Flow Pipeline
Flows that come into JSA go through an in-depth process to extract additional information about the network communication, looking for indicators that a security incident might have occurred.
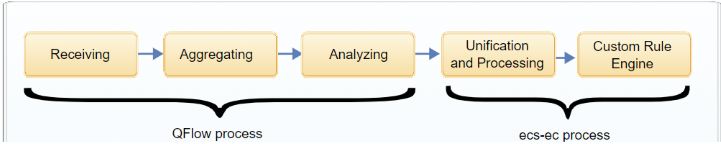
Flow Processor process
The Flow Processor process collects data from a variety of flow sources. It
aggregates the data by parsing and normalizing the data, accruing information over a one
minute period. It then analyzes the flow to extract additional information such as
determining the application and flow direction, and creating superflows before handing
it off to the ecs-ec process.
ecs-ec process
The ecs-ec process further parses the flow record and performs
additional unification and processing, such as deduplication, asymmetric recombination,
licensing, domain tagging, custom flow properties, and flow forwarding. The flow is then
passed to the Custom Rule Engine (CRE) to determine if the flow triggers a rule, which
might indicate that a security incident has occurred.
