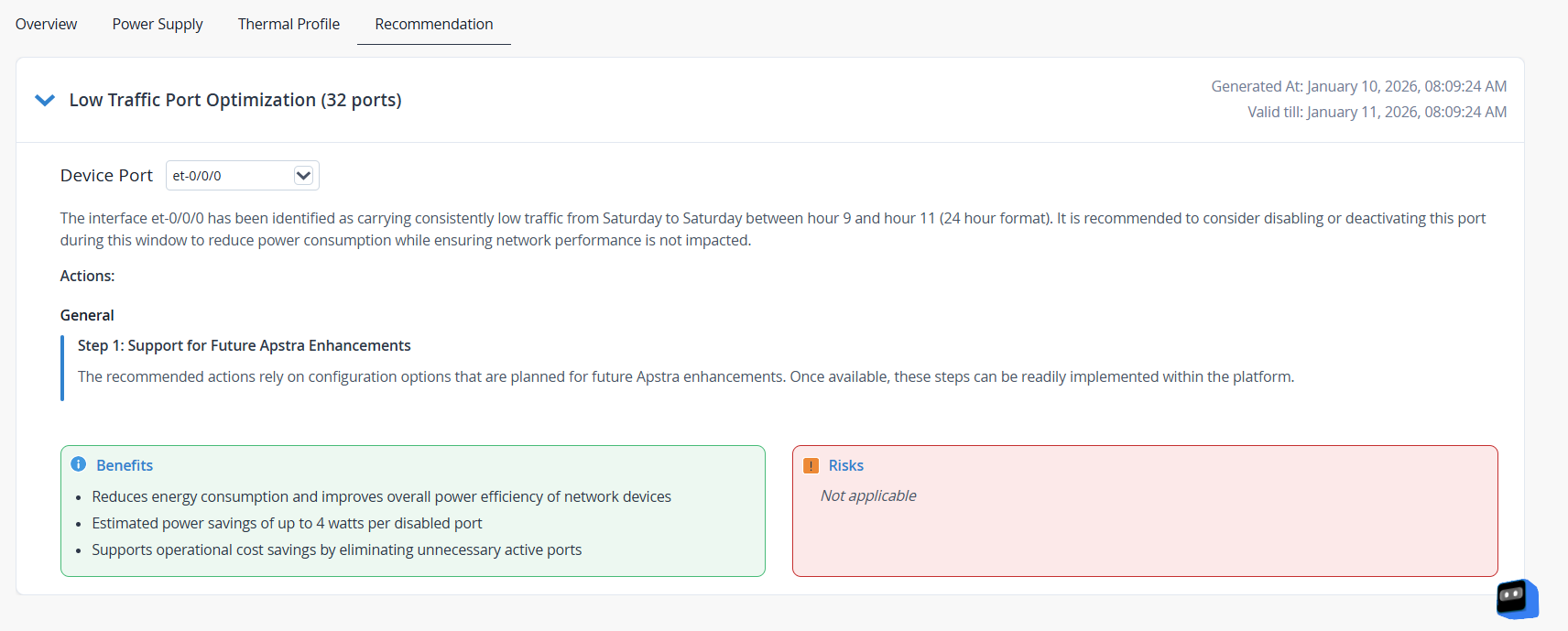
Optimize Low Traffic Ports Based on Historical Traffic Patterns
This topic describes how to reduce device-level energy consumption by disabling ports that consistently carry low or negligible traffic during specific time windows, based on historical usage patterns.
Network traffic often exhibits predictable patterns over time. Some ports consistently carry low or negligible traffic during specific off-peak windows, even though they remain operational. This can be because certain components stay powered on regardless of traffic load. These idle ports continue to consume energy.
The Low Traffic Port Optimization recommendation identifies such ports by analyzing several days of historical per-port traffic telemetry. When the system detects a stable pattern of repeated low utilization during defined time windows, it marks the ports as a safe candidate for temporary shutdown during those windows.
Disabling these ports helps reduce the device’s baseline energy consumption without affecting workload performance.
By aligning each port’s operational state with its actual traffic demand, this recommendation helps make the device’s power usage more proportional to the network’s utilization patterns, improve energy efficiency, and lower operational cost.
A port is included in the Low Traffic Port Optimization recommendation when:
- It consistently operates below the configured low-traffic utilization threshold during
the same hours across multiple consecutive days.Note:
The low-traffic utilization threshold used for this analysis can be configured at the organization and site levels. See, Configure Port Threshold for the Organization and Configure Port Threshold for a Site.
- The port is not part of a critical role (uplink, fabric link, control-plane link).
- Disabling the port during the low-traffic window is operationally safe.
- Sufficient historical telemetry exists to establish a predictable pattern.
The Low Traffic Port Optimization recommendation provides actionable guidance, such as the list of eligible ports, the observed low-traffic windows, and the relevant configlet-based actions required to safely disable ports and reduce idle power consumption.
The recommendation service executes once per day. Each execution uses historical per-port traffic telemetry and the configuration data available at the time of execution. The Recommendation tab displays the most recently generated results for the device.
Changes to port states, traffic patterns, or threshold configurations that occur outside the current execution window are reflected in recommendations after the next execution cycle.
Use the Per-Port Peak / Off-Peak Traffic Patterns heatmap on the Device-Level Energy dashboard to view traffic patterns for all ports.
The Recommendation tab will appear empty, if no safe or meaningful recommendations or power saving actions were identified based on the latest device telemetry.
To view underutilized ports and review the recommended actions: