TALK ALG
The TALK ALG is a visual communication program used for interactive communication between two users. The TALK protocol uses UDP port 517 and port 518 for control channel connections. The talk program consists of a server and a client. The server handles client notifications and helps to establish talk sessions. There are two types of talk servers: ntalk and talkd. The TALK ALG processes packets of both ntalk and talkd formats. It also performs NAT and gate opening as necessary.
Understanding the TALK ALG
The TALK ALG is a visual communication program used for interactive communication between two users. The TALK ALG processes TALK packets, performs Network Address Translation (NAT), and opens two gates (TCP and UDP) on the receiver side. One gate is used for the next LOOKUP packet. The other gate is used for make a connection from a client to a server and to initiate communication between a client and a server located on opposite sides of a Juniper Networks device.
There are two types of TALK servers: ntalkd and talkd.
The TALK ALG processes both ntalk and talkd packets. The TALK ALG uses port UDP517 and port UDP518 to establish a connection between a client and a server.
Example: Configuring the TALK ALG
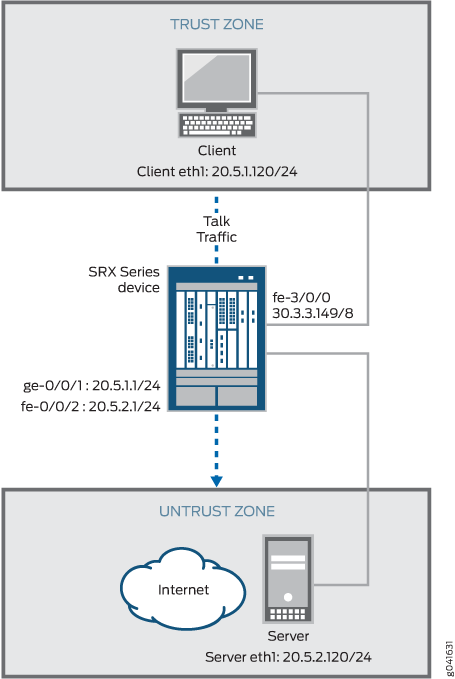
This example show how to configure the TALK ALG in route or NAT mode, allow the TALK traffic to pass through a device, and initiate communication between a client and a server located on opposite sides of a Juniper Networks device.
Requirements
This example uses the following hardware and software components:
-
An SRX Series Firewall
-
Two PCs (client and server)
Before you begin:
-
Understand the concepts behind ALGs. See ALG Overview.
-
Understand the basics of TALK ALG. See Understanding the TALK ALG.
Overview
In this example, first you configure network interfaces on the device, create security zones and assign interfaces to the zones, and configure a policy to allow TALK traffic to go through an SRX Series Firewall.
Then you create a static NAT rule set rs1 with a rule r1 to match the destination address 40.5.2.120/32, and you create a static NAT prefix with address 20.5.2.120/32.
Next you create a source NAT pool src-p1 with a source rule set src-rs1 to translate packets from zone trust to zone untrust. For matching packets, the source address is translated to an IP address in the src-p1 pool.
Then you create a destination NAT pool des-p1 with a destination rule set des-rs1 to translate packets from zone trust to destination address 40.5.2.121/32. For matching packets, the destination address is translated to an IP address in the des-p1 pool. Finally, you configure TALK ALG trace options.
Configuration
To configure the TALK ALG, perform these tasks:
- Configuring a Route Mode
- Configuring a Static NAT Rule Set
- Configuring a Source NAT Pool and Rule Set
- Configuring a Destination NAT Pool and Rule Set
- Configuring TALK ALG trace options
Configuring a Route Mode
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/1 unit 0 family inet address 20.5.1.1/24 set interfaces fe-0/0/2 unit 0 family inet address 20.5.2.1/24 set security zones security-zone trust interfaces ge-0/0/1 host-inbound-traffic system-services all set security zones security-zone trust interfaces ge-0/0/1 host-inbound-traffic protocols all set security zones security-zone untrust interfaces fe-0/0/2 host-inbound-traffic system-services all set security zones security-zone untrust interfaces fe-0/0/2 host-inbound-traffic protocols all set security policies from-zone trust to-zone untrust policy talk match source-address any set security policies from-zone trust to-zone untrust policy talk match destination-address any set security policies from-zone trust to-zone untrust policy talk match application junos-ntalk set security policies from-zone trust to-zone untrust policy talk then permit
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure route mode:
-
Configure interfaces.
[edit interfaces] user@host#set ge-0/0/1 unit 0 family inet address 20.5.1.1/24 user@host#set fe-0/0/2 unit 0 family inet address 20.5.2.1/24
-
Configure zones and assign interfaces to the zones.
[edit security zones security-zone trust] user@host#set interfaces ge-0/0/1 host-inbound-traffic system-services all user@host#set interfaces ge-0/0/1 host-inbound-traffic protocols all [edit security zones security-zone untrust] user@host#set interfaces fe-0/0/2 host-inbound-traffic system-services all user@host#set interfaces fe-0/0/2 host-inbound-traffic protocols all
-
Configure a TALK policy that allows TALK traffic from the trust zone to the untrust zone.
[edit security policies from-zone untrust to-zone trust] user@host#set policy talk match source-address any user@host#set policy talk match destination-address any user@host#set policy talk match application junos-ntalk user@host#set policy talk then permit
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show security zones, and show security policies commands. If the output does
not display the intended configuration, repeat the configuration instructions
in this example to correct it.
For brevity, this show output includes only the configuration
that is relevant to this example. Any other configuration on the system
has been replaced with ellipses (...).
[edit]
user@host# show interfaces
...
ge-0/0/1 {
unit 0 {
family inet {
address 20.5.1.1/24;
}
}
}
...
fe-0/0/2 {
unit 0 {
family inet {
address 20.5.2.1/24;
}
}
}[edit]
user@host# show security zones
security-zone trust {
....
interfaces {
ge-0/0/1.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}
...
security-zone untrust {
interfaces {
fe-0/0/2.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}[edit]
user@host# show security policies
from-zone trust to-zone untrust {
policy talk {
match {
source-address any;
destination-address any;
application junos-ntalk;
}
then {
permit;
}
}
}If you are done configuring the device, enter commit from configuration mode.
Configuring a Static NAT Rule Set
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat static rule-set rs1 from zone trust set security nat static rule-set rs1 rule r1 match destination-address 40.5.2.120/32 set security nat static rule-set rs1 rule r1 then static-nat prefix 20.5.2.120/32
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a static NAT rule set:
-
Create a static NAT rule set.
[edit security nat static rule-set rs1] user@host#set from zone trust
-
Define the rule to match with the destination address.
[edit security nat static rule-set rs1] user@host# set rule r1 match destination-address 40.5.2.120/32
-
Define the static NAT prefix for the device.
[edit security nat static rule-set rs1] user@host# set rule r1 then static-nat prefix 20.5.2.120/32
Results
From configuration mode, confirm your configuration
by entering the show security nat command. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security nat
static {
rule-set rs1 {
from zone trust;
rule r1 {
match {
destination-address 40.5.2.120/32
}
then {
static-nat {
prefix {
20.5.2.120/32;
}
}
}
}
}
}If you are done configuring the device, enter commit from configuration mode.
Configuring a Source NAT Pool and Rule Set
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat source pool src-p1 address 40.5.1.120/32 set security nat source rule-set src-rs1 from zone trust set security nat source rule-set src-rs1 to zone untrust set security nat source rule-set src-rs1 rule src-r1 match source-address 20.5.1.120/32 set security nat source rule-set src-rs1 rule src-r1 match destination-address 20.5.2.120/32 set security nat source rule-set src-rs1 rule src-r1 then source-nat pool src-p1
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a source NAT pool and rule set:
-
Create a source NAT pool.
[edit security nat source] user@host#set pool src-p1 address 40.5.1.120/32
-
Create a source NAT rule set.
[edit security nat source] user@host# set rule-set src-rs1 from zone trust user@host# set rule-set src-rs1 to zone untrust
-
Configure a rule that matches packets and translates the source address to an address in the source pool.
[edit security nat source] user@host# set rule-set src-rs1 rule src-r1 match source-address 20.5.1.120/32
-
Configure a rule that matches packets and translates the destination address to an address in the source pool.
[edit security nat source] user@host# set rule-set src-rs1 rule src-r1 match destination-address 20.5.2.120/32
-
Configure a source NAT pool in the rule.
[edit security nat source] user@host# set rule-set src-rs1 rule src-r1 then source-nat pool src-p1
Results
From configuration mode, confirm your configuration
by entering the show security nat command. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security nat
source {
pool src-p1 {
address {
40.5.1.120/32;
}
}
rule-set src-rs1 {
from zone trust;
to zone untrust;
rule src-r1 {
match {
source-address 20.5.1.120/32;
destination-address 20.5.2.120/32;
}
then {
source-nat {
pool {
src-p1;
}
}
}
}
}
}If you are done configuring the device, enter commit from configuration mode.
Configuring a Destination NAT Pool and Rule Set
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat destination pool des-p1 address 20.5.2.120/32 set security nat destination rule-set des-rs1 from zone trust set security nat destination rule-set des-rs1 rule des-r1 match source-address 20.5.1.120/32 set security nat destination rule-set des-rs1 rule des-r1 match destination-address 40.5.2.120/32 set security nat destination rule-set des-rs1 rule des-r1 then destination-nat pool des-p1
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a destination NAT pool and rule set:
-
Create a destination NAT pool.
[edit security nat destination] user@host#set pool des-p1 address 20.5.2.120/32
-
Create a destination NAT rule set.
[edit security nat destination] user@host# set rule-set des-rs1 from zone trust
-
Configure a rule that matches packets and translates the source address to the address in the pool.
[edit security nat destination] user@host# set rule-set des-rs1 rule des-r1 match source-address 20.5.1.120/32
-
Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination] user@host# set rule-set des-rs1 rule des-r1 match destination-address 40.5.2.120/32
-
Configure a source NAT pool in the rule.
[edit security nat destination] user@host# set rule-set des-rs1 rule des-r1 then destination-nat pool des-p1
Results
From configuration mode, confirm your configuration
by entering the show security nat command. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security nat
destination {
pool des-p1 {
address {
20.5.2.120/32;
}
}
rule-set des-rs1 {
from zone trust;
rule des-r1 {
match {
source-address 20.5.1.120/32;
destination-address 40.5.2.120/32;
}
then {
destination-nat {
pool {
des-p1;
}
}
}
}
}If you are done configuring the device, enter commit from configuration mode.
Configuring TALK ALG trace options
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security alg talk traceoptions flag all set security alg traceoptions file trace set security alg traceoptions file size 1g set security alg traceoptions level verbose
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure TALK ALG trace options:
-
Enable TALK ALG trace otpions.
[edit security alg] user@host#set talk traceoptions flag all
-
Configure the filename to receive output from the tracing operation.
[edit security alg] user@host#set traceoptions file trace
-
Specify the maximum trace file size.
[edit security alg] user@host#set traceoptions file size 1g
-
Specify the level of tracing output.
[edit security alg] user@host#set traceoptions level verbose
Results
From configuration mode, confirm your configuration
by entering the show security alg command. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security alg
traceoptions {
file trace size 1g;
level verbose;
}
talk traceoptions flag all;If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
- Verifying the TALK ALG Control Session
- Verifying the TALK Flow Gate Information
- Verifying TALK ALG
- Verifying the TALK Resource Manager Group
- Verifying the TALK Resource Information
Verifying the TALK ALG Control Session
Purpose
Verify that the TALK control session is created and all the TALK control and data sessions are created.
Action
From operational mode, enter the show security
flow session command.
user@host>show security flow session ession ID: 128570, Policy name: p11/4, Timeout: 56, Valid Resource information : TALK ALG, 2, 0 In: 5.1.1.200/1105 --> 6.1.1.200/518;udp, If: ge-0/0/1.0, Pkts: 3, Bytes: 336 Out: 6.1.1.200/518 --> 5.1.1.200/1105;udp, If: ge-0/0/2.0, Pkts: 3, Bytes: 156 Session ID: 128617, Policy name: p11/4, Timeout: 1796, Valid Resource information : TALK ALG, 2, 2 In: 6.1.1.200/42224 --> 5.1.1.200/518;udp, If: ge-0/0/2.0, Pkts: 1, Bytes: 112 Out: 5.1.1.200/518 --> 6.1.1.200/42224;udp, If: ge-0/0/1.0, Pkts: 1, Bytes: 52 Session ID: 128618, Policy name: p11/4, Timeout: 1796, Valid Resource information : TALK ALG, 2, 3 In: 6.1.1.200/51430 --> 5.1.1.200/32905;tcp, If: ge-0/0/2.0, Pkts: 4, Bytes: 219 Out: 5.1.1.200/32905 --> 6.1.1.200/51430;tcp, If: ge-0/0/1.0, Pkts: 3, Bytes: 167
Meaning
-
Session ID—Number that identifies the session. Use this ID to get more information about the session such as policy name or number of packets in and out.
-
Policy name—Policy name that permitted the traffic.
-
In—Incoming flow (source and destination IP addresses with their respective source and destination port numbers, session is TCP, and the source interface for this session is ge-0/0/1.0).
-
Out—Reverse flow (source and destination IP addresses with their respective source and destination port numbers, session is TCP, and destination interface for this session is fe-0/0/2.0).
Verifying the TALK Flow Gate Information
Purpose
Verify that the gates are opened for TCP data channel and reverse UDP reply.
Action
From operational mode, enter the show security
flow gate command.
user@host>show security flow gate Hole: 6.1.1.200-6.1.1.200/0-0->5.1.1.200-5.1.1.200/518-518 Translated: 0.0.0.0/0->0.0.0.0/0 Protocol: udp Application: TALK ALG/65 Age: 110 seconds Flags: 0x0080 Zone: untrust Reference count: 1 Resource: 11-2-2 Hole: 6.1.1.200-6.1.1.200/0-0->5.1.1.200-5.1.1.200/32905-32905 Translated: 0.0.0.0/0->0.0.0.0/0 Protocol: tcp Application: TALK ALG/65 Age: 110 seconds Flags: 0x0080 Zone: untrust Reference count: 1 Resource: 11-2-3
Meaning
-
Hole—Range of flows permitted by the pinhole.
-
Translated—Tuples used to create the session if it matches the pinhole (source and destination IP addresses with their respective source and destination port numbers).
-
Protocol—Application protocol, such as UDP or TCP.
-
Application—Name of the application.
-
Age—Idle timeout for the pinhole.
-
Flags— Internal debug flags for the pinhole.
-
Zone—Security zone such as from zone and to zone.
-
Reference count—Number of resource manager references to the pinhole.
-
Resource—Resource manager information about the pinhole.
Verifying TALK ALG
Purpose
Verify that the TALK ALG is enabled.
Action
From operational mode, enter the show security
alg status command.
user@host>show security alg status ALG Status : PPTP : Enabled RSH : Disabled RTSP : Enabled SCCP : Enabled SIP : Enabled TALK : Enabled TFTP : Enabled IKE-ESP : Disabled
Meaning
The output shows the TALK ALG status as follows:
-
Enabled—Shows the TALK ALG is enabled.
-
Disabled—Shows the TALK ALG is disabled.
Verifying the TALK Resource Manager Group
Purpose
Verify the total number of resource manager groups and active groups that are used by the TALK ALG.
Action
From operational mode, enter the show security
resource-manager group active command.
user@host>show security resource-manager group active
Group ID 2: Application - TALK ALG
Total groups 3276, active groups 1Verifying the TALK Resource Information
Purpose
Verify the total number of resources and active resources that are used by the TALK ALG.
Action
From operational mode, enter the show security
resource-manager resource active command.
user@host>show security resource-manager resource active Resource ID 3: Group ID - 2, Application - TALK ALG Resource ID 2: Group ID - 2, Application - TALK ALG Total Resources 6015, active resources 2