Step 2: Up and Running
Create a Web Portal Login Account for Juniper ATP Cloud
Now that you’ve got the SRX Series Firewall ready to work with Juniper ATP Cloud, let’s log in to the Juniper ATP Cloud Web Portal and enroll your SRX Series Firewall. You'll need to create a Juniper ATP Cloud Web Portal login account, and then enroll your SRX Series Firewall in Juniper ATP Cloud Web Portal.
Have the following information handy before you start enrollment:
-
Your single sign-on or Juniper Networks Customer Support Center (CSC) credentials.
-
A security realm name. For example, Juniper-Mktg-Sunnyvale. Realm names can contain only alphanumeric characters and the dash (“—”) symbol.
-
Your company name.
-
Your contact information.
-
An email address and password. This will be your login information to access the Juniper ATP Cloud management interface.
Let's get going!
Enroll Your SRX Series Firewall
Now that you've created an account, let's enroll your SRX Series Firewall in Juniper ATP Cloud. In this guide, we show you how to enroll your device using the Juniper ATP Cloud Web Portal hosted by Juniper. However, you can also enroll your device using the Junos OS CLI, the J-Web Portal, or the Junos Space Security Director Web Portal. Choose the configuration tool that's right for you:
-
Juniper ATP Cloud Web Portal—The ATP Cloud Web Portal is hosted by Juniper Networks in the cloud. You don’t need to download or install Juniper ATP Cloud on your local system.
-
CLI commands—Starting in Junos OS Release 19.3R1, you can enroll a device to the Juniper ATP Cloud using the Junos OS CLI on your SRX Series Firewall. See Enroll an SRX Series Firewall Using the CLI.
J-Web Portal—The J-Web Portal comes preinstalled on the SRX Series Firewall and can also be used to enroll an SRX Series Firewall to Juniper ATP Cloud. For details, watch this video:
-
Security Director Policy Enforcer—If you are a licensed Junos Space Security Director Policy Enforcer user, you can use Security Director Policy Enforcer to set up and use Juniper ATP Cloud. For more information about using Security Director with Juniper ATP Cloud, see How to Enroll Your SRX Series Firewall in Juniper Advanced Threat Prevention (ATP) Cloud Using Policy Enforcer.
When you enroll an SRX Series Firewall, you establish a secure connection between the Juniper ATP Cloud server. Enrollment also:
-
Downloads and installs certificate authority (CA) licenses onto your SRX Series Firewall
Note:You can enroll SRX1600 and SRX2300 firewalls with Trusted Platform Module (TPM)-based certificates for TLS-based authentication and a secure connection with the Juniper ATP Cloud. For more information about TPM, see Encryption with Trusted Platform Module. Since the TPM-based certificates are used for connections between the SRX Series Firewall and Juniper ATP Cloud, you must allow traffic to the junipersecurity.net domain on ports 8444 and 7444.
-
Creates local certificates
-
Enrolls local certificates with the cloud server
Juniper ATP Cloud requires that both your Routing Engine (control plane) and Packet Forwarding Engine (data plane) are connected to the Internet. You don’t need to open any ports on the SRX Series Firewall to communicate with the cloud server. However, if you have a device in between, such as a firewall, then that device must have ports 80, 8080, and 443 open.
Also, the SRX Series Firewall must be configured with DNS servers in order to resolve the cloud URL.
Enroll Your SRX Series Firewall in Juniper ATP Cloud Web Portal
Here's how to enroll your SRX Series Firewall in Juniper ATP Cloud Web Portal:
Enroll Your SRX Series Firewall in J-Web Portal
You can also enroll an SRX Series Firewall to Juniper ATP Cloud using J-Web. This is the Web interface that comes up on the SRX Series Firewall.
Before enrolling a device:
-
Decide which region the realm you create will cover because you must select a region when you configure a realm.
-
Ensure the device is registered in the Juniper ATP Cloud Web Portal.
-
In CLI mode, configure
set security forwarding-process enhanced-services-modeon your SRX300, SRX320, SRX340, SRX345, and SRX550M devices to open ports and get the device ready to communicate with Juniper ATP Cloud.
Here's how to enroll your SRX Series Firewall using J-Web Portal.
-
Log in to J-Web. For more information, see Start J-Web.
-
(Optional) Configure a proxy profile.
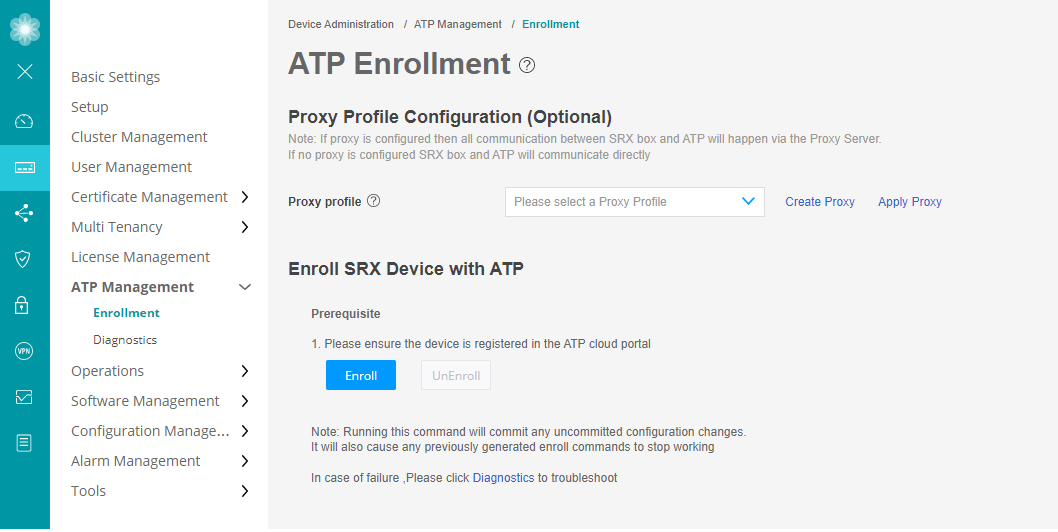
In the J-Web UI, navigate to Device Administration > ATP Management > Enrollment.
The ATP Enrollment page opens.
-
Use either of the following methods to configure the proxy profile:
-
Select an existing proxy profile from the Proxy Profile list.
Note:-
The list displays the existing proxy profiles created using the Proxy Profile page (Security Policies & Objects > Proxy Profiles).
-
The SRX Series Firewall and Juniper ATP Cloud communicate through the proxy server if a proxy profile is configured. Otherwise, they directly communicate with each other
-
-
Click Create Proxy to create a proxy profile.
The Create Proxy Profile page appears.
Complete the configuration:
-
Profile Name—Enter a name for the proxy profile.
-
Connection Type—Select the connection type server (from the list) that the proxy profile uses:
-
Server IP—Enter the IP address of the proxy server.
-
Host Name—Enter the name of the proxy server.
-
-
Port Number—Select a port number for the proxy profile. Range is 0 through 65,535.
-
Click OK.
A new proxy profile is created.
-
-
Click Apply Proxy.
Applying proxy enables the SRX Series Firewall and Juniper ATP Cloud to communicate through the proxy server.
-
Enroll your device to Juniper ATP Cloud.
Click Enroll to open the ATP Enrollment page.
Note:If there are any existing configuration changes, a message appears for you to commit the changes and then to proceed with the enrollment process.
-
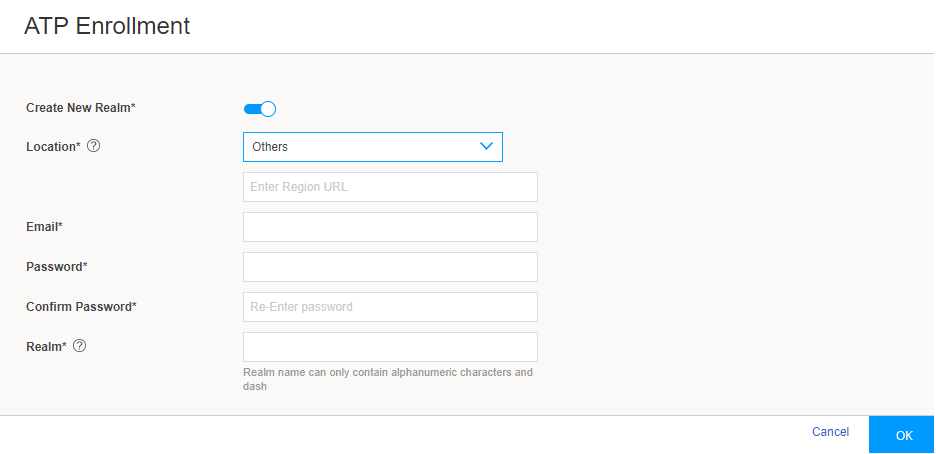
Complete the configuration:
-
Create New Realm—By default, this option is disabled if you have a Juniper ATP Cloud account with an associated license. Enable this option to add a new realm if you do not have a Juniper ATP Cloud account with an associated license.
-
Location—By default, the region is set as Others. Enter the region URL.
-
Email—Enter your e-mail address.
-
Password—Enter a unique string at least eight characters long. Include both uppercase and lowercase letters, at least one number, and at least one special character; no spaces are allowed, and you cannot use the same sequence of characters that are in your e-mail address.
-
Confirm Password—Reenter the password.
-
Realm—Enter a name for the security realm. This should be a name that is meaningful to your organization. A realm name can contain only alphanumeric characters and the dash symbol. Once created, this name cannot be changed.
-
-
Click OK.
The status of the SRX Series Firewall enrollment process is displayed.
Click Diagnostics to troubleshoot any enrollment errors.
Configure Security Polices on the SRX Series Firewall to Use Cloud Feeds
Security policies, such as anti-malware and security-intelligence policies, use
Juniper ATP Cloud threat feeds to inspect files and quarantine hosts that have
downloaded malware. Let's create a security policy,
aamw-policy, for an SRX Series Firewall.
Congratulations! You've completed the initial configuration for Juniper ATP Cloud on your SRX Series Firewall!