Configuring BFD
Use the following examples to configure Bidirectional Forwarding Detection (BFD) on your device.
Example: Configuring BFD for Static Routes for Faster Network Failure Detection
This example shows how to configure Bidirectional Forwarding Detection (BFD) for static routes.
Requirements
In this example, no special configuration beyond device initialization is required.
Overview
There are many practical applications for static routes. Static routing is often used at the network edge to support attachment to stub networks, which, given their single point of entry and egress, are well suited to the simplicity of a static route. In Junos OS, static routes have a global preference of 5. Static routes are activated if the specified next hop is reachable.
In this example, you configure the static route 192.168.47.0/24 from the provider network to the customer network, using the next-hop address of 172.16.1.2. You also configure a static default route of 0.0.0.0/0 from the customer network to the provider network, using a next-hop address of 172.16.1.1.
For demonstration purposes, some loopback interfaces are configured on Device B and Device D. These loopback interfaces provide addresses to ping and thus verify that the static routes are working.
Figure 1 shows the sample network.
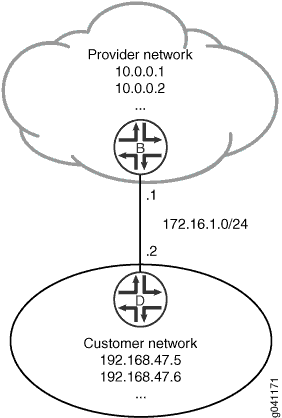
Topology
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a
text file, remove any line breaks, change any details necessary to match your
network configuration, and then copy and paste the commands into the CLI at the
[edit] hierarchy level.
Device B
set interfaces ge-1/2/0 unit 0 description B->D set interfaces ge-1/2/0 unit 0 family inet address 172.16.1.1/24 set interfaces lo0 unit 57 family inet address 10.0.0.1/32 set interfaces lo0 unit 57 family inet address 10.0.0.2/32 set routing-options static route 192.168.47.0/24 next-hop 172.16.1.2 set routing-options static route 192.168.47.0/24 bfd-liveness-detection minimum-interval 1000 set routing-options static route 192.168.47.0/24 bfd-liveness-detection description Site-xxx set protocols bfd traceoptions file bfd-trace set protocols bfd traceoptions flag all
Device D
set interfaces ge-1/2/0 unit 1 description D->B set interfaces ge-1/2/0 unit 1 family inet address 172.16.1.2/24 set interfaces lo0 unit 2 family inet address 192.168.47.5/32 set interfaces lo0 unit 2 family inet address 192.168.47.6/32 set routing-options static route 0.0.0.0/0 next-hop 172.16.1.1 set routing-options static route 0.0.0.0/0 bfd-liveness-detection minimum-interval 1000 set protocols bfd traceoptions file bfd-trace set protocols bfd traceoptions flag all
Procedure
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure BFD for static routes:
On Device B, configure the interfaces.
[edit interfaces] user@B# set ge-1/2/0 unit 0 description B->D user@B# set ge-1/2/0 unit 0 family inet address 172.16.1.1/24 user@B# set lo0 unit 57 family inet address 10.0.0.1/32 user@B# set lo0 unit 57 family inet address 10.0.0.2/32
On Device B, create a static route and set the next-hop address.
[edit routing-options] user@B# set static route 192.168.47.0/24 next-hop 172.16.1.2
On Device B, configure BFD for the static route.
[edit routing-options] user@B# set static route 192.168.47.0/24 bfd-liveness-detection minimum-interval 1000 set routing-options static route 192.168.47.0/24 bfd-liveness-detection description Site-xxx
On Device B, configure tracing operations for BFD.
[edit protocols] user@B# set bfd traceoptions file bfd-trace user@B# set bfd traceoptions flag all
If you are done configuring Device B, commit the configuration.
[edit] user@B# commit
On Device D, configure the interfaces.
[edit interfaces] user@D# set ge-1/2/0 unit 1 description D->B user@D# set ge-1/2/0 unit 1 family inet address 172.16.1.2/24 user@D# set lo0 unit 2 family inet address 192.168.47.5/32 user@D# set lo0 unit 2 family inet address 192.168.47.6/32
On Device D, create a static route and set the next-hop address.
[edit routing-options] user@D# set static route 0.0.0.0/0 next-hop 172.16.1.1
On Device D, configure BFD for the static route.
[edit routing-options] user@D# set static route 0.0.0.0/0 bfd-liveness-detection minimum-interval 1000
On Device D, configure tracing operations for BFD.
[edit protocols] user@D# set bfd traceoptions file bfd-trace user@D# set bfd traceoptions flag all
If you are done configuring Device D, commit the configuration.
[edit] user@D# commit
Results
Confirm your configuration by issuing the show interfaces,
show protocols, and show routing-options
commands. If the output does not display the intended configuration, repeat the
instructions in this example to correct the configuration.
Device B
user@B# show interfaces
ge-1/2/0 {
unit 0 {
description B->D;
family inet {
address 172.16.1.1/24;
}
}
}
lo0 {
unit 57 {
family inet {
address 10.0.0.1/32;
address 10.0.0.2/32;
}
}
}
user@D# show protocols
bfd {
traceoptions {
file bfd-trace;
flag all;
}
}
user@B# show routing-options
static {
route 192.168.47.0/24 {
next-hop 172.16.1.2;
bfd-liveness-detection {
description Site- xxx;
minimum-interval 1000;
}
}
}
Device D
user@D# show interfaces
ge-1/2/0 {
unit 1 {
description D->B;
family inet {
address 172.16.1.2/24;
}
}
}
lo0 {
unit 2 {
family inet {
address 192.168.47.5/32;
address 192.168.47.6/32;
}
}
}
user@D# show routing-options
static {
route 0.0.0.0/0 {
next-hop 172.16.1.1;
bfd-liveness-detection {
description Site - xxx;
minimum-interval 1000;
}
}
}
Verification
Confirm that the configuration is working properly.
Verifying That BFD Sessions Are Up
Purpose
Verify that the BFD sessions are up, and view details about the BFD sessions.
Action
From operational mode, enter the show bfd session
extensive command.
user@B> show bfd session extensive
Detect Transmit
Address State Interface Time Interval Multiplier
172.16.1.2 Up lt-1/2/0.0 3.000 1.000 3
Client Static, description Site-xxx, TX interval 1.000, RX interval 1.000
Session up time 00:14:30
Local diagnostic None, remote diagnostic None
Remote state Up, version 1
Replicated, routing table index 172
Min async interval 1.000, min slow interval 1.000
Adaptive async TX interval 1.000, RX interval 1.000
Local min TX interval 1.000, minimum RX interval 1.000, multiplier 3
Remote min TX interval 1.000, min RX interval 1.000, multiplier 3
Local discriminator 2, remote discriminator 1
Echo mode disabled/inactive
1 sessions, 1 clients
Cumulative transmit rate 1.0 pps, cumulative receive rate 1.0 ppsThe description Site- <xxx> is supported only on the SRX Series Firewalls.
If each client has more than one description field, then it displays "and more" along with the first description field.
user@D> show bfd session extensive
Detect Transmit
Address State Interface Time Interval Multiplier
172.16.1.1 Up lt-1/2/0.1 3.000 1.000 3
Client Static, TX interval 1.000, RX interval 1.000
Session up time 00:14:35
Local diagnostic None, remote diagnostic None
Remote state Up, version 1
Replicated, routing table index 170
Min async interval 1.000, min slow interval 1.000
Adaptive async TX interval 1.000, RX interval 1.000
Local min TX interval 1.000, minimum RX interval 1.000, multiplier 3
Remote min TX interval 1.000, min RX interval 1.000, multiplier 3
Local discriminator 1, remote discriminator 2
Echo mode disabled/inactive
1 sessions, 1 clients
Cumulative transmit rate 1.0 pps, cumulative receive rate 1.0 ppsMeaning
The TX interval 1.000, RX interval 1.000 output represents
the setting configured with the minimum-interval statement.
All of the other output represents the default settings for BFD. To modify
the default settings, include the optional statements under the
bfd-liveness-detection statement.
Viewing Detailed BFD Events
Purpose
View the contents of the BFD trace file to assist in troubleshooting, if needed.
Action
From operational mode, enter the file show
/var/log/bfd-trace command.
user@B> file show /var/log/bfd-trace Nov 23 14:26:55 Data (9) len 35: (hex) 42 46 44 20 70 65 72 69 6f 64 69 63 20 78 6d 69 74 20 72 Nov 23 14:26:55 PPM Trace: BFD periodic xmit rt tbl index 172 Nov 23 14:26:55 Received Downstream TraceMsg (22) len 108: Nov 23 14:26:55 IfIndex (3) len 4: 0 Nov 23 14:26:55 Protocol (1) len 1: BFD Nov 23 14:26:55 Data (9) len 83: (hex) 70 70 6d 64 5f 62 66 64 5f 73 65 6e 64 6d 73 67 20 3a 20 Nov 23 14:26:55 PPM Trace: ppmd_bfd_sendmsg : socket 12 len 24, ifl 78 src 172.16.1.1 dst 172.16.1.2 errno 65 Nov 23 14:26:55 Received Downstream TraceMsg (22) len 93: Nov 23 14:26:55 IfIndex (3) len 4: 0 Nov 23 14:26:55 Protocol (1) len 1: BFD Nov 23 14:26:55 Data (9) len 68: (hex) 42 46 44 20 70 65 72 69 6f 64 69 63 20 78 6d 69 74 20 74
Meaning
BFD messages are being written to the trace file.
Example: Configuring BFD on Internal BGP Peer Sessions
This example shows how to configure internal BGP (IBGP) peer sessions with the Bidirectional Forwarding Detection (BFD) protocol to detect failures in a network.
Requirements
No special configuration beyond device initialization is required before you configure this example.
Overview
The minimum configuration to enable BFD on IBGP sessions is
to include the bfd-liveness-detection minimum-interval statement
in the BGP configuration of all neighbors participating in the BFD
session. The minimum-interval statement specifies the minimum
transmit and receive intervals for failure detection. Specifically,
this value represents the minimum interval after which the local routing
device transmits hello packets as well as the minimum interval that
the routing device expects to receive a reply from a neighbor with
which it has established a BFD session. You can configure a value
from 1 through 255,000 milliseconds.
Optionally, you can specify the minimum transmit and receive
intervals separately using the transmit-interval minimum-interval and minimum-receive-interval statements. For information
about these and other optional BFD configuration statements, see bfd-liveness-detection.
Depending on your network environment, these additional recommendations might apply:
To prevent BFD flapping during the general Routing Engine switchover event, specify a minimum interval of 5000 milliseconds for Routing Engine-based sessions. This minimum value is required because, during the general Routing Engine switchover event, processes such as RPD, MIBD, and SNMPD utilize CPU resources for more than the specified threshold value. Hence, BFD processing and scheduling is affected because of this lack of CPU resources.
For BFD sessions to remain up during the dual chassis cluster control link scenario, when the first control link fails, specify the minimum interval of 6000 milliseconds to prevent the LACP from flapping on the secondary node for Routing Engine-based sessions.
For large-scale network deployments with a large number of BFD sessions, specify a minimum interval of 300 milliseconds for Routing Engine-based sessions and 100 milliseconds for distributed BFD sessions.
For very large-scale network deployments with a large number of BFD sessions, contact Juniper Networks customer support for more information.
For BFD sessions to remain up during a Routing Engine switchover event when nonstop active routing (NSR) is configured, specify a minimum interval of 2500 milliseconds for Routing Engine-based sessions. For distributed BFD sessions with NSR configured, the minimum interval recommendations are unchanged and depend only on your network deployment.
BFD is supported on the default routing instance (the main router), routing instances, and logical systems. This example shows BFD on logical systems.
Figure 2 shows a typical network with internal peer sessions.
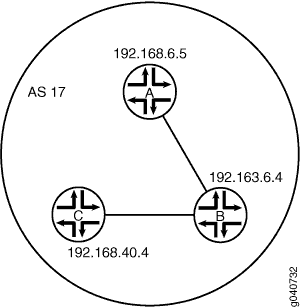
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
and then copy and paste the commands into the CLI at the [edit] hierarchy level.
Device A
set logical-systems A interfaces lt-1/2/0 unit 1 description to-B set logical-systems A interfaces lt-1/2/0 unit 1 encapsulation ethernet set logical-systems A interfaces lt-1/2/0 unit 1 peer-unit 2 set logical-systems A interfaces lt-1/2/0 unit 1 family inet address 10.10.10.1/30 set logical-systems A interfaces lo0 unit 1 family inet address 192.168.6.5/32 set logical-systems A protocols bgp group internal-peers type internal set logical-systems A protocols bgp group internal-peers traceoptions file bgp-bfd set logical-systems A protocols bgp group internal-peers traceoptions flag bfd detail set logical-systems A protocols bgp group internal-peers local-address 192.168.6.5 set logical-systems A protocols bgp group internal-peers export send-direct set logical-systems A protocols bgp group internal-peers bfd-liveness-detection minimum-interval 1000 set logical-systems A protocols bgp group internal-peers neighbor 192.163.6.4 set logical-systems A protocols bgp group internal-peers neighbor 192.168.40.4 set logical-systems A protocols ospf area 0.0.0.0 interface lo0.1 passive set logical-systems A protocols ospf area 0.0.0.0 interface lt-1/2/0.1 set logical-systems A policy-options policy-statement send-direct term 2 from protocol direct set logical-systems A policy-options policy-statement send-direct term 2 then accept set logical-systems A routing-options router-id 192.168.6.5 set logical-systems A routing-options autonomous-system 17
Device B
set logical-systems B interfaces lt-1/2/0 unit 2 description to-A set logical-systems B interfaces lt-1/2/0 unit 2 encapsulation ethernet set logical-systems B interfaces lt-1/2/0 unit 2 peer-unit 1 set logical-systems B interfaces lt-1/2/0 unit 2 family inet address 10.10.10.2/30 set logical-systems B interfaces lt-1/2/0 unit 5 description to-C set logical-systems B interfaces lt-1/2/0 unit 5 encapsulation ethernet set logical-systems B interfaces lt-1/2/0 unit 5 peer-unit 6 set logical-systems B interfaces lt-1/2/0 unit 5 family inet address 10.10.10.5/30 set logical-systems B interfaces lo0 unit 2 family inet address 192.163.6.4/32 set logical-systems B protocols bgp group internal-peers type internal set logical-systems B protocols bgp group internal-peers local-address 192.163.6.4 set logical-systems B protocols bgp group internal-peers export send-direct set logical-systems B protocols bgp group internal-peers bfd-liveness-detection minimum-interval 1000 set logical-systems B protocols bgp group internal-peers neighbor 192.168.40.4 set logical-systems B protocols bgp group internal-peers neighbor 192.168.6.5 set logical-systems B protocols ospf area 0.0.0.0 interface lo0.2 passive set logical-systems B protocols ospf area 0.0.0.0 interface lt-1/2/0.2 set logical-systems B protocols ospf area 0.0.0.0 interface lt-1/2/0.5 set logical-systems B policy-options policy-statement send-direct term 2 from protocol direct set logical-systems B policy-options policy-statement send-direct term 2 then accept set logical-systems B routing-options router-id 192.163.6.4 set logical-systems B routing-options autonomous-system 17
Device C
set logical-systems C interfaces lt-1/2/0 unit 6 description to-B set logical-systems C interfaces lt-1/2/0 unit 6 encapsulation ethernet set logical-systems C interfaces lt-1/2/0 unit 6 peer-unit 5 set logical-systems C interfaces lt-1/2/0 unit 6 family inet address 10.10.10.6/30 set logical-systems C interfaces lo0 unit 3 family inet address 192.168.40.4/32 set logical-systems C protocols bgp group internal-peers type internal set logical-systems C protocols bgp group internal-peers local-address 192.168.40.4 set logical-systems C protocols bgp group internal-peers export send-direct set logical-systems C protocols bgp group internal-peers bfd-liveness-detection minimum-interval 1000 set logical-systems C protocols bgp group internal-peers neighbor 192.163.6.4 set logical-systems C protocols bgp group internal-peers neighbor 192.168.6.5 set logical-systems C protocols ospf area 0.0.0.0 interface lo0.3 passive set logical-systems C protocols ospf area 0.0.0.0 interface lt-1/2/0.6 set logical-systems C policy-options policy-statement send-direct term 2 from protocol direct set logical-systems C policy-options policy-statement send-direct term 2 then accept set logical-systems C routing-options router-id 192.168.40.4 set logical-systems C routing-options autonomous-system 17
Configuring Device A
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure Device A:
Set the CLI to Logical System A.
user@host> set cli logical-system A
Configure the interfaces.
[edit interfaces lt-1/2/0 unit 1] user@host:A# set description to-B user@host:A# set encapsulation ethernet user@host:A# set peer-unit 2 user@host:A# set family inet address 10.10.10.1/30 [edit interfaces lo0 unit 1] user@host:A# set family inet address 192.168.6.5/32
Configure BGP.
The
neighborstatements are included for both Device B and Device C, even though Device A is not directly connected to Device C.[edit protocols bgp group internal-peers] user@host:A# set type internal user@host:A# set local-address 192.168.6.5 user@host:A# set export send-direct user@host:A# set neighbor 192.163.6.4 user@host:A# set neighbor 192.168.40.4
Configure BFD.
[edit protocols bgp group internal-peers] user@host:A# set bfd-liveness-detection minimum-interval 1000
You must configure the same minimum interval on the connecting peer.
(Optional) Configure BFD tracing.
[edit protocols bgp group internal-peers] user@host:A# set traceoptions file bgp-bfd user@host:A# set traceoptions flag bfd detail
Configure OSPF.
[edit protocols ospf area 0.0.0.0] user@host:A# set interface lo0.1 passive user@host:A# set interface lt-1/2/0.1
Configure a policy that accepts direct routes.
Other useful options for this scenario might be to accept routes learned through OSPF or local routes.
[edit policy-options policy-statement send-direct term 2] user@host:A# set from protocol direct user@host:A# set then accept
Configure the router ID and the autonomous system (AS) number.
[edit routing-options] user@host:A# set router-id 192.168.6.5 user@host:A# set autonomous-system 17
If you are done configuring the device, enter
commitfrom configuration mode. Repeat these steps to configure Device B and Device C.
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show policy-options, show protocols, and show routing-options commands.
If the output does not display the intended configuration, repeat
the instructions in this example to correct the configuration.
user@host:A# show interfaces
lt-1/2/0 {
unit 1 {
description to-B;
encapsulation ethernet;
peer-unit 2;
family inet {
address 10.10.10.1/30;
}
}
}
lo0 {
unit 1 {
family inet {
address 192.168.6.5/32;
}
}
}
user@host:A# show policy-options
policy-statement send-direct {
term 2 {
from protocol direct;
then accept;
}
}
user@host:A# show protocols
bgp {
group internal-peers {
type internal;
traceoptions {
file bgp-bfd;
flag bfd detail;
}
local-address 192.168.6.5;
export send-direct;
bfd-liveness-detection {
minimum-interval 1000;
}
neighbor 192.163.6.4;
neighbor 192.168.40.4;
}
}
ospf {
area 0.0.0.0 {
interface lo0.1 {
passive;
}
interface lt-1/2/0.1;
}
}
user@host:A# show routing-options router-id 192.168.6.5; autonomous-system 17;
Verification
Confirm that the configuration is working properly.
- Verifying That BFD Is Enabled
- Verifying That BFD Sessions Are Up
- Viewing Detailed BFD Events
- Viewing Detailed BFD Events After Deactivating and Reactivating a Loopback Interface
Verifying That BFD Is Enabled
Purpose
Verify that BFD is enabled between the IBGP peers.
Action
From operational mode, enter the show bgp neighbor command. You can use the | match bfd filter to narrow
the output.
user@host:A> show bgp neighbor | match bfd Options: <BfdEnabled> BFD: enabled, up Trace file: /var/log/A/bgp-bfd size 131072 files 10 Options: <BfdEnabled> BFD: enabled, up Trace file: /var/log/A/bgp-bfd size 131072 files 10
Meaning
The output shows that Logical System A has two neighbors
with BFD enabled. When BFD is not enabled, the output displays BFD: disabled, down, and the <BfdEnabled> option
is absent. If BFD is enabled and the session is down, the output displays BFD: enabled, down. The output also shows that BFD-related
events are being written to a log file because trace operations are
configured.
Verifying That BFD Sessions Are Up
Purpose
Verify that the BFD sessions are up, and view details about the BFD sessions.
Action
From operational mode, enter the show bfd session extensive command.
user@host:A> show bfd session extensive
Detect Transmit
Address State Interface Time Interval Multiplier
192.163.6.4 Up 3.000 1.000 3
Client BGP, TX interval 1.000, RX interval 1.000
Session up time 00:54:40
Local diagnostic None, remote diagnostic None
Remote state Up, version 1
Logical system 12, routing table index 25
Min async interval 1.000, min slow interval 1.000
Adaptive async TX interval 1.000, RX interval 1.000
Local min TX interval 1.000, minimum RX interval 1.000, multiplier 3
Remote min TX interval 1.000, min RX interval 1.000, multiplier 3
Local discriminator 10, remote discriminator 9
Echo mode disabled/inactive
Multi-hop route table 25, local-address 192.168.6.5
Detect Transmit
Address State Interface Time Interval Multiplier
192.168.40.4 Up 3.000 1.000 3
Client BGP, TX interval 1.000, RX interval 1.000
Session up time 00:48:03
Local diagnostic None, remote diagnostic None
Remote state Up, version 1
Logical system 12, routing table index 25
Min async interval 1.000, min slow interval 1.000
Adaptive async TX interval 1.000, RX interval 1.000
Local min TX interval 1.000, minimum RX interval 1.000, multiplier 3
Remote min TX interval 1.000, min RX interval 1.000, multiplier 3
Local discriminator 14, remote discriminator 13
Echo mode disabled/inactive
Multi-hop route table 25, local-address 192.168.6.5
2 sessions, 2 clients
Cumulative transmit rate 2.0 pps, cumulative receive rate 2.0 ppsMeaning
The TX interval 1.000, RX interval 1.000 output represents the setting configured with the minimum-interval statement. All of the other output represents the default settings
for BFD. To modify the default settings, include the optional statements
under the bfd-liveness-detection statement.
Viewing Detailed BFD Events
Purpose
View the contents of the BFD trace file to assist in troubleshooting, if needed.
Action
From operational mode, enter the file show /var/log/A/bgp-bfd command.
user@host:A> file show /var/log/A/bgp-bfd Aug 15 17:07:25 trace_on: Tracing to "/var/log/A/bgp-bfd" started Aug 15 17:07:26.492190 bgp_peer_init: BGP peer 192.163.6.4 (Internal AS 17) local address 192.168.6.5 not found. Leaving peer idled Aug 15 17:07:26.493176 bgp_peer_init: BGP peer 192.168.40.4 (Internal AS 17) local address 192.168.6.5 not found. Leaving peer idled Aug 15 17:07:32.597979 task_connect: task BGP_17.192.163.6.4+179 addr 192.163.6.4+179: No route to host Aug 15 17:07:32.599623 bgp_connect_start: connect 192.163.6.4 (Internal AS 17): No route to host Aug 15 17:07:36.869394 task_connect: task BGP_17.192.168.40.4+179 addr 192.168.40.4+179: No route to host Aug 15 17:07:36.870624 bgp_connect_start: connect 192.168.40.4 (Internal AS 17): No route to host Aug 15 17:08:04.599220 task_connect: task BGP_17.192.163.6.4+179 addr 192.163.6.4+179: No route to host Aug 15 17:08:04.601135 bgp_connect_start: connect 192.163.6.4 (Internal AS 17): No route to host Aug 15 17:08:08.869717 task_connect: task BGP_17.192.168.40.4+179 addr 192.168.40.4+179: No route to host Aug 15 17:08:08.869934 bgp_connect_start: connect 192.168.40.4 (Internal AS 17): No route to host Aug 15 17:08:36.603544 advertising receiving-speaker only capabilty to neighbor 192.163.6.4 (Internal AS 17) Aug 15 17:08:36.606726 bgp_read_message: 192.163.6.4 (Internal AS 17): 0 bytes buffered Aug 15 17:08:36.609119 Initiated BFD session to peer 192.163.6.4 (Internal AS 17): address=192.163.6.4 ifindex=0 ifname=(none) txivl=1000 rxivl=1000 mult=3 ver=255 Aug 15 17:08:36.734033 advertising receiving-speaker only capabilty to neighbor 192.168.40.4 (Internal AS 17) Aug 15 17:08:36.738436 Initiated BFD session to peer 192.168.40.4 (Internal AS 17): address=192.168.40.4 ifindex=0 ifname=(none) txivl=1000 rxivl=1000 mult=3 ver=255 Aug 15 17:08:40.537552 BFD session to peer 192.163.6.4 (Internal AS 17) up Aug 15 17:08:40.694410 BFD session to peer 192.168.40.4 (Internal AS 17) up
Meaning
Before the routes are established, the No route
to host message appears in the output. After the routes are
established, the last two lines show that both BFD sessions come up.
Viewing Detailed BFD Events After Deactivating and Reactivating a Loopback Interface
Purpose
Check to see what happens after bringing down a router or switch and then bringing it back up. To simulate bringing down a router or switch, deactivate the loopback interface on Logical System B.
Action
From configuration mode, enter the
deactivate logical-systems B interfaces lo0 unit 2 family inetcommand.user@host:A# deactivate logical-systems B interfaces lo0 unit 2 family inet user@host:A# commit
From operational mode, enter the
file show /var/log/A/bgp-bfdcommand.user@host:A> file show /var/log/A/bgp-bfd ... Aug 15 17:20:55.995648 bgp_read_v4_message:9747: NOTIFICATION received from 192.163.6.4 (Internal AS 17): code 6 (Cease) subcode 6 (Other Configuration Change) Aug 15 17:20:56.004508 Terminated BFD session to peer 192.163.6.4 (Internal AS 17) Aug 15 17:21:28.007755 task_connect: task BGP_17.192.163.6.4+179 addr 192.163.6.4+179: No route to host Aug 15 17:21:28.008597 bgp_connect_start: connect 192.163.6.4 (Internal AS 17): No route to host
From configuration mode, enter the
activate logical-systems B interfaces lo0 unit 2 family inetcommand.user@host:A# activate logical-systems B interfaces lo0 unit 2 family inet user@host:A# commit
From operational mode, enter the
file show /var/log/A/bgp-bfdcommand.user@host:A> file show /var/log/A/bgp-bfd ... Aug 15 17:25:53.623743 advertising receiving-speaker only capabilty to neighbor 192.163.6.4 (Internal AS 17) Aug 15 17:25:53.631314 Initiated BFD session to peer 192.163.6.4 (Internal AS 17): address=192.163.6.4 ifindex=0 ifname=(none) txivl=1000 rxivl=1000 mult=3 ver=255 Aug 15 17:25:57.570932 BFD session to peer 192.163.6.4 (Internal AS 17) up
Example: Configuring BFD for OSPF
This example shows how to configure the Bidirectional Forwarding Detection (BFD) protocol for OSPF.
Requirements
Before you begin:
Configure the device interfaces. See the Junos OS Network Interfaces Library for Routing Devices.
Configure the router identifiers for the devices in your OSPF network. See Example: Configuring an OSPF Router Identifier.
Control OSPF designated router election. See Example: Controlling OSPF Designated Router Election.
Configure a single-area OSPF network. See Example: Configuring a Single-Area OSPF Network.
Configure a multiarea OSPF network. See Example: Configuring a Multiarea OSPF Network.
Configure a multiarea OSPF network. See Example: Configuring a Multiarea OSPF Network.
Overview
An alternative to adjusting the OSPF hello interval and dead interval settings to increase route convergence is to configure BFD. The BFD protocol is a simple hello mechanism that detects failures in a network. The BFD failure detection timers have shorter timer limits than the OSPF failure detection mechanisms, thereby providing faster detection.
BFD is useful on interfaces that are unable to detect failure quickly, such as Ethernet interfaces. Other interfaces, such as SONET interfaces, already have built-in failure detection. Configuring BFD on those interfaces is unnecessary.
You configure BFD on a pair of neighboring OSPF interfaces. Unlike the OSPF hello interval and dead interval settings, you do not have to enable BFD on all interfaces in an OSPF area.
In this example, you enable failure detection by including
the bfd-liveness-detection statement on the neighbor OSPF
interface fe-0/1/0 in area 0.0.0.0 and configure the BFD
packet exchange interval to 300 milliseconds, configure 4 as
the number of missed hello packets that causes the originating interface
to be declared down, and configure BFD sessions only for OSPF neighbors
with full neighbor adjacency by including the following settings:
full-neighbors-only—In Junos OS Release 9.5 and later, configures the BFD protocol to establish BFD sessions only for OSPF neighbors with full neighbor adjacency. The default behavior is to establish BFD sessions for all OSPF neighbors.
minimum-interval—Configures the minimum interval, in milliseconds, after which the local routing device transmits hello packets as well as the minimum interval after which the routing device expects to receive a reply from the neighbor with which it has established a BFD session. You can configure a number in the range from 1 through 255,000 milliseconds. You can also specify the minimum transmit and receive intervals separately using the transmit-interval minimum-interval and
minimum-receive-intervalstatements.Note:Depending on your network environment, these additional recommendations might apply:
-
For large-scale network deployments with a large number of BFD sessions, specify a minimum interval of no less than 500 ms. An interval of 1000 ms is recommended to avoid any instability issues.
Note:-
For the bfdd process, the detection time interval set is lower than 300 ms. If there is a high priority process such as ppmd running on the system, the CPU might spend time on the ppmd process rather than the bfdd process.
-
For branch SRX Series Firewalls, we recommend 1000 ms as the minimum keepalive time interval for BFD packets.
-
For vSRX 3.0, we recommend 300 ms as the minimum keepalive time interval for BFD packets.
-
-
For very large-scale network deployments with a large number of BFD sessions, contact Juniper Networks customer support for more information.
-
For BFD sessions to remain up during a Routing Engine switchover event when nonstop active routing (NSR) is configured, specify a minimum interval of 2500 ms for Routing Engine-based sessions. For distributed BFD sessions with NSR configured, the minimum interval recommendations are unchanged and depend only on your network deployment.
-
multiplier—Configures the number of hello packets not received by a neighbor that causes the originating interface to be declared down. By default, three missed hello packets cause the originating interface to be declared down. You can configure a value in the range from 1 through 255.
Topology
Configuration
Procedure
CLI Quick Configuration
To quickly configure the BFD protocol for
OSPF, copy the following commands, paste them into a text file, remove
any line breaks, change any details necessary to match your network
configuration, copy and paste the commands into the CLI at the [edit]
hierarchy level, and then enter commit from configuration
mode.
[edit] set protocols ospf area 0.0.0.0 interface fe-0/0/1 bfd-liveness-detection minimum-interval 300 set protocols ospf area 0.0.0.0 interface fe-0/0/1 bfd-liveness-detection multiplier 4 set protocols ospf area 0.0.0.0 interface fe-0/0/1 bfd-liveness-detection full-neighbors-only
Step-by-Step Procedure
To configure the BFD protocol for OSPF on one neighboring interface:
Create an OSPF area.
Note:To specify OSPFv3, include the
ospf3statement at the[edit protocols]hierarchy level.[edit] user@host# edit protocols ospf area 0.0.0.0
Specify the interface.
[edit protocols ospf area 0.0.0.0] user@host# set interface fe-0/0/1
Specify the minimum transmit and receive intervals.
[edit protocols ospf area 0.0.0.0 ] user@host# set interface fe-0/0/1 bfd-liveness-detection minimum-interval 300
Configure the number of missed hello packets that cause the originating interface to be declared down.
[edit protocols ospf area 0.0.0.0 ] user@host# set interface fe-0/0/1 bfd-liveness-detection multiplier 4
Configure BFD sessions only for OSPF neighbors with full neighbor adjacency.
[edit protocols ospf area 0.0.0.0 ] user@host# set interface fe-0/0/1 bfd-liveness-detection full-neighbors-only
If you are done configuring the device, commit the configuration.
[edit protocols ospf area 0.0.0.0 ] user@host# commit
Note:Repeat this entire configuration on the other neighboring interface.
Results
Confirm your configuration by entering the show
protocols ospf command. If the output does not display the intended
configuration, repeat the instructions in this example to correct
the configuration.
user@host# show protocols ospf
area 0.0.0.0 {
interface fe-0/0/1.0 {
bfd-liveness-detection {
minimum-interval 300;
multiplier 4;
full-neighbors-only;
}
}
}
To confirm your OSPFv3 configuration, enter the show protocols
ospf3 command.
Verification
Confirm that the configuration is working properly.
Verifying the BFD Sessions
Purpose
Verify that the OSPF interfaces have active BFD sessions, and that session components have been configured correctly.
Action
From operational mode, enter the show bfd session detail command.
Meaning
The output displays information about the BFD sessions.
The Address field displays the IP address of the neighbor.
The Interface field displays the interface you configured for BFD.
The State field displays the state of the neighbor and should show Full to reflect the full neighbor adjacency that you configured.
The Transmit Interval field displays the time interval you configured to send BFD packets.
The Multiplier field displays the multiplier you configured.
Example: Configuring BFD for IS-IS
This example describes how to configure the Bidirectional Forwarding Detection (BFD) protocol to detect failures in an IS-IS network.
BFD is not supported with ISIS for IPV6 on QFX10000 series switches.
Requirements
Before you begin, configure IS-IS on both routers. See Example: Configuring IS-IS for information about the required IS-IS configuration.
We provide the IS-IS configuration in the CLI quick configuration section but do not cover the IS-IS configuration in the step-by-step.
This example uses the following hardware and software components:
-
Junos OS Release 7.3 or later
-
Updated and revalidated using Junos OS Release 22.4
-
-
M Series, MX Series, and T Series routers
Overview
This example shows two routers connected to each other. A loopback interface is configured on each router. IS-IS and BFD protocols are configured on both routers.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a
text file, remove any line breaks, change any details necessary to match your
network configuration, and then copy and paste the commands into the CLI at the
[edit] hierarchy level.
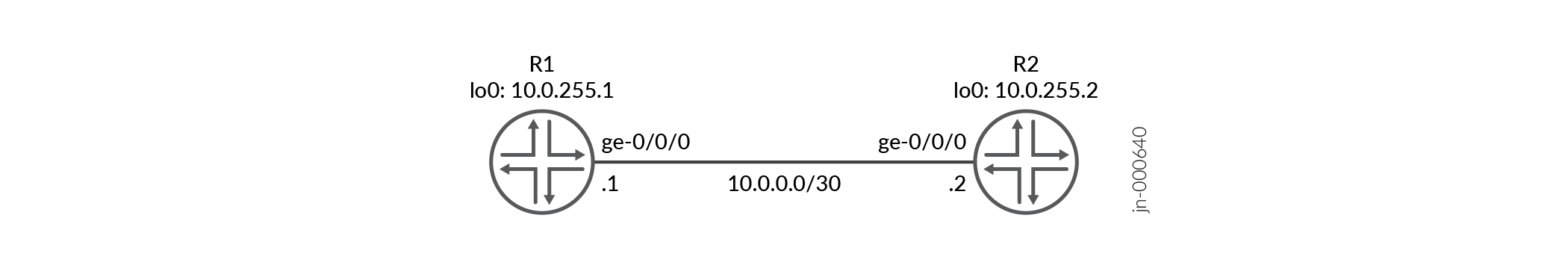
Router R1
set interfaces ge-0/0/0 unit 0 family inet address 10.0.0.1/30 set interfaces ge-0/0/0 unit 0 family iso set interfaces lo0 unit 0 family inet address 10.0.255.1/32 set interfaces lo0 unit 0 family iso address 49.0001.0010.0255.0001.00 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection version automatic set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection minimum-interval 200 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection minimum-receive-interval 100 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection multiplier 2 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection no-adaptation set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection transmit-interval minimum-interval 100 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection transmit-interval threshold 300 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection detection-time threshold 500 set protocols isis interface lo0.0
Router R2
set interfaces ge-0/0/0 unit 0 family inet address 10.0.0.2/30 set interfaces ge-0/0/0 unit 0 family iso set interfaces lo0 unit 0 family inet address 10.0.255.2/32 set interfaces lo0 unit 0 family iso address 49.0001.0010.0255.0002.00 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection version automatic set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection minimum-interval 200 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection minimum-receive-interval 100 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection multiplier 2 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection no-adaptation set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection transmit-interval minimum-interval 100 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection transmit-interval threshold 300 set protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection detection-time threshold 500 set protocols isis interface lo0.0
Procedure
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode.
To simply configure BFD for IS-IS, only the
minimum-interval statement is required. The BFD
protocol selects default parameters for all the other configuration
statements when you use the bfd-liveness-detection
statement without specifying any parameters.
You can change parameters at any time without stopping or restarting the existing session. BFD automatically adjusts to the new parameter value. However, no changes to BFD parameters take place until the values resynchronize with each BFD peer.
To configure BFD for IS-IS on Routers R1 and R2:
We are only showing the steps for R1.
-
Configure the threshold for the adaptation of the detection time, which must be greater than the multiplier number multiplied by the minimum interval.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set detection-time threshold 500
-
Configure the minimum transmit and receive intervals for failure detection.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set minimum-interval 200
-
Configure only the minimum receive interval for failure detection.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set minimum-receive-interval 100
-
Disable BFD adaptation.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set no-adaptation
-
Configure the threshold for the transmit interval, which must be greater than the minimum transmit interval.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set transmit-interval threshold 300
-
Configure the minimum transmit interval for failure detection.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set transmit-interval minimum-interval 100
-
Configure the multiplier number, which is the number of hello packets not received by the neighbor that causes the originating interface to be declared down.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set multiplier 2
-
Configure the BFD version used for detection.
The default is to have the version detected automatically.
[edit protocols isis interface ge-0/0/0.0 family inet bfd-liveness-detection] user@R1# set version automatic
Results
From configuration mode, confirm your configuration by issuing the show
protocols isis interface command. If the output does not display
the intended configuration, repeat the instructions in this example to correct
the configuration.
user@R1# show protocols isis interface ge-0/0/0.0 family inet
bfd-liveness-detection {
version automatic;
minimum-interval 200;
minimum-receive-interval 100;
multiplier 2;
no-adaptation;
transmit-interval {
minimum-interval 100;
threshold 300;
}
detection-time {
threshold 500;
}
}Verification
Confirm that the configuration is working properly.
- Verifying the Connection Between Routers R1 and R2
- Verifying That IS-IS Is Configured
- Verifying That BFD Is configured
Verifying the Connection Between Routers R1 and R2
Purpose
Make sure that Routers R1 and R2 can reach each other.
Action
Ping the other router to check the connectivity between the two routers as per the network topology.
user@R1> ping 10.0.0.2 count 2 PING 10.0.0.2 (10.0.0.2): 56 data bytes 64 bytes from 10.0.0.2: icmp_seq=0 ttl=64 time=2.148 ms 64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=1.923 ms --- 10.0.0.2 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.923/2.035/2.148/0.113 ms
Meaning
Routers R1 and R2 are able to ping each other.
Verifying That IS-IS Is Configured
Purpose
Make sure that the IS-IS instance is running on both routers.
Action
Use the show isis database statement to check if the IS-IS
instance is running on both routers, R1 and R2.
user@R1> show isis database IS-IS level 1 link-state database: LSP ID Sequence Checksum Lifetime Attributes R1.00-00 0x1b 0xa2d5 552 L1 L2 R1.02-00 0x2b 0x8da3 545 L1 L2 R2.00-00 0x1a 0x628d 543 L1 L2 3 LSPs IS-IS level 2 link-state database: LSP ID Sequence Checksum Lifetime Attributes R1.00-00 0x1e 0xb9ba 552 L1 L2 R1.02-00 0x2b 0x8da3 545 L1 L2 R2.00-00 0x1d 0x877e 543 L1 L2 3 LSPs
Meaning
IS-IS is configured on both routers, R1 and R2.
Verifying That BFD Is configured
Purpose
Make sure that the BFD instance is running on both routers, R1 and R2.
Action
Use the show bfd session detail statement to check if BFD
instance is running on the routers.
user@R1> show bfd session detail
Detect Transmit
Address State Interface Time Interval Multiplier
10.0.0.2 Up ge-0/0/0.0 0.200 0.100 2
Client ISIS L1, TX interval 0.100, RX interval 0.100
Client ISIS L2, TX interval 0.100, RX interval 0.100
Session up time 00:02:41, previous down time 00:00:09
Local diagnostic None, remote diagnostic None
Remote state Up, version 1
Session type: Single hop BFD
1 sessions, 2 clients
Cumulative transmit rate 10.0 pps, cumulative receive rate 10.0 ppsMeaning
BFD is configured on Routers R1 and R2 for detecting failures in the IS-IS network.
Example: Configuring BFD for RIP
This example shows how to configure Bidirectional Forwarding Detection (BFD) for a RIP network.
Requirements
No special configuration beyond device initialization is required before configuring this example.
Overview
To enable failure detection, include the bfd-liveness-detection statement:
bfd-liveness-detection { detection-time { threshold milliseconds; } minimum-interval milliseconds; minimum-receive-interval milliseconds; multiplier number; no-adaptation; transmit-interval { threshold milliseconds; minimum-interval milliseconds; } version (1 | automatic); }
Optionally, you can specify the threshold for the adaptation
of the detection time by including the threshold statement.
When the BFD session detection time adapts to a value equal to or
greater than the threshold, a single trap and a system log message
are sent.
To specify the minimum transmit and receive interval for failure
detection, include the minimum-interval statement. This
value represents the minimum interval at which the local routing device
transmits hello packets as well as the minimum interval at which the
routing device expects to receive a reply from a neighbor with which
it has established a BFD session. You can configure a value in the
range from 1 through 255,000 milliseconds. This examples
sets a minimum interval of 600 milliseconds.
Depending on your network environment, these additional recommendations might apply:
The reccomended minimum interval for distributed BFD is 100 ms with a
multiplierof 3.For very large-scale network deployments with a large number of BFD sessions, contact Juniper Networks customer support for more information.
For BFD sessions to remain up during a Routing Engine switchover event when nonstop active routing (NSR) is configured, specify a minimum interval of 2500 ms for Routing Engine-based sessions. For distributed BFD sessions with nonstop active routing configured, the minimum interval recommendations are unchanged and depend only on your network deployment.
You can optionally specify the minimum transmit and receive intervals separately.
To specify only the minimum receive interval for failure detection,
include the minimum-receive-interval statement. This value
represents the minimum interval at which the local routing device
expects to receive a reply from a neighbor with which it has established
a BFD session. You can configure a value in the range from 1
through 255,00 milliseconds.
To specify only the minimum transmit interval for failure detection,
include the transmit-interval minimum-interval statement.
This value represents the minimum interval at which the local routing
device transmits hello packets to the neighbor with which it has established
a BFD session. You can configure a value in the range from 1
through 255,000 milliseconds.
To specify the number of hello packets not received by a neighbor
that causes the originating interface to be declared down, include
the multiplier statement. The default is 3, and you
can configure a value in the range from 1 through 255.
To specify the threshold for detecting the adaptation of the
transmit interval, include the transmit-interval threshold statement. The threshold value must be greater than the transmit
interval.
To specify the BFD version used for detection, include the version statement. The default is to have the version detected
automatically.
You can trace BFD operations by including the traceoptions statement at the [edit protocols bfd] hierarchy level.
In Junos OS Release 9.0 and later, you can configure BFD
sessions not to adapt to changing network conditions. To disable BFD
adaptation, include the no-adaptation statement. We recommend
that you not disable BFD adaptation unless it is preferable not to
have BFD adaptation enabled in your network.
Figure 4 shows the topology used in this example.
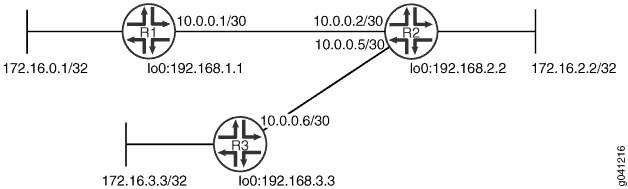
CLI Quick Configuration shows the configuration for all of the devices in Figure 4. The section Step-by-Step Procedure describes the steps on Device R1.
Topology
Configuration
Procedure
CLI Quick Configuration
To quickly configure this
example, copy the following commands, paste them into a text file,
remove any line breaks, change any details necessary to match your
network configuration, and then copy and paste the commands into the
CLI at the [edit] hierarchy level.
Device R1
set interfaces fe-1/2/0 unit 1 family inet address 10.0.0.1/30 set protocols bfd traceoptions file bfd-trace set protocols bfd traceoptions flag all set protocols rip group rip-group export advertise-routes-through-rip set protocols rip group rip-group neighbor fe-1/2/0.1 set protocols rip group rip-group bfd-liveness-detection minimum-interval 600 set policy-options policy-statement advertise-routes-through-rip term 1 from protocol direct set policy-options policy-statement advertise-routes-through-rip term 1 from protocol rip set policy-options policy-statement advertise-routes-through-rip term 1 then accept
Device R2
set interfaces fe-1/2/0 unit 2 family inet address 10.0.0.2/30 set interfaces fe-1/2/1 unit 5 family inet address 10.0.0.5/30 set protocols rip group rip-group export advertise-routes-through-rip set protocols rip group rip-group neighbor fe-1/2/0.2 set protocols rip group rip-group neighbor fe-1/2/1.5 set protocols rip group rip-group bfd-liveness-detection minimum-interval 600 set policy-options policy-statement advertise-routes-through-rip term 1 from protocol direct set policy-options policy-statement advertise-routes-through-rip term 1 from protocol rip set policy-options policy-statement advertise-routes-through-rip term 1 then accept
Device R3
set interfaces fe-1/2/0 unit 6 family inet address 10.0.0.6/30 set protocols rip group rip-group export advertise-routes-through-rip set protocols rip group rip-group neighbor fe-1/2/0.6 set protocols rip group rip-group bfd-liveness-detection minimum-interval 600 set policy-options policy-statement advertise-routes-through-rip term 1 from protocol direct set policy-options policy-statement advertise-routes-through-rip term 1 from protocol rip set policy-options policy-statement advertise-routes-through-rip term 1 then accept
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a BFD for a RIP network:
-
Configure the network interfaces.
[edit interfaces] user@R1# set fe-1/2/0 unit 1 family inet address 10.0.0.1/30
-
Create the RIP group and add the interface.
To configure RIP in Junos OS, you must configure a group that contains the interfaces on which RIP is enabled. You do not need to enable RIP on the loopback interface.
[edit protocols rip group rip-group] user@R1# set neighbor fe-1/2/0.1
-
Create the routing policy to advertise both direct and RIP-learned routes.
[edit policy-options policy-statement advertise-routes-through-rip term 1] user@R1# set from protocol direct user@R1# set from protocol rip user@R1# set then accept
-
Apply the routing policy.
In Junos OS, you can only apply RIP export policies at the group level.
[edit protocols rip group rip-group] user@R1# set export advertise-routes-through-rip
-
Enable BFD.
[edit protocols rip group rip-group] user@R1# set bfd-liveness-detection minimum-interval 600
-
Configure tracing operations to track BFD messages.
[edit protocols bfd traceoptions] user@R1# set file bfd-trace user@R1# set flag all
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show protocols, and show policy-options commands. If the output does
not display the intended configuration, repeat the configuration instructions
in this example to correct it.
user@R1# show interfaces
fe-1/2/0 {
unit 1 {
family inet {
address 10.0.0.1/30;
}
}
}
user@R1# show protocols
bfd {
traceoptions {
file bfd-trace;
flag all;
}
}
rip {
group rip-group {
export advertise-routes-through-rip;
bfd-liveness-detection {
minimum-interval 600;
}
neighbor fe-1/2/0.1;
}
}
user@R1# show policy-options
policy-statement advertise-routes-through-rip {
term 1 {
from protocol [ direct rip ];
then accept;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Verifying That the BFD Sessions Are Up
Purpose
Make sure that the BFD sessions are operating.
Action
From operational mode, enter the show bfd session command.
user@R1> show bfd session
Detect Transmit
Address State Interface Time Interval Multiplier
10.0.0.2 Up fe-1/2/0.1 1.800 0.600 3
1 sessions, 1 clients
Cumulative transmit rate 1.7 pps, cumulative receive rate 1.7 ppsMeaning
The output shows that there are no authentication failures.
Checking the BFD Trace File
Purpose
Use tracing operations to verify that BFD packets are being exchanged.
Action
From operational mode, enter the show log command.
user@R1> show log bfd-trace Feb 16 10:26:32 PPM Trace: BFD periodic xmit to 10.0.0.2 (IFL 124, rtbl 53, single-hop port) Feb 16 10:26:32 Received Downstream TraceMsg (24) len 86: Feb 16 10:26:32 IfIndex (3) len 4: 0 Feb 16 10:26:32 Protocol (1) len 1: BFD Feb 16 10:26:32 Data (9) len 61: (hex) 42 46 44 20 70 61 63 6b 65 74 20 66 72 6f 6d 20 31 30 2e Feb 16 10:26:32 PPM Trace: BFD packet from 10.0.0.1 (IFL 73, rtbl 56, ttl 255) absorbed Feb 16 10:26:32 Received Downstream TraceMsg (24) len 60: Feb 16 10:26:32 IfIndex (3) len 4: 0 Feb 16 10:26:32 Protocol (1) len 1: BFD Feb 16 10:26:32 Data (9) len 35: (hex) 42 46 44 20 70 65 72 69 6f 64 69 63 20 78 6d 69 74 20 6f ...
Meaning
The output shows the normal functioning of BFD.
Configuring Micro BFD Sessions for LAG
The Bidirectional Forwarding Detection (BFD) protocol is a simple detection protocol that quickly detects failures in the forwarding paths. A link aggregation group (LAG) combines multiple links between devices that are in point-to-point connections, thereby increasing bandwidth, providing reliability, and allowing load balancing. To run a BFD session on LAG interfaces, configure an independent, asynchronous mode BFD session on every LAG member link in a LAG bundle. Instead of a single BFD session monitoring the status of the UDP port, independent micro BFD sessions monitor the status of individual member links.
Starting in Junos OS Evolved Release 20.1R1, independent micro Bidirectional Forwarding Detection (BFD) sessions are enabled on a per member link basis of a Link Aggregation Group (LAG) bundle.
To enable failure detection for aggregated Ethernet interfaces:
The
versionoption is not supported on the QFX Series. Starting in Junos OS Release 17.2R1, a warning will appear if you attempt to use this command.This feature works when both the devices support BFD. If BFD is configured at only one end of the LAG, this feature does not work.
Example: Configuring Independent Micro BFD Sessions for LAG
This example shows how to configure an independent micro BFD session for aggregated Ethernet interfaces.
Requirements
This example uses the following hardware and software components:
-
MX Series routers with Junos Trio chipset
Note: AFT-based Trio line cards (MPC10 and newer) use a different hardware design. If micro BFD is activated on an interface, the received packets won't be part of the interface group for the AE interface and won't match filter terms on lo0.0 with the interface group. To ensure terms match, you can set up a separate filter on lo0.0 using port 6784. T Series routers with Type 4 FPC or Type 5 FPC
BFD for LAG is supported on the following PIC types on T-Series:
PC-1XGE-XENPAK (Type 3 FPC),
PD-4XGE-XFP (Type 4 FPC),
PD-5-10XGE-SFPP (Type 4 FPC),
24x10GE (LAN/WAN) SFPP, 12x10GE (LAN/WAN) SFPP, 1X100GE Type 5 PICs
PTX Series routers with 24X10GE (LAN/WAN) SFPP
Junos OS Release 13.3 or later running on all devices
Overview
The example includes two routers that are directly connected. Configure two aggregated Ethernet interfaces, AE0 for IPv4 connectivity and AE1 for IPv6 connectivity. Configure micro BFD session on the AE0 bundle using IPv4 addresses as local and neighbor endpoints on both routers. Configure micro BFD session on the AE1 bundle using IPv6 addresses as local and neighbor endpoints on both routers. This example verifies that independent micro BFD sessions are active in the output.
Topology
Figure 5 shows the sample topology.
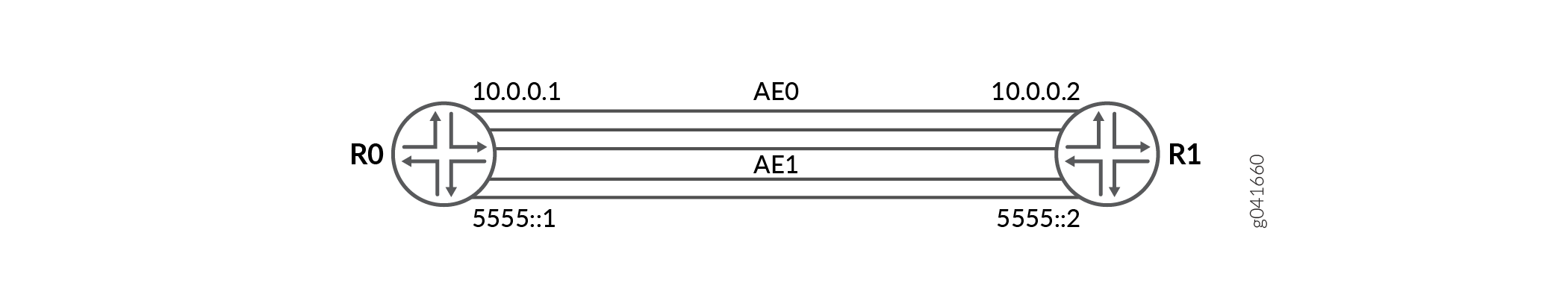
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, and then copy and paste the commands into the CLI at the [edit] hierarchy level.
Router R0
set interfaces ge-1/0/1 unit 0 family inet address 20.20.20.1/30 set interfaces ge-1/0/1 unit 0 family inet6 address 3ffe::1:1/126 set interfaces xe-4/0/0 gigether-options 802.3ad ae0 set interfaces xe-4/0/1 gigether-options 802.3ad ae0 set interfaces xe-4/1/0 gigether-options 802.3ad ae1 set interfaces xe-4/1/1 gigether-options 802.3ad ae1 set interfaces lo0 unit 0 family inet address 10.255.106.107/32 set interfaces lo0 unit 0 family inet6 address 201:DB8:251::aa:aa:1/126 set interfaces ae0 aggregated-ether-options bfd-liveness-detection minimum-interval 100 set interfaces ae0 aggregated-ether-options bfd-liveness-detection neighbor 10.255.106.102 set interfaces ae0 aggregated-ether-options bfd-liveness-detection local-address 10.255.106.107 set interfaces ae0 aggregated-ether-options minimum-links 1 set interfaces ae0 aggregated-ether-options link-speed 10g set interfaces ae0 aggregated-ether-options lacp active set interfaces ae0 unit 0 family inet address 10.0.0.1/30 set interfaces ae1 aggregated-ether-options bfd-liveness-detection minimum-interval 100 set interfaces ae1 aggregated-ether-options bfd-liveness-detection multiplier 3 set interfaces ae1 aggregated-ether-options bfd-liveness-detection neighbor 201:DB8:251::bb:bb:1 set interfaces ae1 aggregated-ether-options bfd-liveness-detection local-address 201:DB8:251::aa:aa:1 set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options link-speed 10g set interfaces ae1 aggregated-ether-options lacp active set interfaces ae1 unit 0 family inet6 address 5555::1/126 set interface ae1 unit 0 family inet6 dad-disable set routing-options nonstop-routing set routing-options static route 30.30.30.0/30 next-hop 10.0.0.2 set routing-options rib inet6.0 static route 3ffe::1:2/126 next-hop 5555::2 set protocols bfd traceoptions file bfd set protocols bfd traceoptions file size 100m set protocols bfd traceoptions file files 10 set protocols bfd traceoptions flag all
Router R1
set interfaces ge-1/1/8 unit 0 family inet address 30.30.30.1/30 set interfaces ge-1/1/8 unit 0 family inet6 address 3ffe::1:2/126 set interfaces xe-0/0/0 gigether-options 802.3ad ae0 set interfaces xe-0/0/1 gigether-options 802.3ad ae0 set interfaces xe-0/0/2 gigether-options 802.3ad ae1 set interfaces xe-0/0/3 gigether-options 802.3ad ae1 set interfaces lo0 unit 0 family inet address 10.255.106.102/32 set interfaces lo0 unit 0 family inet6 address 201:DB8:251::bb:bb:1/126 set interfaces ae0 aggregated-ether-options bfd-liveness-detection minimum-interval 150 set interfaces ae0 aggregated-ether-options bfd-liveness-detection multiplier 3 set interfaces ae0 aggregated-ether-options bfd-liveness-detection neighbor 10.255.106.107 set interfaces ae0 aggregated-ether-options bfd-liveness-detection local-address 10.255.106.102 set interfaces ae0 aggregated-ether-options minimum-links 1 set interfaces ae0 aggregated-ether-options link-speed 10g set interfaces ae0 aggregated-ether-options lacp passive set interfaces ae0 unit 0 family inet address 10.0.0.2/30 set interfaces ae1 aggregated-ether-options bfd-liveness-detection minimum-interval 200 set interfaces ae1 aggregated-ether-options bfd-liveness-detection multiplier 3 set interfaces ae1 aggregated-ether-options bfd-liveness-detection neighbor 201:DB8:251::aa:aa:1 set interfaces ae1 aggregated-ether-options bfd-liveness-detection local-address 201:DB8:251::bb:bb:1 set interfaces ae1 aggregated-ether-options minimum-links 1 set interfaces ae1 aggregated-ether-options link-speed 10g set interfaces ae1 aggregated-ether-options lacp passive set interfaces ae1 unit 0 family inet6 address 5555::2/126 set routing-options static route 20.20.20.0/30 next-hop 10.0.0.1 set routing-options rib inet6.0 static route 3ffe::1:1/126 next-hop 5555::1
Configuring a Micro BFD Session for Aggregated Ethernet Interfaces
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see “Using the CLI Editor in Configuration Mode” in the CLI User Guide.
Repeat this procedure for Router R1, modifying the appropriate interface names, addresses, and any other parameters for each router.
To configure a micro BFD session for aggregated Ethernet interfaces on Router R0:
Configure the physical interfaces.
[edit interfaces] user@R0# set ge-1/0/1 unit 0 family inet address 20.20.20.1/30 user@R0# set ge-1/0/1 unit 0 family inet6 address 3ffe::1:1/126 user@R0# set xe-4/0/0 gigether-options 802.3ad ae0 user@R0# set xe-4/0/1 gigether-options 802.3ad ae0 user@R0# set xe-4/1/0 gigether-options 802.3ad ae1 user@R0# set xe-4/1/1 gigether-options 802.3ad ae1
Configure the loopback interface.
[edit interfaces] user@R0# set lo0 unit 0 family inet address 10.255.106.107/32 user@R0# set lo0 unit 0 family inet6 address 201:DB8:251::aa:aa:1/128
Configure an IP address on the aggregated Ethernet interface ae0 with either IPv4 or IPv6 addresses, as per your network requirements.
[edit interfaces] user@R0# set ae0 unit 0 family inet address 10.0.0.1/30
Set the routing option, create a static route, and set the next-hop address.
Note:You can configure either an IPv4 or IPv6 static route, depending on your network requirements.
[edit routing-options] user@R0# set nonstop-routing user@R0# set static route 30.30.30.0/30 next-hop 10.0.0.2 user@R0# set rib inet6.0 static route 3ffe::1:2/126 next-hop 5555::2
Configure the Link Aggregation Control Protocol (LACP).
[edit interfaces] user@R0# set ae0 aggregated-ether-options lacp active
Configure BFD for the aggregated Ethernet interface ae0, and specify the minimum interval, local IP address, and the neighbor IP address.
[edit interfaces] user@R0# set ae0 aggregated-ether-options bfd-liveness-detection minimum-interval 100 user@R0# set ae0 aggregated-ether-options bfd-liveness-detection multiplier 3 user@R0# set ae0 aggregated-ether-options bfd-liveness-detection neighbor 10.255.106.102 user@R0# set ae0 aggregated-ether-options bfd-liveness-detection local-address 10.255.106.107 user@R0# set ae0 aggregated-ether-options minimum-links 1 user@R0# set ae0 aggregated-ether-options link-speed 10g
Configure an IP addresse on the aggregated Ethernet interface ae1.
You can assign either IPv4 or IPv6 addresses as per your network requirements.
[edit interfaces] user@R0# set ae1 unit 0 family inet6 address 5555::1/126
Configure BFD for the aggregated Ethernet interface ae1.
[edit interfaces] user@R0# set ae1 aggregated-ether-options bfd-liveness-detection minimum-interval 100 user@R0# set ae1 aggregated-ether-options bfd-liveness-detection multiplier 3 user@R0# set ae1 aggregated-ether-options bfd-liveness-detection neighbor 201:DB8:251::bb:bb:1 user@R0# set ae1 aggregated-ether-options bfd-liveness-detection local-address 201:DB8:251::aa:aa:1 user@R0# set ae1 aggregated-ether-options minimum-links 1 user@R0# set ae1 aggregated-ether-options link-speed 10g
Note:Beginning with Junos OS Release 16.1, you can also configure this feature with the AE interface address as the local address in a micro BFD session.
Beginning with Release 16.1R2, Junos OS checks and validates the configured micro BFD
local-addressagainst the interface or loopback IP address before the configuration commit. Junos OS performs this check on both IPv4 and IPv6 micro BFD address configurations, and if they do not match, the commit fails.Configure tracing options for BFD for troubleshooting.
[edit protocols] user@R0# set bfd traceoptions file bfd user@R0# set bfd traceoptions file size 100m user@R0# set bfd traceoptions file files 10 user@R0# set bfd traceoptions flag all
Results
From configuration mode, enter the show interfaces, show protocols, and show routing-options commands and confirm your configuration. If the output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
user@R0> show interfaces
traceoptions {
flag bfd-events;
}
ge-1/0/1 {
unit 0 {
family inet {
address 20.20.20.1/30;
}
family inet6 {
address 3ffe::1:1/126;
}
}
}
xe-4/0/0 {
enable;
gigether-options {
802.3ad ae0;
}
}
xe-4/0/1 {
gigether-options {
802.3ad ae0;
}
}
xe-4/1/0 {
enable;
gigether-options {
802.3ad ae1;
}
}
xe-4/1/1 {
gigether-options {
802.3ad ae1;
}
}
lo0 {
unit 0 {
family inet {
address 10.255.106.107/32;
}
family inet6 {
address 201:DB8:251::aa:aa:1/128;
}
}
}
ae0 {
aggregated-ether-options {
bfd-liveness-detection {
minimum-interval 100;
neighbor 10.255.106.102;
local-address 10.255.106.107;
}
minimum-links 1;
link-speed 10g;
lacp {
active;
}
}
unit 0 {
family inet {
address 10.0.0.1/30;
}
}
}
ae1 {
aggregated-ether-options {
bfd-liveness-detection {
minimum-interval 100;
multiplier 3;
neighbor 201:DB8:251::bb:bb:1;
local-address 201:DB8:251::aa:aa:1;
}
minimum-links 1
link-speed 10g;
}
unit 0 {
family inet6 {
address 5555::1/126;
}
}
}
user@R0> show protocols
bfd {
traceoptions {
file bfd size 100m files 10;
flag all;
}
}
user@R0> show routing-options
nonstop-routing ;
rib inet6.0 {
static {
route 3ffe:1:2/126 {
next-hop 5555::2;
}
}
}
static {
route 30.30.30.0/30 {
next-hop 10.0.0.2;
}
}
If you are done configuring the device, commit the configuration.
user@R0# commit
Verification
Confirm that the configuration is working properly.
Verifying That the Independent BFD Sessions Are Up
Purpose
Verify that the micro BFD sessions are up, and view details about the BFD sessions.
Action
From operational mode, enter the show bfd session extensive command.
user@R0> show bfd session extensive
Detect Transmit
Address State Interface Time Interval Multiplier
10.255.106.102 Up xe-4/0/0 9.000 3.000 3
Client LACPD, TX interval 0.100, RX interval 0.100
Session up time 4d 23:13, previous down time 00:00:06
Local diagnostic None, remote diagnostic None
Remote heard, hears us, version 1
Replicated
Session type: Micro BFD
Min async interval 0.100, min slow interval 1.000
Adaptive async TX interval 0.100, RX interval 0.100
Local min TX interval 0.100, minimum RX interval 0.100, multiplier 3
Remote min TX interval 3.000, min RX interval 3.000, multiplier 3
Local discriminator 21, remote discriminator 75
Echo mode disabled/inactive
Remote is control-plane independent
Session ID: 0x0
Detect Transmit
Address State Interface Time Interval Multiplier
10.255.106.102 Up xe-4/0/1 9.000 3.000 3
Client LACPD, TX interval 0.100, RX interval 0.100
Session up time 4d 23:13, previous down time 00:00:07
Local diagnostic None, remote diagnostic None
Remote heard, hears us, version 1
Replicated
Session type: Micro BFD
Min async interval 0.100, min slow interval 1.000
Adaptive async TX interval 0.100, RX interval 0.100
Local min TX interval 0.100, minimum RX interval 0.100, multiplier 3
Remote min TX interval 3.000, min RX interval 3.000, multiplier 3
Local discriminator 19, remote discriminator 74
Echo mode disabled/inactive
Remote is control-plane independent
Session ID: 0x0
Detect Transmit
Address State Interface Time Interval Multiplier
201:DB8:251::bb:bb:1 Up xe-4/1/1 9.000 3.000 3
Client LACPD, TX interval 0.100, RX interval 0.100
Session up time 4d 23:13
Local diagnostic None, remote diagnostic None
Remote not heard, hears us, version 1
Replicated
Session type: Micro BFD
Min async interval 0.100, min slow interval 1.000
Adaptive async TX interval 0.100, RX interval 0.100
Local min TX interval 1.000, minimum RX interval 0.100, multiplier 3
Remote min TX interval 3.000, min RX interval 3.000, multiplier 3
Local discriminator 17, remote discriminator 67
Echo mode disabled/inactive, no-absorb, no-refresh
Remote is control-plane independent
Session ID: 0x0
Detect Transmit
Address State Interface Time Interval Multiplier
201:DB8:251::bb:bb:1 UP xe-4/1/0 9.000 3.000 3
Client LACPD, TX interval 0.100, RX interval 0.100
Session up time 4d 23:13
Local diagnostic None, remote diagnostic None
Remote not heard, hears us, version 1
Replicated
Session type: Micro BFD
Min async interval 0.100, min slow interval 1.000
Adaptive async TX interval 0.100, RX interval 0.100
Local min TX interval 1.000, minimum RX interval 0.100, multiplier 3
Remote min TX interval 3.000, min RX interval 3.000, multiplier 3
Local discriminator 16, remote discriminator 66
Echo mode disabled/inactive, no-absorb, no-refresh
Remote is control-plane independent
Session ID: 0x0
4 sessions, 4 clients
Cumulative transmit rate 2.0 pps, cumulative receive rate 1.7 pps
Meaning
The Micro BFD field represents the independent micro BFD sessions running on the links in a LAG. The TX interval item, RX interval item output represents the setting configured with the minimum-interval statement. All of the other output represents the default settings for BFD. To modify the default settings, include the optional statements under bfd-liveness-detection statement.
Viewing Detailed BFD Events
Purpose
View the contents of the BFD trace file to assist in troubleshooting, if required.
Action
From operational mode, enter the file show /var/log/bfd command.
user@R0> file show /var/log/bfd Jun 5 00:48:59 Protocol (1) len 1: BFD Jun 5 00:48:59 Data (9) len 41: (hex) 42 46 44 20 6e 65 69 67 68 62 6f 72 20 31 30 2e 30 2e 30 Jun 5 00:48:59 PPM Trace: BFD neighbor 10.255.106.102 (IFL 349) set, 9 0 Jun 5 00:48:59 Received Downstream RcvPkt (19) len 108: Jun 5 00:48:59 IfIndex (3) len 4: 329 Jun 5 00:48:59 Protocol (1) len 1: BFD Jun 5 00:48:59 SrcAddr (5) len 8: 10.255.106.102 Jun 5 00:48:59 Data (9) len 24: (hex) 00 88 03 18 00 00 00 4b 00 00 00 15 00 2d c6 c0 00 2d c6 Jun 5 00:48:59 PktError (26) len 4: 0 Jun 5 00:48:59 RtblIdx (24) len 4: 0 Jun 5 00:48:59 MultiHop (64) len 1: (hex) 00 Jun 5 00:48:59 Unknown (168) len 1: (hex) 01 Jun 5 00:48:59 Unknown (171) len 2: (hex) 02 3d Jun 5 00:48:59 Unknown (172) len 6: (hex) 80 71 1f c7 81 c0 Jun 5 00:48:59 Authenticated (121) len 1: (hex) 01 Jun 5 00:48:59 BFD packet from 10.0.0.2 (IFL 329), len 24 Jun 5 00:48:59 Ver 0, diag 0, mult 3, len 24 Jun 5 00:48:59 Flags: IHU Fate Jun 5 00:48:59 My discr 0x0000004b, your discr 0x00000015 Jun 5 00:48:59 Tx ivl 3000000, rx ivl 3000000, echo rx ivl 0 Jun 5 00:48:59 [THROTTLE]bfdd_rate_limit_can_accept_pkt: session 10.255.106.102 is up or already in program thread Jun 5 00:48:59 Replicate: marked session (discr 21) for update
Meaning
BFD messages are being written to the specified trace file.
Configuring BFD for PIM
The Bidirectional Forwarding Detection (BFD) Protocol is a simple hello mechanism that detects failures in a network. BFD works with a wide variety of network environments and topologies. A pair of routing devices exchanges BFD packets. Hello packets are sent at a specified, regular interval. A neighbor failure is detected when the routing device stops receiving a reply after a specified interval. The BFD failure detection timers have shorter time limits than the Protocol Independent Multicast (PIM) hello hold time, so they provide faster detection.
The BFD failure detection timers are adaptive
and can be adjusted to be faster or slower. The lower the BFD failure
detection timer value, the faster the failure detection and vice versa.
For example, the timers can adapt to a higher value if the adjacency
fails (that is, the timer detects failures more slowly). Or a neighbor
can negotiate a higher value for a timer than the configured value.
The timers adapt to a higher value when a BFD session flap occurs
more than three times in a span of 15 seconds. A back-off algorithm
increases the receive (Rx) interval by two if the local BFD instance
is the reason for the session flap. The transmission (Tx) interval
is increased by two if the remote BFD instance is the reason for the
session flap. You can use the clear bfd adaptation command
to return BFD interval timers to their configured values. The clear bfd adaptation command is hitless, meaning that the command
does not affect traffic flow on the routing device.
You must specify the minimum transmit and minimum receive intervals to enable BFD on PIM.
To enable failure detection:
Enabling Dedicated and Real-Time BFD on SRX Series Firewalls
By default, SRX Series Firewalls operate in centralized BFD mode. They also support distributed BFD, dedicated BFD, and real-time BFD.
Dedicated BFD
Enabling dedicated BFD impacts traffic throughput as one CPU core is removed from data plane processing.
To enable dedicated BFD on the SRX300, SRX320, SRX340, SRX345, SRX380, SRX1500, vSRX, and vSRX3.0 devices:
-
Include the
dedicated-ukern-cpustatement at the[edit chassis]hierarchy level and then commit the configuration.-
[edit] -
user@host# set chassis dedicated-ukern-cpu
user@host# commit
The following warning message to reboot the system displays when you commit the configuration:
warning: Packet processing throughput may be impacted in dedicated-ukernel-cpu mode. warning: A reboot is required for dedicated-ukernel-cpu mode to be enabled. Please use "request system reboot" to reboot the system. commit complete
-
-
Reboot the device to enable the configuration:
-
user@host> request system reboot
-
-
Verify that dedicated BFD is enabled.
user@host> show chassis dedicated-ukern-cpu
Dedicated Ukern CPU Status: Enabled
Real-Time BFD
Enabling real-time BFD does not impact data plane performance. Higher priority is given to the Packet Forwarding Engine process handling BFD in distributed mode. This is suitable for scenarios where less than half of the maximum number of BFD sessions are being used. See this list for the maximum number of BFD sessions supported per SRX device.
For more information about BFD in distributed mode, see Understanding How BFD Detects Network Failures.
To enable real-time BFD on SRX300, SRX320, SRX340, and SRX345 devices:
-
Include the
realtime-ukern-threadstatement at the[edit chassis]hierarchy level and then commit the configuration.-
[edit]
-
user@host# set chassis realtime-ukern-thread
user@host# commit
The following warning message to reboot the system displays when you commit the configuration:
WARNING: realtime-ukern-thread is enable. Please use the command request system reboot.
-
-
Reboot the device to enable the configuration:
-
user@host> request system reboot
-
-
Verify that real-time BFD is enabled.
user@host> show chassis realtime-ukern-thread
realtime Ukern thread Status: Enabled
BFD Support By SRX Platform
SRX Series Firewalls support the following maximum number of BFD sessions:
-
Up to four sessions on SRX300 and SRX320 devices.
-
Up to 50 sessions on SRX340, SRX345, and SRX380 devices.
-
Up to 120 sessions on SRX1500 devices.
On all SRX Series Firewalls, high CPU utilization triggered for reasons such as CPU intensive commands and SNMP walks causes the BFD protocol to flap while processing large BGP updates. (Platform support depends on the Junos OS release in your installation.)
SRX Series Firewalls operating in chassis cluster mode support only BFD centralized mode.
The table below shows the BFD modes supported on each SRX Series Firewall.
|
SRX Series Firewall |
Centralized BFD Mode |
Distributed BFD |
Real-Time BFD |
Dedicated Core |
|---|---|---|---|---|
|
SRX300 |
Default |
Configuration |
Configuration (Optional) |
Not supported |
|
SRX320 |
Default |
Configuration |
Configuration (Optional) |
Not supported |
|
SRX340 |
Default |
Configuration |
Configuration |
Configuration (Optional) |
|
SRX345 |
Default |
Configuration |
Configuration |
Configuration (Optional) |
|
SRX380 |
Default |
Configuration |
Configuration |
Configuration (Optional) |
| SRX1500 | BFD failure detection time >= 500 ms and dedicated mode is not enabled | BFD failure detection time < 500 ms and dedicated mode is not enabled | Not supported | Configuration |
| SRX4100 | BFD failure detection time >= 500 ms | BFD failure detection time < 500 ms | Not supported | Not supported |
| SRX4200 | BFD failure detection time >= 500 ms | BFD failure detection time < 500 ms | Not supported | Not supported |
| SRX4600 | BFD failure detection time >= 500 ms | BFD failure detection time < 500 ms | Not supported | Not supported |
|
SRX5000 line of devices with SPC2 card |
Default |
Not supported |
Not supported |
Not supported |
|
SRX5000 line of devices with SPC3 card |
BFD failure detection time >= 500 ms |
BFD failure detection time < 500 ms |
Not supported |
Not supported |
|
vSRX 3.0 |
BFD failure detection time > 500ms |
BFD failure detection time <= 500ms |
Not supported |
Configuration |