Stateful Firewall Traffic Flow in a Single MX Series Router (CSDS Traffic Orchestrator) and Scaled-Out SRX Series Firewalls
In this topic, you’ll see how stateful firewall traffic flows in a single MX Series router with CSDS Traffic Orchestrator and SRX Series Firewalls.
See Figure 1 for topology. In this topology:
- Configure a single MX Series with two interfaces logical interfaces (IFL) for TRUST and UNTRUST routing instances. MX Series CSDS Traffic Orchestrator (CSDS-TO) does health check on all the scaled-out SRX Series Firewalls and builds the next-hop for load balancing the traffic.
- Connect all the scaled-out SRX Series Firewalls to the MX Series with BGP connections.
-
Configure the MX Series router with CSDS-TO on the TRUST routing instance. CSDS-TO performs the load balancing of data traffic coming from client side gateway router toward the scaled-out SRX Series Firewalls. For the return traffic coming from the server side on the MX Series UNTRUST routing instance, configure another instance on the MX Series UNTRUST side.
-
Configure unique IP addresses, such as the loopback, for all the scaled-out SRX Series Firewalls connected to MX Series router. CSDS-TO uses the IP addresses to perform the health check and build the selector table in the Packet Forwarding Engine. The Packet Forwarding Engine uses this selector table to load-balance the packet across the available next-hops. This health check is reachable through the BGP connection.
-
Filter-based forwarding (FBF) based on source IP address match is used in MX Series router to push stateful firewall traffic to the CSDS-TO TRUST forwarding instance.
-
CSDS-TO forwarding instance has a default route with next hop as list of SRX Series Firewalls. CSDS-TO installs this default route when its health check passes with at least one SRX Series Firewalls.
-
CSDS-TO does source-based hash load balancing across all the available SRX Series Firewall next hop devices.
-
Load balanced stateful firewall data sessions are anchored on any available SRX Series Firewalls and stateful firewall flow gets created. Then it is routed to reach the server through MX Series router over UNTRUST routing instance.
-
For the return traffic coming from server to client direction on the MX Series UNTRUST routing instance, another instance is configured on MX Series UNTRUST routing instance to do the load balancing back to the same SRX Series Firewalls.
-
FBF of the destination IP address match is used in MX Series router to push stateful firewall traffic to the CSDS-TO UNTRUST forwarding instance.
-
CSDS-TO forwarding instance has a default route with next-hop as list of SRX Series Firewalls. CSDS-TO installs this default route when its health check passes with at least one SRX Series Firewalls.
-
CSDS-TO does destination-based hash load balancing across all the available SRX Series Firewall next-hop devices.
-
Load balanced stateful firewall data sessions are load balanced to the same SRX Series Firewalls on the return direction and uses the same flow to reach the client through MX Series router over TRUST routing instance.
Figure 1 illustrates the step-by-step traffic flow.
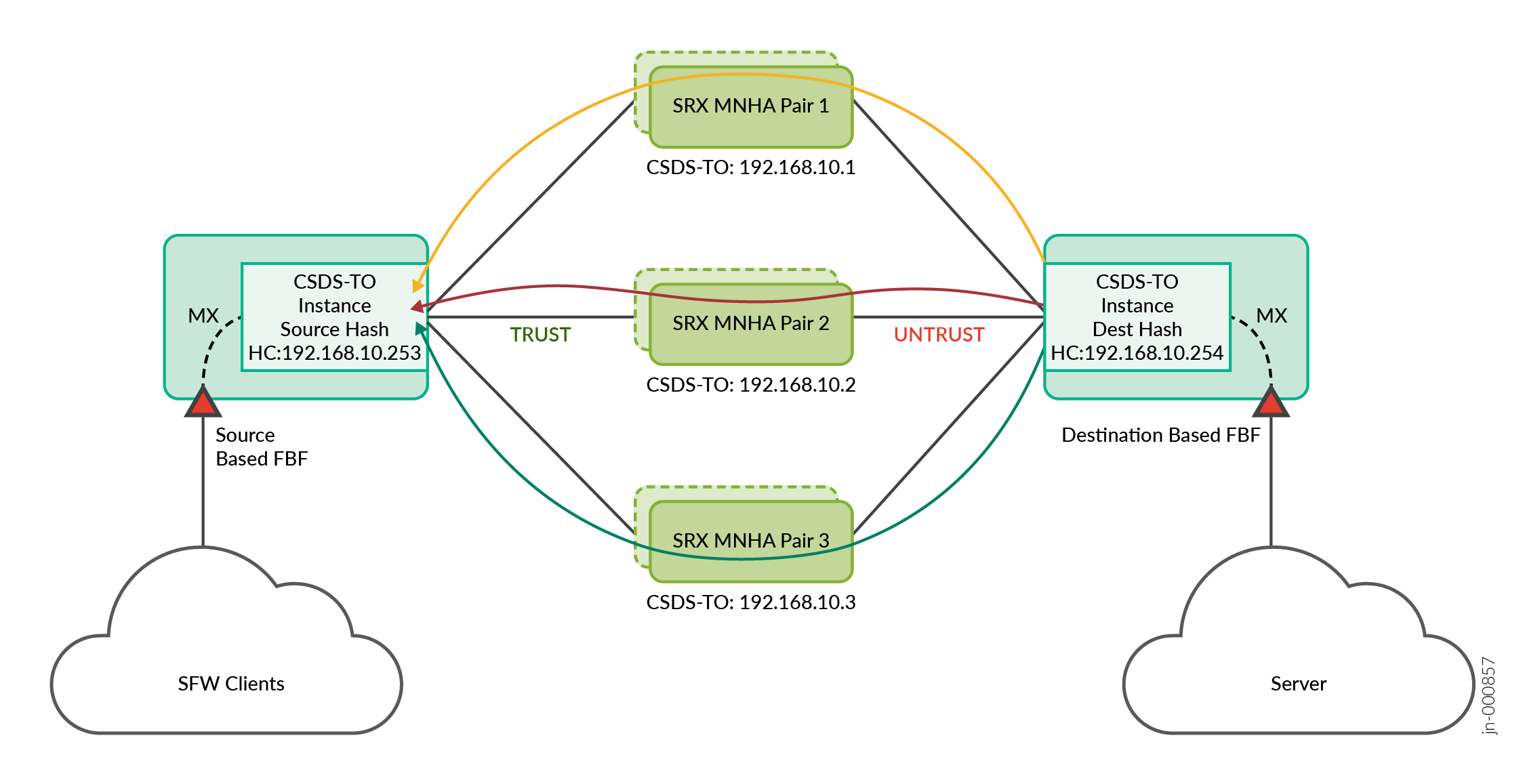
The MX Series is a single router setup with multiple logical interfaces toward scaled-out SRX Series Firewalls on the TRUST VR and UNTRUST VR direction.
For the forward traffic coming from client to server, the MX Series router uses FBF based on the source IP address match to push the stateful firewall traffic to the CSDS-TO TRUST forwarding instance. CSDS-TO forwarding instance includes a default route with next-hop as the list of SRX Series Firewalls. CSDS-TO installs this default route when the health check passes for at least one SRX Series Firewalls.
CSDS-TO performs source-based hash load balancing across all the available SRX Series Firewall next-hop devices.
Load balanced statfeul firewall data sessions are anchored on any available SRX Series Firewalls and stateful firewall flow is created.
Then the traffic is routed to reach the server through the MX Series over UNTRUST routing instance.
For the return traffic coming from the server-to-client on the MX Series UNTRUST routing instance, another instance is configured on MX Series UNTRUST routing instance to perform the load balancing back to the same SRX Series Firewalls. The FBF based on the destination IP address match is used in MX Series router to push next-generation firewall traffic to the CSDS-TO UNTRUST forwarding instance. CSDS-TO forwarding instance includes a default route with next-hop as list of SRX Series Firewalls. CSDS-TO installs this default route when the health check passes for at least one SRX Series Firewalls.
CSDS-TO performs destination-based hash load balancing across all the available SRX Series Firewall next-hop devices. Load balanced stateful firewall data sessions are anchored to the same SRX Series Firewalls.
SRX Series Firewalls use the same flow to process the return traffic and forwards to MX.
MX Series routes the packet back to the client.
For more information, see Example: Single MX Series (CSDS Traffic Orchestrator) and Scaled-Out SRX Series Firewall (MNHA) for Stateful Firewall.
