How to Install Contrail Command and Provision Your Contrail Cluster
Use this document to install Contrail Command—the graphical user interface for Contrail Networking—and provision your servers or VMs as nodes in a Contrail cluster. Servers or VMs are provisioned into compute nodes, control nodes, orchestrator nodes, Contrail Insights nodes, Contrail Insights Flows nodes, or service nodes to create your Contrail cluster using this procedure.
Contrail Insights and Contrail Insights Flows were previously named Appformix and Appformix Flows.
When to Use This Document
We strongly recommend Contrail Command as the primary interface for configuring and maintaining Contrail Networking.
You should, therefore, complete the procedures in this document as an initial configuration task in your Contrail Networking environment.
Server Requirements
A Contrail Networking environment can include physical servers or VMs providing server functions, although we highly recommended using physical servers for scalability and availability reasons whenever possible.
Each server in a Contrail environment must have a minimum of:
64 GB memory.
300 GB hard drive.
4 CPU cores.
At least one Ethernet port.
For additional information on server requirements for Contrail Networking, see Server Requirements and Supported Platforms.
Software Requirements
Contrail Command and Contrail Networking
Contrail Command and Contrail Networking are updated simultaneously and always run the same version of Contrail Networking software.
Each Contrail Networking release has software compatibility requirements based on the orchestration platform version, the deployer used to deploy the orchestration platform, the supported server operating system version, and other software requirements.
For a list of supported platforms for all Contrail Networking releases and additional environment-specific software requirements, see Contrail Networking Supported Platforms List.
Contrail Insights and Contrail Insights Flows
Starting in Contrail Release 2005, the Contrail Insights and Contrail Insights Flows images that support a Contrail Networking release are automatically provisioned within Contrail Command. When you download your version of Contrail Command, Contrail Command pulls the Contrail Insights and Contrail Insights Flows images for your Contrail Networking version automatically from within the Juniper Contrail registry. You do not, therefore, need to separately download any individual Contrail Insights software or have awareness of Contrail Insights or Contrail Insights version numbers for your installation.
How to Obtain Contrail Images
The procedures used in this document download the Contrail Command, Contrail Insights, and Contrail Insights Flows software from the Juniper Networks Contrail docker private secure registry at hub.juniper.net. Email mailto:contrail-registry@juniper.net to obtain access credentials to this registry.
You will need to know the Container Tags for your Contrail image to retrieve Contrail images from the Contrail registry. See README Access to Contrail Registry 21XX.
Contrail Networking images are also available at the Contrail Downloads page. Enter Contrail Networking as the product name.
Contrail Insights and Contrail Insights Flows images are also available at the Contrail Insights Download page. Enter Contrail Insights as the product name.
How to Install Contrail Command
Contrail Command is a single pane-of-glass GUI interface for Contrail Networking. For an optimized Contrail Networking experience, we strongly recommend installing Contrail Command before creating your Contrail clusters. Contrail Command is installed using these instructions.
For additional information on Contrail Command, see Understanding Contrail Networking Components.
- Before You Begin
- Preparing Your Contrail Command Server for the Installation
- Installing Contrail Command
Before You Begin
Ensure your Contrail Command server—the server that will host Contrail Command—is a virtual machine (VM) or a physical x86 server that meets these minimum system requirements:
4 vCPUs
32 GB RAM
100 GB disk storage with all user storage in the “/” partition.
If the “/home” partition exists, remove it and increase the “/” partition by the amount of freed storage.
Meets the specifications listed in Server Requirements.
Runs a version of CentOS that supports your version of Contrail Networking.
For a list of CentOS versions that are supported with Contrail Networking and orchestration platform combinations, see Contrail Networking Supported Platforms List.
You can install CentOS with updated packages using the
yum updatecommand.Has access to the Contrail Container registry at hub.juniper.net. This access is needed because the Contrail Command deployer, which includes the Contrail Command docker images, is retrieved from this registry during this installation procedure.
If you do not have access to the Contrail Container registry, email mailto:contrail-registry@juniper.net to obtain access credentials. See README Access to Contrail Registry 21XX for additional information about accessing this registry.
Has an active connection to the Internet.
Includes at least one active IP interface attached to the management network. Contrail Command manages Contrail and orchestrator clusters over a management IP interface.
Obtain the container tag for the release that you are installing. A container tag is necessary to identify the Contrail Command container files in the hub.juniper.net repository that are installed during this procedure.
The container tag for any Contrail Release 21-based image can be found in README Access to Contrail Registry 21XX.
Preparing Your Contrail Command Server for the Installation
To prepare your servers or VMs for the installation:
Installing Contrail Command
To install Contrail Command onto a server:
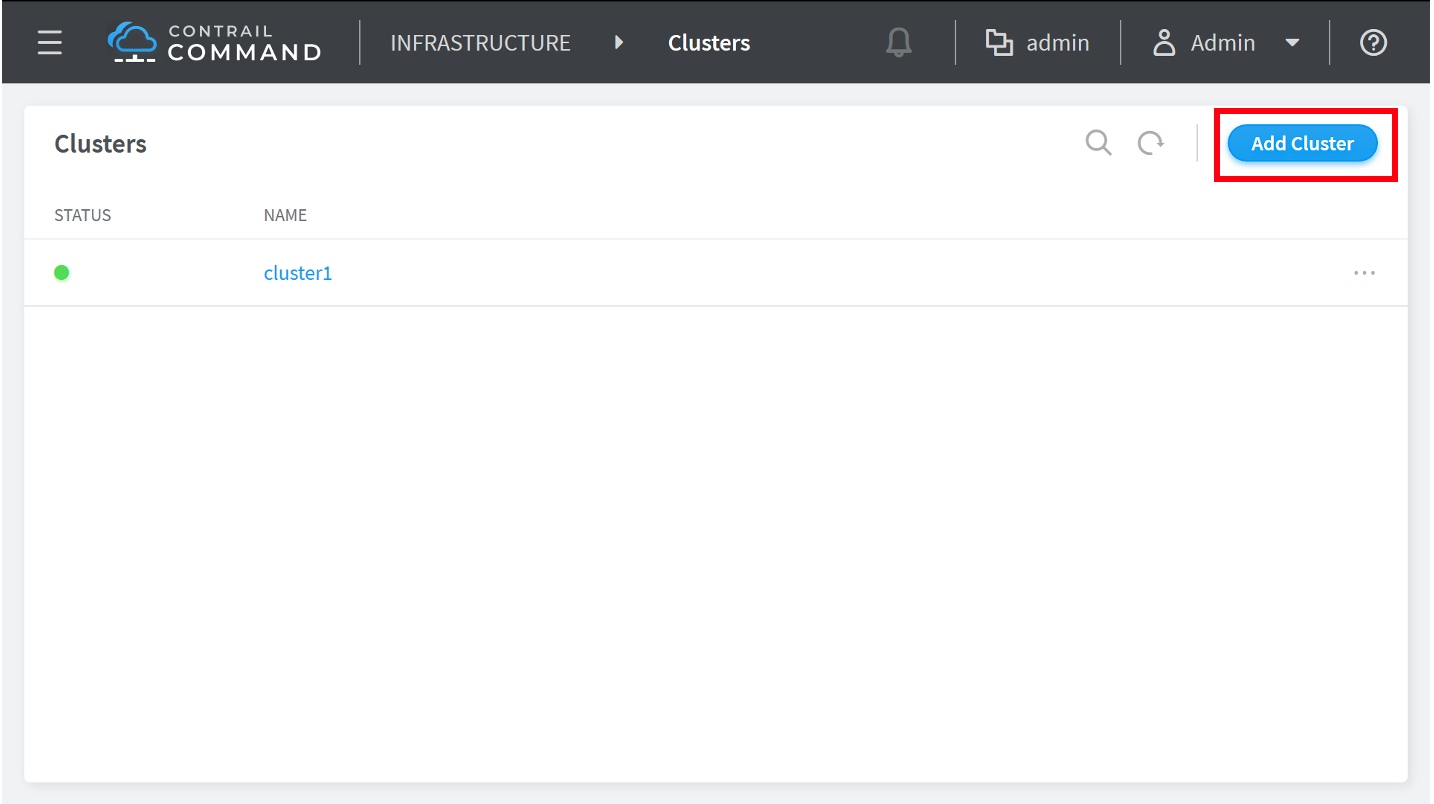
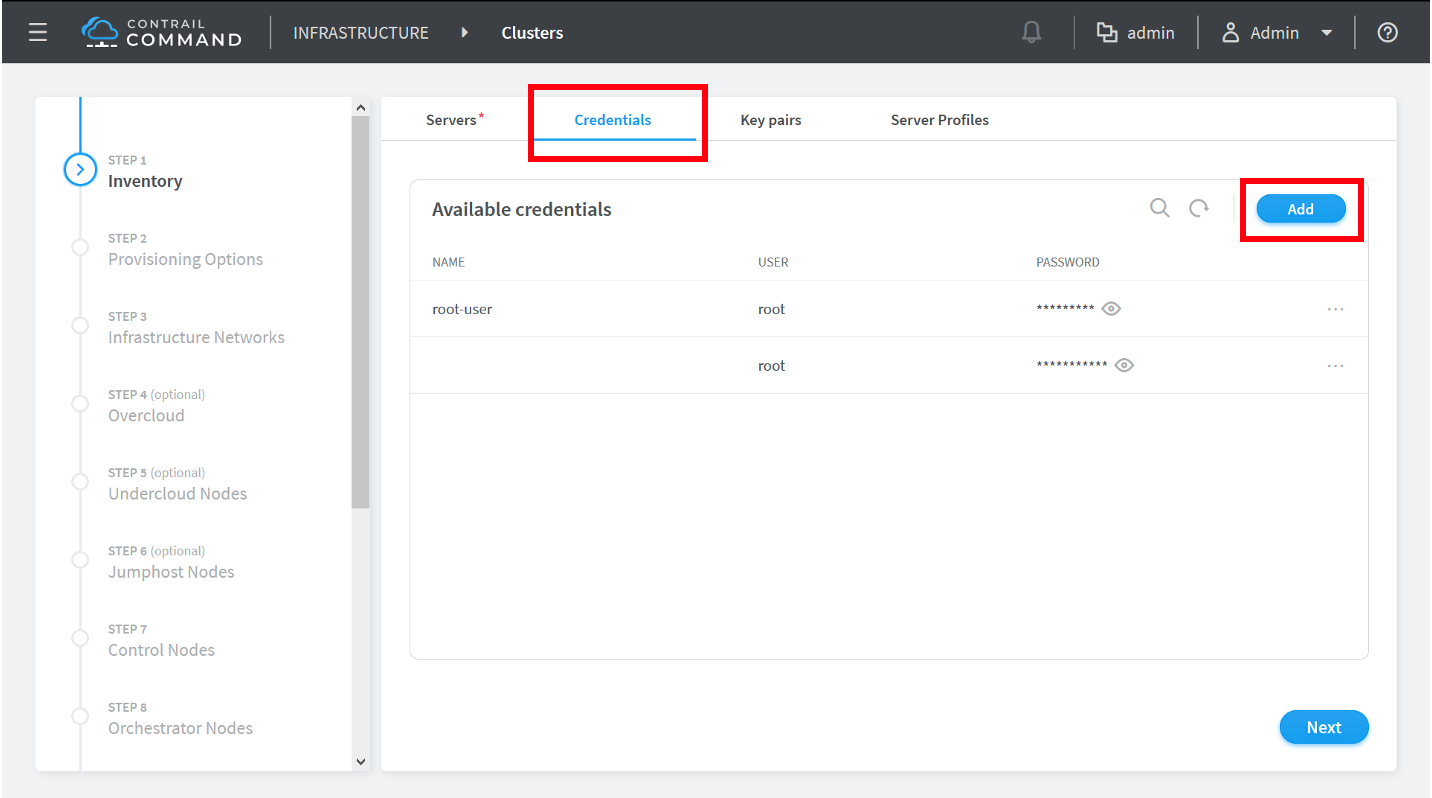
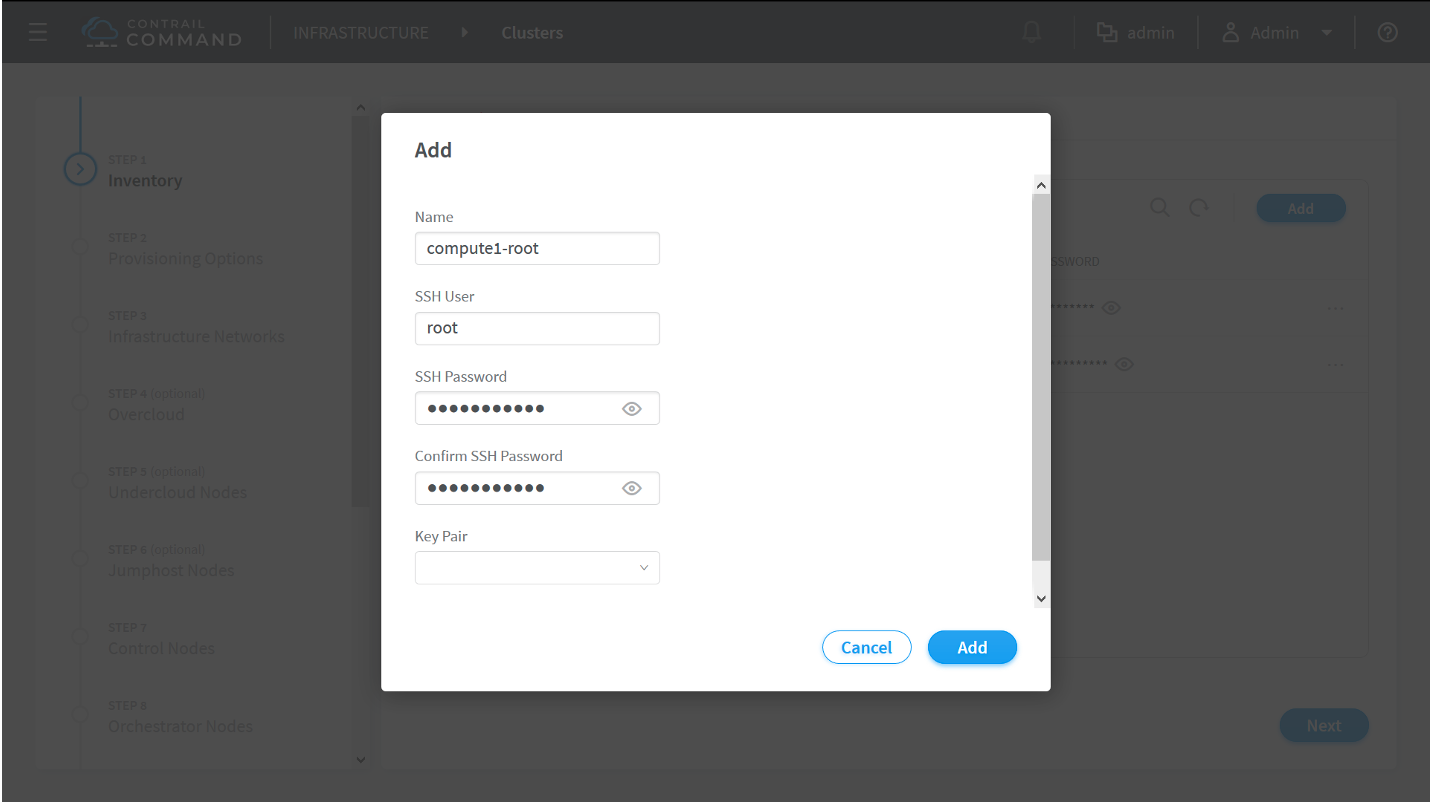
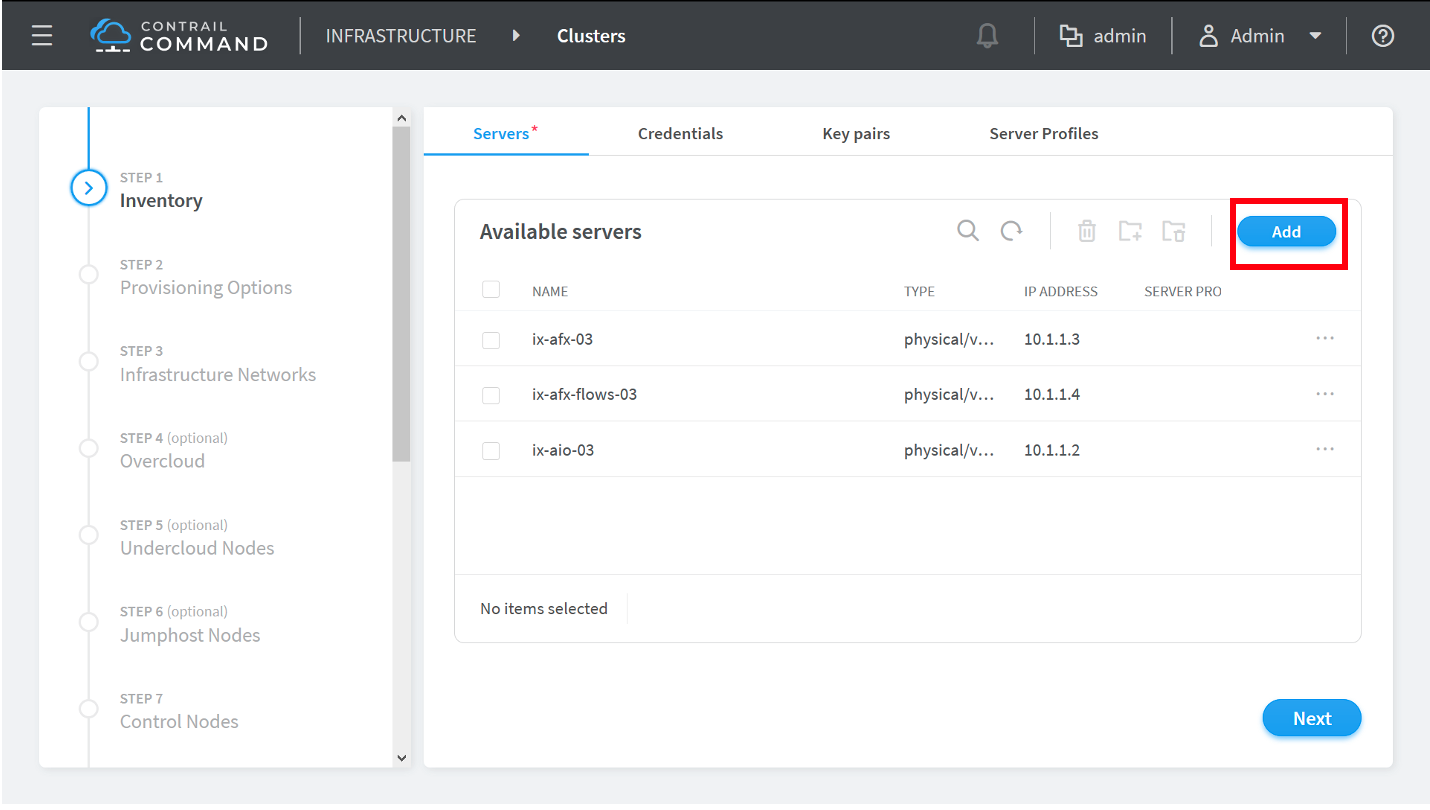
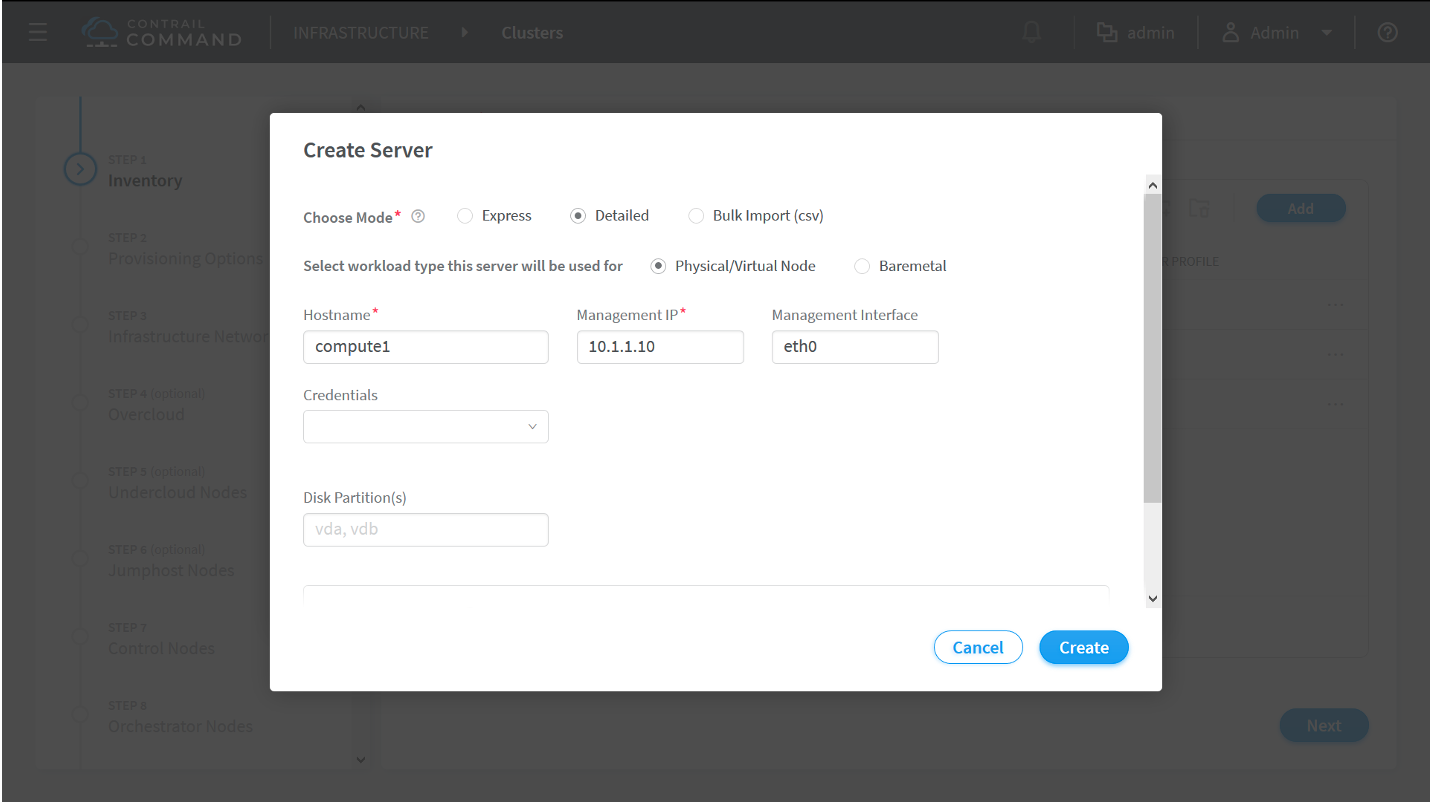
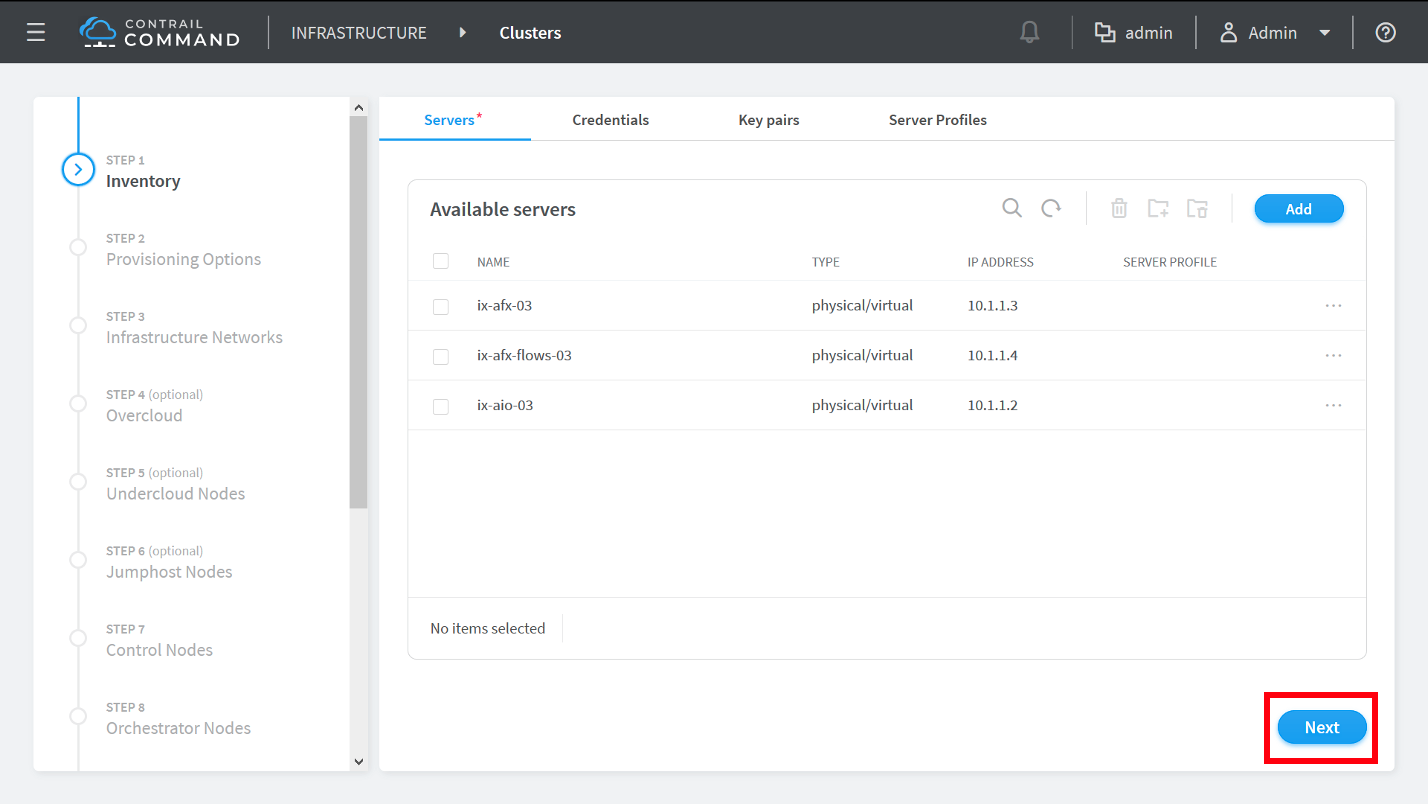
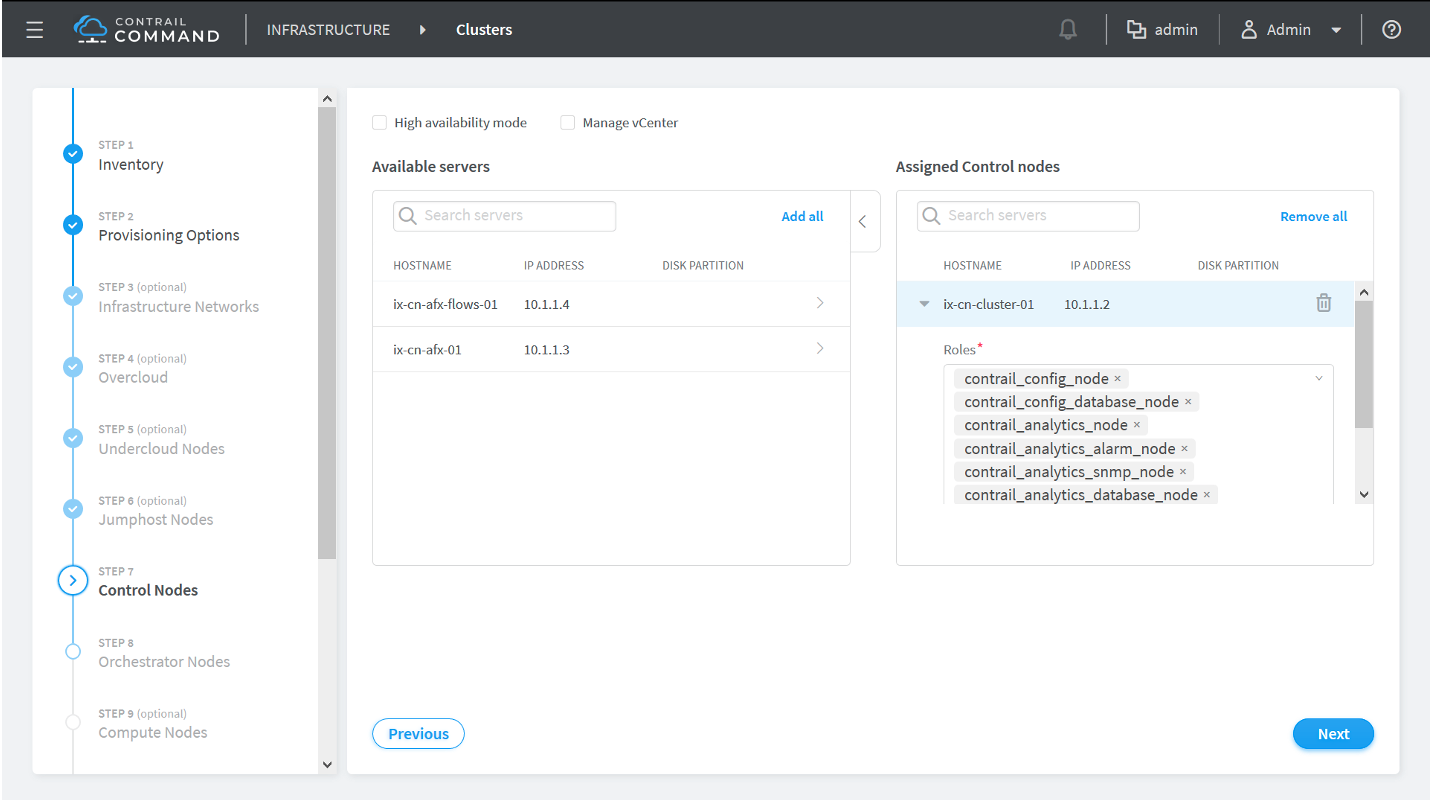
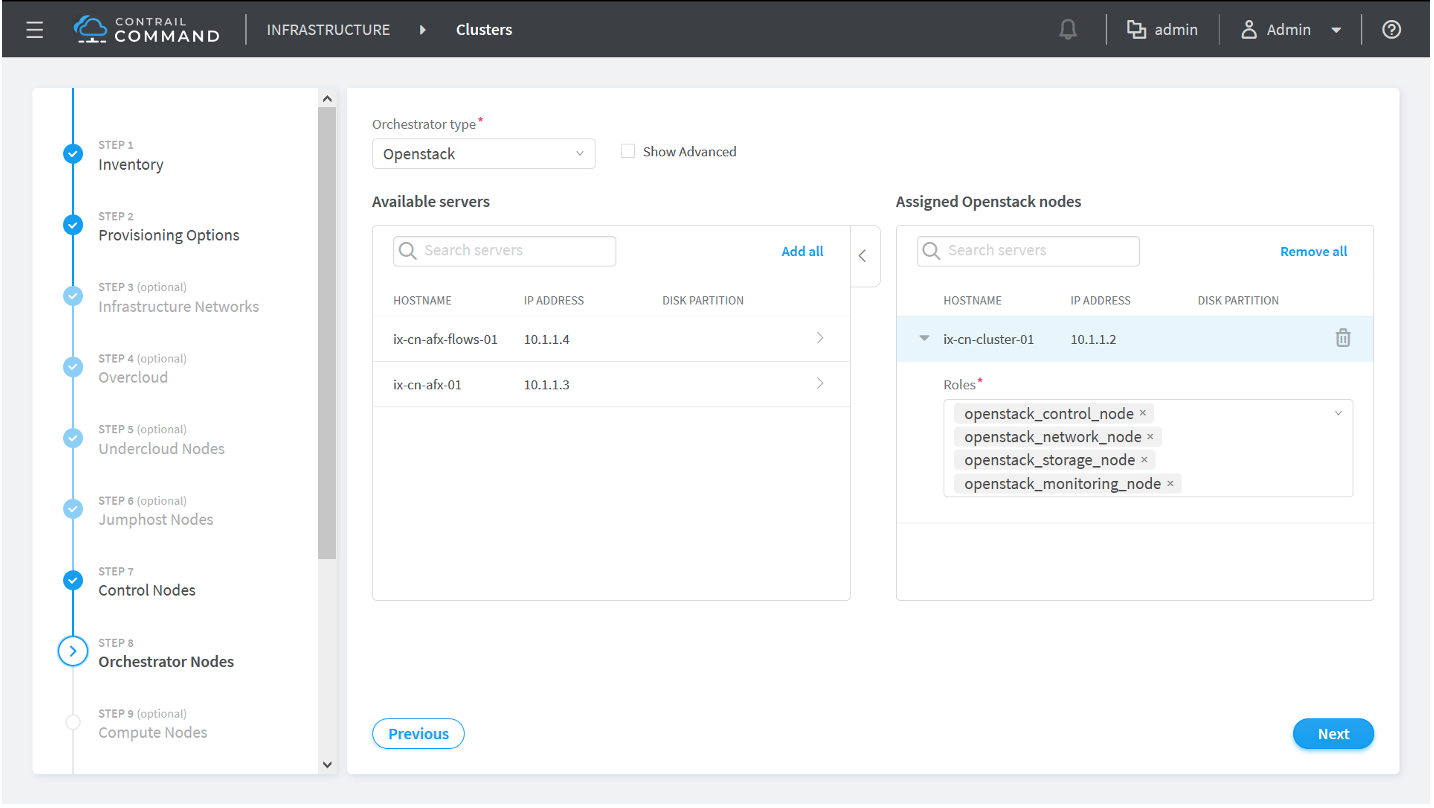
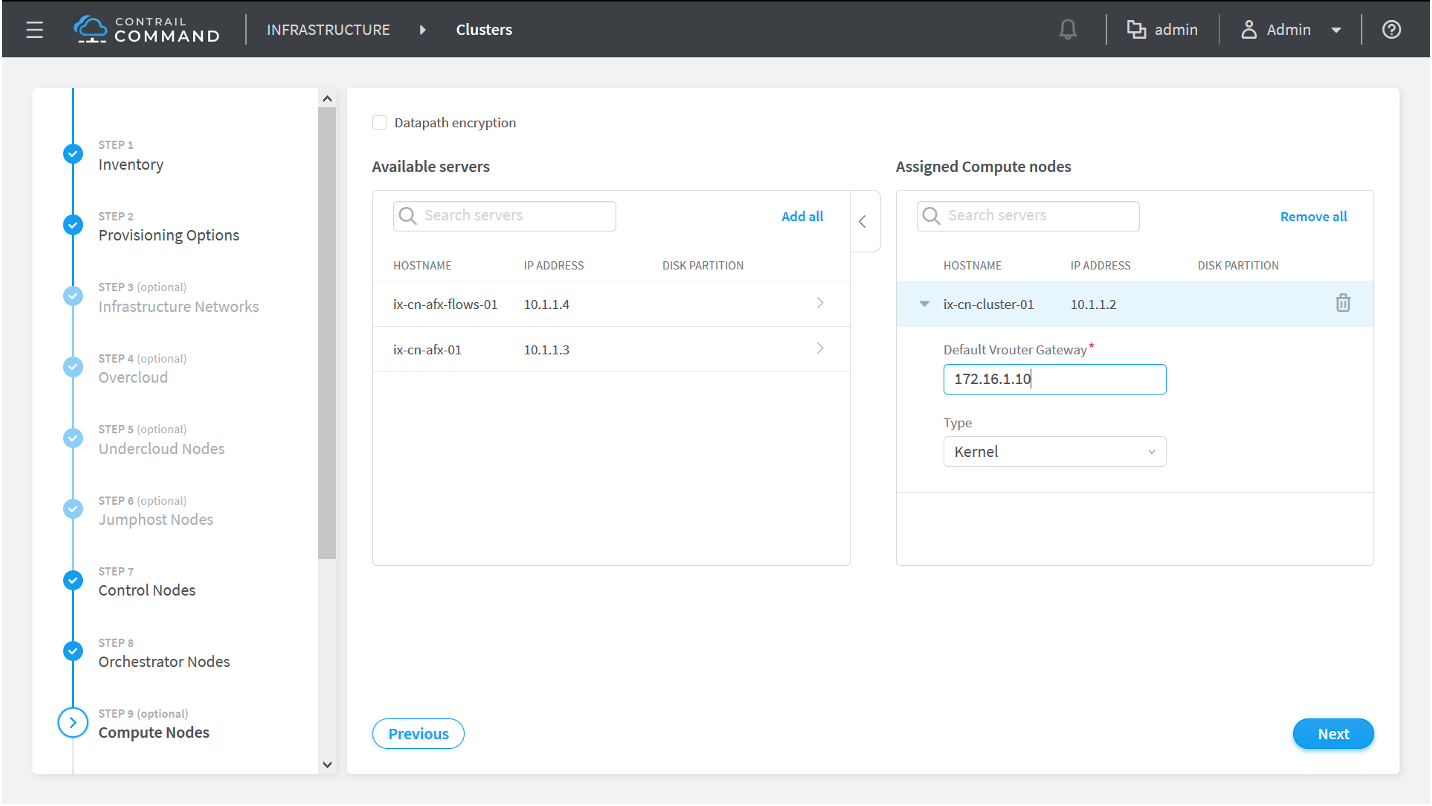
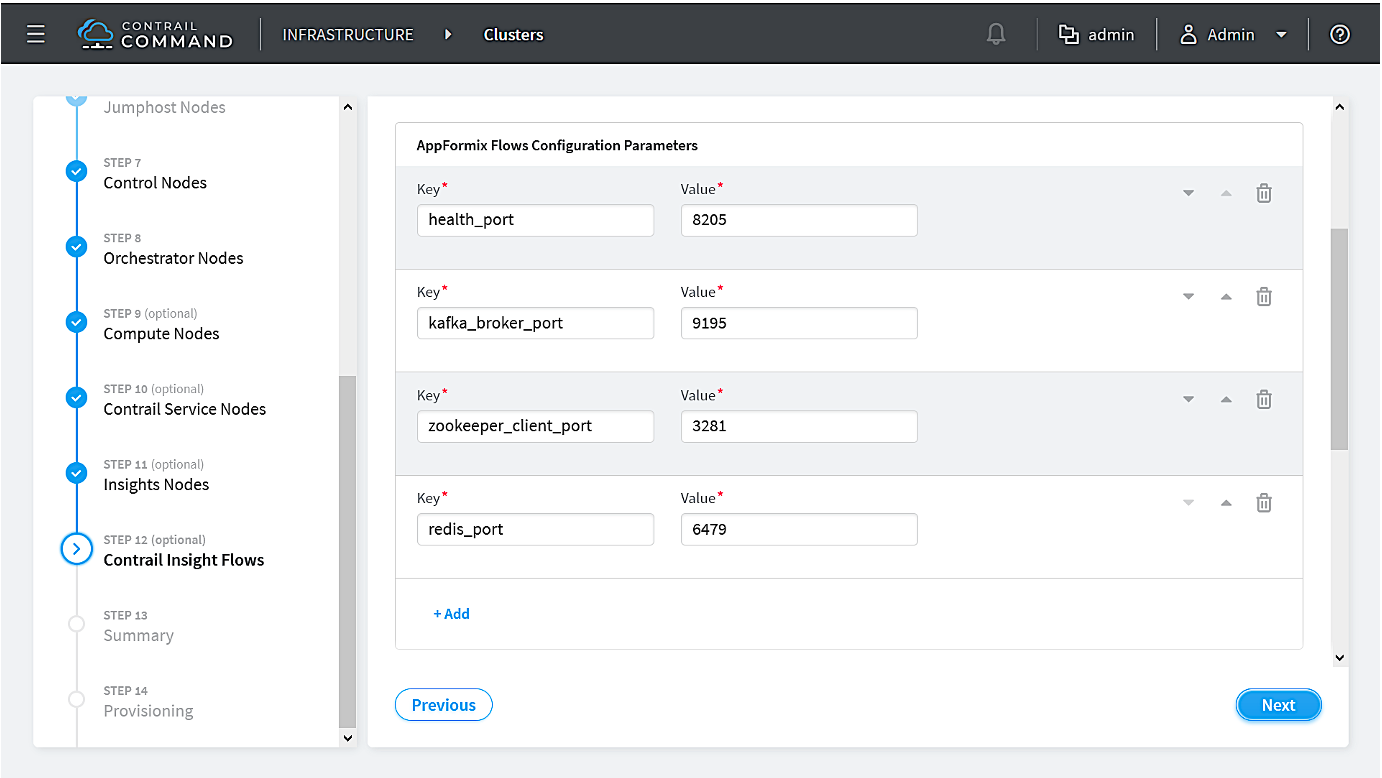
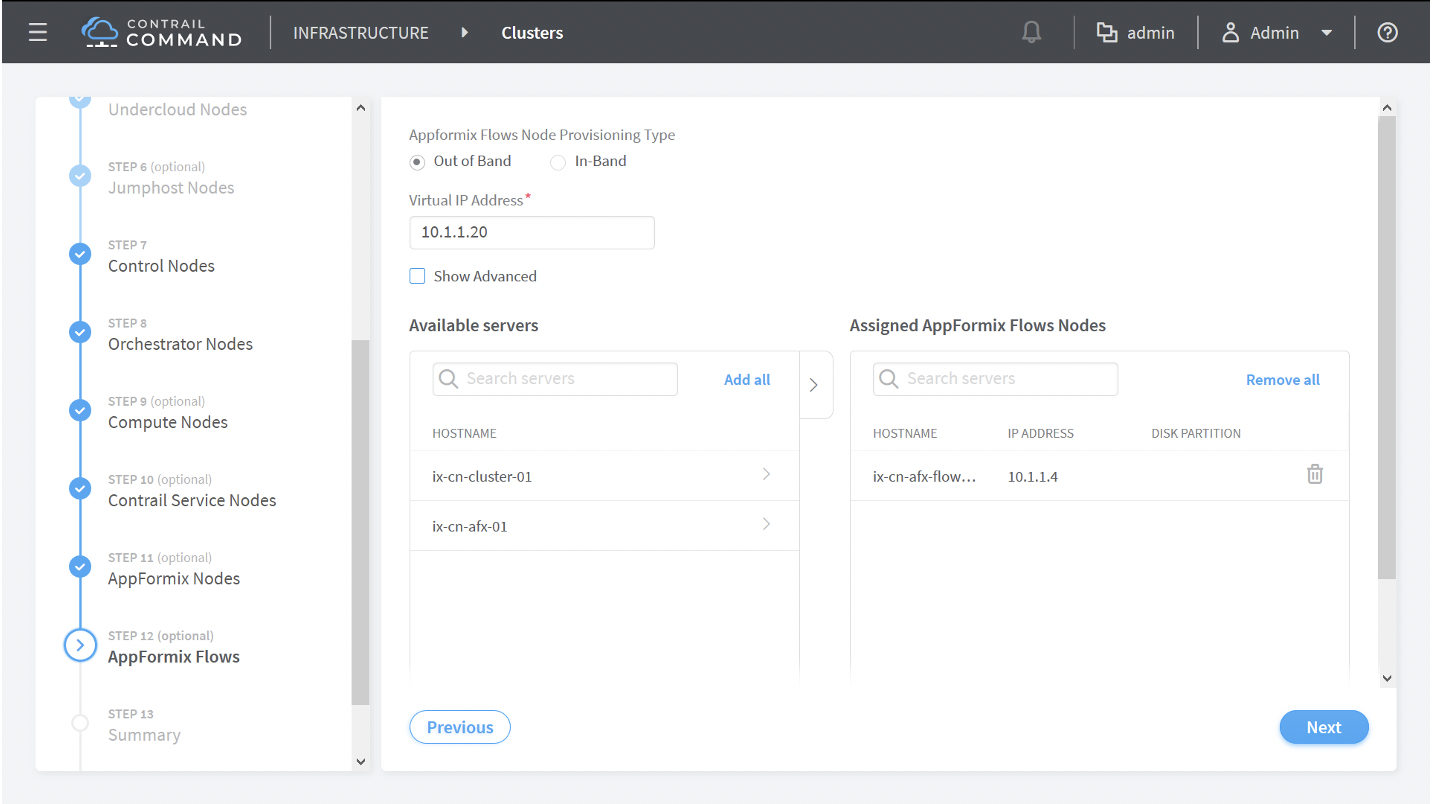
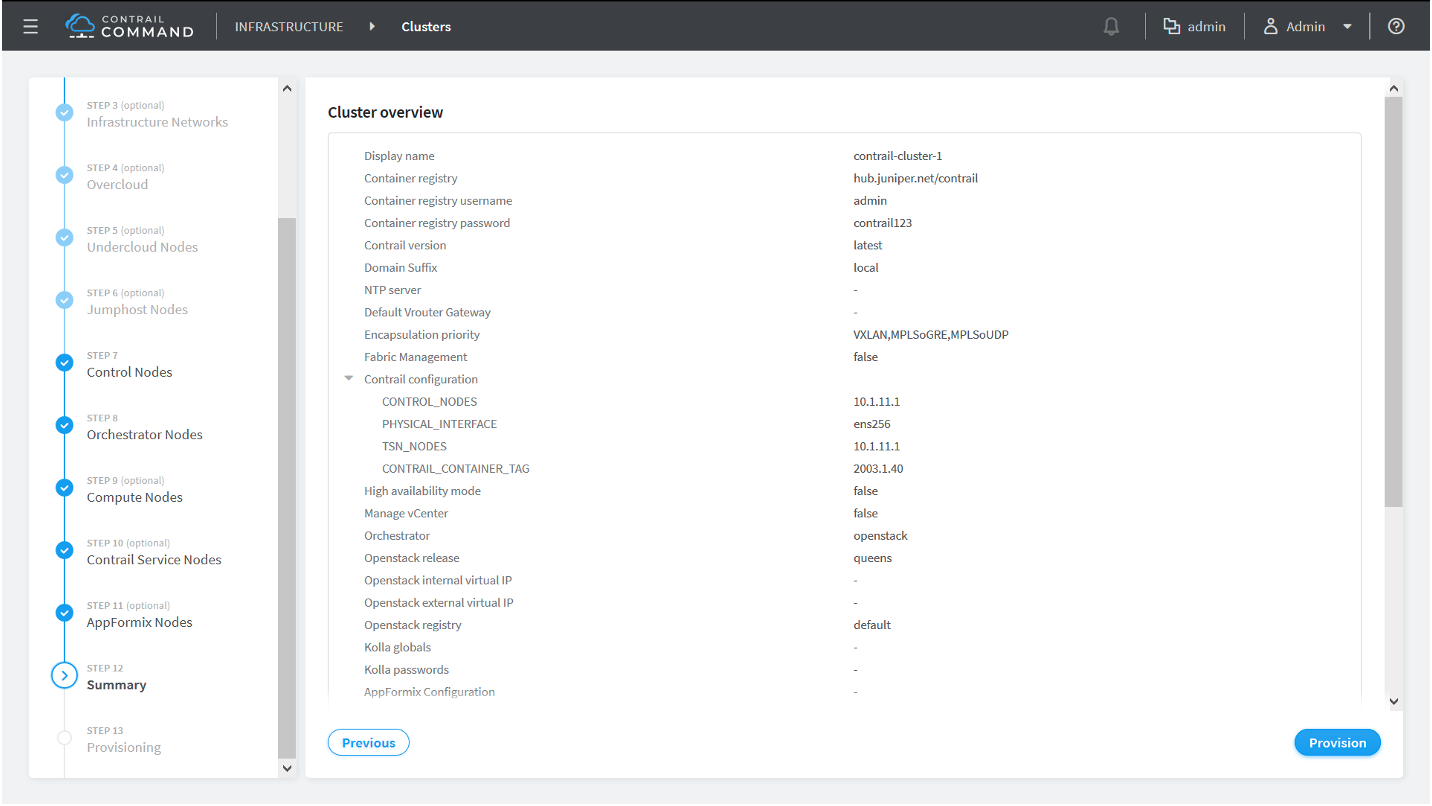
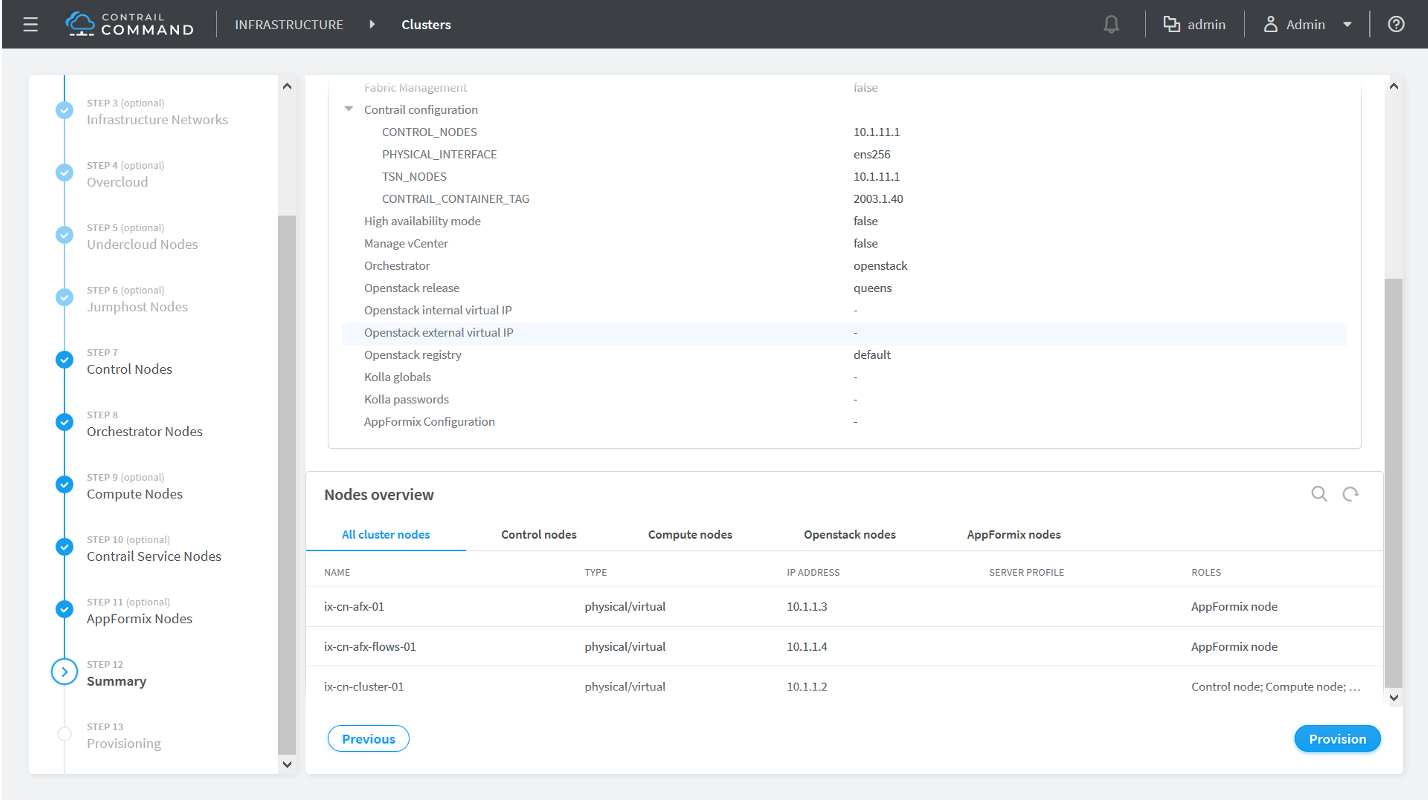
How to Provision Servers into the Contrail Cluster
Use this procedure to provision servers into your Contrail cluster. A Contrail cluster is a collection of interconnected servers that have been provisioned as compute nodes, control nodes, orchestrator nodes, Contrail Insights nodes, Contrail Insights Flows nodes, or service nodes in a cloud networking environment.
Before You Begin
Before you begin:
Plan your topology.
Ensure an out-of-band management network is established.
Ensure Contrail Command is installed. See How to Install Contrail Command.
Ensure all servers hosting Contrail cluster functions meet the specifications listed in Server Requirements.
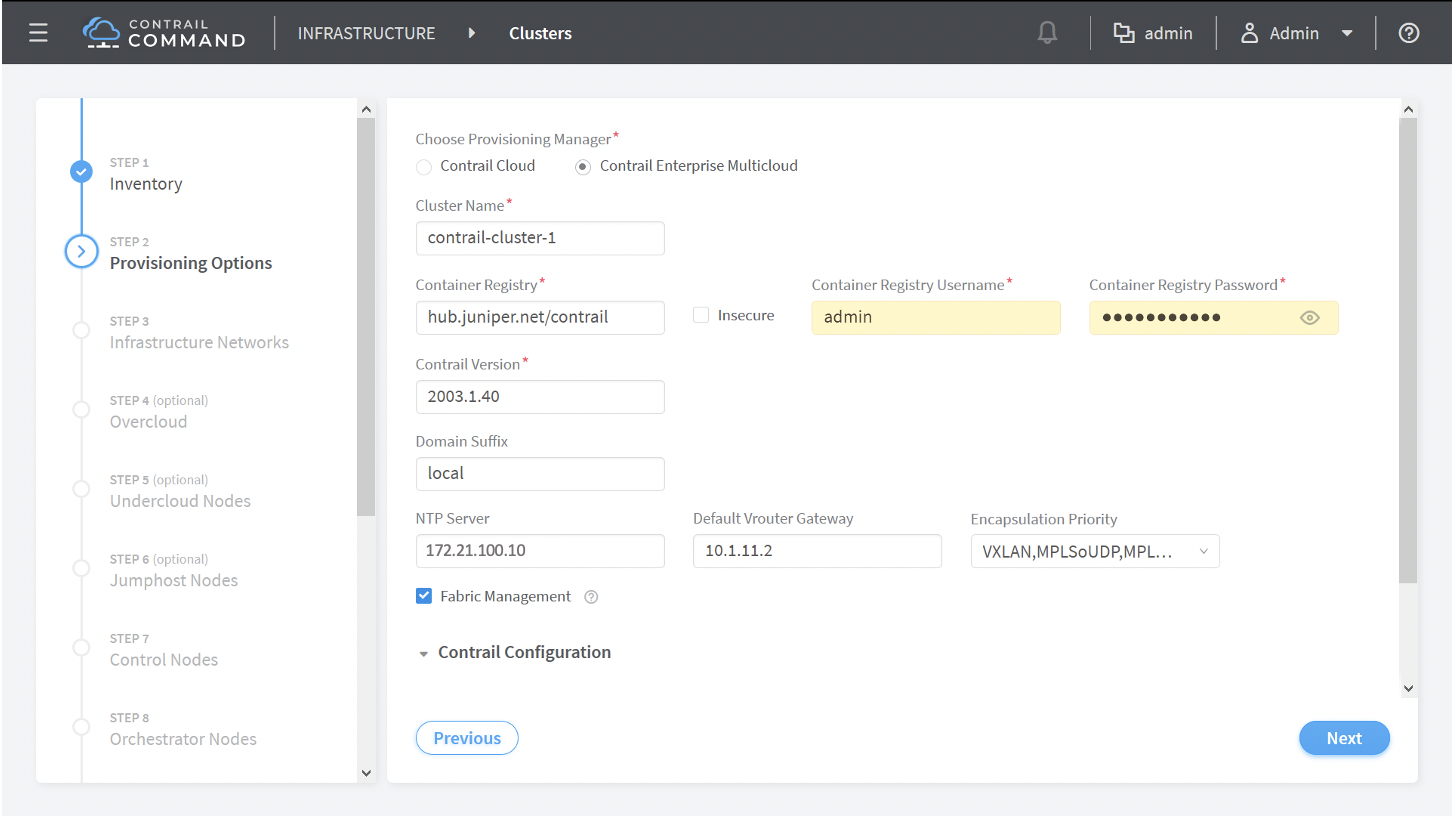
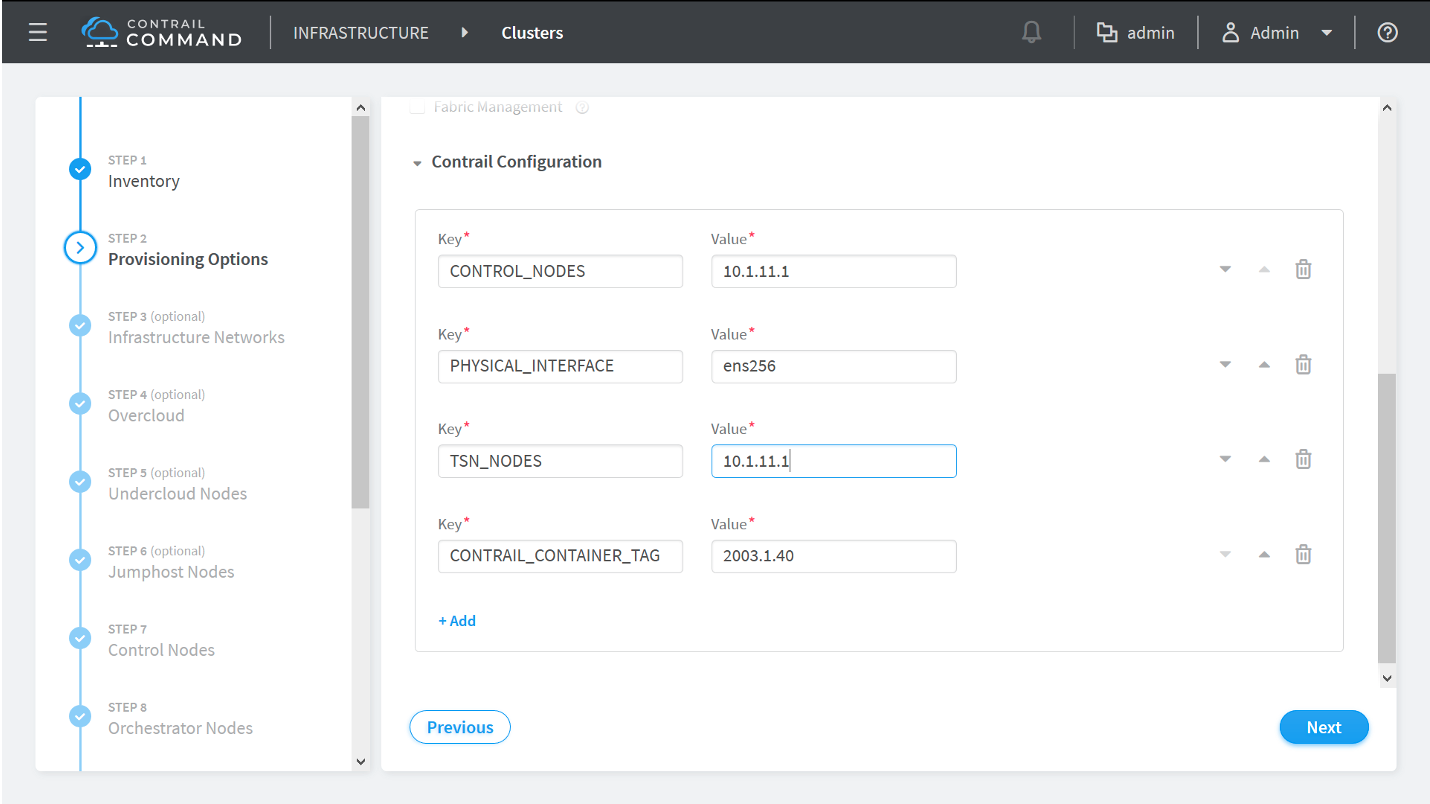
How to Provision the Contrail Cluster
To provision the Contrail cluster:
Sample command_servers.yml Files for Installing Contrail Command
- Minimal command_servers.yml file
- Complete command_servers.yml File
- Disaster Recovery and Troubleshooting
Minimal command_servers.yml file
The following sample file has the minimum configuration that you need when you install Contrail Command.
For security purposes, we strongly recommend creating unique username and password combinations in your environment. Username and password combinations are provided in this example for illustrative purposes only.
---
# Required for Appformix and Appformix Flows installations in Release 2003 and earlier
user_command_volumes:
- /opt/software/appformix:/opt/software/appformix
- /opt/software/xflow:/opt/software/xflow
command_servers:
server1:
ip: <IP Address> # IP address of server where you want to install Contrail Command
connection: ssh
ssh_user: root
ssh_pass: <contrail command server password>
sudo_pass: <contrail command server root password>
ntpserver: <NTP Server address>
registry_insecure: false
container_registry: hub.juniper.net/contrail
container_tag: <container_tag>
container_registry_username: <registry username>
container_registry_password: <registry password>
config_dir: /etc/contrail
contrail_config:
database:
type: postgres
dialect: postgres
password: contrail123
keystone:
assignment:
data:
users:
admin:
password: contrail123
insecure: true
client:
password: contrail123
Complete command_servers.yml File
The following sample file has an exhaustive list of configurations and supporting parameters that you can use when you install Contrail Command.
For security purposes, we strongly recommend creating unique username and password combinations in your environment. Username and password combinations are provided in this example for illustrative purposes only.
---
# Required for Appformix and Appformix Flows installations in Release 2003 and earlier
user_command_volumes:
- /opt/software/appformix:/opt/software/appformix
- /opt/software/xflow:/opt/software/xflow
# User defined volumes
#user_command_volumes:
# - /var/tmp/contrail:/var/tmp/contrail
command_servers:
server1:
ip: <IP Address>
connection: ssh
ssh_user: root
ssh_pass: <contrail command server password>
sudo_pass: <contrail command server root password>
ntpserver: <NTP Server address>
# Specify either container_path
#container_path: /root/contrail-command-051618.tar
# or registry details and container_name
registry_insecure: false
container_registry: hub.juniper.net/contrail
container_name: contrail-command
container_tag: <container_tag>
container_registry_username: <registry username>
container_registry_password: <registry password>
config_dir: /etc/contrail
# contrail command container configurations given here go to /etc/contrail/contrail.yml
contrail_config:
# Database configuration. PostgreSQL supported
database:
type: postgres
dialect: postgres
host: localhost
user: root
password: contrail123
name: contrail_test
# Max Open Connections for DB Server
max_open_conn: 100
connection_retries: 10
retry_period: 3s
# Log Level
log_level: debug
# Cache configuration
cache:
enabled: true
timeout: 10s
max_history: 100000
rdbms:
enabled: true
# Server configuration
server:
enabled: true
read_timeout: 10
write_timeout: 5
log_api: true
address: ":9091"
# TLS Configuration
tls:
enabled: true
key_file: /usr/share/contrail/ssl/cs-key.pem
cert_file: /usr/share/contrail/ssl/cs-cert.pem
# Enable GRPC or not
enable_grpc: false
# Static file config
# key: URL path
# value: file path. (absolute path recommended in production)
static_files:
/: /usr/share/contrail/public
# API Proxy configuration
# key: URL path
# value: String list of backend host
#proxy:
# /contrail:
# - http://localhost:8082
notify_etcd: false
# VNC Replication
enable_vnc_replication: true
# Keystone configuration
keystone:
local: true
assignment:
type: static
data:
domains:
default: &default
id: default
name: default
projects:
admin: &admin
id: admin
name: admin
domain: *default
demo: &demo
id: demo
name: demo
domain: *default
users:
admin:
id: admin
name: Admin
domain: *default
password: contrail123
email: admin@juniper.nets
roles:
- id: admin
name: admin
project: *admin
bob:
id: bob
name: Bob
domain: *default
password: bob_password
email: bob@juniper.net
roles:
- id: Member
name: Member
project: *demo
store:
type: memory
expire: 36000
insecure: true
authurl: https://localhost:9091/keystone/v3
# disable authentication with no_auth true and comment out keystone configuraion.
#no_auth: true
insecure: true
etcd:
endpoints:
- localhost:2379
username: ""
password: ""
path: contrail
watcher:
enabled: false
storage: json
client:
id: admin
password: contrail123
project_name: admin
domain_id: default
schema_root: /
endpoint: https://localhost:9091
compilation:
enabled: false
# Global configuration
plugin_directory: 'etc/plugins/'
number_of_workers: 4
max_job_queue_len: 5
msg_queue_lock_time: 30
msg_index_string: 'MsgIndex'
read_lock_string: "MsgReadLock"
master_election: true
# Plugin configuration
plugin:
handlers:
create_handler: 'HandleCreate'
update_handler: 'HandleUpdate'
delete_handler: 'HandleDelete'
agent:
enabled: true
backend: file
watcher: polling
log_level: debug
# The following are optional parameters used to patch/cherrypick
# revisions into the contrail-ansible-deployer sandbox. These configs
# go into the /etc/contrail/contrail-deploy-config.tmpl file
# cluster_config:
# ansible_fetch_url: "https://review.opencontrail.org/Juniper/contrail-ansible-deployer refs/changes/80/40780/20"
# ansible_cherry_pick_revision: FETCH_HEAD
# ansible_revision: GIT_COMMIT_HASH
Disaster Recovery and Troubleshooting
This section lists commonly seen errors and failure scenarios and procedures to fix them.
Problem
Description
Recovering the Galera Cluster Upon Server Shutdown—In an OpenStack HA setup provisioned using Kolla and OpenStack Rocky, if you shut down all the servers at the same time and bring them up later, the Galera cluster fails.
Solution
To recover the Galera cluster, follow these steps:
Edit the /etc/kolla/mariadb/galera.cnf file to remove the
wsrepaddress on one of the controllers as shown here.wsrep_cluster_address = gcomm:// #wsrep_cluster_address = gcomm://10.x.x.8:4567,10.x.x.10:4567,10.x.x.11:4567
Note:If all the controllers are shut down in the managed scenario at the same time, you must select the controller that was shut down last.
Docker start mariadb on the controller on which you edited the file.
Wait for a couple of minutes, ensure that the mariadb container is not restarting, and then Docker start mariadb on the remaining controllers.
Restore the /etc/kolla/mariadb/galera.cnf file changes and restart the mariadb container on the previously selected controller.
Problem
Description
Containers from Private Registry Not Accessible—You might have a situation in which containers that are pulled from a private registry named CONTAINER_REGISTRY are not accessible.
Solution
To resolve, check to ensure that REGISTRY_PRIVATE_INSECURE is set to True.