Router Data Flow Overview
The Junos® operating system (Junos OS) provides a policy framework, which is a collection of Junos OS policies that enable you to control flows of routing information and packets within the router.
Flow of Routing Information
Routing information is the information about routes learned by the routing protocols from a router’s neighbors. This information is stored in routing tables. The routing protocols advertise active routes only from the routing tables. An active route is a route that is chosen from all routes in the routing table to reach a destination.
To control which routes the routing protocols place in the routing tables and which routes the routing protocols advertise from the routing tables, you can configure routing policies, which are sets of rules that the policy framework uses to preempt default routing policies.
The Routing Engine, which runs the router's control plane software, handles the flow of routing information between the routing protocols and the routing tables and between the routing tables and the forwarding table. The Routing Engine runs the Junos OS and routing policies and stores the active router configuration, the master routing table, and the master forwarding table,
Flow of Data Packets
Data packets are chunks of data that transit the router as they are being forwarded from a source to a destination. When a router receives a data packet on an interface, it determines where to forward the packet by looking in the forwarding table for the best route to a destination. The router then forwards the data packet toward its destination through the appropriate interface.
The Packet Forwarding Engine, which is the central processing element of the router’s forwarding plane, handles the flow of data packets in and out of the router’s physical interfaces. Although the Packet Forwarding Engine contains Layer 3 and Layer 4 header information, it does not contain the packet data itself (the packet's payload).
To control the flow of data packets transiting the device as the packets are being forwarded from a source to a destination, you can apply stateless firewall filters to the input or output of the router’s or switch’s physical interfaces.
To enforce a specified bandwidth and maximum burst size for traffic sent or received on an interface, you can configure policers. Policers are a specialized type of stateless firewall filter and a primary component of the Junos OS class-of-service (CoS).
Flow of Local Packets
Local packets are chunks of data that are destined for or sent by the router. Local packets usually contain routing protocol data, data for IP services such as Telnet or SSH, and data for administrative protocols such as the Internet Control Message Protocol (ICMP). When the Routing Engine receives a local packet, it forwards the packet to the appropriate process or to the kernel, which are both part of the Routing Engine, or to the Packet Forwarding Engine.
The Routing Engine handles the flow of local packets from the router’s physical interfaces and to the Routing Engine.
To control the flow of local packets between the physical interfaces and the Routing Engine, you can apply stateless firewall filters to the input or output of the loopback interface. The loopback interface (lo0) is the interface to the Routing Engine and carries no data packets.
Interdependent Flows of Routing Information and Packets
Figure 1 illustrates the flow of data through a router. Although routing information flows and packet flows are very different from one another, they are also interdependent.
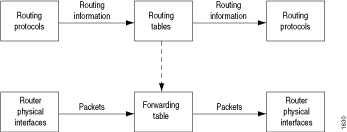
Routing policies determine which routes the Routing Engine places in the forwarding table. The forwarding table, in turn, has an integral role in determining the appropriate physical interface through which to forward a packet.
Stateless and Stateful Firewall Filters
A stateless firewall filter, also known as an access control list (ACL), does not statefully inspect traffic. Instead, it evaluates packet contents statically and does not keep track of the state of network connections. In contrast, a stateful firewall filter uses connection state information derived from other applications and past communications in the data flow to make dynamic control decisions.
The basic purpose of a stateless firewall filter is to enhance security through the use of packet filtering. Packet filtering enables you to inspect the components of incoming or outgoing packets and then perform the actions you specify on packets that match the criteria you specify. The typical use of a stateless firewall filter is to protect the Routing Engine processes and resources from malicious or untrusted packets.
