Flow Sources
JSA can receive flows from many different types of flow sources. The flow sources are classified as either internal or external.
Internal Flow Sources
Internal flow sources collect raw packets from either a network tap device or a span or mirror port that is connected to a network interface card. These sources provide raw packet data as it appears on the network, and sends it to a monitoring port on a JSA Flow Processor, which converts the packet data into flow records.
Internal flow sources can be multithreaded. JSA does not keep the entire packet payload. Instead, it captures only some of the packets from the beginning of the communication. This snapshot is referred to as the payload or content capture.
External Flow Sources
JSA also supports external flow sources, such as routers that send common network monitoring protocols, such as NetFlow, IPFIX, sFlow J-Flow, and Packeteer data.
These external flow sources can provide a different level of visibility than internal flow sources. For example, NetFlow records can provide both the router interface that the packets crossed, as well as the ASN record numbers of the originating network. When using IPFIX, additional fields that are not parsed into normalized fields can be placed into the payload as name value pairs, which can then be used as custom properties.
External sources do not require as much CPU utilization to process so you can send them directly to a Flow Processor. In this configuration, you can have a dedicated Flow Processor, both receiving and creating flow data.
NetFlow
NetFlow is a proprietary accounting technology that is developed by Cisco Systems. NetFlow monitors traffic flows through a switch or router, and interprets the client, server, protocol, and port that is used. It also counts the number of bytes and packets, and sends that data to a NetFlow collector.
The process of sending data from NetFlow is often referred to as a NetFlow Data Export (NDE).
JSA accepts NetFlow Data Exports (NDE) so that it functions as a NetFlow collector. JSA supports NetFlow versions 1, 5, 7, and 9.
While NetFlow expands the amount of the network that is monitored, it uses a connection-less protocol (UDP) to deliver NDEs. After an NDE is sent from a switch or router, the NetFlow record is purged. UDP doesn't guarantee the delivery of data. As a result, inaccurate presentations of both traffic volumes and bidirectional flows, and reduced alerting capabilities, might result with a NetFlow flow source.
For more information about NetFlow, see the Cisco web site.
NetFlow Flow Source Configuration
When you configure an external flow source for NetFlow, you must do the following tasks:
-
Make sure that the appropriate firewall rules are configured.
If you change your External Flow Source Monitoring Port parameter in the Flow Processor configuration, you must also update your firewall access configuration.
-
Make sure that the appropriate ports are configured for your Flow Processor.
For more information, see Configuring a Flow Processor.
NetFlow Flow Source Template
Juniper suggests that, at minimum, the following fields are included in the NetFlow flow source template:
-
FIRST_SWITCHED
-
LAST_SWITCHED
-
PROTOCOL
-
IPV4_SRC_ADDR
-
IPV4_DST_ADDR
-
L4_SRC_PORT
-
L4_DST_PORT
-
IN_BYTES or OUT_BYTES
-
IN_PKTS or OUT_PKTS
-
TCP_FLAGS (TCP flows only)
Supported Fields
The following lists show some of the types of fields that are supported for NetFlow flow sources.
VLAN fields
The following VLAN fields are supported for NetFlow:
-
vlanId (IANA Element ID 58)
-
postVlanId (IANA Element ID 59)
-
dot1qVlanId (IANA Element ID 243)
-
dot1qPriority (IANA Element ID 244)
-
dot1qCustomerVlanId (IANA Element ID 245)
-
dot1qCustomerPriority (IANA Element ID 246)
-
postDot1qVlanId (IANA Element ID 254)
-
postDotqCustomerVlanId (IANA Element ID 255)
-
dot1qDEI (IANA Element ID 388)
-
dot1qCustomerDEI (IANA Element ID 389)
MAC Address Fields
The following MAC address fields are supported for NetFlow:
-
sourceMacAddress (IANA Element ID 56)
-
postDestinationMacAddress (IANA Element ID 57)
-
DestinationMacAddress (IANA Element ID 80)
-
postSourceMacAddress (IANA Element ID 81)
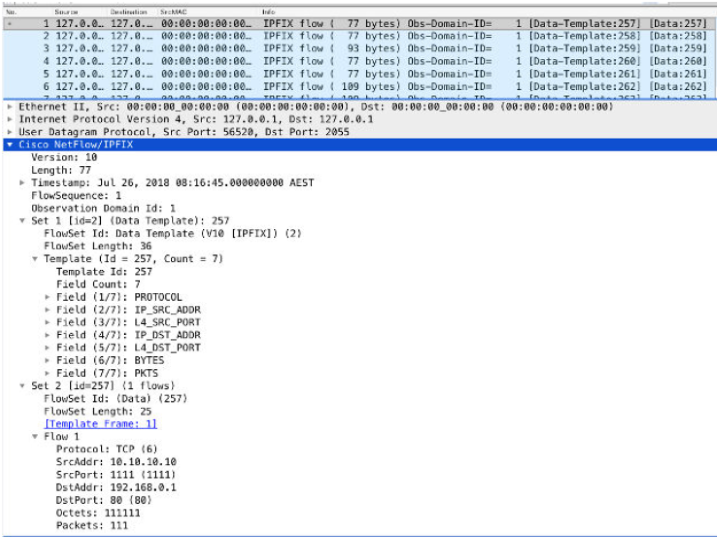
IPFIX
Internet Protocol Flow Information Export (IPFIX) is an accounting technology that monitors traffic flows through a switch or router. It interprets the traffic to determine the client, server, protocol, and port that is used. It also counts the number of bytes and packets, and sends that data to an IPFIX collector.
The process of sending IPFIX data is often referred to as a NetFlow Data Export (NDE), but IPFIX provides more flow information and deeper insight than NetFlow v9.
JSA accepts NDEs so that it functions as an IPFIX collector. IPFIX uses User Datagram Protocol (UDP) to deliver NDEs. After an NDE is sent from the IPFIX forwarding device, the IPFIX record might be purged.
- IPFIX Flow Source Configuration
- IPFIX Flow Source Template
- Supported Fields
- MAC Address Fields
- Network Address Translation (NAT) fields
- MPLS Fields
IPFIX Flow Source Configuration
When you configure an external flow source for IPFIX, you must do the following tasks:
-
Add a NetFlow flow source.
Note:Your JSA might include a default NetFlow flow source. If it does, JSA can use the default NetFlow flow source to process the IPFIX flows.
To confirm that your system includes a default NetFlow flow source, on the Admin tab, select Flow Sources. If default_Netflow is listed in the flow source list, IPFIX is already configured.
-
Ensure that the appropriate firewall rules are configured.
If you change your External Flow Source Monitoring Port parameter in the Flow Processor configuration, you must also update your firewall access configuration.
-
Ensure that the appropriate ports are configured for your Flow Processor.
For more information, see Configuring a Flow Processor.
IPFIX Flow Source Template
Ensure that the IPFIX template from the IPFIX source includes the following IANA-listed Information Elements:
-
protocolIdentifier (4)
-
sourceIPv4Address (8)
-
destinationIPv4Address (12)
-
sourceTransportPort (7)
-
destinationTransportPort (11)
-
octetDeltaCount (1) or postOctetDeltaCount (23)
-
packetDeltaCount (2) or postPacketDeltaCount (24)
-
tcpControlBits (6) (TCP flows only).
-
flowStartSeconds (150) or flowStartMilliseconds (152) or flowStartDeltaMicroseconds (158)
-
flowEndSeconds (151) or flowEndMilliseconds (153) or flowEndDeltaMicroseconds (159)
Supported Fields
The following lists show some of the types of fields that are supported for IPFIX flow sources.
To add support for additional IPFIX fields that are not shown by JSA, you can use the /api/ariel/taggedfields API to create a new tagged field.
VLAN fields
The following VLAN fields are supported for IPFIX:
-
vlanId (IANA Element ID 58)
-
postVlanId (IANA Element ID 59)
-
dot1qVlanId (IANA Element ID 243)
-
dot1qPriority (IANA Element ID 244)
-
dot1qCustomerVlanId (IANA Element ID 245)
-
dot1qCustomerPriority (IANA Element ID 246)
-
postDot1qVlanId (IANA Element ID 254)
-
postDot1qCustomerVlanId (IANA Element ID 255)
-
dot1qDEI (IANA Element ID 388)
-
dot1qCustomerDEI (IANA Element ID 389)
MAC Address Fields
The following MAC address fields are supported for IPFIX:
-
sourceMacAddress (IANA Element ID 56)
-
postDestinationMacAddress (IANA Element ID 57)
-
DestinationMacAddress (IANA Element ID 80)
-
postSourceMacAddress (IANA Element ID 81)
Network Address Translation (NAT) fields
The following fields are supported for Network Address Translation (NAT) and Network Address Port Translation (NAPT):
-
postNATSourceIPv4Address (IANA Element ID 225)
-
postNATDestinationIPv4Address (IANA Element ID 226)
-
postNAPTSourceTransportPort (IANA Element ID 227)
-
postNAPTDestinationTransportPort (IANA Element ID 228)
MPLS Fields
The following MPLS fields are supported for IPFIX:
-
mplsTopLabelType (IANA Element 46)
-
mplsTopLabelIPv4Address (IANA Element 47)
-
mplsTopLabelStackSection (IANA Element 70)
-
mplsLabelStackSection2 (IANA Element 71)
-
mplsLabelStackSection3 (IANA Element 72)
-
mplsLabelStackSection4 (IANA Element 73)
-
mplsLabelStackSection5 (IANA Element 74)
-
mplsLabelStackSection6 (IANA Element 75)
-
mplsLabelStackSection7 (IANA Element 76)
-
mplsLabelStackSection8 (IANA Element 77)
-
mplsLabelStackSection9 (IANA Element 78)
-
mplsLabelStackSection10 (IANA Element 79)
-
mplsVpnRouteDistinguisher (IANA Element 90)
-
mplsTopLabelPrefixLength (IANA Element 91)
-
mplsTopLabelIPv6Address (IANA Element 140)
-
mplsPayloadLength (IANA Element 194)
-
mplsTopLabelTTL (IANA Element 200)
-
mplsLabelStackLength (IANA Element 201)
-
mplsLabelStackDepth (IANA Element 202)
-
mplsTopLabelExp (IANA Element 203)
-
postMplsTopLabelExp (IANA Element 237)
-
pseudoWireType (IANA Element 250)
-
pseudoWireControlWord (IANA Element 251)
-
mplsLabelStackSection (IANA Element 316)
-
mplsPayloadPacketSection (IANA Element 317 )
-
sectionOffset (IANA Element 409)
-
sectionExportedOctets (IANA Element 410)
sFlow
sFlow is a multi-vendor and user standard for sampling technology that provides continuous monitoring of application-level traffic flows on all interfaces simultaneously.
An sFlow combines interface counters and flow samples into sFlow datagrams that are sent across the network to an sFlow collector. sFlow traffic is based on sampled data and, therefore, might not represent all network traffic.
JSA supports flow sources for sFlow versions 2, 4, and 5.
sFlow uses a connection-less protocol (UDP). When data is sent from a switch or router, the sFlow record is purged. UDP doesn't guarantee delivery of the data. As such, inaccurate presentations of both traffic volumes and bidirectional flows, and reduced alerting capabilities, might result when using an sFlow flow source.
For more information, see the sFlow website.
sFlow Flow Source Configuration
When you configure an external flow source for sFlow, you must do the following tasks:
Ensure that the appropriate firewall rules are configured.
Ensure that the appropriate ports are configured.
For more information, see Configuring a Flow Processor.
J-Flow
J-Flow is a proprietary accounting technology used by Juniper Networks that allows you to collect IP traffic flow statistics.
J-Flow enables you to export data to a UDP port on a J-Flow collector. You can also enable J-Flow on a router or network interface to collect network statistics for specific locations on your network.
J-Flow uses a connection-less protocol (UDP). When data is sent from a switch or router, the J-Flow record is purged. UDP doesn't guarantee delivery of the data. As such, inaccurate presentations of both traffic volumes and bidirectional flows, and reduced alerting capabilities, might result when using a J-Flow flow source. J-Flow traffic is based on sampled data and, therefore, might not represent all network traffic.
For more information about J-Flow, see the Juniper Networks website.
J-Flow Flow Source Configuration
When you configure an external flow source for J-Flow, you must do the following tasks:
Ensure that the appropriate firewall rules are configured.
Ensure that the appropriate ports are configured.
For more information, see Configuring a Flow Processor.
Supported VLAN Fields
The following VLAN fields are supported for J-Flow:
vlanId
postVlanId
dot1qVlanId
dot1qPriority
dot1qCustomerVlanId
dot1qCustomerPriority
dot1qDEI
dot1qCustomerDEI
postDot1qVlanId
postDotqCustomerVlanId
Packeteer
Packeteer devices collect, aggregate, and store network performance data.
After you configure an external flow source for Packeteer, you can send flow information from a Packeteer device to JSA.
Packeteer uses a connection-less protocol (UDP). When data is sent from a switch or router, the Packeteer record is purged. Because UDP doesn't guarantee delivery of the data, inaccurate presentations of both traffic volumes and bidirectional flows, and reduced alerting capabilities might result when using a Packeteer flow source.
Packeteer Flow Source Configuration
To configure Packeteer as an external flow source, you must do the following tasks:
Ensure that the appropriate firewall rules are configured.
Ensure that you configure Packeteer devices to export flow detail records, and configure the Flow Processor as the destination for the data export.
Ensure that the appropriate ports are configured.
Ensure that the class IDs from the Packeteer devices can automatically be detected by the Flow Processor.
For more information, see Configuring a Flow Processor.
Network Interface
JSA can monitor packets that come in on any network interface card that is installed on your system. The network interface card must be installed for JSA to show it in the list of configurable packet-based flow sources.
When you configure the Network Interface flow source, configure only one log source for each Ethernet interface. To filter the network traffic that comes in on the flow source, specify a Berkeley Packet Filter (BPF) in the Filter String field.
After the flow source is configured and the changes are deployed, you can view the network traffic on the Network Activity tab.
You can customize the way that JSA processes the network traffic. For example, you can configure the way that applications are detected, superflow thresholds, flow direction configuration, and network hierarchy. You can also write rules, perform queries, and filter the network traffic.
For more information, see Configuring a Flow Processor.
