Understanding How Firewall Filters Are Evaluated
A firewall filter consists of one or more terms, and the order of the terms within a filter is important. Before you configure firewall filters, you should understand how switches evaluate the terms within a filter and how packets are evaluated against the terms.
When a firewall filter consists of a single term, the filter is evaluated as follows:
If the packet matches all the conditions, the action in the
thenstatement is taken.If the packet matches all the conditions, and no action is specified in the
thenstatement, the default action accept is taken.If the packet does not match all the conditions, the switch discards it.
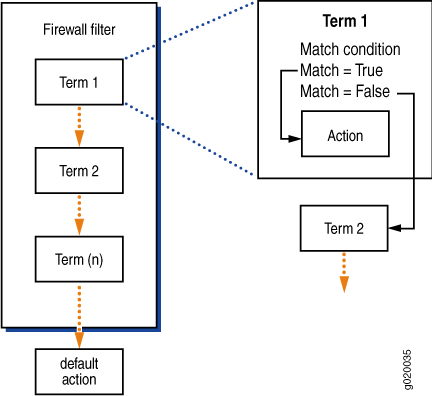
When a firewall filter consists of more than one term, the filter is evaluated sequentially:
The packet is evaluated against the conditions in the
fromstatement in the first term.If the packet matches all the conditions in the term, the action in the
thenstatement is taken and the evaluation ends. Subsequent terms in the filter are not evaluated.If the packet does not match all the conditions in the term, the packet is evaluated against the conditions in the
fromstatement in the second term.This process continues until the packet matches all the conditions in the
fromstatement in one of the subsequent terms or there are no more terms in the filter.If a packet passes through all the terms in the filter without a match, the switch discards it.
The order of conditions in a from statement is not important because
a packet must match all the conditions to be considered a match.
Figure 1 shows how switches evaluate the terms within a firewall filter.
If you do not include a from statement in a term, all packets will match
the term and be processed by the then statement. If a term does not contain a then statement or if an action has not been configured in the then statement,
the term accepts any matching packets.
Every firewall filter contains an implicit deny statement at the end of the
filter, which is equivalent to the following explicit filter term:
term implicit-rule {
then discard;
}
Consequently, a packet that does not match any of the terms in a firewall filter is discarded. If you configure a filter that has no terms, all packets that pass through the filter are discarded.
Firewall filtering is supported on packets that are at least 64 bytes long.
