ON THIS PAGE
Example: Configuring a Filter to Block TCP Access to a Port Except from Specified BGP Peers
This example shows how to configure a standard stateless firewall filter that blocks all TCP connection attempts to port 179 from all requesters except from specified BGP peers.
Requirements
No special configuration beyond device initialization is required before you configure this example.
Overview
In this example, you create a stateless firewall filter that blocks all TCP connection attempts to port 179 from all requesters except the specified BGP peers.
The stateless firewall filter filter_bgp179 matches all packets from the directly connected interfaces on Device A and Device B to the destination port number 179.
Topology
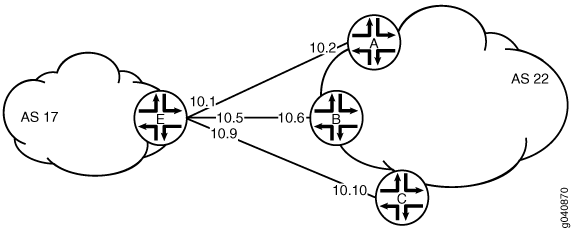
Figure 1 shows the topology used in this example. Device C attempts to make a TCP connection to Device E. Device E blocks the connection attempt. This example shows the configuration on Device E.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, and then copy and paste the commands into the CLI at the [edit] hierarchy level.
Device C
set interfaces ge-1/2/0 unit 10 description to-E set interfaces ge-1/2/0 unit 10 family inet address 10.10.10.10/30 set protocols bgp group external-peers type external set protocols bgp group external-peers peer-as 17 set protocols bgp group external-peers neighbor 10.10.10.9 set routing-options autonomous-system 22
Device E
set interfaces ge-1/2/0 unit 0 description to-A set interfaces ge-1/2/0 unit 0 family inet address 10.10.10.1/30 set interfaces ge-1/2/1 unit 5 description to-B set interfaces ge-1/2/1 unit 5 family inet address 10.10.10.5/30 set interfaces ge-1/0/0 unit 9 description to-C set interfaces ge-1/0/0 unit 9 family inet address 10.10.10.9/30 set interfaces lo0 unit 2 family inet filter input filter_bgp179 set interfaces lo0 unit 2 family inet address 192.168.0.1/32 set protocols bgp group external-peers type external set protocols bgp group external-peers peer-as 22 set protocols bgp group external-peers neighbor 10.10.10.2 set protocols bgp group external-peers neighbor 10.10.10.6 set protocols bgp group external-peers neighbor 10.10.10.10 set routing-options autonomous-system 17 set firewall family inet filter filter_bgp179 term 1 from source-address 10.10.10.2/32 set firewall family inet filter filter_bgp179 term 1 from source-address 10.10.10.6/32 set firewall family inet filter filter_bgp179 term 1 from destination-port bgp set firewall family inet filter filter_bgp179 term 1 then accept set firewall family inet filter filter_bgp179 term 2 then reject
Configuring Device E
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure Device E with a stateless firewall filter that blocks all TCP connection attempts to port 179 from all requestors except specified BGP peers:
Configure the interfaces.
user@E# set interfaces ge-1/2/0 unit 0 description to-A user@E# set interfaces ge-1/2/0 unit 0 family inet address 10.10.10.1/30 user@E# set interfaces ge-1/2/1 unit 5 description to-B user@E# set interfaces ge-1/2/1 unit 5 family inet address 10.10.10.5/30 user@E# set interfaces ge-1/0/0 unit 9 description to-C user@E# set interfaces ge-1/0/0 unit 9 family inet address 10.10.10.9/30
Configure BGP.
[edit protocols bgp group external-peers] user@E# set type external user@E# set peer-as 22 user@E# set neighbor 10.10.10.2 user@E# set neighbor 10.10.10.6 user@E# set neighbor 10.10.10.10
Configure the autonomous system number.
[edit routing-options] user@E# set autonomous-system 17
Define the filter term that accepts TCP connection attempts to port 179 from the specified BGP peers.
[edit firewall family inet filter filter_bgp179] user@E# set term 1 from source-address 10.10.10.2/32 user@E# set term 1 from source-address 10.10.10.6/32 user@E# set term 1 from destination-port bgp user@E# set term 1 then accept
Define the other filter term to reject packets from other sources.
[edit firewall family inet filter filter_bgp179] user@E# set term 2 then reject
Apply the firewall filter to the loopback interface.
[edit interfaces lo0 unit 2 family inet] user@E# set filter input filter_bgp179 user@E# set address 192.168.0.1/32
Results
From configuration mode, confirm your configuration by entering the show firewall, show interfaces, show protocols, and show routing-options commands. If the output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
user@E# show firewall
family inet {
filter filter_bgp179 {
term 1 {
from {
source-address {
10.10.10.2/32;
10.10.10.6/32;
}
destination-port bgp;
}
then accept;
}
term 2 {
then {
reject;
}
}
}
}
user@E# show interfaces
lo0 {
unit 2 {
family inet {
filter {
input filter_bgp179;
}
address 192.168.0.1/32;
}
}
}
ge-1/2/0 {
unit 0 {
description to-A;
family inet {
address 10.10.10.1/30;
}
}
}
ge-1/2/1 {
unit 5 {
description to-B;
family inet {
address 10.10.10.5/30;
}
}
}
ge-1/0/0 {
unit 9 {
description to-C;
family inet {
address 10.10.10.9/30;
}
}
}
user@E# show protocols
bgp {
group external-peers {
type external;
peer-as 22;
neighbor 10.10.10.2;
neighbor 10.10.10.6;
neighbor 10.10.10.10;
}
}
user@E# show routing-options autonomous-system 17;
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
- Verifying That the Filter Is Configured
- Verifying the TCP Connections
- Monitoring Traffic on the Interfaces
Verifying That the Filter Is Configured
Purpose
Make sure that the filter is listed in output of the show firewall filter command.
Action
user@E> show firewall filter filter_bgp179 Filter: filter_bgp179
Verifying the TCP Connections
Purpose
Verify the TCP connections.
Action
From operational mode, run the show system connections
extensive command on Device C and Device E.
The output on Device C shows the attempt to establish a TCP connection. The output on Device E shows that connections are established with Device A and Device B only.
user@C> show system connections extensive | match 10.10.10 tcp4 0 0 10.10.10.9.51872 10.10.10.10.179 SYN_SENT
user@E> show system connections extensive | match 10.10.10 tcp4 0 0 10.10.10.5.179 10.10.10.6.62096 ESTABLISHED tcp4 0 0 10.10.10.6.62096 10.10.10.5.179 ESTABLISHED tcp4 0 0 10.10.10.1.179 10.10.10.2.61506 ESTABLISHED tcp4 0 0 10.10.10.2.61506 10.10.10.1.179 ESTABLISHED
Monitoring Traffic on the Interfaces
Purpose
Use the monitor traffic command to compare the traffic on an interface that establishes a TCP connection with the traffic on an interface that does not establish a TCP connection.
Action
From operational mode, run the monitor traffic command on the Device E interface to Device B and on the Device E interface to Device C. The following sample output verifies that in the first example, acknowledgment (ack) messages are received. In the second example, ack messages are not received.
user@E> monitor traffic size 1500 interface ge-1/2/1.5 19:02:49.700912 Out IP 10.10.10.5.bgp > 10.10.10.6.62096: P 3330573561:3330573580(19) ack 915601686 win 16384 <nop,nop,timestamp 1869518816 1869504850>: BGP, length: 19 19:02:49.801244 In IP 10.10.10.6.62096 > 10.10.10.5.bgp: . ack 19 win 16384 <nop,nop,timestamp 1869518916 1869518816> 19:03:03.323018 In IP 10.10.10.6.62096 > 10.10.10.5.bgp: P 1:20(19) ack 19 win 16384 <nop,nop,timestamp 1869532439 1869518816>: BGP, length: 19 19:03:03.422418 Out IP 10.10.10.5.bgp > 10.10.10.6.62096: . ack 20 win 16384 <nop,nop,timestamp 1869532539 1869532439> 19:03:17.220162 Out IP 10.10.10.5.bgp > 10.10.10.6.62096: P 19:38(19) ack 20 win 16384 <nop,nop,timestamp 1869546338 1869532439>: BGP, length: 19 19:03:17.320501 In IP 10.10.10.6.62096 > 10.10.10.5.bgp: . ack 38 win 16384 <nop,nop,timestamp 1869546438 1869546338>
user@E> monitor traffic size 1500 interface ge-1/0/0.9 18:54:20.175471 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,nop,wscale 0,nop,nop,timestamp 1869009240 0,sackOK,eol> 18:54:23.174422 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,nop,wscale 0,nop,nop,timestamp 1869012240 0,sackOK,eol> 18:54:26.374118 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,nop,wscale 0,nop,nop,timestamp 1869015440 0,sackOK,eol> 18:54:29.573799 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,sackOK,eol> 18:54:32.773493 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,sackOK,eol> 18:54:35.973185 Out IP 10.10.10.9.61335 > 10.10.10.10.bgp: S 573929123:573929123(0) win 16384 <mss 1460,sackOK,eol>
