Verify Default Branch Connectivity
First, let's verify the default WAN and LAN connectivity on the SRX.
Verify WAN Connectivity
Confirm the DHCP Client on the WAN Interface
Verify that the WAN interface received an IP address from the DHCP service provided by the ISP (ISP). In the default configuration, the ge-0/0/0 interface is part of the untrust zone and is set as a DHCP client.
root@branch_SRX> show dhcp client binding IP address Hardware address Expires State Interface 172.16.1.10 78:4f:9b:26:21:f5 77215 BOUND ge-0/0/0.0
Confirm Internet Connectivity
Confirm Internet access with a successful ping to www.juniper.net.
root@branch_SRX> ping www.juniper.net inet count 2 PING e1824.dscb.akamaiedge.net (104.100.54.237): 56 data bytes 64 bytes from 104.100.54.237: icmp_seq=0 ttl=47 time=7.268 ms 64 bytes from 104.100.54.237: icmp_seq=1 ttl=47 time=9.803 ms --- e1824.dscb.akamaiedge.net ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 7.268/8.536/9.803/1.267 ms
Verify LAN Connectivity
- Confirm LAN DHCP Server
- Display VLANs
- Verify MAC Address Learning
- Confirm LAN Connectivity in the Trust Zone
Verify LAN connectivity. SRX300 Line Default Security Policies summarizes the factory default security zones and their behavior. See SRX300 Line Default Connectivity for details on the physical connectivity and MAC addresses used by the various LAN devices.
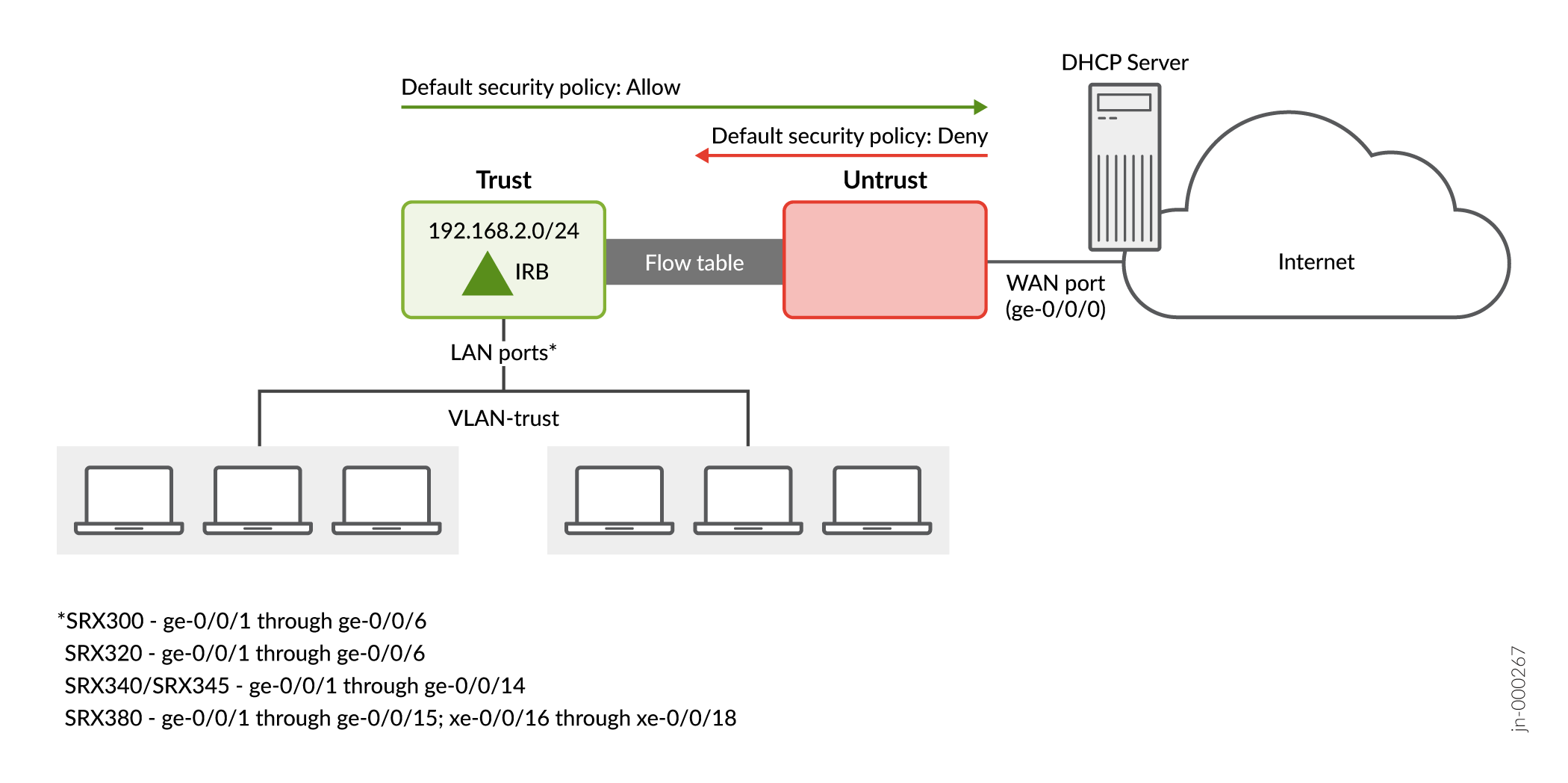
While the port type and count varies between branch SRX models (SRX 300 Series), the factory default configuration results in the same type of connectivity:
- All LAN ports have full Layer 2 connectivity within the trust zone
- Traffic sent from any LAN port is allowed in the untrust zone
- Return traffic from the untrust zone is permitted back to the trust zone
- Traffic that originates in the untrust zone is blocked from the trust zone
Keep these defaults in mind as you continue to verify default connectivity.
Confirm LAN DHCP Server
Verify that the SRX assigns IP addresses to the LAN clients. Recall that in the factory default configuration, a Layer 3 capable Integrated Routing and Bridging (IRB) interface functions as a DCHP server for all LAN ports. Refer to Figure 1 to map the MAC addresses shown in the output to the devices and SRX ports used in our branch office.
root@branch_SRX> show dhcp server binding IP address Session Id Hardware address Expires State Interface 192.168.2.5 3530 08:81:f4:82:a4:5c 70025 BOUND irb.0 192.168.2.8 3529 08:81:f4:8a:eb:51 68662 BOUND irb.0 192.168.2.13 3534 20:4e:71:a6:a7:01 86366 BOUND irb.0 192.168.2.7 3535 d4:20:b0:00:c3:37 86126 BOUND irb.0
The output confirms that the SRX device correctly assigns IP addresses from the default 192.168.2.0/24 address pool to the LAN clients.
Display VLANs
In the factory-default configuration, all LAN ports are in the same VLAN
(vlan-trust) with full (unfiltered) Layer 2 connectivity
for the shared 192.168.2.0/24 IP subnet. Use the show vlans
command to display all VLANs on the device.
root@branch_SRX> show vlans
Routing instance VLAN name Tag Interfaces
default-switch default 1
default-switch vlan-trust 3
ge-0/0/1.0*
ge-0/0/10.0
ge-0/0/11.0
ge-0/0/12.0
ge-0/0/13.0
ge-0/0/14.0
ge-0/0/15.0
ge-0/0/2.0*
ge-0/0/3.0*
ge-0/0/4.0
ge-0/0/5.0
ge-0/0/6.0
ge-0/0/7.0
ge-0/0/8.0
ge-0/0/9.0
xe-0/0/16.0
xe-0/0/17.0
xe-0/0/18.0
The output shows there are two VLANs: the default VLAN, assigned
VLAN ID 1, and the vlan-trust VLAN, assigned VLAN ID 3. In
the factory-default configuration, no interfaces are associated with the default
VLAN. All the LAN ports are associated with the vlan-trust
VLAN. Again, all interfaces assigned to the same VLAN have full connectivity at
Layer 2.
Verify MAC Address Learning
Issue the show ethernet-switching table command to verify MAC
learning in the vlan-trust VLAN.
root@branch_SRX> show ethernet-switching table
MAC flags (S - static MAC, D - dynamic MAC, L - locally learned, P - Persistent static, C - Control MAC
SE - statistics enabled, NM - non configured MAC, R - remote PE MAC, O - ovsdb MAC)
Ethernet switching table : 6 entries, 6 learned
Routing instance : default-switch
Vlan MAC MAC Age Logical NH RTR
name address flags interface Index ID
vlan-trust 08:81:f4:82:a4:5c D - ge-0/0/3.0 0 0
vlan-trust 08:81:f4:8a:eb:51 D - ge-0/0/2.0 0 0
vlan-trust 20:4e:71:a6:a7:01 D - ge-0/0/1.0 0 0
The output confirms the expected MAC address learning for our LAN clients in the vlan-trust VLAN.
In a VLAN, MAC address learning occurs anytime a device sends any type of traffic. The SRX learns based on the source MAC address. This learning builds the Ethernet switching table that is used to forward traffic, based on the destination MAC address. Broadcast, unknown unicast, and multicast (BUM) traffic is flooded to all ports in the VLAN. In our case, the use of DHCP to obtain an IP address is enough to trigger the MAC address learning shown.
Confirm LAN Connectivity in the Trust Zone
To confirm LAN connectivity in the trust zone, simply send a ping between LAN clients. Alternatively, you can send pings from the SRX to each LAN client. For verification, log in to an employee device attached to the SRX ge-0/0/2 interface, and test connectivity to both the IRB interface in the SRX, and to the LAN device attached to the SRX's ge-0/0/1 interface. Use the MAC and IP addresses shown in the preceding command output.
First, confirm the employee device interface parameters. Specifically, the MAC and IP addresses:
root@employee> show interfaces ge-1/0/1
Physical interface: ge-1/0/1, Enabled, Physical link is Up
Interface index: 153, SNMP ifIndex: 522
Link-level type: Ethernet, MTU: 1514, MRU: 1522, LAN-PHY mode, Speed: 1000mbps, BPDU Error: None, Loop Detect PDU Error: None,
. . .
Current address: 08:81:f4:8a:eb:51, Hardware address: 08:81:f4:8a:eb:51
. . .
Logical interface ge-1/0/1.0 (Index 338) (SNMP ifIndex 598)
Flags: Up SNMP-Traps 0x0 Encapsulation: ENET2
Input packets : 1338313
Output packets: 40277
Protocol inet, MTU: 1500
Max nh cache: 75000, New hold nh limit: 75000, Curr nh cnt: 1, Curr new hold cnt: 0, NH drop cnt: 0
Flags: Sendbcast-pkt-to-re
Addresses, Flags: Is-Preferred Is-Primary
Destination: 192.168.2/24, Local: 192.168.2.8, Broadcast: 192.168.2.255
Protocol multiservice, MTU: Unlimited
Flags: Is-Primary
Next, test the expected LAN connectivity with a ping to the SRX's IRB interface and to the LAN device attached to the ge-0/0/1 interface. As shown above, the LAN device on ge-0/0/1 is assigned IP address 192.168.2.13:
root@employee> ping 192.168.2.1 count 2 PING 192.168.2.1 (192.168.2.1): 56 data bytes 64 bytes from 192.168.2.1: icmp_seq=0 ttl=64 time=0.938 ms 64 bytes from 192.168.2.1: icmp_seq=1 ttl=64 time=0.893 ms --- 192.168.2.1 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.893/0.915/0.938/0.023 ms root@employee> ping 192.168.2.13 count 2 PING 192.168.2.13 (192.168.2.13): 56 data bytes 64 bytes from 192.168.2.13: icmp_seq=0 ttl=64 time=2.798 ms 64 bytes from 192.168.2.13: icmp_seq=1 ttl=64 time=1.818 ms --- 192.168.2.13 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.818/2.308/2.798/0.490 ms root@employee> traceroute 192.168.2.13 traceroute to 192.168.2.13 (192.168.2.13), 30 hops max, 40 byte packets 1 192.168.2.13 (192.168.2.13) 1.759 ms 1.991 ms 1.786 ms
The pings are successful which verifies the expected connectivity for the trust VLAN ports. The added traceroute output confirms the shared IP subnet, and resulting direct connectivity, for the LAN stations. This connectivity will change when you later deploy multiple VLANs and IP subnets to secure local branch connectivity.
Verify LAN to WAN Connectivity with Source NAT
Send a ping to an Internet destination from a LAN client. If desired, you can source a ping from the SRX's IRB interface to exercise the same packet flow. The goal is to verify that traffic originating in the trust zone flows to the untrust zone with source NAT . This provides the LAN station with Internet connectivity.
Let's test Internet connectivity from the LAN client attached to the SRX ge-0/0/2 interface by sending a ping to the juniper.net website.
root@employee> ping www.juniper.net count 2 inet
PING e1824.dscb.akamaiedge.net (104.100.54.237): 56 data bytes
64 bytes from 104.100.54.237: icmp_seq=0 ttl=44 time=4.264 ms
64 bytes from 104.100.54.237: icmp_seq=1 ttl=44 time=4.693 ms
--- e1824.dscb.akamaiedge.net ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max/stddev = 4.264/4.479/4.693/0.214 ms
root@employee> show route 104.100.54.237
inet.0: 23 destinations, 23 routes (22 active, 0 holddown, 1 hidden)
+ = Active Route, - = Last Active, * = Both
0.0.0.0/0 *[Access-internal/12] 3w6d 01:45:40, metric 0
> to 192.168.2.1 via ge-1/0/1.0The ping is successful which confirms LAN to WAN connectivity. The output of the
show route command confirms that the LAN station sends the
test traffic to the SRX as its default gateway.
It's important to note that sending a ping from a LAN station to an Internet destination involves packet flow from the trust zone to untrust zone. The SRX is a flow-based device. A security policy is needed to permit flows between zones. As we noted in Figure 1, the factory-default policies allow trust to untrust packet flows.
View the flow session table to confirm that there are active sessions between the LAN clients and the WAN.
root@branch_SRX> show security flow session Session ID: 8590056439, Policy name: trust-to-untrust/5, State: Stand-alone, Timeout: 2, Valid In: 192.168.2.8/28282 --> 104.100.54.237/56711;icmp, Conn Tag: 0x0, If: irb.0, Pkts: 1, Bytes: 84, Out: 104.100.54.237/56711 --> 172.16.1.10/7273;icmp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 1, Bytes: 84, . . .
The output shows that your test traffic successfully created a flow table entry. A second entry for the same flow confirms that the SRX performed source NAT on the traffic (using 172.16.1.10 from its WAN interface), before sending the ping to the destination at 104.100.54.237 (www.juniper.net). This confirms that the traffic is permitted to flow from the trust zone to the untrust zone with source NAT. Your successful ping from a LAN station to www.juniper.net confirms the expected factory-default LAN-WAN connectivity.
Next, we'll show you how to alter the default LAN connectivity to secure the local branch according to your requirements.
