Superflows
JSA analyzes individual flows to look for indicators that common attack vectors are being used on your network. When the number of flows that match the criteria reaches a specified number, JSA groups the individual flows into a superflow. Each superflow counts as only one flow against the flows per minute (FPM) license, regardless of how many flow records are bundled within it.
You can configure the flow threshold to control the number of unique flows that must match the criteria before a superflow is created. Given a threshold of 100, the first 99 flows are sent as normal flow records. The 100th flow and subsequent matching flows are included in the superflow record. JSA continues to report on the superflow every minute, until one full interval passes with no matching traffic. Because a superflow is kept alive even if only one flow record matches, some superflows might appear to be small.
If you do not want JSA to create superflows, in the Flow Processor configuration settings, change the Create Super Flows setting to No.
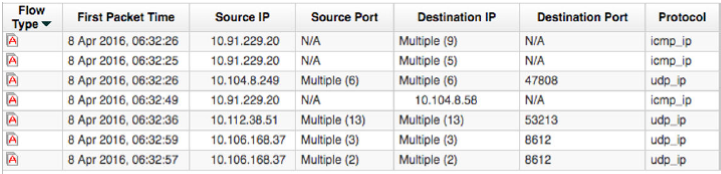
Superflow Type A: Network Scan
A network scan attempts to discover all of the active hosts on your network and map the hosts to an IP address.
JSA looks for flows where one host sends data to many hosts, and flags this type of activity as a Type A superflow. This unidirectional flow is an aggregate of all of the flows that have the same source IP with different destination IPs, but the following parameters are the same:
Protocol
Source bytes-to-packets ratio
Source IP address
Destination port (TCP and UDP flows only)
TCP flags (TCP flows only)
ICMP type and code (ICMP flows only)
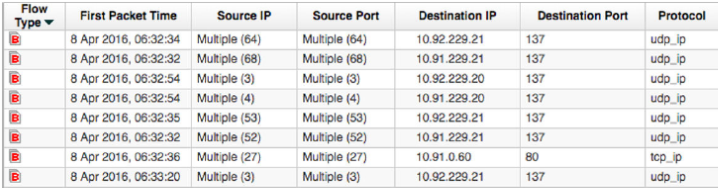
Superflow Type B: Distributed Denial of Service (DDoS)
A DDoS attack occurs when multiple systems flood the bandwidth or resources of a targeted system.
JSA looks for flows where many hosts send data to one destination host, and flags this activity as a Type B superflow. This unidirectional flow is an aggregate of all of the flows that have different source IPs with a single destination IP, but the following parameters are the same:
Protocol
Source bytes-to-packets ratio
Destination IP address
Destination port (TCP and UDP flows only)
TCP flags (TCP flows only)
ICMP type and code (ICMP flows only)
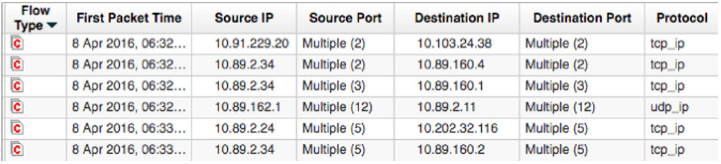
Superflow Type C: Port Scan
A port scan attempts to identify the ports that are in use by a specific host on your network.
JSA looks for flows that have one source IP and one destination IP, but many ports. This unidirectional flow is an aggregate of all non-ICMP flows that have different source or destination ports, but the following parameters are the same:
Protocol
Source IP address
Destination IP address
Source bytes-to-packets ratio
TCP flags (TCP flows only)