Example: Configuring Firewall Filters for Port, VLAN, and Router Traffic on EX Series Switches
This example shows how to configure and apply firewall filters to control traffic that is entering or exiting a port on the switch, a VLAN on the network, and a Layer 3 interface on the switch. Firewall filters define the rules that determine whether to forward or deny packets at specific processing points in the packet flow.
Requirements
This example uses the following software and hardware components:
Junos OS Release 9.0 or later for EX Series switches.
Two Juniper Networks EX3200-48T switches: one to be used as an access switch, the other to be used as a distribution switch
One Juniper Networks EX-UM-4SFP uplink module
One Juniper Networks J-series router
Before you configure and apply the firewall filters in this example, be sure you have:
An understanding of firewall filter concepts, policers, and CoS
Installed the uplink module in the distribution switch. See Installing an Uplink Module in an EX3200 Switch.
Overview
This configuration example show how to configure and apply firewall filters to provide
rules to evaluate the contents of packets and determine when to discard, forward, classify,
count, and analyze packets that are destined for or originating from the EX Series switches
that handle all voice-vlan, employee-vlan, and guest-vlan traffic. Table 1 shows the firewall filters that are configured
for the EX Series switches in this example.
| Component | Purpose/Description |
|---|---|
Port firewall filter, |
This firewall filter performs two functions:
This firewall filter is applied to port interfaces on the access switch. |
VLAN firewall filter, |
Prevents rogue devices from using HTTP sessions to mimic the gatekeeper device
that manages call registration, admission, and call status for VoIP calls. Only TCP or UDP
ports should be used; and only the gatekeeper uses HTTP. That is, all This firewall filter is applied to VLAN interfaces on the access switch. |
VLAN firewall filter, |
Accepts This firewall filter is applied to vlan interfaces on the access switch. |
VLAN firewall filter, |
Prevents guests (non-employees) from talking with employees or employee hosts
on This firewall filter is applied to VLAN interfaces on the access switch. |
Router firewall filter, |
Prioritizes This firewall filter is applied to a routed port (Layer 3 uplink module) on the distribution switch. |
Figure 1 shows the application of port, VLAN, and Layer 3 routed firewall filters on the switch.
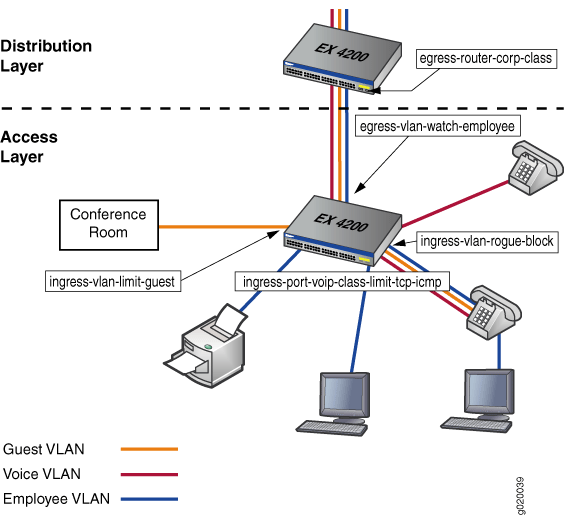
Network Topology
The topology for this configuration example consists of one EX-3200-48T switch at the access layer, and one EX-3200-48T switch at the distribution layer. The distribution switch's uplink module is configured to support a Layer 3 connection to a J-series router.
The EX Series switches are configured to support VLAN membership. Table 2 shows the VLAN configuration components for the VLANs.
VLAN Name |
VLAN ID |
VLAN Subnet and Available IP Addresses |
VLAN Description |
|---|---|---|---|
|
|
|
Voice VLAN used for employee VoIP traffic |
|
|
|
VLAN standalone PCs, PCs connected to the network through the hub in VoIP telephones,
wireless access points, and printers. This VLAN completely includes the voice VLAN. Two VLANs |
|
|
|
VLAN for guests’ data devices (PCs). The scenario assumes that the corporation has an area open to visitors, either in the lobby or in a conference room, that has a hub to which visitors can plug in their PCs to connect to the Web and to their company’s VPN. |
|
|
|
VLAN for the corporate security cameras. |
Ports on the EX Series switches support Power over Ethernet (PoE) to provide both network connectivity and power for VoIP telephones connecting to the ports. Table 3 shows the switch ports that are assigned to the VLANs and the IP and MAC addresses for devices connected to the switch ports:
Switch and Port Number |
VLAN Membership |
IP and MAC Addresses |
Port Devices |
|---|---|---|---|
ge-0/0/0, ge-0/0/1 |
|
IP addresses: MAC addresses: |
Two VoIP telephones, each connected to one PC. |
ge-0/0/2, ge-0/0/3 |
|
|
Printer, wireless access points |
ge-0/0/4, ge-0/0/5 |
|
|
Two hubs into which visitors can plug in their PCs. Hubs are located in an area open to visitors, such as a lobby or conference room |
ge-0/0/6, ge-0/0/7 |
|
|
Two security cameras |
ge-0/0/9 |
|
IP address: MAC address: |
Gatekeeper device. The gatekeeper manages call registration, admission, and call status for VoIP phones. |
ge-0/1/0 |
IP address: |
Layer 3 connection to a router; note that this is a port on the switch’s uplink module |
Configuring an Ingress Port Firewall Filter to Prioritize Voice Traffic and Rate-Limit TCP and ICMP Traffic
To configure and apply firewall filters for port, VLAN, and router interfaces, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure and apply a port firewall filter to prioritize voice traffic and
rate-limit packets that are destined for the employee-vlan subnet, copy the following
commands and paste them into the switch terminal window:
[edit]
set firewall policer tcp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m
set firewall policer tcp-connection-policer then discard
set firewall policer icmp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m
set firewall policer icmp-connection-policer then discard
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from source-mac-address 00.00.5E.00.53.01
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from source-mac-address 00.00.5E.00.53.02
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from protocol udp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high then forwarding-class expedited-forwarding
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high then loss-priority low
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control from precedence net-control
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control then forwarding-class network-control
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control then loss-priority low
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection from protocol tcp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then policer tcp-connection-policer
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then count tcp-counter
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then loss-priority high
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection from protocol icmp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then policer icmp-connection-policer
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then count icmp-counter
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then loss-priority high
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term best-effort then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term best-effort then loss-priority high
set interfaces ge-0/0/0 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port"
set interfaces ge-0/0/0 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
set interfaces ge-0/0/1 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port"
set interfaces ge-0/0/1 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
set class-of-service schedulers voice-high buffer-size percent 15
set class-of-service schedulers voice-high priority high
set class-of-service schedulers net-control buffer-size percent 10
set class-of-service schedulers net-control priority high
set class-of-service schedulers best-effort buffer-size percent 75
set class-of-service schedulers best-effort priority low
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class expedited-forwarding scheduler voice-high
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class network-control scheduler net-control
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class best-effort scheduler best-effort Step-by-Step Procedure
To configure and apply a port firewall filter to prioritize voice traffic and
rate-limit packets that are destined for the employee-vlan subnet:
Define the policers
tcp-connection-policerandicmp-connection-policer:[edit] user@switch# set firewall policer tcp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m user@switch# set firewall policer tcp-connection-policer then discard user@switch# set firewall policer icmp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m user@switch# set firewall policer icmp-connection-policer then discard
Define the firewall filter
ingress-port-voip-class-limit-tcp-icmp:[edit firewall] user@switch# set family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp
Define the term
voip-high:[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp ] user@switch# set term voip-high from source-mac-address 00.00.5E.00.53.01 user@switch# set term voip-high from source-mac-address 00.00.5E.00.53.02 user@switch# set term voip-high from protocol udp user@switch# set term voip-high then forwarding-class expedited-forwarding user@switch# set term voip-high then loss-priority low
Define the term
network-control:[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp ] user@switch# set term network-control from precedence net-control user@switch# set term network-control then forwarding-class network-control user@switch# set term network-control then loss-priority low
Define the term
tcp-connectionto configure rate limits for TCP traffic:[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term tcp-connection from destination-address 192.0.2.16/28 user@switch# set term tcp-connection from protocol tcp user@switch# set term tcp-connection then policer tcp-connection-policer user@switch# set term tcp-connection then count tcp-counter user@switch# set term tcp-connection then forwarding-class best-effort user@switch# set term tcp-connection then loss-priority high
Define the term
icmp-connectionto configure rate limits for ICMP traffic:[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term icmp-connection from destination-address 192.0.2.16/28 user@switch# set term icmp-connection from protocol icmp user@switch# set term icmp-connection then policer icmp-policer user@switch# set term icmp-connection then count icmp-counter user@switch# set term icmp-connection then forwarding-class best-effort user@switch# set term icmp-connection then loss-priority high
Define the term
best-effortwith no match conditions for an implicit match on all packets that did not match any other term in the firewall filter:[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term best-effort then forwarding-class best-effort user@switch# set term best-effort then loss-priority high
Apply the firewall filter
ingress-port-voip-class-limit-tcp-icmpas an input filter to the port interfaces foremployee-vlan:[edit interfaces] user@switch# set ge-0/0/0 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port" user@switch# set ge-0/0/0 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp user@switch# set ge-0/0/1 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port" user@switch# set ge-0/0/1 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
Configure the parameters that are desired for the different schedulers.
Note:When you configure parameters for the schedulers, define the numbers to match your network traffic patterns.
[edit class-of-service] user@switch# set schedulers voice-high buffer-size percent 15 user@switch# set schedulers voice-high priority high user@switch# set schedulers network—control buffer-size percent 10 user@switch# set schedulers network—control priority high user@switch# set schedulers best-effort buffer-size percent 75 user@switch# set schedulers best-effort priority low
Assign the forwarding classes to schedulers with a scheduler map:
[edit class-of-service] user@switch# set scheduler-maps ethernet-diffsrv-cos-map user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class expedited-forwarding scheduler voice-high user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class network-control scheduler net-control user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class best-effort scheduler best-effort
Associate the scheduler map with the outgoing interface:
[edit class-of-service] user@switch# set interfaces ge–0/1/0 scheduler-map ethernet-diffsrv-cos-map
Results
Display the results of the configuration:
user@switch# show
firewall {
policer tcp-connection-policer {
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 30k;
}
then {
discard;
}
}
policer icmp-connection-policer {
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 30k;
}
then {
discard;
}
}
family ethernet-switching {
filter ingress-port-voip-class-limit-tcp-icmp {
term voip-high {
from {
destination-mac-address 00.00.5E.00.53.01;
destination-mac-address 00.00.5E.00.53.02;
protocol udp;
}
then {
forwarding-class expedited-forwarding;
loss-priority low;
}
}
term network-control {
from {
precedence net-control ;
}
then {
forwarding-class network-control;
loss-priority low;
}
}
term tcp-connection {
from {
destination-address 192.0.2.16/28;
protocol tcp;
}
then {
policer tcp-connection-policer;
count tcp-counter;
forwarding-class best-effort;
loss-priority high;
}
}
term icmp-connection
from {
protocol icmp;
}
then {
policer icmp-connection-policer;
count icmp-counter;
forwarding-class best-effort;
loss-priority high;
}
}
term best-effort {
then {
forwarding-class best-effort;
loss-priority high;
}
}
}
}
}
interfaces {
ge-0/0/0 {
description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port";
unit 0 {
family ethernet-switching {
filter {
input ingress-port-voip-class-limit-tcp-icmp;
}
}
}
}
ge-0/0/1 {
description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port";
unit 0 {
family ethernet-switching {
filter {
input ingress-port-voip-class-limit-tcp-icmp;
}
}
}
}
}
scheduler-maps {
ethernet-diffsrv-cos-map {
forwarding-class expedited-forwarding scheduler voice-high;
forwarding-class network-control scheduler net-control;
forwarding-class best-effort scheduler best-effort;
}
}
interfaces {
ge/0/1/0 {
scheduler-map ethernet-diffsrv-cos-map;
}
}
Configuring a VLAN Ingress Firewall Filter to Prevent Rogue Devices from Disrupting VoIP Traffic
To configure and apply firewall filters for port, VLAN, and router interfaces, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure a VLAN firewall filter on voice-vlan to prevent rogue devices from using HTTP sessions to mimic the gatekeeper device that manages
VoIP traffic, copy the following commands and paste them into the switch terminal window:
[edit]
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper from destination-address 192.0.2.14
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper from destination-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper then accept
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper from source-address 192.0.2.14
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper from source-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper then accept
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper from destination-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper then count rogue-counter
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper then discard
set vlans voice-vlan description "block rogue devices on voice-vlan"
set vlans voice-vlan filter input ingress-vlan-rogue-block Step-by-Step Procedure
To configure and apply a VLAN firewall filter on voice-vlan to prevent
rogue devices from using HTTP to mimic the gatekeeper device that manages VoIP traffic:
Define the firewall filter
ingress-vlan-rogue-blockto specify filter matching on the traffic you want to permit and restrict:[edit firewall] user@switch# set family ethernet-switching filter ingress-vlan-rogue-block
Define the term
to-gatekeeperto accept packets that match the destination IP address of the gatekeeper:[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term to-gatekeeper from destination-address 192.0.2.14 user@switch# set term to-gatekeeper from destination-port 80 user@switch# set term to-gatekeeper then accept
Define the term
from-gatekeeperto accept packets that match the source IP address of the gatekeeper:[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term from-gatekeeper from source-address 192.0.2.14 user@switch# set term from-gatekeeper from source-port 80 user@switch# set term from-gatekeeper then accept
Define the term
not-gatekeeperto ensure allvoice-vlantraffic on TCP ports is destined for the gatekeeper device:[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term not-gatekeeper from destination-port 80 user@switch# set term not-gatekeeper then count rogue-counter user@switch# set term not-gatekeeper then discard
Apply the firewall filter
ingress-vlan-rogue-blockas an input filter to the VLAN interface for the VoIP telephones:[edit] user@switch# set vlans voice-vlan description "block rogue devices on voice-vlan" user@switch# set vlans voice-vlan filter input ingress-vlan-rogue-block
Results
Display the results of the configuration:
user@switch# show
firewall {
family ethernet-switching {
filter ingress-vlan-rogue-block {
term to-gatekeeper {
from {
destination-address 192.0.2.14/32
destination-port 80;
}
then {
accept;
}
}
term from-gatekeeper {
from {
source-address 192.0.2.14/32
source-port 80;
}
then {
accept;
}
}
term not-gatekeeper {
from {
destination-port 80;
}
then {
count rogue-counter;
discard;
}
}
}
vlans {
voice-vlan {
description "block rogue devices on voice-vlan";
filter {
input ingress-vlan-rogue-block;
}
}
}
Configuring a VLAN Firewall Filter to Count, Monitor, and Analyze Egress Traffic on the Employee VLAN
To configure and apply firewall filters for port, VLAN, and router interfaces, perform these tasks:
Procedure
CLI Quick Configuration
A firewall filter is configured and applied to VLAN interfaces to
filter employee-vlan egress traffic. Employee traffic destined for the corporate
subnet is accepted but not monitored. Employee traffic destined for the Web is counted and
analyzed.
To quickly configure and apply a VLAN firewall filter, copy the following commands and paste them into the switch terminal window:
[edit]
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-corp from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-corp then accept
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web from destination-port 80
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web then count employee-web-counter
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web then analyzer employee-monitor
set vlans employee-vlan description "filter at egress VLAN to count and analyze employee to Web traffic"
set vlans employee-vlan filter output egress-vlan-watch-employee Step-by-Step Procedure
To configure and apply an egress port firewall filter to count and analyze employee-vlan traffic that is destined for the Web:
Define the firewall filter
egress-vlan-watch-employee:[edit firewall] user@switch# set family ethernet-switching filter egress-vlan-watch-employee
Define the term
employee-to-corpto accept but not monitor allemployee-vlantraffic destined for the corporate subnet:[edit firewall family ethernet-switching filter egress-vlan-watch-employee] user@switch# set term employee-to-corp from destination-address 192.0.2.16/28 user@switch# set term employee-to-corp then accept
Define the term
employee-to-webto count and monitor allemployee-vlantraffic destined for the Web:[edit firewall family ethernet-switching filter egress-vlan-watch-employee] user@switch# set term employee-to-web from destination-port 80 user@switch# set term employee-to-web then count employee-web-counter user@switch# set term employee-to-web then analyzer employee-monitor
Note:See Example: Configuring Port Mirroring for Local Monitoring of Employee Resource Use on EX Series Switches for information about configuring the
employee-monitoranalyzer.Apply the firewall filter
egress-vlan-watch-employeeas an output filter to the port interfaces for the VoIP telephones:[edit] user@switch# set vlans employee-vlan description "filter at egress VLAN to count and analyze employee to Web traffic" user@switch# set vlans employee-vlan filter output egress-vlan-watch-employee
Results
Display the results of the configuration:
user@switch# show
firewall {
family ethernet-switching {
filter egress-vlan-watch-employee {
term employee-to-corp {
from {
destination-address 192.0.2.16/28
}
then {
accept;
}
}
term employee-to-web {
from {
destination-port 80;
}
then {
count employee-web-counter:
analyzer employee-monitor;
}
}
}
}
}
vlans {
employee-vlan {
description "filter at egress VLAN to count and analyze employee to Web traffic";
filter {
output egress-vlan-watch-employee;
}
}
}
Configuring a VLAN Firewall Filter to Restrict Guest-to-Employee Traffic and Peer-to-Peer Applications on the Guest VLAN
To configure and apply firewall filters for port, VLAN, and router interfaces, perform these tasks:
Procedure
CLI Quick Configuration
In the following example, the first filter term permits guests to
talk with other guests but not employees on employee-vlan. The second filter term
allows guests Web access but prevents them from using peer-to-peer applications on guest-vlan.
To quickly configure a VLAN firewall filter to restrict guest-to-employee traffic, blocking
guests from talking with employees or employee hosts on employee-vlan or attempting
to use peer-to-peer applications on guest-vlan, copy the following commands and
paste them into the switch terminal window:
[edit]
set firewall family ethernet-switching filter ingress-vlan-limit-guest term guest-to-guest from destination-address 192.0.2.33/28
set firewall family ethernet-switching filter ingress-vlan-limit-guest term guest-to-guest then accept
set firewall family ethernet-switching filter ingress-vlan-limit-guest term no-guest-employee-no-peer-to-peer from destination-mac-address 00.05.5E.00.00.DF
set firewall family ethernet-switching filter ingress-vlan-limit-guest term no-guest-employee-no-peer-to-peer then accept
set vlans guest-vlan description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN"
set vlans guest-vlan forwarding-options filter input ingress-vlan-limit-guest Step-by-Step Procedure
To configure and apply a VLAN firewall filter to restrict guest-to-employee traffic
and peer-to-peer applications on guest-vlan:
Define the firewall filter
ingress-vlan-limit-guest:[edit firewall] set firewall family ethernet-switching filter ingress-vlan-limit-guestDefine the term
guest-to-guestto permit guests on theguest-vlanto talk with other guests but not employees on theemployee-vlan:[edit firewall family ethernet-switching filter ingress-vlan-limit-guest] user@switch# set term guest-to-guest from destination-address 192.0.2.33/28 user@switch# set term guest-to-guest then accept
Define the term
no-guest-employee-no-peer-to-peerto allow guests onguest-vlanWeb access but prevent them from using peer-to-peer applications on theguest-vlan.Note:The
destination-mac-addressis the default gateway, which for any host in a VLAN is the next-hop router.[edit firewall family ethernet-switching filter ingress-vlan-limit-guest] user@switch# set term no-guest-employee-no-peer-to-peer from destination-mac-address 00.05.5E.00.00.DF user@switch# set term no-guest-employee-no-peer-to-peer then accept
Apply the firewall filter
ingress-vlan-limit-guestas an input filter to the interface forguest-vlan:[edit] user@switch# set vlans guest-vlan description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN" user@switch# set vlans guest-vlan forwarding-options filter input ingress-vlan-limit-guest
Results
Display the results of the configuration:
user@switch# show
firewall {
family ethernet-switching {
filter ingress-vlan-limit-guest {
term guest-to-guest {
from {
destination-address 192.0.2.33/28;
}
then {
accept;
}
}
term no-guest-employee-no-peer-to-peer {
from {
destination-mac-address 00.05.5E.00.00.DF;
}
then {
accept;
}
}
}
}
}
vlans {
guest-vlan {
description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN";
filter {
input ingress-vlan-limit-guest;
}
}
}
Configuring a Router Firewall Filter to Give Priority to Egress Traffic Destined for the Corporate Subnet
To configure and apply firewall filters for port, VLAN, and router interfaces, perform these tasks:
Procedure
CLI Quick Configuration
To quickly configure a firewall filter for a routed port (Layer 3
uplink module) to filter employee-vlan traffic, giving highest forwarding-class
priority to traffic destined for the corporate subnet, copy the following commands and paste
them into the switch terminal window:
[edit]
set firewall family inet filter egress-router-corp-class term corp-expedite from destination-address 192.0.2.16/28
set firewall family inet filter egress-router-corp-class term corp-expedite then forwarding-class expedited-forwarding
set firewall family inet filter egress-router-corp-class term corp-expedite then loss-priority low
set firewall family inet filter egress-router-corp-class term not-to-corp then accept
set interfaces ge-0/1/0 description "filter at egress router to expedite destined for corporate network"
set ge-0/1/0 unit 0 family inet address 203.0.113.0
set interfaces ge-0/1/0 unit 0 family inet filter output egress-router-corp-class Step-by-Step Procedure
To configure and apply a firewall filter to a routed port (Layer 3 uplink module)
to give highest priority to employee-vlan traffic destined for the corporate subnet:
Define the firewall filter
egress-router-corp-class:[edit] user@switch# set firewall family inet filter egress-router-corp-class
Define the term
corp-expedite:[edit firewall] user@switch# set family inet filter egress-router-corp-class term corp-expedite from destination-address 192.0.2.16/28 user@switch# set family inet filter egress-router-corp-class term corp-expedite then forwarding-class expedited-forwarding user@switch# set family inet filter egress-router-corp-class term corp-expedite then loss-priority low
Define the term
not-to-corp:[edit firewall] user@switch# set family inet filter egress-router-corp-class term not-to-corp then accept
Apply the firewall filter
egress-router-corp-classas an output filter for the port on the switch's uplink module, which provides a Layer 3 connection to a router:[edit interfaces] user@switch# set ge-0/1/0 description "filter at egress router to expedite employee traffic destined for corporate network" user@switch# set ge-0/1/0 unit 0 family inet address 203.0.113.0 user@switch# set ge-0/1/0 unit 0 family inet filter output egress-router-corp-class
Results
Display the results of the configuration:
user@switch# show
firewall {
family inet {
filter egress-router-corp-class {
term corp-expedite {
from {
destination-address 192.0.2.16/28;
}
then {
forwarding-class expedited-forwarding;
loss-priority low;
}
}
term not-to-corp {
then {
accept;
}
}
}
}
}
interfaces {
ge-0/1/0 {
unit 0 {
description "filter at egress router interface to expedite employee traffic destined for corporate network";
family inet {
source-address 203.0.113.0
filter {
output egress-router-corp-class;
}
}
}
}
}
Verification
To confirm that the firewall filters are working properly, perform the following tasks:
- Verifying that Firewall Filters and Policers are Operational
- Verifying that Schedulers and Scheduler-Maps are Operational
Verifying that Firewall Filters and Policers are Operational
Purpose
Verify the operational state of the firewall filters and policers that are configured on the switch.
Action
Use the operational mode command:
user@switch> show firewall Filter: ingress-port-voip-class-limit-tcp-icmp Counters: Name Packets icmp-counter 0 tcp-counter 0 Policers: Name Packets icmp-connection-policer 0 tcp-connection-policer 0 Filter: ingress-vlan-rogue-block Filter: egress-vlan-watch-employee Counters: Name Packets employee-web—counter 0
Meaning
The show firewall command displays the names of the firewall filters,
policers, and counters that are configured on the switch. The output fields show byte and
packet counts for all configured counters and the packet count for all policers.
Verifying that Schedulers and Scheduler-Maps are Operational
Purpose
Verify that schedulers and scheduler-maps are operational on the switch.
Action
Use the operational mode command:
user@switch> show class-of-service scheduler-map
Scheduler map: default, Index: 2
Scheduler: default-be, Forwarding class: best-effort, Index: 20
Transmit rate: 95 percent, Rate Limit: none, Buffer size: 95 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 default-drop-profile
Low TCP 1 default-drop-profile
High non-TCP 1 default-drop-profile
High TCP 1 default-drop-profile
Scheduler: default-nc, Forwarding class: network-control, Index: 22
Transmit rate: 5 percent, Rate Limit: none, Buffer size: 5 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 default-drop-profile
Low TCP 1 default-drop-profile
High non-TCP 1 default-drop-profile
High TCP 1 default-drop-profileScheduler map: ethernet-diffsrv-cos-map, Index: 21657
Scheduler: best-effort, Forwarding class: best-effort, Index: 61257
Transmit rate: remainder, Rate Limit: none, Buffer size: 75 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
Scheduler: voice-high, Forwarding class: expedited-forwarding, Index: 3123
Transmit rate: remainder, Rate Limit: none, Buffer size: 15 percent,
Priority: high
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
Scheduler: net-control, Forwarding class: network-control, Index: 2451
Transmit rate: remainder, Rate Limit: none, Buffer size: 10 percent,
Priority: high
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
Meaning
Displays statistics about the configured schedulers and schedulers-maps.
