Lawful Intercept on Junos Multi-Access User Plane
Lawful intercept is a process for obtaining communications network data related to a target individual or organization, as authorized by a judicial or administrative order.
Junos Multi-Access User Plane supports 4G and 5G compliance for lawful interception. You can lawfully intercept up to two percent of the maximum subscribers that the platform supports.
Lawful intercept on the Junos Multi-Access User Plane supports graceful Routing Engine switchover (GRES). It does not currently support unified ISSU.
Lawful Intercept on 4G Networks
The Junos Multi-Access User Plane supports 4G-compliant lawful intercept only over the System Architecture Evolution Gateway-User Plane (SAEGW-U).
Figure 1 shows the entities involved in lawful interception on 4G networks and the interfaces between them.
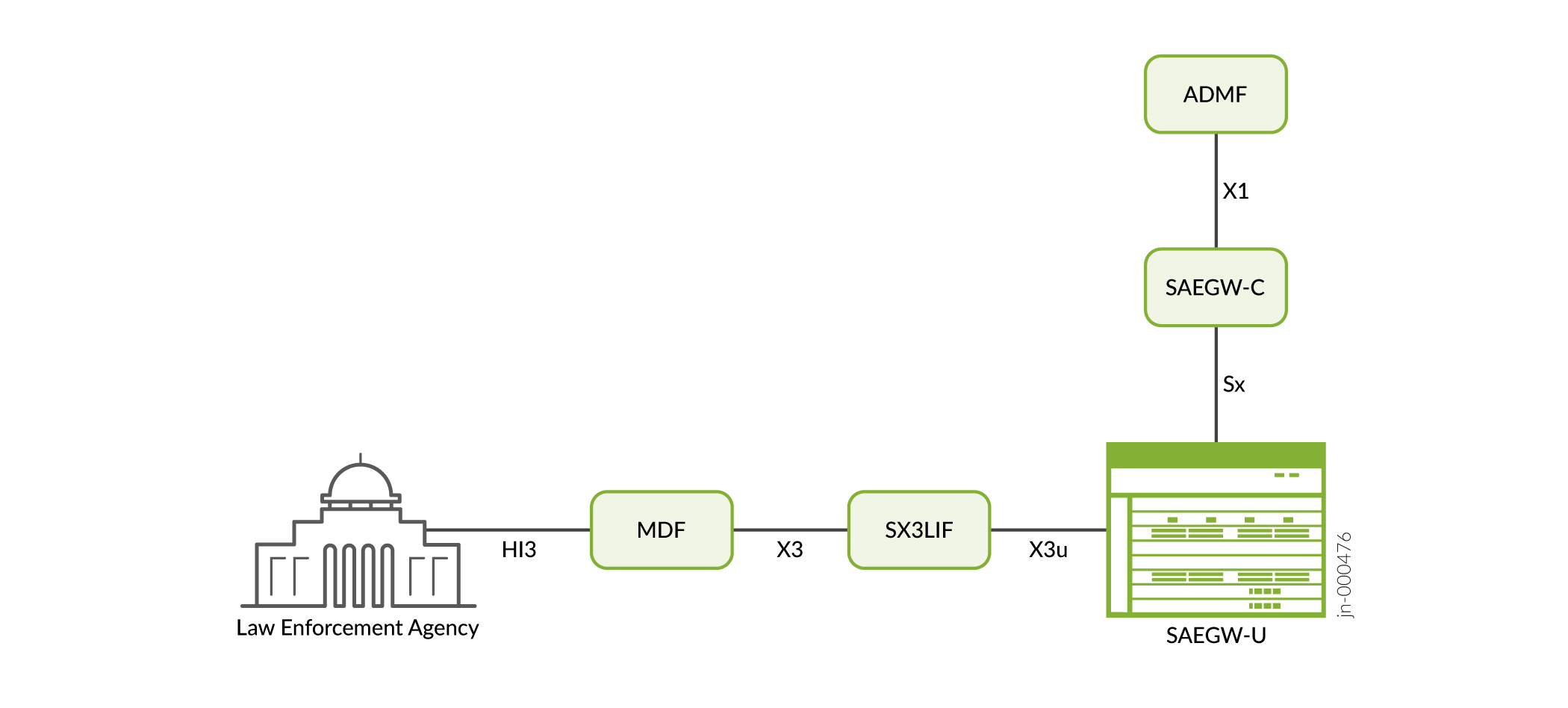
The process for lawful interception on 4G networks is as follows:
-
The Administrative Function (ADMF) performs the overall management of the lawful intercept system. It sends signals containing targeting information to the control plane over the X1 interface. The ADMF also informs the control plane which subscribers’ traffic to duplicate and to send to the law enforcement agency.
-
The control plane (SAEGW-C) triggers the user plane over the Sx interface to start duplicating the subscriber traffic. It also sends the address of the Mediation and Delivery Function (MDF) to which the data is to be forwarded.
-
The Junos Multi-Access User Plane (SAEGW-U) sends the duplicated traffic to the split X3 lawful intercept internetworking function (SX3LIF) over the X3u interface. The SX3LIF then forwards it to the MDF over the X3 interface.
-
The MDF derives the intercept-related information from the LI_X3 headers sent along with the duplicated traffic. It then forwards the intercepted traffic to the law enforcement agency over the HI3 interface.
Lawful Intercept on 5G Networks
The Junos Multi-Access User Plane supports 5G-compliant lawful intercept only over the user plane function (UPF) or content of communication point of interception (CC-POI).
Figure 2 shows the entities involved in lawful interception on 5G networks and the interfaces between them.
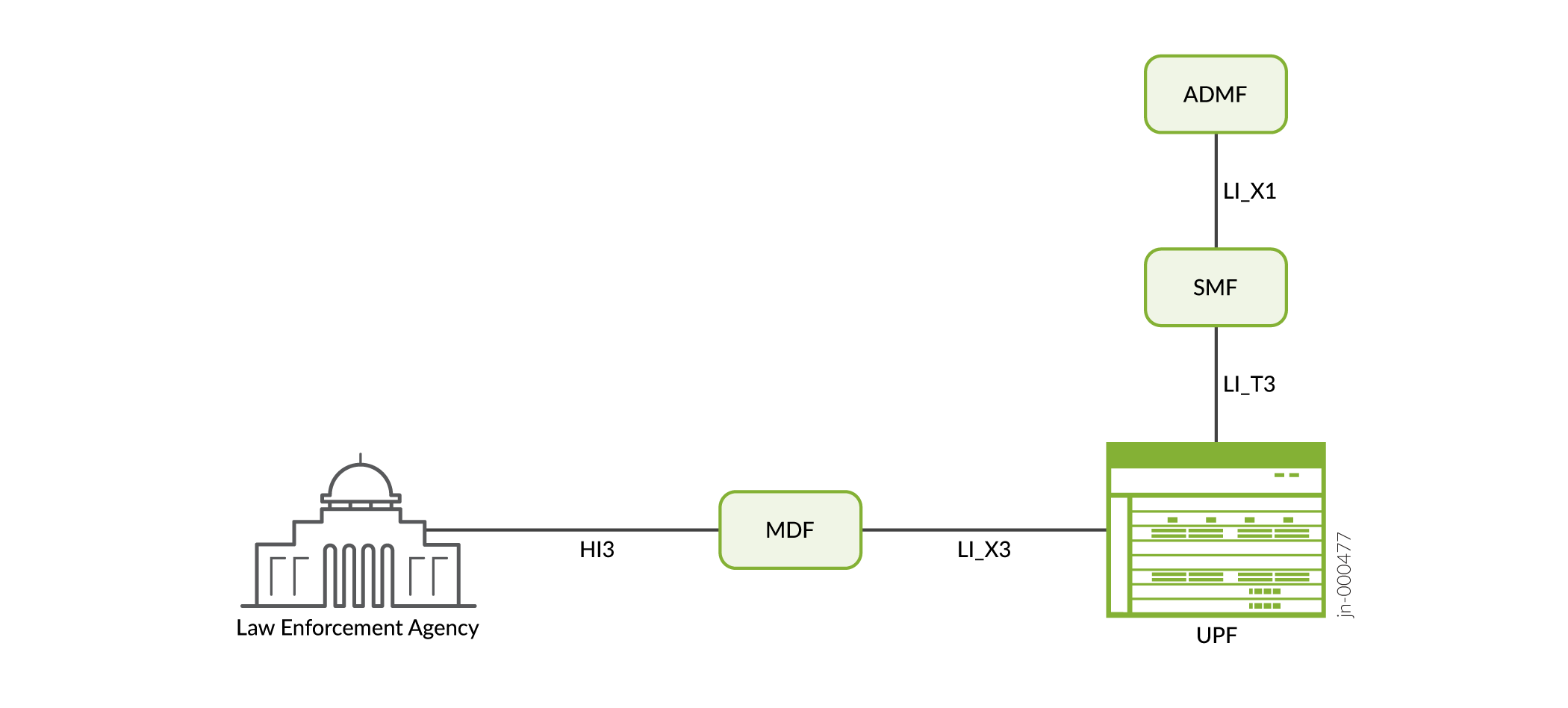
The process for lawful interception is as follows:
-
The Administrative Function (ADMF) performs the overall management of the lawful intercept system. It sends signals containing targeting information to the control plane over the LI_X1 interface. It also informs the control plane which subscribers’ traffic to duplicate and to send to the law enforcement agency.
-
The control plane (SMF) triggers the user plane over the LI_T3 interface to start duplicating the subscriber traffic. It also sends the address of the Mediation and Delivery Function (MDF) to which the data is to be forwarded.
-
The Junos Multi-Access User Plane (UPF) sends the duplicated traffic to the MDF over the LI_X3 interface.
-
The MDF derives the intercept-related information from the LI_X3 headers sent along with the duplicated traffic. It then forwards the intercepted traffic to the law enforcement agency over the HI3 interface.
Requirements for Lawful Intercept
To configure lawful intercept for 4G networks, you must:
-
Configure a loopback address on the Junos Multi-Access User Plane. This address is used as the source address for the lawfully intercepted traffic.
[edit interfaces lo0 unit 0 family inet] user@host# set address loopback-address
To configure lawful intercept for 5G networks, you must:
-
Set the loopback address to 127.0.0.1/32 on the Junos Multi-Access User Plane. This address is used as the source address for the lawfully intercepted traffic.
[edit interfaces lo0 unit 0 family inet] user@host# set address 127.0.0.1/32
-
Configure the HTTPS server on the Junos Multi-Access User Plane using the REST-API under the
[edit system services rest https-5g]hierarchy.[edit system services rest https-5g] user@host# set port port-number user@host# set addresses ip-address user@host# set server-certificate local-certificate-identifier user@host# set mutual-authentication certificate-authority certificate-authority-profile-name
For more information on the REST API, see Configuring the REST API.
For information on certificate authority and public key infrastructure, see PKI in Junos OS.
-
(Optional) Configure the connection limit for the REST-API. We recommend this configuration to enhance the performance of lawful intercept.
[edit system services rest control] user@host# set connection-limit limit
Security Considerations for Lawful Intercept
Due to its nature, lawfully intercepted data must be transmitted in a secure manner. The 3GPP standards require that lawful intercept traffic on 5G networks must be sent to the Mediation and Delivery Function (MDF) using Transport Layer Security (TLS).
The Junos Multi-Access User Plane does not support TLS, but can send lawful intercept traffic to the MDF over IPsec tunnels. When using IPsec on the Junos Multi-Access User Plane, make sure that you:
-
Configure the virtual multiservices interfaces and the next-hop-style service set.
Use the following commands to configure the virtual multiservices interfaces:
[edit interfaces] user@host# set interface-name unit logical-unit-number family inet user@host# set interface-name unit logical-unit-number service-domain inside user@host# set interface-name unit logical-unit-number family inet user@host# set interface-name unit logical-unit-number service-domain outside
Use the following commands to configure a next-hop-style service set:
[edit services] user@host# set service-set service-set-name [edit services service-set service-set-name] user@host# set next-hop-service inside-service-interface interface-name.unit-number outside-service-interface interface-name.unit-number
The inside-service-interface must be a service interface logical unit that is configured with
service-domain insideThe outside-service-interface must be a service interface logical unit that is configured withservice-domain outside. -
Configure the Internet Key Exchange (IKE).
[edit security ike] user@host# set proposal proposal-name [edit security ike proposal proposal-name] user@host# set authentication-method pre-shared-keys user@host# set dh-group dh-group-number user@host# set authentication-algorithm algorithm user@host# set encryption-algorithm algorithm [edit security ike] user@host# set policy policy-name [edit security ike policy policy-name] user@host# set proposals proposal-name user@host# set pre-shared-key ascii-text key [edit security ike] user@host# set gateway gateway-name [edit security ike gateway gateway-name] user@host# set ike-policy policy-name user@host# set address ip-address user@host# set external-interface interface-name user@host# set local-address address
For more information on IKE, see Internet Key Exchange (IKE) for IPsec VPN.
-
Use the IPsec tunnel mode.
Note:To use IPsec, you must have an MX-SPC3 services card installed on your device.
[edit security ipsec] user@host# set proposal proposal-name [edit security ipsec proposal proposal-name] user@host# set protocol (ah | esp) user@host# set authentication-algorithm algorithm user@host# set encryption-algorithm algorithm [edit security ipsec] user@host# set policy policy-name [edit security ipsec policy policy-name] user@host# set proposals proposal-name [edit security ipsec] user@host# set vpn vpn-name [edit security ipsec vpn vpn-name] user@host# set bind-interface interface-name user@host# set ike gateway gateway-name user@host# set ike ipsec-policy policy-name user@host# set establish-tunnels immediately
For more information on configuring IPsec tunnels, see IPsec VPN Configuration Overview.
If IPsec cannot be used, we recommend using a content of communication point of aggregation (CC-PAG) device, which encrypts the data using TLS before sending it to the MDF.
You can still lawfully intercept traffic on 5G networks without configuring IPsec. However, we recommend that you use IPsec to comply with 3GPP standards.
The LI_T3 interface between the SMF and UPF supports TLS encryption. You can enable this by
configuring a server certificate and mutual authentication on the local HTTPS server under
the [edit system services rest https-5g] hierarchy.
