ON THIS PAGE
Configuring Protocol-Independent Firewall Filter for Port Mirroring
Example: Mirroring Employee Web Traffic with a Firewall Filter
Layer 2 Port Mirroring of PE Router or PE Switch Logical Interfaces
Layer 2 Port Mirroring of PE Router or PE Switch Aggregated Ethernet Interfaces
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a Bridge Domain
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a VPLS Routing Instance
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a VLAN
Example: Layer 2 Port Mirroring for a Layer 2 VPN with LAG Links
Configuring Port Mirroring on Logical Interfaces
Layer 2 Port Mirroring Firewall Filters
This topic describes the following information:
- Layer 2 Port Mirroring Firewall Filters Overview
- Mirroring of Packets Received or Sent on a Logical Interface
- Mirroring of Packets Forwarded or Flooded to a VLAN
- Mirroring of Packets Forwarded or Flooded to a VPLS Routing Instance
Layer 2 Port Mirroring Firewall Filters Overview
On an MX Series router and on an EX Series switch, you can configure a firewall filter term to specify that Layer 2 port mirroring is to be applied to all packets at the interface to which the firewall filter is applied.
You can apply a Layer 2 port-mirroring firewall filter to the input or output logical interfaces (including aggregated Ethernet logical interfaces), to traffic forwarded or flooded to a VLAN, or traffic forwarded or flooded to a VPLS routing instance.
MX Series routers and EX Series switches support Layer 2
port mirroring of VPLS (family ethernet-switching or family vpls) traffic and Layer 2 VPN traffic with family ccc in a Layer 2 environment
Within a firewall filter term, you can specify the
Layer 2 port-mirroring properties under the then statement
in either of the following ways:
Implicitly reference the Layer 2 port mirroring properties in effect on the port.
Explicitly reference a particular named instance of Layer 2 port mirroring.
When configuring a Layer 2 port-mirroring firewall filter,
do not include the optional from statement that specifies
match conditions based on the route source address. Omit this statement
so that all packets are considered to match and all actions and action-modifiers specified in the then statement are taken.
If you want to mirror all incoming packets, then you must not use the from statement; /* comment: one configure filter terms with from if they are interested in mirroring only a subset of packets.
If you associate integrated routing and bridging (IRB) with
the VLAN (or VPLS routing instance), and also configure within the
VLAN (or VPLS routing instance) a forwarding table filter with the port-mirror or port-mirror-instance action, then
the IRB packet is mirrored as a Layer 2 packet. You can disable this
behavior by configuring the no-irb-layer-2-copy statement in the
VLAN (or VPLS routing instance).
For a detailed description of how to configure a Layer 2 port-mirroring firewall filter, see Defining a Layer 2 Port-Mirroring Firewall Filter.
For detailed information about how you can use Layer 2 port-mirroring firewall filters with MX Routers and EX Series switches configured as provider edge (PE) routers or PE switches, see Understanding Layer 2 Port Mirroring of PE Router Logical Interfaces. For detailed information about configuring firewall filters in general (including in a Layer 3 environment), see the Routing Policies, Firewall Filters, and Traffic Policers User Guide.
Mirroring of Packets Received or Sent on a Logical Interface
To mirror Layer 2 traffic received or sent on a logical interface, apply a port-mirroring firewall filter to the input or output of the interface.
A port-mirroring firewall filter can also be applied to an aggregated-Ethernet logical interface. For details, see Understanding Layer 2 Port Mirroring of PE Router Aggregated Ethernet Interfaces.
If port-mirroring firewall filters are applied at both the input and output of a logical interface, two copies of each packet are mirrored. To prevent the router or switch from forwarding duplicate packets to the same destination, you can enable the “mirror-once” option for Layer 2 port mirroring in the global instance for the Layer 2 packet address family.
Mirroring of Packets Forwarded or Flooded to a VLAN
To mirror Layer 2 traffic forwarded to or flooded to a VLAN, apply a port-mirroring firewall filter to the input to the forwarding table or flood table. Any packet received for the VLAN forwarding or flood table and that matches the filter conditions is mirrored.
For more information about VLANs, see Layer 2 Bridge Domains Overview. For information about flooding behavior in a VLAN, see Configure Layer 2 Learning and Forwarding for Bridge Domains Functioning as Switches.
When you configure port mirroring on any interface under one VLAN, the mirrored packet can move to an external analyzer located on different VLANs.
Mirroring of Packets Forwarded or Flooded to a VPLS Routing Instance
To mirror Layer 2 traffic forwarded to or flooded to a VPLS routing instance, apply a port-mirroring firewall filter to the input to the forwarding table or flood table. Any packet received for the VPLS routing instance forwarding or flood table and that matches the filter condition is mirrored.
For more information about VPLS routing instances, see Configuring a VPLS Routing Instance and Configuring VLAN Identifiers for Bridge Domains and VPLS Routing Instances. For information about flooding behavior in VPLS, see the Junos OS VPNs Library for Routing Devices.
Defining a Layer 2 Port-Mirroring Firewall Filter
For virtual private LAN service (VPLS) traffic (family ethernet-switching or family vpls) and for Layer 2 VPNs with family cccon MX Series routers
and on EX Series switches only, you can define a firewall filter that
specifies Layer 2 port mirroring as the action to be performed
if a packet matches the conditions configured in the firewall filter
term.
You can use a Layer 2 port-mirroring firewall filter in the following ways:
To mirror packets received or sent on a logical interface.
To mirror packets forwarded or flooded to a VLAN.
To mirror packets forwarded or flooded to a VPLS routing instance.
To mirror tunnel interface input packets only to multiple destinations.
For a summary of the three types of Layer 2 port-mirroring you can configure on an MX Series router and on an EX Series switch, see Application of Layer 2 Port Mirroring Types.
To define a firewall filter with a Layer 2 port-mirroring action:
Configuring Protocol-Independent Firewall Filter for Port Mirroring
On MX Series routers with MPCs, you can configure a firewall filter to mirror Layer 2 and Layer 3 packets at a global level and at an instance level. When port mirror is configured at ingress or egress, the packet entering or exiting an interface is copied and the copies are sent to the local interface for local monitoring.
Starting with
Junos OS Release 13.3R6, only MPC interfaces support family any to do port mirroring. DPC interfaces do
not support family any.
Typically, the firewall filter is configured such that it mirrors either Layer 2 or Layer 3 packets based on the family configured at the interface. However, in case of an integrated routing and bridging (IRB) interface, Layer 2 packets are not completely mirrored because IRB interfaces are configured to mirror only Layer 3 packets. On such an interface, you can configure a firewall filter and port mirroring parameters in the family any to ensure that a packet is completely mirrored irrespective of whether it is a Layer 2 or a Layer 3 packet.
For port mirroring at an instance, you can configure one or more families such as inet, inet6, ccc, and vpls simultaneously for the same instance.
In case of Layer 2 port mirroring, VLAN tags, MPLS headers are retained and can be seen in the mirrored copy at egress.
For VLAN normalization, the information before normalization is seen for a mirrored packet at ingress. Similarly, at egress, the information after normalization is seen for the mirrored packet.
Before you begin configuring port mirroring, you must configure valid physical interfaces.
To configure a protocol-independent firewall filter for port mirroring:
Example: Mirroring Employee Web Traffic with a Firewall Filter
Requirements
This example uses the following hardware and software components:
One switch
Junos 14.1X53-D20
Overview
In this example, xe-0/0/0 and xe-0/0/6 serve as connections for employee computers. Interface xe-0/0/47 is connected to a device running an analyzer application.
Rather than mirror all traffic, it is usually desirable to mirror only certain traffic. This is a more-efficient use of your bandwidth and hardware and might be necessary because of constraints on these assets. This example mirrors only traffic sent from employee computers to the Web.
Topology
Figure 1 shows the network topology for this example.
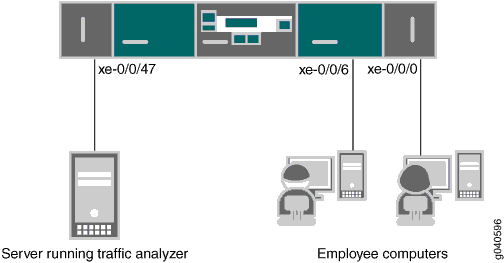
Configuring
To specify that the only traffic that will be mirrored is traffic sent by employees to the Web, perform the tasks explained in this section. To select this traffic for mirroring, you use a firewall filter to specify this traffic and direct it to a port-mirroring instance.
Procedure
CLI Quick Configuration
To quickly configure local port mirroring of traffic from employee computers that is destined for the Web, copy the following commands and paste them into a switch terminal window:
[edit] set forwarding-options port-mirroring family inet output interface xe-0/0/47.0 next-hop 192.0.2.100/24 set firewall family inet filter watch-employee term employee-to-corp from destination-address 192.0.2.16/24 set firewall family inet filter watch-employee term employee-to-corp from source-address 192.0.2.16/24 set firewall family inet filter watch-employee term employee-to-corp then accept set firewall family inet filter watch-employee term employee-to-web from destination-port 80 set firewall family inet filter watch-employee term employee-to-web then port-mirror set interfaces xe-0/0/0 unit 0 family address 192.0.1.1/24 set interfaces xe-0/0/6 unit 0 family address 192.0.1.2/24 set interfaces xe-0/0/47 unit 0 family address 192.0.1.3/24 set interfaces xe-0/0/0 unit 0 family inet filter input watch-employee set interfaces xe-0/0/6 unit 0 family inet filter input watch-employee
The ip-address command under set forwarding
options port-mirroring family inet output is not supported
for the EX9253 platform.
Step-by-Step Procedure
To configure local port mirroring of employee to web traffic from the two ports connected to employee computers:
Configure a port-mirroring instance, including the output interface and the IP address of the device running the analyzer application as the next hop. (Configure only the output—the input comes from the filter.) You must also specifying that the mirror is for IPv4 traffic (
family inet).[edit forwarding-options] user@switch# set forwarding-options port-mirroring family inet output interface xe-0/0/47.0 next-hop 192.0.2.100/28
Configure an IPv4 (
family inet) firewall filter calledwatch-employeethat includes a term to match traffic sent to the Web and send it to the port-mirroring instance. Traffic sent to and arriving from the corporate subnet (destination or source address of192.0.nn.nn/24) does not need to be copied, so first create another term to accept that traffic before it reaches the term that sends Web traffic to the instance:[edit firewall family inet] er@switch# set filter watch-employee term employee-to-corp from destination-address 192.0.nn.nn/24 user@switch# set filter watch-employee term employee-to-corp from source-address 192.0.nn.nn/24 user@switch# set filter watch-employee term employee-to-corp then accept user@switch# set filter watch-employee term employee-to-web from destination-port 80 user@switch# set filter watch-employee term employee-to-web then port-mirror
Configure addresses for the IPv4 interfaces connected to the employee computers and the analyzer device:
[edit interfaces] user@switch# set xe-0/0/0 unit 0 family inet address 192.0.1.1/24 user@switch# set xe-0/0/6 unit 0 family inet address 192.0.1.2/24 user@switch# set interfaces xe-0/0/47 unit 0 family address 192.0.1.3/24
Apply the firewall filter to the appropriate interfaces as an ingress filter:
[edit interfaces] user@switch# set xe-0/0/0 unit 0 family inet filter input watch-employee user@switch# set xe-0/0/6 unit 0 family inet filter input watch-employee
Results
Check the results of the configuration:
[edit]
user@switch# show
forwarding-options {
port-mirroring {
employee-web-monitor {
output {
ip-address 192.0.2.100.0;
}
}
}
}
}
}
...
firewall family inet {
filter watch-employee {
term employee-to-corp {
from {
destination-address 192.0.2.16/24;
source-address 192.0.2.16/24;
}
then accept {
}
term employee-to-web {
from {
destination-port 80;
}
then port-mirror;
}
}
}
...
interfaces {
xe-0/0/0 {
unit 0 {
family inet {
filter {
input watch-employee;
}
}
}
}
xe-0/0/6 {
family inet {
filter {
input watch-employee;
}
}
}
}
Verification
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer has been created on the switch with the appropriate input interfaces and appropriate output interface.
Action
You can verify that the port mirror analyzer has been
configured as expected using the show forwarding-options port-mirroring command.
user@switch> show forwarding-options port-mirroring
Instance Name: &global_instance
Instance Id: 1
Input parameters:
Rate : 1
Run-length : 0
Maximum-packet-length : 0
Output parameters:
Family State Destination Next-hop
inet up xe-0/0/47.0 192.0.2.100 Meaning
This output shows that the port-mirroring instance
has a ratio of 1 (mirroring every packet, the default setting) and
the maximum size of the original packet that was mirrored (0 indicates the entire packet). If the state of the
output interface is down or if the output interface is not configured,
the value of state will be down and the
instance will not be programmed for mirroring.
Layer 2 Port Mirroring of PE Router or PE Switch Logical Interfaces
For a router or switch configured as a provider edge (PE) device on the customer-facing edge of a service provider network, you can apply a Layer 2 port-mirroring firewall filter at the following ingress and egress points to mirror the traffic between the router or switch and customer edge (CE) devices, which are typically also routers and Ethernet switches.
Table 1 describes the ways in which you can apply Layer 2 port-mirroring firewall filters to a router or switch configured as a PE device.
Point of Application |
Scope of Mirroring |
Notes |
Configuration Details |
|---|---|---|---|
Ingress Customer-Facing Logical Interface |
Packets originating within a service provider customer’s network, sent first to a CE device, and sent next to the PE device. |
You can also configure aggregated Ethernet interfaces between CE devices and PE devices for VPLS routing instances. Traffic is load-balanced across all of the links in the aggregated interface. Traffic received on an aggregated Ethernet interface is forwarded over a different interface based on a lookup of the destination MAC (DMAC) address:
|
See Applying Layer 2 Port Mirroring to a Logical Interface. For more information about VPLS routing instances, see Configuring a VPLS Routing Instance and Configuring VLAN Identifiers for Bridge Domains and VPLS Routing Instances. |
Egress Customer-Facing Logical Interface |
Unicast packets being forwarded by the PE device to another PE device. NOTE: If you apply a port-mirroring filter to the output for a logical interface, only unicast packets are mirrored. To mirror multicast, unknown unicast, and broadcast packets, apply a filter to the input to the flood table of a VLAN or VPLS routing instance. |
||
Input to a VLAN Forwarding Table or Flood Table |
Forwarding traffic or flood traffic sent to the VLAN from a CE device. |
Forwarding and flood traffic typically consists of broadcast packets, multicast packets, unicast packets with an unknown destination MAC address, or packets with a MAC entry in the DMAC routing table. |
See Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a Bridge Domain. For information about flooding behavior in VPLS, see the Junos OS VPNs Library for Routing Devices. |
Input to a VPLS Routing Instance Forwarding Table or Flood Table |
Forwarding traffic or flood traffic sent to the VPLS routing instance from a CE device. |
See Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a VPLS Routing Instance. For information about flooding behavior in VPLS, see the Junos OS VPNs Library for Routing Devices. |
Layer 2 Port Mirroring of PE Router or PE Switch Aggregated Ethernet Interfaces
An aggregated Ethernet interface is a virtual aggregated link that consists of a set of physical interfaces of the same speed and operating in full-duplex link connection mode. You can configure aggregated Ethernet interfaces between CE devices and PE devices for VPLS routing instances. Traffic is load-balanced across all of the links in the aggregated interface. If one or more links in the aggregated interface fails, the traffic is switched to the remaining links.
You can apply a Layer 2 port-mirroring firewall filter to an aggregated Ethernet interface to configure port mirroring at the parent interface. However, if any child interfaces are bound to different Layer 2 port-mirroring instances, packets received at the child interfaces will be mirrored to the destinations specified by their respective port-mirroring instances. Thus, multiple child interfaces can mirror packets to multiple destinations.
For example, suppose the parent aggregated Ethernet interface
instance ae0 has two child interfaces:
xe-2/0/0xe-3/1/2
Suppose that these child interfaces on ae0 are bound to two different Layer 2 port-mirroring instances:
pm_instance_A—A named instance of Layer 2 port-mirroring, bound to child interfacexe-2/0/0.pm_instance_B—A named instance of Layer 2 port-mirroring, bound to child interfacexe-3/1/2.
Now suppose you apply a Layer 2 port-mirroring firewall
filter to the Layer 2 traffic sent on ae0.0 (logical unit 0 on the aggregated Ethernet interface instance 0). This enables port mirroring on ae0.0, which has the following effect on the processing of
traffic received on the child interfaces for which Layer 2 port-mirroring
properties are specified:
The packets received on
xe-2/0/0are mirrored to the output interfaces configured in port-mirroring instancepm_instance_A.The packets received on
xe-3/1/2.0are mirrored to the output interfaces configured in port-mirroring instancepm_instance_B.
Because pm_instance_A and pm_instance_B can specify different packet-selection properties or mirror destination
properties, the packets received on xe-2/0/0 and xe-3/1/2.0 can mirror different packets to different destinations.
Applying Layer 2 Port Mirroring to a Logical Interface
You can apply a Layer 2 port-mirroring firewall filter to the input or to the output of a logical interface, including an aggregated Ethernet logical interface. Only packets of the address-type family specified by the filter action are mirrored.
Before you begin, complete the following task:
Define a Layer 2 port-mirroring firewall filter to be applied to the input to a logical interface or output to a logical interface. For details, see Defining a Layer 2 Port-Mirroring Firewall Filter.
Note:This configuration task shows two Layer 2 port-mirroring firewall filters: one filter applied to the logical interface ingress traffic, and one filter applied to the logical interface egress traffic.
To apply a Layer 2 port-mirroring firewall filter to an input or output logical interface:
Applying Layer 2 Port Mirroring to Family ccc Traffic with Demux Logical Interfaces Over Aggregated Ethernet
This topic provides guidelines and steps to help you set up the demux logical interfaces for this purpose of saving on the use of member physical interfaces in an AE bundle.
Guidelines
We'll point out the configuration elements that are specific to this use of configuring the demux logical interfaces over aggregated Ethernet interfaces.
-
Configure the family as
cccfor-
The port-mirroring configuration at
edit forwarding-options port mirroring family -
The firewall filter configuration at
edit firewall family -
The demux interface configuration at
edit interfaces demux0 unit 0 family
-
-
Ensure that the configurations of families for firewall filters and port mirroring are either (1) the same or (2) in the same hierarchy.
-
You can configure the demux interface over an
aeinterface for global port mirroring and for port mirroring instances. -
For the firewall filter, in addition to using
cccas the family:-
Use
port-mirroras the action for the filter. -
Apply the filter on the demux interface.
-
- Configure the
aeinterface as the demux logical interface's underlying interface by using theunderlying-interfacestatement, like this:set interfaces demux0 unit 0 demux-options underlying-interface ae0
Configuration Sample
The following is a sparse configuration—we just want to show you a picture of how the preceding guidelines would play out in a sample configuration.
set interfaces xe-0/0/2:0 gigether-options 802.3ad ae0 set interfaces xe-0/0/2:1 gigether-options 802.3ad ae1 set interfaces xe-0/0/2:2 encapsulation ethernet-bridge set interfaces xe-0/0/2:2 unit 0 family bridge set interfaces xe-0/0/2:3 encapsulation ethernet-bridge set interfaces xe-0/0/2:3 unit 0 family bridge set interfaces ae0 flexible-vlan-tagging set interfaces ae0 encapsulation flexible-ethernet-services set interfaces ae1 flexible-vlan-tagging set interfaces ae1 encapsulation flexible-ethernet-services set interfaces demux0 unit 0 encapsulation vlan-ccc set interfaces demux0 unit 0 vlan-id 300 set interfaces demux0 unit 0 demux-options underlying-interface ae0 set interfaces demux0 unit 0 family ccc filter input port-mirror set interfaces demux0 unit 1 encapsulation vlan-ccc set interfaces demux0 unit 1 vlan-id 300 set interfaces demux0 unit 1 demux-options underlying-interface ae1 set interfaces demux0 unit 1 family ccc set forwarding-options port-mirroring input rate 1 set forwarding-options port-mirroring family ccc output interface xe-0/0/2:3.0 set firewall family ccc filter port-mirror term term1 then count Counter1 set firewall family ccc filter port-mirror term term1 then port-mirror set protocols l2circuit local-switching interface demux0.0 end-interface interface demux0.1 set protocols mpls interface demux0.0 set protocols mpls interface demux0.1 set bridge-domains br1 interface xe-0/0/2:0.0 set bridge-domains br1 interface xe-0/0/2:3.0 set bridge-domains br1 interface xe-0/0/2:1.0 set bridge-domains br2 vlan-id 300
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a Bridge Domain
You can apply a Layer 2 port-mirroring firewall filter to traffic being forwarded or flooded to a bridge domain. Only packets of the specified family type and forwarded or flooded to that bridge domain are mirrored.
Before you begin, complete the following task:
Define a Layer 2 port-mirroring firewall filter to be applied to the traffic being forwarded to a bridge domain or flooded to a bridge domain. For details, see Defining a Layer 2 Port-Mirroring Firewall Filter.
Note:This configuration task shows two Layer_2 port-mirroring firewall filters: one filter applied to the bridge domain forwarding table ingress traffic, and one filter applied to the bridge domain flood table ingress traffic.
To apply a Layer 2 port-mirroring firewall filter to the forwarding table or flood table of a bridge domain:
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a VPLS Routing Instance
You can apply a Layer 2 port-mirroring firewall filter to traffic being forwarded or flooded to a VPLS routing instance. Only packets of the specified family type and forwarded or flooded to that VPLS routing instance are mirrored.
Before you begin, complete the following task:
Define a Layer 2 port-mirroring firewall filter to be applied to the traffic being forwarded to a VPLS routing instance or flooded to a VLAN. For details, see Defining a Layer 2 Port-Mirroring Firewall Filter.
Note:This configuration task shows two Layer_2 port-mirroring firewall filters: one filter applied to the VPLS routing instance forwarding table ingress traffic, and one filter applied to the VPLS routing instance flood table ingress traffic.
To apply a Layer 2 port-mirroring firewall filter to the forwarding table or flood table of a VPLS routing instance:
Applying Layer 2 Port Mirroring to Traffic Forwarded or Flooded to a VLAN
You can apply a Layer 2 port-mirroring firewall filter to traffic being forwarded or flooded to a VLAN. Only packets of the specified family type and forwarded or flooded to that VLAN are mirrored.
Before you begin, complete the following task:
Define a Layer 2 port-mirroring firewall filter to be applied to the traffic being forwarded to a VLAN or flooded to a VLAN. For details, see Defining a Layer 2 Port-Mirroring Firewall Filter.
Note:This configuration task shows two Layer_2 port-mirroring firewall filters: one filter applied to the VLAN forwarding table ingress traffic, and one filter applied to the VLAN flood table ingress traffic.
To apply a Layer 2 port-mirroring firewall filter to the forwarding table or flood table of a VLAN:
Example: Layer 2 Port Mirroring at a Logical Interface
The following steps describe an example in which the global port-mirroring instance and a port-mirroring firewall filter are used to configure Layer 2 port mirroring for the input to a logical interface.
Configure the VLAN example-bd-with-analyzer, which contains the external packet analyzer, and the VLAN example-bd-with-traffic, which contains the source and destination of the Layer 2 traffic being mirrored:
[edit] bridge-domains { example-bd-with-analyzer { # Contains an external traffic analyzer vlan-id 1000; interface ge-2/0/0.0; # External analyzer } example-bd-with-traffic { # Contains traffic input and output interfaces vlan-id 1000; interface ge-2/0/6.0; # Traffic input port interface ge-3/0/1.2; # Traffic output port } }Assume that logical interface ge-2/0/0.0 is associated with an external traffic analyzer that is to receive port-mirrored packets. Assume that logical interfaces ge-2/0/6.0 and ge-3/0/1.2 will be traffic input and output ports, respectively.
Configure Layer 2 port-mirroring for the global instance, with the port-mirroring destination being the VLAN interface associated with the external analyzer (logical interface ge-2/0/0.0 on VLAN example-bd-with-analyzer). Be sure to enable the option that allows filters to be applied to this port-mirroring destination:
[edit] forwarding-options { port-mirroring { input { rate 10; run-length 5; } family ethernet-switching { output { interface ge-2/0/0.0; # Mirror packets to the external analyzer no-filter-check; # Allow filters on the mirror destination interface } } } }The
inputstatement at the[edit forwarding-options port-mirroring]hierarchy level specifies that sampling begins every tenth packet and that each of the first five packets selected are to be mirrored.The
outputstatement at the[edit forwarding-options port-mirroring family ethernet-switching]hierarchy level specifies the output mirror interface for Layer 2 packets in a bridging environment:Logical interface ge-2/0/0.0, which is associated with the external packet analyzer, is configured as the port-mirroring destination.
The optional
no-filter-checkstatement allows filters to be configured on this destination interface.
Configure the Layer 2 port-mirroring firewall filter example-bridge-pm-filter:
[edit] firewall { family ethernet-switching { filter example-bridge-pm-filter { term example-filter-terms { then { accept; port-mirror; } } } } }When this firewall filter is applied to the input or output of a logical interface for traffic in a bridging environment, Layer 2 port mirroring is performed according to the input packet-sampling properties and mirror destination properties configured for the Layer 2 port mirroring global instance. Because this firewall filter is configured with the single, default filter action accept, all packets selected by the input properties (rate = 10 and run-length = 5) match this filter.
Configure the logical interfaces:
[edit] interfaces { ge-2/0/0 { # Define the interface to the external analyzer encapsulation ethernet-bridge; unit 0 { family ethernet-switching; } } ge-2/0/6 { # Define the traffic input port flexible-vlan-tagging; encapsulation extended-vlan-bridge; unit 0 { vlan-id 100; family ethernet-switching { filter { input example-bridge-pm-filter; # Apply the port-mirroring firewall filter } } } } ge-3/0/1 { # Define the traffic output port flexible-vlan-tagging; encapsulation extended-vlan-bridge; unit 2 { vlan-tags outer 10 inner 20; family ethernet-switching; } } }Packets received at logical interface ge-2/0/6.0 on VLAN example-bd-with-traffic are evaluated by the port-mirroring firewall filter example-bridge-pm-filter. The firewall filter acts on the input traffic according to the filter actions configured in the firewall filter itself plus the input packet-sampling properties and mirror destination properties configured in the global port-mirroring instance:
All packets received at ge-2/0/6.0 are forwarded to their (assumed) normal destination at logical interface ge-3/0/1.2.
For every ten input packets, copies of the first five packets in that selection are forwarded to the external analyzer at logical interface ge-0/0/0.0 in the other VLAN, example-bd-with-analyzer.
If you configure the port-mirroring firewall filter example-bridge-pm-filter to take the discard action instead of the accept action, all original packets are discarded while copies of the packets selected using the global port-mirroring input properties are sent to the external analyzer.
Example: Layer 2 Port Mirroring for a Layer 2 VPN
The following example is not a complete configuration, but shows all the steps needed to configure port mirroring on an L2VPN using family ccc.
Configure the VLAN port-mirror-bd, which contains the external packet analyzer:
[edit] vlans { port-mirror-vlan { # Contains an external traffic analyzer interface ge-2/2/9.0; # External analyzer } }Configure the Layer 2 VPN CCC to connect logical interface ge-2/0/1.0 and logical interface ge-2/0/1.1:
[edit] protocols { mpls { interface all; } connections { interface-switch if_switch { interface ge-2/0/1.0; interface ge-2/0/1.1; } } }Configure Layer 2 port mirroring for the global instance, with the port-mirroring destination being the VLAN interface associated with the external analyzer (logical interface ge-2/2/9.0 on VLAN example-bd-with-analyzer):
[edit] forwarding-options { port-mirroring { input { rate 1; maximum-packet-length 200; } family ccc { output { interface ge-2/2/9.0; # Mirror packets to the external analyzer } } instance { inst1 { input { rate 1; maximum-packet-length 300; } family ccc { output { interface ge-2/2/9.0; } { } } } }Define the Layer 2 port-mirroring firewall filter pm_filter_ccc for family ccc:
[edit] firewall { family ccc { filter pm_filter_ccc { term pm { then port-mirror; } } } }Apply the port mirror instance to the chassis:
[edit] chassis { fpc 2 { port-mirror-instance inst1; } }Configure interface ge-2/2/9 for the VLANs, and configure interface ge-2/0/1 for port mirroring with the pm_filter_ccc firewall filter:
[edit] interfaces { ge-2/2/9 { encapsulation ethernet-bridge; unit 0 { family ethernet-switching; } } ge-2/0/1 { vlan-tagging; encapsulation extended-vlan-ccc; unit 0 { vlan-id 10; family ccc { filter { input pm_filter_ccc; } } } unit 1 { vlan-id 20; family ccc { filter { output pm_filter_ccc; } } } } }
Example: Layer 2 Port Mirroring for a Layer 2 VPN with LAG Links
The following example is not a complete configuration, but shows all the steps needed to configure port mirroring on an L2VPN using family ccc and aggregated Ethernet links.
Configure the VLAN port_mirror_bd, which contains the external packet analyzer:
[edit] vlans { port_mirror_vlan { # Contains an external traffic analyzer interface ge-2/2/8.0; # External analyzer } }Configure the Layer 2 VPN CCC to connect interface ae0.0 and interface ae0.1:
[edit] protocols { mpls { interface all; } connections { interface-switch if_switch { interface ae0.0; interface ae0.1; } } }Configure Layer 2 port mirroring for the global instance, with the port-mirroring destination being the VLAN interface associated with the external analyzer (logical interface ge-2/2/9.0 on VLAN example_bd_with_analyzer):
[edit] forwarding-options { port-mirroring { input { rate 1; maximum-packet-length 200; } family ccc { output { interface ge-2/2/8.0; # Mirror packets to the external analyzer } } instance { pm_instance_1 { input { rate 1; maximum-packet-length 300; } family ccc { output { interface ge-2/2/8.0; } { } } } }Configure the firewall filter pm_ccc for family ccc:
[edit] firewall { family ccc { filter pm_ccc { term pm { then port-mirror; } } } }Apply the aggregated Ethernet interfaces and port mirror instance to the chassis:
[edit] chassis { aggregated-devices { ethernet { device-count 10; } } fpc 2 { port-mirror-instance pm_instance_1; } }Configure interfaces ae0 and ge-2/0/2 (for aggregated Ethernet) and ge-2/2/8 (for port mirroring) with the pm_ccc filter:
[edit] interfaces { ae0 { vlan-tagging; encapsulation extended-vlan-ccc; unit 0 { vlan-id 10; family ccc { filter { input pm_ccc; } } } unit 1 { vlan-id 20; family ccc { filter { output pm_ccc; } } } } ge-2/0/2 { gigether-options { 802.3ad ae0; } } ge-2/2/8 { encapsulation ethernet-bridge; unit 0 { family ethernet-switching; } } }
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
family any to do port mirroring.