Create Allowlists and Blocklists
Access these pages from or .
Use these pages to configure custom trusted and untrusted lists. You can also upload hash files.
Content downloaded from locations on the allowlist is trusted and does not have to be inspected for malware. Hosts cannot download content from locations on the blocklist, because those locations are untrusted.
Before You Begin
-
Read the Allowlist and Blocklist Overview topic.
-
Decide on the type of item you intend to define:
-
URL
-
IP
-
File Hash
-
E-mail sender
-
AI-PTP
-
C&C
-
ETI
-
DNS
-
-
Review current list entries to ensure the item you are adding does not exist.
-
If you are uploading hash files, the files must be in a text file (TXT) with each hash on its own single line.
Create Allowlists
Select .
Select one of the types mentioned in Allowlists Supported Types.
Table 1: Allowlists Supported Types Type
Information
Anti-malware
IP address, URL, file hash, e-mail sender, and AI-PTP
SecIntel
C&C IP address and domain
ETI
IP address and hostname
DNS
Domains
Reverse Shell
Destination IP addresses and domains
Note:Domain refers to a fully qualified domain name (FQDN).
Enter the required information.
Click OK.
Create Blocklists
Select .
Select one of the types mentioned in Blocklists Supported Types.
Table 2: Blocklists Supported Types Type
Information
Anti-malware
IP address, URL, file hash, and e-mail sender
SecIntel
C&C IP address and domain
Enter the required information.
Click OK.
See the following tables for the data required by each type.
- IP
- URL
- File Hash
- Email Sender
- AI-PTP
- C&C Server
- Encrypted Traffic Insights (ETI)
- Domain Name System (DNS)
- Reverse Shell
IP
When you create an IP list item, you must select the Type of list as IP. You must enter the required information. See the following table.
|
Setting |
Guideline |
|---|---|
|
IP |
Enter the IPv4 or IPv6 IP address. For example: 1.2.3.4 or 0:0:0:0:0:ffff:0102:0304. CIDR notation and IP address ranges are also accepted. Any of the following IPv4 formats are valid: 1.2.3.4, 1.2.3.4/30, or 1.2.3.4-1.2.3.6. Any of the following IPv6 formats are valid: 1111::1, 1111::1-1111::9, or 1111:1::0/64. Note:
Address ranges: No more than a block of /16 IPv4 addresses and /48 IPv6 addresses are accepted. For example, 10.0.0.0-10.0.255.255 is valid, but 10.0.0.0-10.1.0.0 is not. Bitmasks: The maximum amount of IP addresses covered by bitmask in a subnet record for IPv4 is 16 and for IPv6 is 48. For example, 10.0.0.0/15 and 1234::/47 are not valid. |
|
Note:
To edit an allowlist or blocklist IP entry, select the check box next to the entry you want to edit, click the pencil icon and click OK. |
|
URL
When you create a URL list item, you must choose the Type of list: URL. Enter the required information. See the following table.
|
Setting |
Guideline |
|---|---|
|
URL |
Enter the URL using the following format: juniper.net. Wildcards and protocols are not valid entries. The system automatically adds a wildcard to the beginning and end of URLs. Therefore juniper.net also matches a.juniper.net, a.b.juniper.net, and a.juniper.net/abc. If you explicitly enter a.juniper.net, it matches b.a.juniper.net, but not c.juniper.net. You can enter a specific path. If you enter juniper.net/abc, it matches x.juniper.net/abc, but not x.juniper.net/123. To edit an allowlist or blocklist URL entry, select the check box next to the entry you want to edit, click the pencil icon and click OK. |
File Hash
When you upload a hash file, it must be in a TXT with each hash on its own single line. You can only have one running hash file. To add to it or edit it, see the instructions in the following table.
|
Field |
Guideline |
|---|---|
|
You can add custom allowlist and blocklist hashes for filtering, but these hashes must be listed in a TXT with each entry on a single line. You can only have one running hash file containing up to 15,000 file hashes. This file contains the “current” list, but you can add to it, edit it, and delete it at any time. |
|
|
SHA-256 Hash Item |
To add to hash entries, you can upload several TXT files and these files will automatically combine into one file. See all, merge, delete and replace options below. Download—Click this button to download the TXT if you want to view or edit it. You can select any of the following options from the Select Hash File Items Upload Option drop-down list:
Delete All or Delete Selected—Sometimes it is more efficient to delete the current list rather than downloading it and editing it. Click this button to delete the current selected list or all lists that have been added and accumulated here. |
|
Source |
This field indicates either Allowlist or Blocklist. |
|
Date Added |
The month, date, year, and time when the hash file was last uploaded or edited. |
Email Sender
Add email addresses to be allowlist or blocklist if found in either the sender or recipient of an email communication. Add addresses one at a time using the + icon.
|
Field |
Guideline |
|---|---|
|
Email address |
Enter an email address in the format name@domain.com. Wildcards and partial matches are not supported, but if you want to include an entire domain, you could enter only the domain as follows: domain.com |
|
If an email matches the blocklist, it is considered to be malicious and is handled the same way as an email with a malicious attachment. The email is blocked and a replacement email is sent. If an email matches the allowlist, that email is allowed through without any scanning. See Quarantined Emails Overview. It is worth noting that attackers can easily fake the “From” email address of an email, making blocklists a less effective way to stop malicious emails. |
|
AI-PTP
Juniper Networks' AI-Predictive Threat Prevention is an advanced malware detection and prevention solution designed to safeguard your network against threats arising from users accessing corporate resources from various locations and browsing the Internet to many destinations. Powered by AI and ML, this intelligent security solution enhances the ability to predict and identify genuine threats more swiftly, allowing human experts to concentrate on strategic security initiatives.
For more information about AI-Predictive Threat Prevention (AI-PTP), see AI-Predictive Threat Prevention Overview.
You can use the AI-PTP tab to add, replace, merge, or delete AI-PTP signatures in the allowlists. You can add the file signatures that are identified as false positives to the allowlists. This process excludes the specified signatures from malware inspection performed by the SRX Series Firewalls.
To add or edit a list of signatures:
Select .
The AI-PTP Signature page is displayed.
Select any of the following options from the Signature File Upload Option drop-down list:
Replace current list—Upload a text file (TXT) containing a list of file signatures or modify the existing list without deleting it. Download, edit, and re-upload the file. You can upload multiple TXT files that will automatically combine into one file.
You can obtain AI-PTP signatures from the following sources:
HTTP File Downloads—Navigate to
Figure 1: AI-PTP Signatures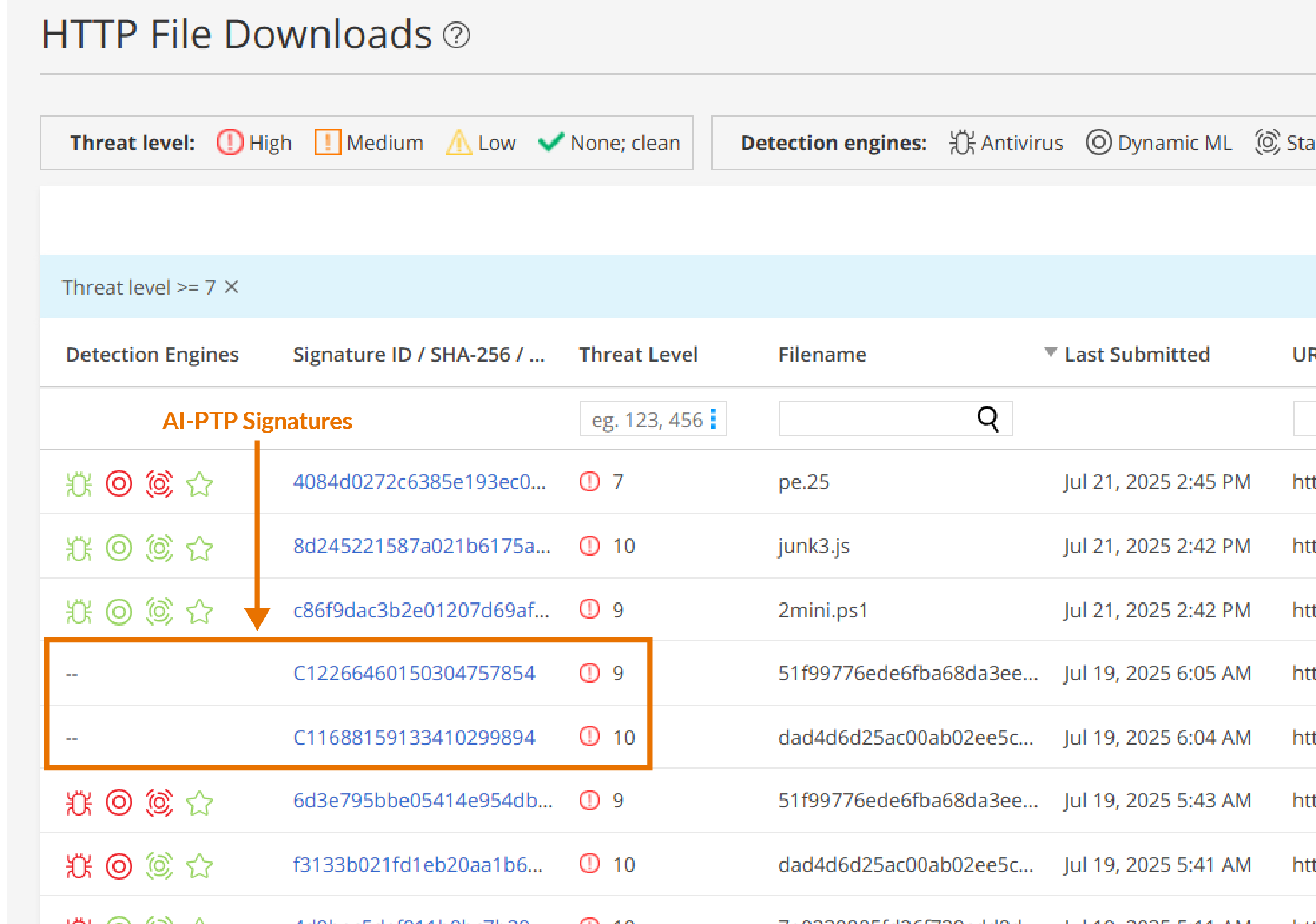
Email Attachments—Navigate to
SMB File Downloads—Navigate to
Syslogs on SRX Series Firewalls
Merge with current list—Combine a new TXT with the existing file, creating a single file with all signatures.
Delete from current list—Remove specific signatures. Create a TXT with the signatures to be removed, upload it, and only those signatures will be deleted.
The Upload Hash List window is displayed.
Browse your computer and select the TXT file.
Click OK.
The AI-PTP signatures are added to the allowlists.
Table 7 describes the AI-PTP Signature fields.
Table 7: AI-PTP Signature Fields Field
Description
Signature
Number of file signatures added to the allowlists
Date Added
Date and time when the file signatures list was last uploaded or edited.
Click Download to download the TXT if you want to view or edit it.
Click Delete All to delete all lists that have been added to the allowlists.
To view the list of advanced-anti-malware (AAMW) signatures added to the allowlists
on SRX Series Firewalls, use the CLI command show services
advanced-anti-malware signature-exempt-list.
show services advance-anti-malware signature-exempt-list Advanced-anti-malware Signature Exempt List: J1994069136041805794 C5381964424818232941 J12111449344962437113 C4660909146742838820 Total exempt signatures: 4
To view the list of anti-virus signatures added to the allowlists
on SRX Series Firewalls, use the CLI command show services anti-virus
signature-exempt-list.
Anti-virus Signature Exempt List: C1994069136041805794 J5381964424818232941 J12111449344962437113 J4660909146742838820 Total exempt signatures: 4
To clear the file signature allowlists on the SRX Series
Firewalls, use CLI command clear services anti-virus
signature-exempt-list.
You can also run the following CLI commands on your SRX Series Firewalls to add, delete, export, and import file signatures:
-
request services anti-virus signature-exempt-list add <signature-id>—add file signature IDs on your SRX Series Firewall. For example,request services anti-virus signature-exempt-list add J4660909146742838820. -
request services anti-virus signature-exempt-list delete <signature-id>—delete file signature IDs on your SRX Series Firewall. For example,request services anti-virus signature-exempt-list delete J4660909146742838820. -
request services anti-virus signature-exempt-list import <txt-file-with-signature-ids>—import TXT file that contains signature IDs on your SRX Series Firewall. For example,request services anti-virus signature-exempt-list import /var/tmp/av-exempt-list.txt. -
request services anti-virus signature-exempt-list export <txt-file-with-signature-ids>—export TXT file that contain signature IDs from your SRX Series Firewall. For example,request services anti-virus signature-exempt-list export /var/tmp/av-exempt-list.txt.
C&C Server
When you allowlist a C&C server, the SRX Series Firewalls receive the IP or hostname. The firewalls then exclude it from any SecIntel blocklists or C&C feeds, including Juniper’s global threat feed and third-party feeds. The server will also now be listed under the C&C allowlist management page.
You can enter C&C server data manually or upload a list of servers. That list must be a TXT with each IP or Domain on its own single line. The TXT must include all IPs or all Domains, each in their own file. You can upload multiple files, one at a time.
You can also manage allowlist and blocklist entries using the Threat Intelligence API. When adding entries to the allowlist/blocklist data, these entries will be available in the Threat Intelligence API under the following feed names: “whitelist_domain” or “whitelist_ip”, and “blacklist_domain” or “blacklist_ip.” See the Juniper ATP Cloud Threat Intelligence Open API Setup Guide for details on using the API to manage any custom feeds.
|
Field |
Guideline |
|---|---|
|
Type |
Select IP to enter the IP address of a C&C server that you want to add to the allowlist. Select Domain to allowlist an entire domain on the C&C server list. |
|
IP or Domain |
For IP, enter an IPv4 or IPv6 address. An IP can be IP address, IP range or IP subnet. For domain, use the following syntax: juniper.net. Wildcards are not supported. |
|
Description |
Enter a description that indicates why an item has been added to the list. |
|
You can also allowlist C&C servers directly from the C&C Monitoring page details view. See Command And Control Servers: More Information. Warning:
Adding a C&C server to the allowlist automatically triggers a remediation process to update any affected hosts (in that organization) that have contacted this C&C server. All C&C events related to this allowlisted server will be removed from the affected hosts’ events, and a host threat level recalculation will occur. If the host score changes during this recalculation, a new host event appears describing why it was rescored. For example, “Host threat level updated after C&C server 1.2.3.4 was cleared". Additionally, the server will no longer appear in the list of C&C servers because it has been cleared. |
|
Encrypted Traffic Insights (ETI)
You can specify the IP address or domain names that you want to allowlist from encrypted traffic analysis. Use this tab to add, modify, or delete the allowlists for encrypted traffic analysis.
|
Field |
Guideline |
|---|---|
|
Type |
Select whether you want to specify the IP address or domain name for the allowlist. |
|
IP or Domain |
Enter the IP address or domain name for the allowlist. |
Domain Name System (DNS)
You can specify the domains that you want to allowlist from DNS filtering. Use this tab to add, modify, or delete the allowlists for DNS filtering.
|
Field |
Guideline |
|---|---|
|
URL |
Enter the URL for domain that you want to allowlist. |
|
Comments |
Enter a description that indicates why the domain has been added to the list. |
Reverse Shell
You can specify the IP addresses or domains that you want to allowlist from reverse shell detection. Use this tab to add, modify, or delete the allowlists for reverse shell detection.
|
Field |
Guideline |
|---|---|
|
IP |
Enter the IP address for the allowlist. |
|
URL |
Enter the URL for domain that you want to allowlist. |
Juniper ATP Cloud periodically polls for new and updated content and automatically downloads it to your SRX Series Firewall. You don't need to manually push your allowlist or blocklist files.
