet filter mgmt_fil1 term t1 then count c1 user@switch# set firewall family inet filter mgmt_fil1 term t2 then accept
These statements set a counter c1 to count the number of SSH packets that egress from the source SSH interface on the management interface.
Set the firewall filter for the management interface:
[edit] user@switch# set interfaces me0 unit 0 family inet filter output mgmt_fil1
Note:You can also set the firewall filter for a VME interface.
Results
Check the results of the configuration:
[edit]
user@switch# show
interfaces {
me0 {
unit 0 {
family inet {
filter {
output mgmt_fil1;
}
address 10.93.54.6/24;
}
}
}
}
firewall {
family inet {
filter mgmt_fil1{
term t1 {
from {
source-port ssh;
then count c1;
}
}
term t2 {
then accept;
}
}
}
}
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying That the Firewall Filter Is Configured on a Management Interface
Purpose
Verify that the firewall filter has been enabled on the management interface on the switch.
Action
Verify that the firewall filter is applied to the management interface:
[edit] user@switch# show interfaces me0 unit 0 { family inet { filter { output mgmt_fil1; } address 10.204.33.103/20; } }Check the counter value that is associated with the firewall filter:
user@switch> show firewall Filter: mgmt_fil1 Counters: Name Bytes Packets c1 0 0
From the management PC, establish a secure shell session with the switch:
[user@management-pc ~]$ ssh user@10.204.33.103
Check counter values after SSH packets are generated from the switch in response to the secure shell session request by the management PC:
user@switch> show firewall Filter: mgmt_fil1 Counters: Name Bytes Packets c1 3533 23
Meaning
The output indicates that the firewall filter has been applied to the management interface and the counter value indicates that 23 SSH packets were generated from the switch.
