ON THIS PAGE
Example: Configuring a Stateless Firewall Filter to Protect Against TCP and ICMP Floods
This example shows how to create a stateless firewall filter that protects against TCP and ICMP denial-of-service attacks.
Requirements
No special configuration beyond device initialization is required before configuring stateless firewall filters.
Overview
In this example we create a stateless firewall filter
called protect-RE to police TCP and ICMP packets. It uses
the policers described here:
tcp-connection-policer—This policer limits TCP traffic to 1,000,000 bits per second (bps) with a maximum burst size of 15,000 bytes. Traffic exceeding either limit is discarded.icmp-policer—This policer limits ICMP traffic to 1,000,000 bps with a maximum burst size of 15,000 bytes. Traffic exceeding either limit is discarded.
When specifying limits, the bandwidth limit can be from 32,000 bps to 32,000,000,000 bps and the burst-size limit can be from 1,500 bytes through 100,000,000 bytes. Use the following abbreviations when specifying limits: k (1,000), m (1,000,000), and g (1,000,000,000).
Each policer is incorporated into the action of a filter term. This example includes the following terms:
tcp-connection-term—Polices certain TCP packets with a source address of 192.168.0.0/24 or 10.0.0.0/24. These addresses are defined in thetrusted-addressesprefix list.Filtered packets include
tcp-establishedpackets Thetcp-establishedmatch condition is an alias for the bit-field match conditiontcp-flags “(ack | rst)”, which indicates an established TCP session, but not the first packet of a TCP connection.icmp-term—Polices ICMP packets. All ICMP packets are counted in theicmp-countercounter.
You can move terms within the firewall filter by using
the insert command. See insert in the Junos OS CLI User Guide.
You can apply a stateless firewall to the input or output sides, or both, of an interface. To filter packets transiting the device, apply the firewall filter to any non-Routing Engine interface. To filter packets originating from, or destined for, the Routing Engine, apply the firewall filter to the loopback (lo0) interface.
Figure 1 shows the sample network.
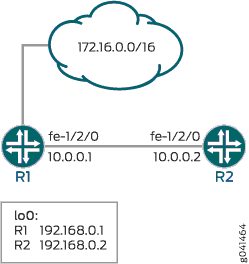
Because this firewall filter limits Routing Engine traffic to TCP packets, routing protocols that use other transport protocols for Layer 4 cannot successfully establish sessions when this filter is active. To demonstrate, this example sets up OSPF between Device R1 and Device R2.
CLI Quick Configuration shows the configuration for all of the devices in Figure 1.
The section #configuration1102__policy-firewall-tcp-icmp-st describes the steps on Device R2.
Configuration
Procedure
CLI Quick Configuration
To quickly configure the stateless firewall filter, copy the following commands to a text file, remove any line breaks, and then paste the commands into the CLI.
Device R1
set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.1/30 set interfaces lo0 unit 0 family inet address 192.168.0.1/32 primary set interfaces lo0 unit 0 family inet address 172.16.0.1/32 set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext peer-as 200 set protocols bgp group ext neighbor 10.0.0.2 set protocols ospf area 0.0.0.0 interface fe-1/2/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 passive set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept set routing-options router-id 192.168.0.1 set routing-options autonomous-system 100
Device R2
set interfaces fe-1/2/0 unit 0 family inet address 10.0.0.2/30 set interfaces lo0 unit 0 family inet filter input protect-RE set interfaces lo0 unit 0 family inet address 192.168.0.2/32 primary set interfaces lo0 unit 0 family inet address 172.16.0.2/32 set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext neighbor 10.0.0.1 peer-as 100 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface fe-1/2/0.0 set policy-options prefix-list trusted-addresses 10.0.0.0/24 set policy-options prefix-list trusted-addresses 192.168.0.0/24 set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept set routing-options router-id 192.168.0.2 set routing-options autonomous-system 200 set firewall family inet filter protect-RE term tcp-connection-term from source-prefix-list trusted-addresses set firewall family inet filter protect-RE term tcp-connection-term from protocol tcp set firewall family inet filter protect-RE term tcp-connection-term from tcp-established set firewall family inet filter protect-RE term tcp-connection-term then policer tcp-connection-policer set firewall family inet filter protect-RE term tcp-connection-term then accept set firewall family inet filter protect-RE term icmp-term from source-prefix-list trusted-addresses set firewall family inet filter protect-RE term icmp-term from protocol icmp set firewall family inet filter protect-RE term icmp-term then policer icmp-policer set firewall family inet filter protect-RE term icmp-term then count icmp-counter set firewall family inet filter protect-RE term icmp-term then accept set firewall policer tcp-connection-policer filter-specific set firewall policer tcp-connection-policer if-exceeding bandwidth-limit 1m set firewall policer tcp-connection-policer if-exceeding burst-size-limit 15k set firewall policer tcp-connection-policer then discard set firewall policer icmp-policer filter-specific set firewall policer icmp-policer if-exceeding bandwidth-limit 1m set firewall policer icmp-policer if-exceeding burst-size-limit 15k set firewall policer icmp-policer then discard
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Use the CLI Editor in Configuration Mode.
To configure stateless firewall filter to discard :
Configure the device interfaces.
[edit interfaces fe-1/2/0 unit 0 family inet ] user@R2# set address 10.0.0.2/30 [edit interfaces lo0 unit 0 family inet] user@R2# set address 192.168.0.2/32 primary user@R2# set address 172.16.0.2/32
Configure the BGP peering session.
[edit protocols bgp group ext] user@R2# set type external user@R2# set export send-direct user@R2# set neighbor 10.0.0.1 peer-as 100
Configure the autonomous system (AS) number and router ID.
[edit routing-options] user@R2# set autonomous-system 200 user@R2# set router-id 192.168.0.2
Configure OSPF.
[edit protocols ospf area 0.0.0.0] user@R2# set interface lo0.0 passive user@R2# set interface fe-1/2/0.0
Define the list of trusted addresses.
[edit policy-options prefix-list trusted-addresses] user@R2# set 10.0.0.0/24 user@R2# set 192.168.0.0/24
Configure a policy to advertise direct routes.
[edit policy-options policy-statement send-direct term 1] user@R2# set from protocol direct user@R2# set then accept
Configure the TCP policer.
[edit firewall policer tcp-connection-policer] user@R2# set filter-specific user@R2# set if-exceeding bandwidth-limit 1m user@R2# set if-exceeding burst-size-limit 15k user@R2# set then discard
Create the ICMP policer.
[edit firewall policer icmp-policer] user@R2# set filter-specific user@R2# set if-exceeding bandwidth-limit 1m user@R2# set if-exceeding burst-size-limit 15k user@R2# set then discard
Configure the TCP filter rules.
[edit firewall family inet filter protect-RE term tcp-connection-term] user@R2# set from source-prefix-list trusted-addresses user@R2# set from protocol tcp user@R2# set from tcp-established user@R2# set then policer tcp-connection-policer user@R2# set then accept
Configure the ICMP filter rules.
[edit firewall family inet filter protect-RE term icmp-term] user@R2# set from source-prefix-list trusted-addresses user@R2# set from protocol icmp user@R2# set then policer icmp-policer user@R2# set then count icmp-counter user@R2# set then accept
Apply the filter to the loopback interface.
[edit interfaces lo0 unit 0] user@R2# set family inet filter input protect-RE
Results
Confirm your configuration by entering the show
interfaces, show protocols, show policy-options, show routing-options, and show firewall commands
from configuration mode. If the output does not display the intended
configuration, repeat the instructions in this example to correct
the configuration.
user@R2# show interfaces
fe-1/2/0 {
unit 0 {
family inet {
address 10.0.0.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
filter {
input protect-RE;
}
address 192.168.0.2/32 {
primary;
}
address 172.16.0.2/32;
}
}
}
user@R2# show protocols
bgp {
group ext {
type external;
export send-direct;
neighbor 10.0.0.1 {
peer-as 100;
}
}
}
ospf {
area 0.0.0.0 {
interface lo0.0 {
passive;
}
interface fe-1/2/0.0;
}
}
user@R2# show policy-options
prefix-list trusted-addresses {
10.0.0.0/24;
192.168.0.0/24;
}
policy-statement send-direct {
term 1 {
from protocol direct;
then accept;
}
}
user@R2# show routing-options router-id 192.168.0.2; autonomous-system 200;
user@R2# show firewall
family inet {
filter protect-RE {
term tcp-connection-term {
from {
source-prefix-list {
trusted-addresses;
}
protocol tcp;
tcp-established;
}
then {
policer tcp-connection-policer;
accept;
}
}
term icmp-term {
from {
source-prefix-list {
trusted-addresses;
}
protocol icmp;
}
then {
policer icmp-policer;
count icmp-counter;
accept;
}
}
}
}
policer tcp-connection-policer {
filter-specific;
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 15k;
}
then discard;
}
policer icmp-policer {
filter-specific;
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 15k;
}
then discard;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
To verify the TCP policer, you can use a packet generation tool. This task is not shown here.
- Displaying Stateless Firewall Filter That Are in Effect
- Using telnet to Verify the tcp-established Condition in the TCP Firewall Filter
- Using telnet to Verify the Trusted Prefixes Condition in the TCP Firewall Filter
- Using OSPF to Verify the TCP Firewall Filter
- Verifying the ICMP Firewall Filter
Displaying Stateless Firewall Filter That Are in Effect
Purpose
Verify the configuration of the firewall filter.
Action
From operational mode, enter the show firewall command.
user@R2> show firewall Filter: protect-RE Counters: Name Bytes Packets icmp-counter 0 0 Policers: Name Bytes Packets icmp-policer 0 tcp-connection-policer 0
Meaning
The output shows the filter, the counter, and the policers that are in effect on Device R2.
Using telnet to Verify the tcp-established Condition in the TCP Firewall Filter
Purpose
Make sure that telnet traffic works as expected.
Action
Verify that the device can establish only TCP sessions
with hosts that meet the from tcp-established condition.
From Device R2, make sure that the BGP session with Device R1 is established.
user@R2> show bgp summary | match down Groups: 1 Peers: 1 Down peers: 0
From Device R2, telnet to Device R1.
user@R2> telnet 192.168.0.1 Trying 192.168.0.1... Connected to R1.example.net. Escape character is '^]'. R1 (ttyp4) login:
From Device R1, telnet to Device R2.
user@R1> telnet 192.168.0.2 Trying 192.168.0.2... telnet: connect to address 192.168.0.2: Operation timed out telnet: Unable to connect to remote host
On Device R2, deactivate the
from tcp-establishedmatch condition.[edit firewall family inet filter protect-RE term tcp-connection-term] user@R2# deactivate from tcp-established user@R2# commit
From Device R1, try again to telnet to Device R2.
user@R1> telnet 192.168.0.1 Trying 192.168.0.2... Connected to R2.example.net. Escape character is '^]'. R2 (ttyp4) login:
Meaning
Verify the following information:
As expected , the BGP session is established. The
from tcp-establishedmatch condition is not expected to block BGP session establishment.From Device R2, you can telnet to Device R1. Device R1 has no firewall filter configured, so this is the expected behavior.
From Device R1, you cannot telnet to Device R2. Telnet uses TCP as the transport protocol, so this result might be surprising. The cause for the lack of telnet connectivity is the
from tcp-establishedmatch condition. This match condition limits the type of TCP traffic that is accepted of Device R2. After this match condition is deactivated, the telnet session is successful.
Using telnet to Verify the Trusted Prefixes Condition in the TCP Firewall Filter
Purpose
Make sure that telnet traffic works as expected.
Action
Verify that the device can establish only telnet sessions
with a host at an IP address that matches one of the trusted source
addresses. For example, log in to the device with the telnet command from another host with one of the trusted address prefixes.
Also, verify that telnet sessions with untrusted source addresses
are blocked.
From Device R1, telnet to Device R2 from an untrusted source address.
user@R1> telnet 172.16.0.2 source 172.16.0.1 Trying 172.16.0.2... ^C
From Device R2, add 172.16/16 to the list of trusted prefixes.
[edit policy-options prefix-list trusted-addresses] user@R2# set 172.16.0.0/16 user@R2# commit
From Device R1, try again to telnet to Device R2.
user@R1> telnet 172.16.0.2 source 172.16.0.1 Trying 172.16.0.2... Connected to R2.example.net. Escape character is '^]'. R2 (ttyp4) login:
Meaning
Verify the following information:
From Device R1, you cannot telnet to Device R2 with an unstrusted source address. After the 172.16/16 prefix is added to the list of trusted prefixes, the telnet request from source address 172.16.0.1 is accepted.
OSPF session establishment is blocked. OSPF does not use TCP as its transport protocol. After the
from protocol tcpmatch condition is deactivated, OSPF session establishment is not blocked.
Using OSPF to Verify the TCP Firewall Filter
Purpose
Make sure that OSPF traffic works as expected.
Action
Verify that the device cannot establish OSPF connectivity.
From Device R1, check the OSPF sessions.
user@R1> show ospf neighbor Address Interface State ID Pri Dead 10.0.0.2 fe-1/2/0.0 Init 192.168.0.2 128 34
From Device R2, check the OSPF sessions.
user@R2> show ospf neighbor
From Device R2, remove the
from protocol tcpmatch condition.[edit firewall family inet filter protect-RE term tcp-connection-term] user@R2# deactivate from protocol user@R2# commit
From Device R1, recheck the OSPF sessions.
user@R1> show ospf neighbor Address Interface State ID Pri Dead 10.0.0.2 fe-1/2/0.0 Full 192.168.0.2 128 36
From Device R2, recheck the OSPF sessions.
user@R2> show ospf neighbor Address Interface State ID Pri Dead 10.0.0.1 fe-1/2/0.0 Full 192.168.0.1 128 39
Meaning
Verify the following information:
OSPF session establishment is blocked. OSPF does not use TCP as its transport protocol. After the
from protocol tcpmatch condition is deactivated, OSPF session establishment is successful.
Verifying the ICMP Firewall Filter
Purpose
Verify that ICMP packets are being policed and counted. Also make sure that ping requests are discarded when the requests originate from an untrusted source address.
Action
Undo the configuration changes made in previous verification steps.
Reactivate the TCP firewall settings, and delete the 172.16/16 trusted source address.
[edit firewall family inet filter protect-RE term tcp-connection-term] user@R2# activate from protocol user@R2# activate from tcp-established [edit policy-options prefix-list trusted-addresses] user@R2# delete 172.16.0.0/16 user@R2# commit
From Device R1, ping the loopback interface on Device R2.
user@R1> ping 192.168.0.2 rapid count 600 size 2000 PING 192.168.0.2 (192.168.0.2): 2000 data bytes !!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!!!.!!!!!!!!.!!!!!!!!.!!!!!!!! --- 192.168.0.2 ping statistics --- 600 packets transmitted, 536 packets received, 10% packet loss pinground-trip min/avg/max/stddev = 2.976/3.405/42.380/2.293 ms
From Device R2, check the firewall statistics.
user@R2> show firewall Filter: protect-RE Counters: Name Bytes Packets icmp-counter 1180804 1135 Policers: Name Bytes Packets icmp-policer 66 tcp-connection-policer 0
From an untrusted source address on Device R1, send a ping request to Device R2’s loopback interface.
user@R1> ping 172.16.0.2 source 172.16.0.1 PING 172.16.0.2 (172.16.0.2): 56 data bytes ^C --- 172.16.0.2 ping statistics --- 14 packets transmitted, 0 packets received, 100% packet loss
Meaning
Verify the following information:
The ping output shows that 10% packet loss is occurring.
The ICMP packet counter is incrementing, and the icmp-policer is incrementing.
Device R2 does not send ICMP responses to the
ping 172.16.0.2 source 172.16.0.1command.
