Advanced Policy-Based Routing
Advanced policy-based routing (APBR) also known as application-based routing, a new addition to Juniper Networks suite, provides the ability to forward traffic based on applications. For more information, see the following topics:
Understanding Advanced Policy-Based Routing
- Advanced Policy-Based Routing
- Benefits of APBR
- Understanding How APBR Works
- APBR Workflow
- Advanced Policy-Based Routing Options
- Use Case
- Limitations
Advanced Policy-Based Routing
The relentless growth of voice, data, and video traffic and applications traversing on the network requires that networks recognize traffic types to effectively prioritize, segregate, and route traffic without compromising performance or availability.
Advanced policy-based routing is a type of session-based, application-aware routing. This mechanism combines the policy-based routing and application-aware traffic management solution. APBR implies classifying the flows based on applications’ attributes and applying filters based on these attributes to redirect the traffic. The flow-classifying mechanism is based on packets representing the application in use.
APBR implements:
-
Deep packet inspection and pattern-matching capabilities of AppID to identify application traffic or a user session within an application
-
Lookup in ASC for application type and the corresponding destination IP address, destination port, protocol type, and service for a matching rule
If a matching rule is found, the traffic is directed to an appropriate route and the corresponding interface or device.
Benefits of APBR
-
Enables you to define the routing behavior based on applications.
-
Provides more flexible traffic-handling capabilities and offers granular control for forwarding packets based on application attributes.
Understanding How APBR Works
Lets understand about the APBR components before we discuss working of APBR:
-
Create an APBR profile (also referred to as an application profile in this document). The profile includes multiple APBR rules. Each rule includes multiple applications or application groups as match criteria. If the traffic matches any of the application or application groups of a rule, the rule is considered as a match and the profile directs the application traffic to the associated routing-instance.
-
APBR profile associates a routing instance with the APBR rule. When the traffic matches an application profile, the associated static route and next hop defined in the routing instance is used to route the traffic for the particular session.
-
Associate the application profile to the ingress traffic. You can attach APBR profile to an APBR policy and apply as application services for the session.
Lets proceed with understanding about APBR workflow and then discuss about the APBR midstream support and then about the first packet classification in APBR.
APBR Workflow
Figure 1 summarizes APBR behavior prior to Junos OS Release 21.3R1.
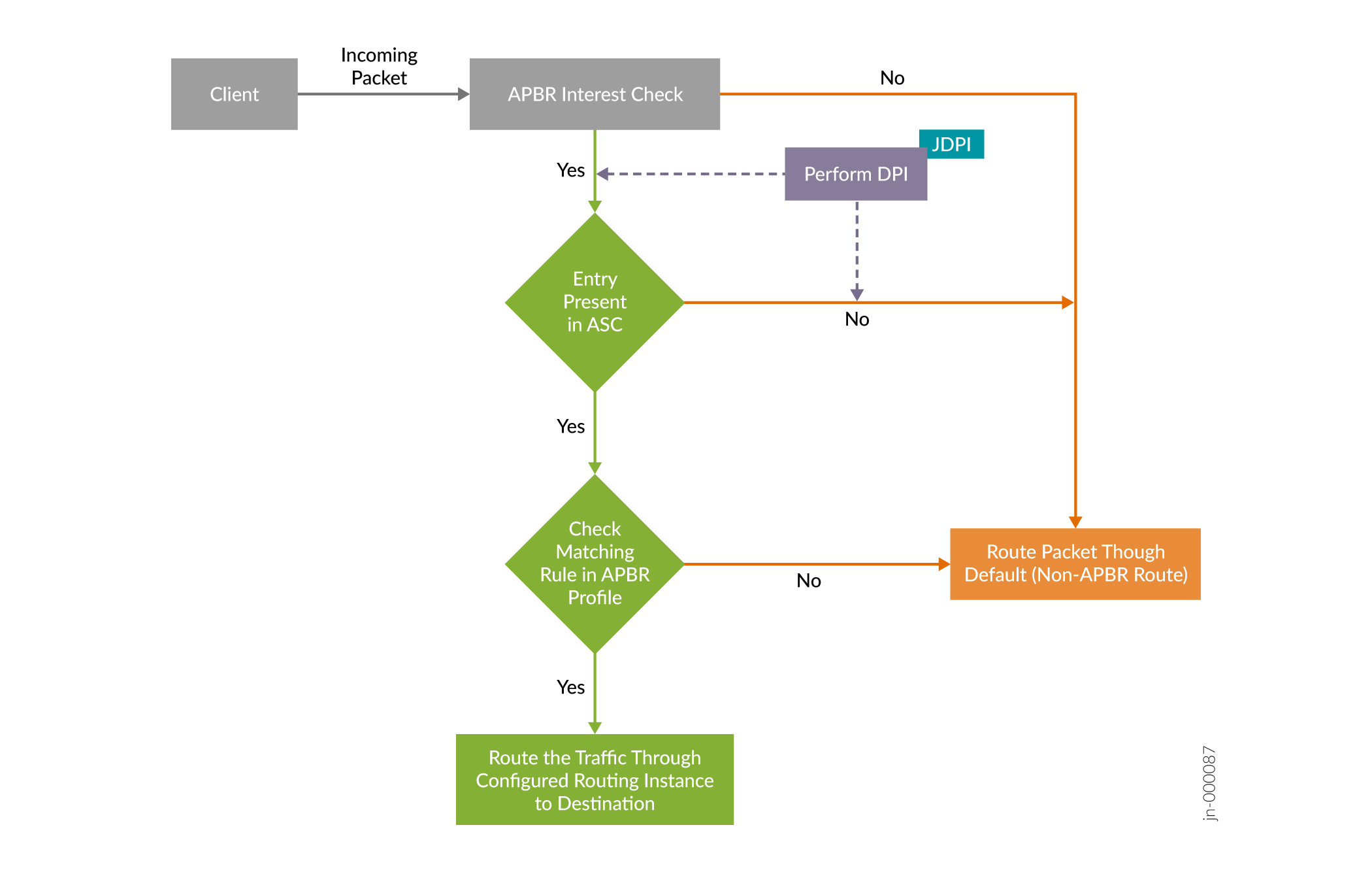
Security device uses DPI to identify attributes of an application and uses APBR to route the traffic over the network. In a service chain, application traffic undergoes DPI before the device applies ABPR. The process of identifying an application using DPI requires analysis of multiple packets. In such cases, initial traffic traverses through a default route (non-APBR route) to reach the destination. The process continues still DPI identifies the application. Once DPI identifies the application, APBR applies rules for the rest of the session. Traffic traverse through the route according to the APBR profile rule.
When you use different NAT pools for source NAT and apply midstream APBR, the source IP address of the session remains same as the one with which the session was using before midstream APBR.
- APBR Midstream Support
- APBR with First Packet Classification
- Benefits of First Packet Classification
- Limitations
APBR Midstream Support
APBR middle of a session (which is also known as midstream support) enables you to apply APBR for a non-cacheable application and also for the first session of the cacheable application. The enhancement provides more flexible traffic-handling capabilities that offer granular control for forwarding packets.
First packet of session goes through midstream re-routing case. That is, when the application is not yet identified, the traffic traverses through a default route (non-APBR route) to the destination. At the same time, DPI continues till application is identified. Once the application is identified, the device applies APBR profile and the rest of the session packets passes through the route as per the rules defined in the APBR profile. The traffic traverses through a non-APBR route till application signatures or ALG identify the application.
When you use different NAT pools for source NAT and apply midstream APBR, the source IP address of the session remains same as the one with which the session was using before midstream APBR.
APBR with First Packet Classification
APBR uses first-packet classification to identify applications in network traffic. APBR identifies applications by examining the very first packet in the traffic flow and then applies application-specific rules to forward the traffic.
The first-packet classification feature works on a subset of cacheable applications, considering the factors such as the availability of DNS cache and static IP mapping.
Figure 2 shows how APBR uses the first-packet classification to get application details.
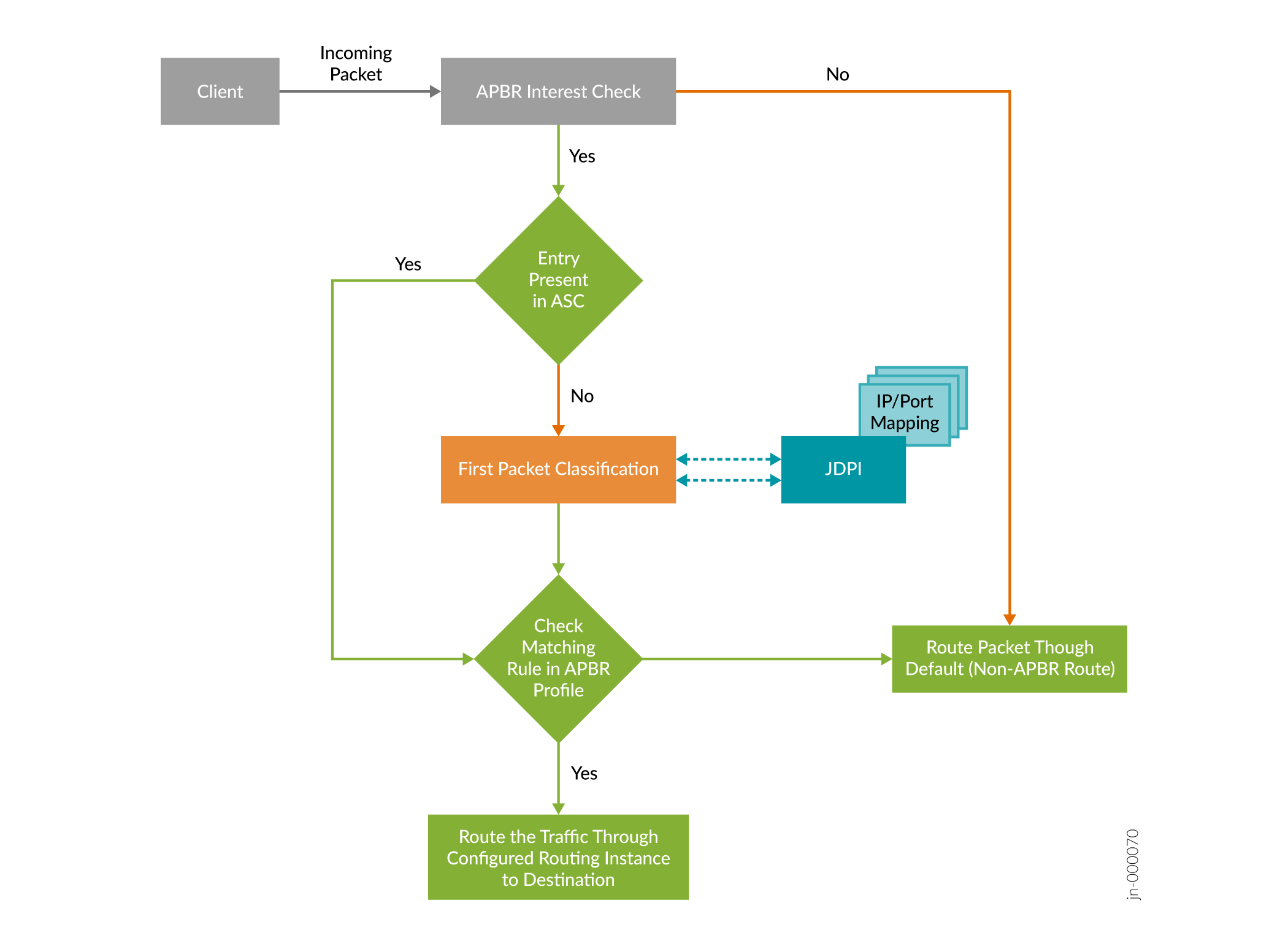
First-packet classification leverages on the repository that includes details such as static IP mapping and ports details of applications. The repository is part of the application signature package (JDPI).
For the first session of a cacheable application, APBR queries the ASC to get application details of the flow. If the entry of the application is not available in the ASC, APBR queries JDPI for the application details. APBR uses the IP address and the port details of the flow for the query. If the application mapping is available, then JDPI returns the details to APBR. After getting application details, APBR searches for the configured profile of the application and routes the packet through the assigned routing instance.
At the same time, JDPI continues to process the packets and updates the ASC (if enabled). For the subsequent flows, APBR performs routing of the traffic based on the application entry present in the ASC for the flow.
With first-packet classification, you can use different NAT pools for source NAT in your APBR configuration for cacheable application.
Benefits of First Packet Classification
With first-packet classification, you can steer the traffic accurately and efficiently over the network, optimizing network link utilization and boosting the performance.
Limitations
-
For non-cacheable applications, when you use different NAT pools for the source NAT and apply APBR in the middle of the session, the source IP address of the session continues to remain same even after applying the APBR in the midstream.
- If IP address and port range details of an application changes, the change might not immediately reflect in the application signature package. You must install the application signature package to get the latest updates of IP address and port ranges.
- In case of micro-services hosting multiple applications such as OFFICE365 on the cloud, it is not possible to have IP addresses and ports ranges at a granular level. For such cases, the first packet classification returns the parent application details. You must configure APBR profile rule to include nested application and the parent application. Example: create APBR rule with dynamic application as MS-TEAMS, and add OFFICE365-CREATE-CONVERSATION in the same rule for first packet classification.
Advanced Policy-Based Routing Options
You can streamline the traffic handling with APBR by using the following options:
-
Limit route change- Some sessions go through continuous classification in the middle of the session as application signatures identify the application. Whenever an application is identified by the application signatures, APBR is applied, and this results in a change in the route of the traffic. You can limit the number of times a route can change for a session by using the
max-route-changeoption of thetunablesstatement.set security advance-policy-based-routing tunables max-route-change valueExample:
[edit]set security advance-policy-based-routing tunables max-route-change 5In this example, you want to limit the number of route changes per session to 5. When there is a change in the route in the middle of the session, this count is reduced to 4. This process continues until the count reaches 0. After that, APBR is not applied in the middle of the session.
If an identified application has an entry in the ASC, then, the count is not reduced for that session, because the session started with the specified route according to the APBR configuration.
-
Terminate session if APBR is bypassed–You can terminate the session if there is a mismatch between zones when APBR is being applied in the middle of the session. When you want to apply APBR in the middle of a session, both new egress interface and existing egress interface must be part of the same zone. If you change the zone for an interface in the middle of a session, then, by default, APBR is not applied, and the traffic continues to traverse through the existing interface. To change this default behavior, you can terminate the session entirely, instead of allowing traffic to traverse through the same route bypassing APBR, by using the
drop-on-zone-mismatchoption of thetunablesstatement.Example:
[edit]set security advance-policy-based-routing tunables drop-on-zone-mismatch -
Enable logging—You can enable logging to record events that occur on the device, for instance, when APBR is bypassed because of a change in the zones for interfaces. You can use the
enable-loggingoption of thetunablesstatement to configure the logging.Example:
[edit]set security advance-policy-based-routing tunables enable-logging -
Enable reverse reroute—For deployments that requires traffic symmetry for ECMP routes, and the incoming traffic needs to switch in the middle of session, the rerouting can be achieved using the option enable-reverse-reroute specific to a security zone as follows:
Example:
[edit]set security zones security-zone zone-name enable-reverse-rerouteWhen the above configuration is enabled for a security zone, where an incoming packet arrives on an interface and has a different outgoing/return interface, a change in the interface is detected and triggers a reroute. A route lookup is performed for the reverse path, and the preference will be given to the interface on which the packet has arrived.
Further processing stops for a particular session when a route lookup fails for the traffic on reverse path.
-
Support for Layer 3 and Layer 4
Applications—APBR supports Layer 3 and Layer 4 custom
applications. You can manually disable Layer 3 and Layer 4 custom application
lookup in APBR by using the following configuration-statement:
user@host# set security advance-policy-based-routing tunables no-l3l4-app-lookup
-
Application Tracking—
You can enable, AppTrack to inspect traffic and collect statistics for application flows in the specified zone. See Understanding Application Tracking for more details.
Use Case
-
When multiple ISP links are used:
-
APBR can be used for selecting high-bandwidth, low-latency links for important applications, when more than one link is available.
-
APBR can be used for creating a fallback link for important traffic in case of link failure. When multiple links are available, and the main link carrying the important application traffic suffers an outage, then the other link configured as the fallback link can be used to carry traffic.
-
APBR can be used for segregating the traffic for deep inspection or analysis. With this feature, you can classify the traffic based on applications that are required to go through deep inspection and audit. If required, such traffic can be routed to a different device.
-
Limitations
APBR has the following limitations:
-
Traffic routing depends on a successful lookup in the Application System Cache (ASC). If the ASC entry is missing, routing fails. For the first session—when the ASC isn't yet populated—traffic uses a default (non-APBR) route. This behavior applies only to older Junos OS versions.
-
APBR does not work if an application signature package is not installed or application identification is not enabled.
APBR with midstream support has the following limitations:
-
APBR works only for forward traffic.
-
APBR does not work for data sessions initiated by an entity from the control session, such as active FTP.
-
When using different NAT pools for source NAT and midstream APBR is applied, the source IP address of the session continues to be the same as the one with which the session has been using before applying the midstream APBR.
-
APBR with midstream support works only when all egress interfaces are in the same zone. Because of this, only the forwarding and virtual routing and forwarding (VRF) routing instances can be used to avail APBR midstream support.
See Also
Example: Configuring Advanced Policy-Based Routing for Application-Aware Traffic Management Solution
This example shows how to configure APBR on an SRX Series Firewall.
Requirements
This example uses the following hardware and software components:
-
Valid application identification feature license installed on an SRX Series Firewall.
-
SRX Series Firewall with Junos OS Release 15.1X49-D60 or later. This configuration example is tested for Junos OS Release 15.1X49-D60.
Overview
In this example, you want to forward HTTP, social networking, and Yahoo traffic arriving at the trust zone to a specific device or interface as specified by the next-hop IP address.
When traffic arrives at the trust zone, it is matched by the APBR profile, and if a matching rule is found, the packets are forwarded to the static route and next hop as specified in the routing instance. The static route configured in the routing table is inserted into the forwarding table when the next-hop address is reachable. All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or interface.
Figure 3 shows the topology used in this configuration example.
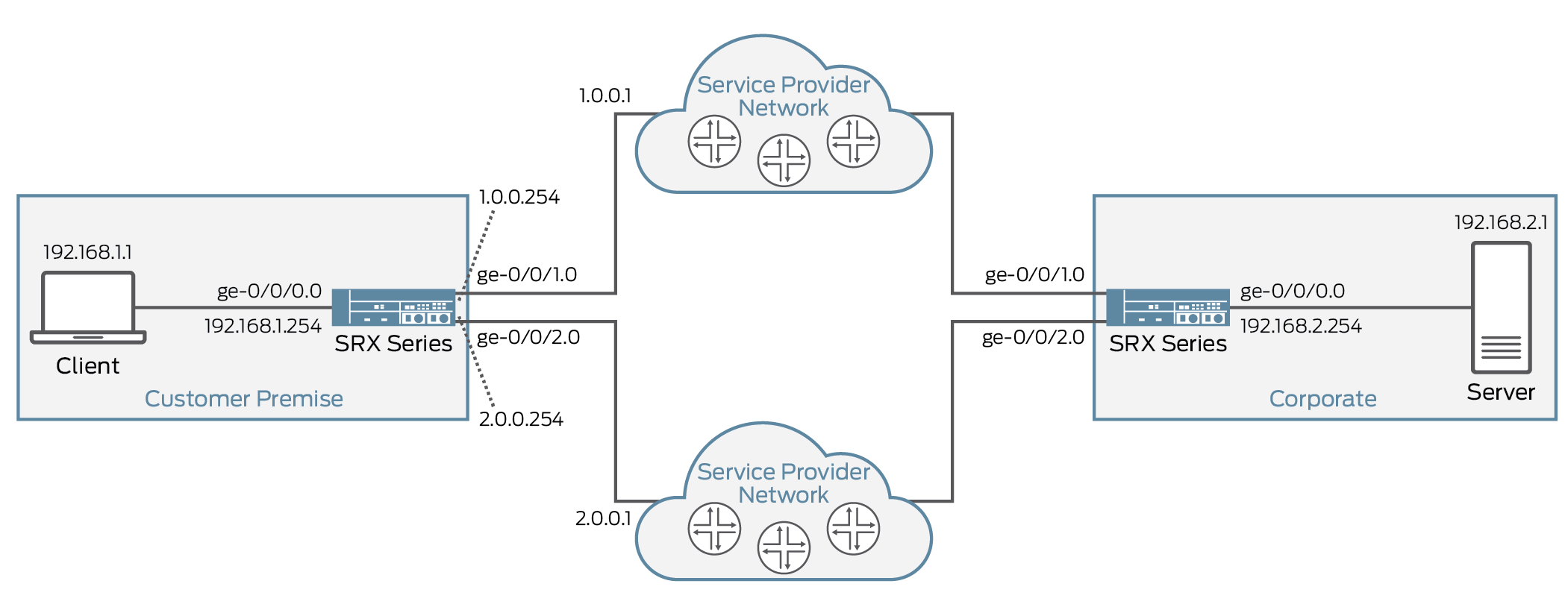
Table 1 provides the details of the parameters used in this example.
|
Parameter |
Name |
Description |
|---|---|---|
|
Routing Instance |
|
Routing instance of type forwarding is used for forwarding the traffic. All the qualified traffic destined for the static route (example: 192.168.0.0/16) is forwarded to the next-hop device (example: with 1.0.0.1 address on its interface). |
|
||
|
RIB Group |
apbr_group |
Name of the routing information base (RIB) (also known as routing table) group. This RIB group is configured to import interface route entries from inet.0, RI1.inet.0, RI2.inet.0, and RI3.inet.0. |
|
APBR Profile |
profile-1 |
Name of the APBR profile. This profile matches applications and application groups and redirects the matching traffic to the specified routing instance (example: R1) for the route lookup. The profile includes multiple rules. |
|
Rule |
|
Define the rules for the APBR profile. Associate the rule with one or more than one application (example: for HTTP) or application groups. If the application matches any of the application or application groups of a rule in a profile, the application profile rule is considered as a match and the traffic will be redirected to the routing instance (example: R1) for the route lookup. |
|
||
|
Zone |
trust |
Specify the source zone to which the APBR profile can be applied. |
To use the APBR for redirecting the traffic based on applications, importing interface routes might be required from one routing instance to another routing instance. You can use one of the following mechanisms:
-
RIB groups to import interface routes
-
Routing policy to import interface routes
When you use routing policy to import interface routes, it might cause management local routes (using fxp0) to leak to non-default routing instance, if the appropriate action is not used for the routing policy. When devices are in chassis cluster mode, such scenarios might result in RG0 failover due to limitations. We recommend not configure fxp0 local route in the routing table of non-default routing instance. Following sample depicts a sample configuration of policy options. Note that the reject action helps in eliminating the routes that are not required. You can use specific routes to reject the fxp0 routes.
policy-statement statement-name {
term 1 {
from {
instance master;
route-filter route-filter-ip-address exact;
}
then accept;
}
then reject;
}
APBR is used for routing the packets in a forward path. For return traffic to arrive over the same path, we recommend to configure the remote SRX Series Firewall with ECMP configuration along with load balance routing policy as shown in the following sample configuration:
user@host> set routing-options static route ip-address next-hop ip-address
user@host> set routing-options static route ip-address next-hop ip-address
user@host> set policy-options policy-statement load-balance-policy then load-balance per-packet
user@host> set routing-options forwarding-table export load-balance-policy
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set routing-instances R1 instance-type forwarding
set routing-instances R1 routing-options static route 192.168.0.0/16 next-hop 1.0.0.1
set routing-instances R2 instance-type forwarding
set routing-instances R2 routing-options static route 192.168.0.0/16 next-hop 2.0.0.1
set routing-options interface-routes rib-group inet apbr_group
set routing-options rib-groups apbr_group import-rib inet.0
set routing-options rib-groups apbr_group import-rib RI1.inet.0
set routing-options rib-groups apbr_group import-rib RI2.inet.0
set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTP
set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1
set security advance-policy-based-routing profile profile1 rule rule-app2 match dynamic-application-group junos:web:social-networking
set security advance-policy-based-routing profile profile1 rule rule-app2 then routing-instance R2
set security zones security-zone trust host-inbound-traffic system-services all
set security zones security-zone trust host-inbound-traffic protocols all
set security zones security-zone trust interfaces ge-0/0/0.0
set security zones security-zone trust advance-policy-based-routing-profile profile1
Configuring Advanced Policy-Based Routing
Step-by-Step Procedure
To configure APBR:
-
Create routing instances.
[edit] user@host# set routing-instances R1 instance-type forwarding user@host# set routing-instances R1 routing-options static route 192.168.0.0/16 next-hop 1.0.0.1 user@host# set routing-instances R2 instance-type forwarding user@host# set routing-instances R2 routing-options static route 192.168.0.0/16 next-hop 2.0.0.1 -
Group one or more routing tables to form a RIB group called apbr_group and import routes into the routing tables.
[edit] set routing-options interface-routes rib-group inet apbr_group set routing-options rib-groups apbr_group import-rib inet.0 set routing-options rib-groups apbr_group import-rib RI1.inet.0 set routing-options rib-groups apbr_group import-rib RI2.inet.0 -
Create the APBR profile and define the rules.
[edit] user@host# set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTP user@host# set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1 user@host# set security advance-policy-based-routing profile profile1 rule rule-app2 match dynamic-application-group junos:web:social-networking user@host# set security advance-policy-based-routing profile profile1 rule rule-app2 then routing-instance R2 -
Apply the APBR profile to the security zone.
[edit] user@host# set security zones security-zone trust host-inbound-traffic system-services all user@host# set security zones security-zone trust host-inbound-traffic protocols all user@host# set security zones security-zone trust interfaces ge-0/0/0.0 user@host# set security zones security-zone trust advance-policy-based-routing-profile profile1
Results
From configuration mode, confirm your configuration
by entering the show routing-instances and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show routing-instances
R1 {
instance-type forwarding;
routing-options {
static {
route 192.168.0.0/16 next-hop 1.0.0.1;
}
}
}
R2 {
instance-type forwarding;
routing-options {
static {
route 192.168.0.0/16 next-hop 2.0.0.1;
}
}
}
[edit]
user@host# show routing-options
interface-routes {
rib-group inet apbr_group;
}
rib-groups {
apbr_group {
import-rib [ inet.0 RI1.inet.0 RI2.inet.0 ];
}
}
[edit]
user@host# show security advance-policy-based-routing
profile profile1 {
rule rule-app1 {
match {
dynamic-application junos:HTTP;
}
then {
routing-instance R1;
}
}
rule rule-app2 {
match {
dynamic-application-group junos:web:social-networking;
}
then {
routing-instance R2;
}
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
advance-policy-based-routing-profile {
profile1;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying Advanced Policy-Based Routing Statistics
Purpose
Display the statistics for APBR such as the number of sessions processed for the application-based routing, number of times the APBR is applied for the session, and so on.
Action
From configuration mode, enter the show security
advance-policy-based-routing statistics command.
user@host> show security advance-policy-based-routing statistics Advance Profile Based Routing statistics: Sessions Processed 9 App rule hit on cache hit 0 App rule hit on HTTP Proxy/ALG 0 Midstream disabled rule hit on cache hit 2 URL cat rule hit on cache hit 0 DSCP rule hit on first packet 2 App and DSCP hit on first packet 0 App rule hit midstream 1 Default rule match 0 Midstream disabled rule hit midstream 1 URL cat rule hit midstream 0 App and DSCP rule hit midstream 0 DSCP rule hit midstream 0 Route changed on cache hits 2 Route changed on HTTP Proxy/ALG 0 Route changed midstream 0 Default rule applied 0 Zone mismatch 0 Drop on zone mismatch 0 Next hop not found 0 Application services bypass 0
Meaning
The command output displays the following details:
-
Sessions processed for the application-based routing.
-
The number of times the application traffic matches the APBR profile and APBR is applied for the session based on different criteria.
-
The number of times AppID was consulted to identify application traffic.
-
The number of instances when there was a mismatch in security zone of the default route and the APBR selected route and the traffic was dropped due to this mismatch.
See show security advance-policy-based-routing statistics for more details.
Verifying Advanced Policy-Based Routing
Purpose
Display information about the sessions and packet flows active on the device, including detailed information about specific sessions.
Action
From configuration mode, enter the show security
flow session command to display information about all currently
active security sessions on the device.
Meaning
The command output displays the following details:
-
All active sessions and packet flows on your device
-
List of incoming and outgoing IP flows, including services
-
Security attributes associated with a flow, for example, the policies that apply to traffic belonging to that flow
-
Session timeout value, when the session became active, how long the session has been active, and if there is active traffic on the session
Configuring Advanced Policy-Based Routing Policies
You can configure advanced policy-based routing (APBR) policies by defining source addresses, destination addresses, and applications as match conditions; and after a successful match, the configured APBR profile is applied as an application services for the session. In the previous releases of Junos OS, an APBR profile could be attached to an incoming security zone of the ingress traffic, and the APBR was applied per security zone basis. Now, with support of APBR policies, you can apply different set of APBR rules on the traffic based on incoming security zone, source address, destination address and application
This enhancement provides more flexible traffic-handling capabilities that offer granular control for forwarding packets.
Supported match criteria includes source addresses, destination addresses, and applications. The applications can be used to support the matching condition based on protocol and Layer 4 ports.
If one or more APBR policy is configured for the security zone, then the policy is evaluated during session creating phase. The policy lookup is terminated once the policy, matching the session, is selected. After a successful match, the APBR profile configured with the APBR policy is used for the session.
How APBR Policy Works?
APBR policies are defined for a security zone. If there is one or more APBR policy associated with a zone, the session that is initiated from the security zone goes through the policy match.
The following sequences are involved in matching the traffic by an APBR policy and applying advanced policy-based routing to forward the traffic, based on the defined parameters/rules:
-
When traffic arrives at the ingress zone, it is matched by the APBR policy rules. The policy match condition include the source address, destination address and application.
-
When the traffic matches the security policy rules, the action of the APBR policy is applied to the traffic. You can enable APBR as an application service in the APBR policy action by specifying the APBR profile name.
-
The APBR profile configuration incudes the set of rules that contains set of dynamic applications and dyamic application groups as match condition. The action part of those rules contain the routing instance through which traffic needs to be forwarded. The routing instance can include configuration of static routs or dynamic learned routes.
-
All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or interface.
APBR policy rules are terminal, which means that once the traffic is matched by a policy, it is not processed further by the other policies.
If an APBR policy has the matching traffic and APBR profile does not have any traffic matching the rule, then the traffic matching the APBR policy traverses through a default routing-instance [inet0] to the destination.
Legacy APBR Profile Support
In older Junos OS releases, APBR profile was applied at security zone-level. With the support for APBR policy, APBR configuration at security-zone level is deprecated future, rather than being immediately removed in order to provide backward compatibility and a chance to bring your configuration into compliance with the new configuration.
However, if you have configured a zone-based APBR, and you attempt to add an APBR policy for the particular security zone, commit might fail. You must delete the zone-based configuration in order to configure the APBR policy for the zone. Similarly if an APBR policy is configured for a security zone, and you attempt to configure zone-based APBR, results in commit error.
Limitation
-
When using specific address or address set in the APBR policy rule, we recommend to use the global address book. Because, zone specific rules might not be applicable for destination address, as the destination zone is not known at time of policy evaluation.
-
Configuring APBR policy for the security zone junos-host zone is not supported.
Example: Configuring Advanced Policy-Based Routing Policies
This example shows how configure an APBR policy and apply the APBR profile on the session that matches the APBR policy rules.
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall with Junos OS Release 18.2R1 or later. This configuration example is tested on Junos OS Release 18.2R1.
-
Valid application identification feature license installed on an SRX Series Firewall.
Overview
In this example, you want to forward HTTP traffic arriving at the trust zone to a specific device or interface as specified by the next-hop IP address.
When traffic arrives at the trust zone, it is matched by the APBR policy. When the traffic matches the policy, the configured APBR rule is applied on the permitted traffic as application services. The packets are forwarded based on the APBR rule to the static route and next hop as specified in the routing instance. The static route configured in the routing table is inserted into the forwarding table when the next-hop address is reachable. All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or interface.
In this example, you must complete the following configurations:
-
Define routing instance and RIB group.
-
Create an ABPR profile.
-
Create a security zone.
-
Create an APBR policy and attach the APBR profile to it.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set routing-instances R1 instance-type forwarding set routing-instances R1 routing-options static route 5.0.0.0/24 next-hop 3.0.0.2 set routing-options interface-routes rib-group inet fbf-group set routing-options rib-groups fbf-group import-rib inet.0 set routing-options rib-groups fbf-group import-rib RI1.inet.0 set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTP set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/1.0 set security advance-policy-based-routing from-zone trust policy SLA1 match source-address any set security advance-policy-based-routing from-zone trust policy SLA1 match destination-address any set security advance-policy-based-routing from-zone trust policy SLA1 match application any set security advance-policy-based-routing from-zone trust policy SLA1 then application-services advance-policy-based-routing-profile profile1
Configuring Advanced Policy-Based Routing
Step-by-Step Procedure
To apply APBR on the traffic matching the APBR policy:
-
Create routing instances.
[edit]
user@host#set routing-instances R1 instance-type forwardinguser@host#set routing-instances R1 routing-options static route 5.0.0.0/24 next-hop 3.0.0.2 -
Group one or more routing tables to form a RIB group called apbr_group and import routes into the routing tables.
[edit]
user@host#set routing-options interface-routes rib-group inet fbf-groupuser@host#set routing-options rib-groups fbf-group import-rib inet.0user@host#set routing-options rib-groups fbf-group import-rib RI1.inet.0 -
Create the APBR profile and define the rules.
[edit]
user@host#set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTPuser@host#set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1 -
Create a security zone.
[edit]
user@host#set security zones security-zone trust host-inbound-traffic system-services alluser@host#set security zones security-zone trust host-inbound-traffic protocols alluser@host#set security zones security-zone trust interfaces ge-0/0/1.0 -
Create an APBR policy and apply the APBR profile to the security zone.
[edit]
user@host#set security advance-policy-based-routing from-zone trust policy SLA1 match source-address anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 match destination-address anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 match application anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 then application-services advance-policy-based-routing-profile profile1
Results
From configuration mode, confirm your configuration
by entering the show routing-instances and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show routing-instances
R1 {
instance-type forwarding;
routing-options {
static {
route 5.0.0.0/24 next-hop 3.0.0.2;
}
}
}
[edit]
user@host# show routing-options
interface-routes {
rib-group inet fbf_group;
}
rib-groups {
fbf_group {
import-rib [ inet.0 RI1.inet.0];
}
}
[edit]
user@host# show security advance-policy-based-routing
from-zone trust {
policy SLA1 {
match {
source-address any;
destination-address any;
application any;
}
then {
application-services {
advanced-policy-based-routing-profile profile1;
}
}
}
}
profile profile1 {
rule rule-app1 {
match {
dynamic-application junos:HTTP;
}
then {
routing-instance R1;
}
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/1.0;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying Advanced Policy-Based Routing Statistics
Purpose
Display the statistics for APBR such as the number of sessions processed for the application-based routing, number of times the APBR is applied for the session, and so on.
Action
From configuration mode, enter the show security
advance-policy-based-routing statistics command.
Sessions Processed 18994 AppID cache hits 18994 AppID requested 0 Rule matches 0 Route changed on cache hits 0 Route changed midstream 0 Zone mismatch 0 Drop on zone mismatch 0 Next hop not found 0
Meaning
The command output displays the following details:
-
Sessions processed for the application-based routing.
-
The number of times the application traffic matches the APBR profile and APBR is applied for the session.
-
The number of times AppID was consulted to identify application traffic.
See show security advance-policy-based-routing statistics for more details.
Verifying APBR Policy Configuration
Purpose
Display information about the APBR policy, associated APBR profile and to display information about the APBR policy hit count.
Action
From configuration mode, enter the show security
advanced-policy-based-routing command.
user@host>
show security advanced-policy-based-routing policy-name SLA1
From zone: trust
Policy: SLA1, State: enabled, Index: 7, Sequence number: 1
Source addresses: any
Destination addresses: any
Applications: any
APBR profile: profile1
From configuration mode, enter the show security
advanced-policy-based-routing hit-count command.
user@host>
show security advanced-policy-based-routing hit-count
Logical system: root-logical-system
Index From zone Name Hit count
1 trust SLA1 3
2 trust SLA2 0
3 trust SLA1 0
Number of policy: 3
Meaning
The command output displays the following details:
-
Details such as status of the policy, associated APBR profile.
-
Display the utility rate of policies according to the number of hits they receive.
Understanding URL Category-Based Routing
URL category-based routing enables you to use URL categories as match criteria in an APBR profile. The URL categories are based on the destination server IP address, and the category identification is leveraged from the Enhanced Web Filtering (EWF) and local Web filtering results obtained from the Content Security module.
URL category-based routing enables you to identify and selectively route Web traffic (HTTP and HTTPS) to a specified destination.
Web filtering classifies websites into the categories according to host, URL, or IP address, and performs the filtering based on those categories. You can configure APBR profiles by specifying a URL category as the match condition in the rule. The APBR profile rule matches the traffic with specified match criteria, and after a successful match, the configured APBR profile is applied as the application service for the session. For example, suppose you want to route all the traffic belonging to a specific website category, such as social media, through a specific next hop. In this case, you can create a new APBR profile with the list of URL categories such as Enhanced_Social_Web_Facebook, Enhanced_Social_Web_Linkedin, Enhanced_Social_Web_Twitter or Enhanced_Social_Web_Youtube or any other custom URL as match criteria in the policy. The traffic that matches one of the defined URL categories in the rule is forwarded using the routes of the specific routing instance.
When an APBR profile matches the traffic against the URL categories included in the rule, APBR queries the Web filtering module to get the URL category details. If the URL category is not available in the URL filtering cache, then the security device sends a request to the private cloud configured with Web filtering for the categorization details. If the traffic does not match any URL categories, the request is uncategorized, and the session undergoes normal processing (non-APBR route).
If the private cloud configured with EWF does not respond to the URL category request within an interval of 3 seconds, then the session undergoes normal processing (non-APBR route).
- Rule Processing in an APBR Profile
- Benefits of URL Category-Based Routing
- Limitations of URL Category-Based Routing
Rule Processing in an APBR Profile
You can provide advanced policy-based routing by classifying the traffic based on applications’ attributes and applying policies based on these attributes to redirect the traffic. To do this, you must define the APBR profile and associate it to a APBR policy. You can create an APBR profile to include multiple rules with either dynamic applications, application groups or both, or a URL category as match criteria. The rules configured in the APBR profile can include either of the following:
-
One or more applications, dynamic applications, or application groups
-
URL category (IP destination address)—EWF or local Web filtering.
In an APBR profile, rule lookup is performed for both the match criteria. If only one match criteria is available, the rule lookup is done based on the available match criteria.
The APBR profile includes the rules to match the traffic with applications or URL categories and the action to redirect the matching traffic to the specified routing instance for the route lookup.
The URL category match is done based on the destination IP address; because of this, URL category-based rule match is terminated at the first packet of the session. As a dynamic application might be identified in the middle of the session, the matching process for the dynamic application rules continues until the process of application identification is complete.
Benefits of URL Category-Based Routing
-
Using URL-based categories enables you to have granular control over Web traffic. The traffic belonging to specific categories of websites is redirected through different paths, and based on the category, it is subjected to further security processing, including SSL decryption for HTTPS traffic.
-
Traffic-handling capabilities based on URL categories enable you to use different paths for selected websites. Using different paths results in better quality of experience (QoE) and also enables you to utilize the available bandwidth effectively.
-
SD-WAN solutions can utilize URL category-based routing in addition to the dynamic application-based routing.
-
URL category-based routing can be used for local Internet breakout solutions as it can work with source NAT configuration changes.
Limitations of URL Category-Based Routing
Using URL categories in an APBR profile has the following limitations:
-
Only the destination IP address is used for the URL category identification in an APBR profile. URL categories based on the host, or on the URL or the SNI field are not supported.
-
You can configure either a dynamic application or a URL category as the match condition in an APBR profile rule. Configuring a rule with both URL category and dynamic application results in a commit error.
Example: Configuring URL Category-Based Routing
This example shows you how to configure URL category-based routing.
- Requirements
- Overview
- Configuring URL Category-Based Routing by Using EWF
- Configuring URL-Based Routing by Using Local Web Filtering
- Verification
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall with Junos OS Release 18.3 R1 or later. This configuration example is tested on Junos OS Release 18.3 R1.
-
Valid application identification feature license installed on the SRX Series Firewall.
-
The Enhanced Web Filtering (EWF) option requires you to purchase a Juniper Networks Web filtering license. No license is required for local Web filtering.
Overview
This example shows how to configure APBR on your SRX Series Firewall to forward social media traffic arriving at the trust zone to a specific device or to an interface using URL category-based routing.
When traffic arrives, it is matched by the APBR profile, and if a matching rule is found, the packets are forwarded to the static route and next-hop IP address as specified in the routing instance. The static route configured in the routing table is added to the forwarding table when the next-hop address is reachable. All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or to an interface.
In this example, you complete the following configurations:
-
Enable either of the following types of Web filtering:
-
Enhanced Web Filtering (EWF)—When you enable EWF on the device, the EWF engine intercepts the HTTP and the HTTPS requests and categorizes the URL into one of the 95 or more predefined categories and also provides site reputation information. See Configuring URL Category-Based Routing by Using EWF.
-
Local Web filtering—When you enable local Web filtering, you can configure custom URL categories with multiple URL lists and apply them to a Content Security Web filtering profile with actions such as permit, permit and log, block, and quarantine. To use local Web filtering, you must create a Web filtering profile and ensure that category custom is part of the profile. See Configuring URL-Based Routing by Using Local Web Filtering.
-
-
Define the routing instances and the routing information base (RIB; also known as routing table group.)
-
Define the APBR profile and associate it to an APBR policy.
Configuring URL Category-Based Routing by Using EWF
This section provides the steps to configure URL category-based routing using EWF. Table 2 provides the details of the parameters used in this example.
|
Parameters |
Name |
Description |
|---|---|---|
|
APBR profile |
apbr-pr1 |
Name of the APBR profile. |
|
APBR policy |
p1 |
Name of the APBR policy. |
|
Rule |
|
Name of the APBR profile rule. The APBR profile rule matches the traffic to the defined URL categories and redirects the matching traffic to the specified routing instance (example: RI1) for the route lookup. |
|
Category |
Enhanced_Social_Web_Facebook |
Category defined in the APBR profile rule for matching the traffic. |
|
Routing instance |
|
Routing instance of type forwarding is used for forwarding the traffic. All the qualified traffic destined for the static route (with IP address 1.0.0.254/8) is forwarded to the next-hop device (with IP address 1.0.0.1). |
|
RIB group |
apbr_group |
Name of the RIB group. The RIB group shares interface routes with the forwarding routing instances. To ensure that the next hop is resolvable, interface routes from the main routing table are shared through a RIB group with the routing tables specified in the routing instances. |
To perform URL category-based routing using EWF, you must complete the following procedures:
- Enabling Enhanced Web Filtering
- Defining the Routing Instance and the RIB Group
- Configuring the APBR Profile
- Configuring the APBR Policy and Attaching the APBR Profile
Enabling Enhanced Web Filtering
Step-by-Step Procedure
To use URL categories as match criteria in an APBR profile, you must enable EWF in Content Security.
The EWF option requires you to purchase a Juniper Networks Web filtering license. No license is required for local Web filtering.
-
Enable EWF by specifying the Web filtering type as
juniper-enhanced.[edit]
user@host#set security utm feature-profile web-filtering type juniper-enhanced -
Set the cache size as 500 and cache timeout as 1800 seconds for the configured EWF engine.
[edit]
user@host#set security utm feature-profile web-filtering juniper-enhanced cache size 500user@host#set security utm feature-profile web-filtering juniper-enhanced cache timeout 1800For more information about EWF configuration, see Enhanced Web Filtering (EWF).
Defining the Routing Instance and the RIB Group
Step-by-Step Procedure
Define routing instance and the RIB group.
-
Create the routing instance to forward traffic to the different next hops. In this step, you configure the static route 1.0.0.254/8, and the next-hop address as 1.0.0.1.
[edit]
user@host#set routing-instances RI1 instance-type forwardinguser@host#set routing-instances RI1 routing-options static route 1.0.0.254/8 next-hop 1.0.0.1 -
Create a RIB group.
[edit]
user@host#set routing-options interface-routes rib-group inet apbr_groupuser@host#set routing-options rib-groups apbr_group import-rib inet.0user@host#set routing-options rib-groups apbr_group import-rib RI1.inet.0Interface routes from the main routing table (inet.0) are shared through a RIB group with the routing table specified in the routing instance RI1.inet.0.
Configuring the APBR Profile
Step-by-Step Procedure
Create a rule for the Facebook applications and forward the matching traffic to the routing instance RI1.
-
Create the APBR profile and define the match criteria for the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr1 rule rule-social-nw match category Enhanced_Social_Web_FacebookThe APBR profile rule matches the traffic to the defined URL category—that is, the Facebook application in this example.
-
Specify the action for the traffic matching the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr1 rule rule-social-nw then routing-instance RI1In this step, you are specifying that the traffic that matches the apbr-pr1 rule is to be redirected to the routing instance RI1.
Configuring the APBR Policy and Attaching the APBR Profile
Step-by-Step Procedure
Associate the application profile to the APBR policy to enable URL category-based routing.
-
Define the APBR policy. Specify the policy match condition as
anyfor the source address, destination address, and application.[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p1 match source-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p1 match destination-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p1 match application anyWhen traffic arrives, it is matched by the APBR policy rules.
-
Attach the APBR profile to the policy.
[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p1 then application-servicesadvance-policy-based-routing-profile apbr-pr1When the traffic matches the APBR policy (p1) rules, the APBR profile apbr-pr1 is applied to the traffic as the action of the APBR policy. The traffic that matches the Facebook application is redirected to the routing instance RI1 according to the APBR profile rule rule-social-nw.
Results
From configuration mode, confirm your configuration
by entering the show commands. If the output does not display
the intended configuration, repeat the configuration instructions
in this example to correct it.
[edit security]
user@host# show advance-policy-based-routing
profile apbr-pr1 {
rule rule-social-nw {
match {
category Enhanced_Social_Web_Facebook;
}
then {
routing-instance RI1;
}
}
}
from-zone trust {
policy p1 {
match {
source-address any;
destination-address any;
application any;
}
then {
application-services {
advance-policy-based-routing-profile apbr-pr1;
}
}
}
}
[edit]
user@host# routing-options
interface-routes {
rib-group inet apbr_group;
}
rib-groups {
apbr_group {
import-rib [ inet.0 RI1.inet.0 ];
}
}
[edit]
user@host# show routing-instances
RRI1 {
instance-type forwarding;
routing-options {
static {
route 1.0.0.254/8 next-hop 1.0.0.1;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Configuring URL-Based Routing by Using Local Web Filtering
This section provides the steps to configure URL category-based routing by using local Web filtering.
Table 3 provides the details of the parameters used in this example.
|
Parameters |
Name |
Description |
|---|---|---|
|
APBR profile |
apbr-pr2 |
Name of the APBR profile. |
|
APBR policy |
p2 |
Name of the APBR policy. |
|
Rule |
|
Name of the APBR profile rule. The APBR profile rule matches the traffic to the defined URL categories and redirects the matching traffic to the specified routing instance (example: RI2) for the route lookup. |
|
Custom Category (URL Pattern) |
203.0.113.0 203.0.113.10 |
Category defined in the APBR profile rule for matching the traffic. |
|
Routing instance |
|
Routing instance of type forwarding is used for forwarding the traffic. All the qualified traffic destined for the static route (with IP address 5.0.0.10) is forwarded to the next-hop device (with IP address 9.0.0.1). |
|
RIB group |
apbr_group2 |
Name of the RIB group. The RIB group shares interface routes with the forwarding routing instances. To ensure that the next hop is resolvable, interface routes from the main routing table are shared through a RIB group with the routing tables specified in the routing instances. |
To perform URL category-based routing using local Web filtering, you must complete the following procedures:
- Enabling Local Web Filtering
- Defining the Routing Instance and the RIB Group
- Configuring the APBR Profile
- Configuring APBR Policy and Attaching the APBR Profile
Enabling Local Web Filtering
Step-by-Step Procedure
To use URL categories as match criteria in an APBR profile, you must enable local Web filtering in Content Security.
-
Enable local Web filtering by specifying the Web filtering type as
juniper-local.[edit]
user@host#set security utm feature-profile web-filtering type juniper-local -
Create custom objects and URL pattern lists.
[edit]
user@host#set security utm custom-objects url-pattern local1 value 203.0.113.0user@host#set security utm custom-objects url-pattern local1 value 203.0.113.10In this step, a pattern that matches the IP address 203.0.113.0 or 203.0.113.10 on HTTP is created.
-
Configure the custom URL category list.
user@host#set security utm custom-objects custom-url-category custom value local1The URL category specified in this example is custom, where you can add URL lists. In this step, you are adding the URL list
local1, which includes the patterns matching the addresses 203.0.113.1 and 203.0.113.10 that are created in step 2. -
Configure a Web filtering profile.
user@host#set security utm feature-profile web-filtering juniper-local profile P1 category custom action permitA Web filtering profile includes a user-defined category with a permit action.
For more information about local Web filtering configuration, see Local Web Filtering.
Defining the Routing Instance and the RIB Group
Step-by-Step Procedure
Define the routing instance and the RIB group.
-
Create the routing instance to forward traffic to the different next hops. In this example, you configure the static route 5.0.0.0/10, using the next-hop address of 9.0.0.1.
[edit]
user@host#set routing-instances RI2 instance-type forwardinguser@host#set routing-instances RI2 routing-options static route 5.0.0.0/16 next-hop 9.0.0.1 -
Create a RIB group.
[edit]
user@host#set routing-options interface-routes rib-group inet apbr_group2user@host#set routing-options rib-groups apbr_group2 import-rib inet.0user@host#set routing-options rib-groups apbr_group2 import-rib RI2.inet.0Interface routes from the main routing table (inet.0) are shared through a RIB group with the routing table specified in the routing instance (RI2.inet.0).
Configuring the APBR Profile
Step-by-Step Procedure
Create a rule to forward the traffic matching the custom URL pattern to the routing instance RI2.
-
Create the APBR profile and define the match criteria for the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr2 rule rule2 match category customThe APBR profile rule matches the traffic to the defined custom URL category—that is, traffic with URL patterns matching the addresses 203.0.113.1 and 203.0.113.10 in this example.
-
Specify the action for the traffic matching the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr2 rule rule2 then routing-instance RI2In this step, you are specifying that the traffic that matches the rule is to be redirected to the routing instance RI2.
Configuring APBR Policy and Attaching the APBR Profile
Step-by-Step Procedure
Associate the APBR profile to the APBR policy to enable URL category-based routing.
-
Define the APBR policy. Specify the policy match condition as
anyfor the source address, destination address, and application.[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p2 match source-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p2 match destination-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p2 match application anyWhen traffic arrives, is matched by the APBR policy rules.
-
Attach the APBR profile to the policy.
[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p2 then application-services advance-policy-based-routing-profile apbr-pr2When the traffic matches the APBR policy (p2) rules, the APBR profile apbr-pr2 is applied to the traffic as the action of the APBR policy. The traffic that matches the Facebook application is redirected to the routing instance RI2 according to the APBR profile rule rule2.
Results
From configuration mode, confirm your configuration
by entering the show commands. If the output does not display
the intended configuration, repeat the configuration instructions
in this example to correct it.
[edit security]
user@host# show advance-policy-based-routing
profile apbr-pr2 {
rule rule2 {
match {
category custom;
}
then {
routing-instance RI2;
}
}
}
from-zone trust {
policy p2 {
match {
source-address any;
destination-address any;
application any;
}
then {
application-services {
advance-policy-based-routing-profile apbr-pr2;
}
}
}
}
[edit]
user@host# show routing-options
interface-routes {
rib-group inet apbr_group2;
}
rib-groups {
apbr_group2 {
import-rib [ inet.0 RI2.inet.0 ];
}
}
[edit]
user@host# show routing-instances
RI2 {
instance-type forwarding;
routing-options {
static {
route 5.0.0.0/10 next-hop 9.0.0.1;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying APBR Statistics
Purpose
Display the statistics for APBR, such as the number of sessions processed for the application-based routing, the number of times the APBR is applied for the session, and so on.
Action
From configuration mode, enter the show security
advance-policy-based-routing statistics command.
user@host> show security advance-policy-based-routing
statistics
Advance Profile Based Routing statistics: Session Processed: 5529 ASC Success: 3113 Rule match success: 107 Route modified: 107 AppID Requested: 2416
Meaning
The command output displays the following details:
-
Sessions processed for the application-based routing
-
The number of times the presence of an entry in the application system cache (ASC) is found
-
The number of times the application traffic matches the APBR profile and APBR is applied for the session
-
The number of times application identification (AppID) was consulted to identify application traffic
-
The number of times the APBR is applied for the session
Bypassing Application Services in an APBR Rule
You can create an APBR profile to include multiple rules with either dynamic applications, application groups or both, or a URL category as match criteria on security devices. URL category-based routing enables you to identify and selectively route Web traffic (HTTP and HTTPS) to a specified destination or to another device where further inspection on the Web traffic is required. In such cases, you can select not to apply or bypass application services on the session that is to be forwarded to the device for further inspection.
You can bypass application services for a session that is re-routed using the APBR rule.
The following sequences are involved in bypassing the application services:
-
APBR uses the application details to look for a matching rule in the APBR profile (application profile).
-
If a matching APBR rule is found, the traffic is redirected to the specified routing instance for the route lookup.
-
If you configure the option to bypass application services on the sessions in an APBR rule, then an attempt is done to bypass the application services to the session.
-
A log message is generated or updated to indicate the bypassing of the application services on the session.
You can bypass the application services including security policies, application quality of service (AppQoS), Juniper ATP Cloud, IDP, Security Intelligence (SecIntel) and Content Security using the APBR rule.
For bypass to be effective, it is required that the APBR rule is matched in the first packet. If the rule is matched after the first packet, and the rule has a bypass option configured, the bypass option is ignored and the application services are not bypassed.
ALG Service is not bypassed due to this feature as bypassing the ALG could potentially result in the correlated (data) session not being matched to appropriate security policy.
Example: Bypassing Application Services by Using APBR Rule
This example shows you how to bypass application services on the session using APBR rule. Using URL category-based routing, you can identify and selectively route Web traffic (HTTP and HTTPS) to a specified destination or to another device. Here, you can configure to bypass the application services on the session where further inspection on the Web traffic could be performed.
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall with Junos OS Release 19.1R1 or later. This configuration example is tested on Junos OS Release 19.1R1.
-
Valid application identification feature license installed on the SRX Series Firewall.
Before you begin:
-
Define routing instance and RIB group.
-
Appropriate security policies to enforce rules for the transit traffic, to specify what traffic can pass through the device, and the actions that need to take place on the traffic as it passes through the device.
Overview
This example shows how to configure APBR on your SRX Series Firewall to forward social media traffic arriving at the trust zone to a specific device or to an interface using URL category-based routing and bypass the application services on the same session.
In this example, you complete the following configurations:
-
Define the APBR profile and associate it to a APBR policy. The APBR profile includes the rules to match the traffic with applications and URL categories.
-
Next, specify the action of the APBR profile rule. That is, to redirect the matching traffic to the specified routing instance for the route lookup.
-
Specify application bypass option for the matching traffic.
When traffic arrives, it is matched by the APBR profile, and if a matching rule is found, the packets are forwarded to the static route. All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or to an interface. Since you configured application bypass option for the matching traffic, the traffic forwarded to the specific device at next-hop address is not applied with application services.
Configuration
This section provides steps to configure URL category-based routing by using enhanced Web filtering (EWF) and also enable by passing application services on the traffic.
- Enabling Enhanced Web Filtering
- Configuring the APBR Rule
- Configuring APBR Policy and Attaching the APBR Profile
Enabling Enhanced Web Filtering
Step-by-Step Procedure
To use URL categories as match criteria in an APBR profile, you must enable EWF in Content Security.
The EWF option requires you to purchase a Juniper Networks Web filtering license. No license is required for local Web filtering.
-
Enable EWF by specifying the Web filtering type as
juniper-enhanced.[edit]
user@host#set security utm feature-profile web-filtering type juniper-enhanced -
Set the cache size as 500 and cache timeout as 1800 seconds for the configured EWF engine.
[edit]
user@host#set security utm feature-profile web-filtering juniper-enhanced cache size 500user@host#set security utm feature-profile web-filtering juniper-enhanced cache timeout 1800For more information about EWF configuration, see Enhanced Web Filtering (EWF).
Configuring the APBR Rule
Step-by-Step Procedure
Create a rule for the Facebook applications and forward the matching traffic to the routing instance RI1.
-
Create the APBR profile and define the match criteria for the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr1 rule rule-social-nw match category Enhanced_Social_Web_FacebookThe APBR profile rule matches the traffic to the defined URL category—that is, the Facebook application in this example.
-
Specify the action for the traffic matching the URL category.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr1 rule rule-social-nw then routing-instance RI1In this step, you are specifying that the traffic that matches the apbr-pr1 rule is to be redirected to the routing instance RI1.
-
Specify the bypassing application services for the traffic matching the APBR rule.
[edit]
user@host#set security advance-policy-based-routing profile apbr-pr1 rule rule-social-nw then application-services-bypassIn this step, you are specifying that the traffic that matches the apbr-pr1 rule is to be bypassed application services.
Configuring APBR Policy and Attaching the APBR Profile
Step-by-Step Procedure
Associate the application profile to the APBR policy to enable URL category-based routing.
-
Define the APBR policy. Specify the policy match condition as
anyfor the source address, destination address, and application.[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p1 match source-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p1 match destination-address anyuser@host#set security advance-policy-based-routing from-zone trust policy p1 match application anyWhen traffic arrives, it is matched by the APBR policy rules.
-
Attach the APBR profile to the policy.
[edit]
user@host#set security advance-policy-based-routing from-zone trust policy p1 then application-services advance-policy-based-routing-profile apbr-pr1When the traffic matches the APBR policy (p1) rules, the APBR profile apbr-pr1 is applied to the traffic as the action of the APBR policy. The traffic that matches the Facebook application is redirected to the routing instance RI1 according to the APBR profile rule rule-social-nw. Also application services are bypassed for the session as specified in APBR profile rule rule-social-nw.
Results
From configuration mode, confirm your configuration
by entering the show commands. If the output does not display
the intended configuration, repeat the configuration instructions
in this example to correct it.
[edit security]
user@host# show advance-policy-based-routing
profile apbr-pr1 {
rule rule-social-nw {
match {
category Enhanced_Social_Web_Facebook;
}
then {
routing-instance RI1;
application-services-bypass;
}
}
}
from-zone trust {
policy p1 {
match {
source-address any;
destination-address any;
application any;
}
then {
application-services {
advance-policy-based-routing-profile apbr-pr1;
}
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying APBR Statistics
Purpose
Display the statistics for APBR, such as the number of sessions processed for the application-based routing, the number of times the APBR is applied for the session, and so on.
Action
From configuration mode, enter the show security
advance-policy-based-routing statistics command.
user@host> show security advance-policy-based-routing
statistics
Advance Profile Based Routing statistics: Sessions Processed 110 AppID cache hits 110 AppID requested 0 Rule matches 2 Route changed on cache hits 1 Route changed midstream 1 Zone mismatch 0 Drop on zone mismatch 0 Next hop not found 0 Application Services Bypass 1
Meaning
The command output displays the following details:
-
Sessions processed for the application-based routing
-
The number of times the presence of an entry in the application system cache (ASC) is found
-
The number of times the application traffic matches the APBR profile and APBR is applied for the session
-
The number of times application identification (AppID) was consulted to identify application traffic
-
The number of times the APBR is applied for the session
-
The number of times the application services are bypassed for the session
Support for User Source Identity in APBR Policies
You can configure advanced policy-based routing (APBR) policies by defining user source identity as one of the match criteria along with source addresses, destination addresses, and applications. After a successful match, the APBR profile configured with the APBR policy is applied as an application service for the session. The source identity enables you to leverage user information stored in a repository such as user identification table (UIT).
The source-identity field specifies the users and roles to which the policy applies. When the source-identity field is specified in a policy as a matching criterion, user and role information must be retrieved before policy lookup can proceed. Using the source-identity option as a matching criterion in the APBR policy is optional. If the value in the source-identity field is configured as any or there is no entry in the source-identity field, user information and role information are not required and the other match criteria are used for policy lookup.
You can specify one or more users or user roles using the source-identity field with the following keywords:
-
authenticated-user—Users that have been authenticated.
-
unauthenticated-user—Users that have not been authenticated.
-
any—All users regardless of authentication status. If the source-identity field is not configured or is set to any, only other matching criteria are used for matching
-
unknown-user—Users that can not be authenticated due to an authentication server disconnection, such as a power outage.
On your security device, the user identification table (UIT) provides user and role information for an active user who has already been authenticated. Each entry in the table maps an IP address to an authenticated user and any role.
UIT contains the IP address, username, and role information for all authenticated user. The entries in the user identification table are ordered by IP address.
On your security device, the type of UIT supported is local authentication table. The local authentication table serves as the authentication source for the information required by APBR policies. Local authentication table is a static UIT created on the device either manually or programmatically using CLI commands. All users included in the local authentication table are considered authenticated users. To retrieve user and role information, a search is performed in the authentication table for an entry with an IP address corresponding to the traffic. When a matching IP address is found, user and role information is retrieved from the table entry and are associated with the traffic. If not found, the user is classified as an unauthenticated user.
User and role information can be created on the device manually or ported from a third-party authentication server, but the data in the local authentication table is not updated in real time.
During APBR policy lookup, if a user and user role that are configured in the APBR policy, but the entry is not present in the local authentication table, then the policy does not match. Hit count value that display the utility rate of security policies according to the number of hits they receive, does not increment.
For more information on user role retrieval and the policy lookup process, see User Role Firewall Security Policies.
Benefits
-
Enables you to define the routing behavior at more granular levels to ensure safe enforcement of policy on the application traffic traversing the network.
-
Provides more flexible traffic-handling capabilities and offers granular control for forwarding packets based on the roles and business requirements of users.
Local Authentication Table
You can manage the local authentication table with CLI commands that add or delete entries. You can add IP addresses, usernames, and roles from a third-party authentication source to the local authentication table programmatically using CLI commands. If an authentication source defines users and groups, the groups can be configured as roles and associated with the user as usual.
Use the following command to add an entry to a local authentication table. The entries in the table are entered using the IP address.
user@host > request security user-identification local-authentication-table add user user-name ip-address ip-address role [role-name role-name ]
Example:
user@host > request security user-identification local-authentication-table add user-name user1 ip-address 2.2.2.2 roles role1
Use the following command to delete an entry by IP address or by username.
user@host > request security user-identification local-authentication-table delete (ip-address | user-name)
Use the following command to clear the local authentication table:
user@host > clear security user-identification local-authentication-table
Use the following command to display the content of the local authentication table:
user@host > show security user-identification local-authentication-table all (brief | extensive)
For more information, see Local Authentication Table.
Example: Configuring Advanced Policy-Based Routing Policies with Source Identity
This example shows how to configure an APBR policy with source identity and how to apply the APBR profile on a session that matches the APBR policy rules.
Requirements
This example uses the following hardware and software components:
-
An SRX Series Firewall with Junos OS Release 19.1R1 or later. This configuration example is tested on Junos OS Release 19.1R1.
-
Valid application identification feature license installed on an SRX Series Firewall.
Overview
In this example, you want to forward HTTP traffic arriving at the trust zone to a specific device or interface as specified by the next-hop IP address.
When traffic arrives at the trust zone, it is matched by the APBR policy. When the traffic matches the policy, the configured APBR rule is applied on the permitted traffic as application services. The packets are forwarded based on the APBR rule to the static route and next hop as specified in the routing instance. The static route configured in the routing table is inserted into the forwarding table when the next-hop address is reachable. All traffic destined for the static route is transmitted to the next-hop address for transit to a specific device or interface.
In this example, you must complete the following configurations:
-
Define a routing instance and a RIB group.
-
Create an ABPR profile.
-
Create an APBR policy and attach the APBR profile to it.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set routing-instances R1 instance-type forwarding set routing-instances R1 routing-options static route 5.0.0.0/24 next-hop 3.0.0.2 set routing-options interface-routes rib-group inet fbf-group set routing-options rib-groups fbf-group import-rib inet.0 set routing-options rib-groups fbf-group import-rib RI1.inet.0 set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTP set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/1.0 set security advance-policy-based-routing from-zone trust policy SLA1 match source-address any set security advance-policy-based-routing from-zone trust policy SLA1 match destination-address any set security advance-policy-based-routing from-zone trust policy SLA1 match application any set security advance-policy-based-routing from-zone trust policy SLA1 match source-identity identity-1 set security advance-policy-based-routing from-zone trust policy SLA1 then application-services advance-policy-based-routing-profile profile1
Configuring Advanced Policy-Based Routing
Step-by-Step Procedure
To add an entry to a local authentication table.
-
Enter the username, IP address, and user role details.
user@host>request security user-identification local-authentication-table add user-name user1 ip-address 2.2.2.2 roles role1
Step-by-Step Procedure
To apply APBR on traffic that matches the APBR policy:
-
Create routing instances.
[edit]
user@host#set routing-instances R1 instance-type forwardinguser@host#set routing-instances R1 routing-options static route 5.0.0.0/24 next-hop 3.0.0.2 -
Group one or more routing tables to form a RIB group called apbr_group and import routes into the routing tables.
[edit]
user@host#set routing-options interface-routes rib-group inet fbf-groupuser@host#set routing-options rib-groups fbf-group import-rib inet.0user@host#set routing-options rib-groups fbf-group import-rib RI1.inet.0 -
Create the APBR profile and define the rules.
[edit]
user@host#set security advance-policy-based-routing profile profile1 rule rule-app1 match dynamic-application junos:HTTPuser@host#set security advance-policy-based-routing profile profile1 rule rule-app1 then routing-instance R1 -
Create a security zone.
[edit]
user@host#set security zones security-zone trust host-inbound-traffic system-services alluser@host#set security zones security-zone trust host-inbound-traffic protocols alluser@host#set security zones security-zone trust interfaces ge-0/0/1.0 -
Create an APBR policy and apply the APBR profile to the security zone.
[edit]
user@host#set security advance-policy-based-routing from-zone trust policy SLA1 match source-address anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 match destination-address anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 match application anyuser@host#set security advance-policy-based-routing from-zone trust policy SLA1 match source-identity identity-1user@host#set security advance-policy-based-routing from-zone trust policy SLA1 then application-services advance-policy-based-routing-profile profile1
Results
From configuration mode, confirm your configuration
by entering the show routing-instances and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show routing-instances
R1 {
instance-type forwarding;
routing-options {
static {
route 5.0.0.0/24 next-hop 3.0.0.2;
}
}
}
[edit]
user@host# show routing-options
interface-routes {
rib-group inet fbf_group;
}
rib-groups {
fbf_group {
import-rib [ inet.0 RI1.inet.0];
}
}
[edit]
user@host# show security advance-policy-based-routing
from-zone trust {
policy SLA1 {
match {
source-address any;
destination-address any;
application any;
source-identity identity-1;
}
then {
application-services {
advanced-policy-based-routing-profile profile1;
}
}
}
}
profile profile1 {
rule rule-app1 {
match {
dynamic-application junos:HTTP;
}
then {
routing-instance R1;
}
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/1.0;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying APBR Policy Configuration
Purpose
Display information about the APBR policy, associated APBR profile and to display information about the APBR policy hit count.
Action
From configuration mode, enter the show security
advance-policy-based-routing detail command.
user@host>show security advance-policy-based-routing detail Policy: SLA1, State: enabled, Index: 5 Policy Type: Configured Sequence number: 1 From zone: trust Source addresses: any-ipv4(global): 0.0.0.0/0 any-ipv6(global): ::/0 Destination addresses: any-ipv4(global): 0.0.0.0/0 any-ipv6(global): ::/0 Application: any IP protocol: 0, ALG: 0, Inactivity timeout: 0 Source port range: [0-0] Destination port range: [0-0] APBR-Profile: profile1Source identities: identity-1
Meaning
The command output displays the source identity details
in the Source identities field.
Using DSCP as Match Criteria in APBR Rules
This topic includes the following sections:
Introduction
Application identification techniques rely on deep packet inspection (DPI). There are some cases where DPI engine might not be able to identify the application, for example—encrypted traffic. If you apply APBR rules on such traffic, the traffic undergoes normal processing without APBR functionality applied on it.
You can DSCP values in an APBR rule as match criteria to perform APBR functionality on the DSCP-tagged traffic. You can configure DSCP value in addition to the other matching criteria of the APBR rule such as dynamic application, and dynamic application group.
By configuring the DSCP value in an APBR rule, you can extend the APBR service to the traffic with the DSCP markings.
Use Case
You can use APBR rules with DSCP as match criteria for the encrypted traffic.
Limitation
-
Support not available for configuring rules with DSCP value and URL category in a single APBR profile.
APBR Rule Lookup When Using a DSCP Value as Match Criteria
In a APBR rule, you can configure a DSCP value or dynamic applications or combination of both.
If you have configured both DSCP and dynamic application in a APBR rule, the rule is considered as match if the traffic matches all the criteria specified in the rule. If there are multiple DSCP values present in the APBR rule, then if any one criteria matches, it is considered as match.
A APBR profile can contain multiple rules, each rule with a variety of match conditions.
In case of multiple APBR rules in a APBR profile, the rule lookup uses the following priority order:
-
Rule with DSCP + dynamic application
-
Rule with dynamic application
-
Rule with DSCP value
If a APBR profile contains multiple rules, the system performs rule lookup and applies the rule in the following order:
-
System applies the DSCP-based rules for the first packet of the session.
-
System continues to check if any application information available either from DPI classification or application system cache (ASC).
-
In the middle of the session, if DPI identifies a new application, the system performs a rule lookup and applies new rule (application-based rule or DSCP-based rule or combination of both) as applicable.
-
Identifying application and rule lookup continues till the DPI identifies an application as the final application or maximum reroute value is reached.
-
If the rule lookup does not match any rule, no further action is taken.
Lets understand how APBR performs rule lookup and applies the rules with the following two examples:
Example 1
In this example, you configure three APBR rules with— one with DSCP value 30, next rule with application as HTTP, and the third rule with both DSCP value as 30 and application as HTTP. Configure maximum route change value as 1 (default value).
Table 4 shows how APBR performs rule lookup and applies the rules.
|
Session |
Traffic Type |
ASC Cache |
DPI Classification |
Matching Rule |
|---|---|---|---|---|
|
First session |
DSCP=30 |
NA |
NA |
Rule 1 |
|
Midstream session |
DSCP=30 Application = HTTP |
Yes |
HTTP |
Rule 3 The traffic switches because rule lookup matched the new rule. When traffic switches based on rule change in the middle of the session, the count for maximum route change reduces to 0. Now no further route change takes place in this scenario. |
Example 2
In this example, you configure three APBR rules with— one with DSCP value 30, next rule with DSCP value 60, and the third rule with both DSCP value as 30 and application as HTTP.
Table 5 shows how APBR performs rule lookup and applies the rules.
|
Session |
Traffic Type |
ASC Cache |
DPI Classification |
Matching Rule |
|---|---|---|---|---|
|
First session |
DSCP=30 |
NA |
NA |
Rule 1 |
|
Midstream session |
DSCP=60 Application = HTTP |
Yes |
DSCP=60 HTTP |
Rule 2 Rule 3 does not match with traffic because DSCP value is changed from 30 to 60 in midstream. |
Configure APBR Rules with DSCP Values as Match Criteria
This example shows how to configure APBR rules with DSCP values as match criteria.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set interfaces ge-0/0/1 unit 0 family inet address 192.0.2.1/24 set interfaces ge-0/0/2 unit 0 family inet address 192.0.3.1/24 set interfaces ge-0/0/3 unit 0 family inet address 192.0.4.1/24 set security zones security-zone untrust interfaces ge-0/0/1.0 set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 family inet address 4.0.0.1/24 set routing-instances RI1 instance-type forwarding set routing-instances RI1 routing-options static route 192.0.0.0/16 next-hop 192.0.2.254 set routing-instances RI2 instance-type forwarding set routing-instances RI2 routing-options static route 192.0.0.0/16 next-hop 192.0.3.254 set routing-instances RI3 instance-type forwarding set routing-instances RI3 routing-options static route 192.0.0.0/16 next-hop 192.0.4.254 set routing-options rib-groups apbr-group import-rib inet.0 set routing-options rib-groups apbr-group import-rib RI1.inet.0 set routing-options rib-groups apbr-group import-rib RI2.inet.0 set routing-options rib-groups apbr-group import-rib RI3.inet.0 set routing-options interface-routes rib-group inet apbr-group set security advance-policy-based-routing profile p1 rule R1 match dynamic-application junos:HTTP set security advance-policy-based-routing profile p1 rule R1 then routing-instance RI1 set security advance-policy-based-routing profile p1 rule R2 match dscp 56 set security advance-policy-based-routing profile p1 rule R2 match dynamic-application junos:HTTP set security advance-policy-based-routing profile p1 rule R2 then routing-instance RI2 set security advance-policy-based-routing profile p1 rule R3 match dscp 46 set security advance-policy-based-routing profile p1 rule R3 then routing-instance RI3 set security zones security-zone trust advance-policy-based-routing-profile p1 set security zones security-zone trust advance-policy-based-routing-profile p1
Step-by-Step Procedure
Configure APBR rule with DSCP and dynamic application as match criteria.
-
Define security zones and interfaces.
[edit]
user@host#set interfaces ge-0/0/1 unit 0 family inet address 192.0.2.1/24user@host#set interfaces ge-0/0/2 unit 0 family inet address 192.0.3.1/24user@host#set interfaces ge-0/0/3 unit 0 family inet address 192.0.4.1/24user@host#set security zones security-zone untrust host-inbound-traffic system-services alluser@host#set security zones security-zone untrust host-inbound-traffic protocols alluser@host#set security zones security-zone untrust interfaces ge-0/0/1.0user@host#set security zones security-zone untrust interfaces ge-0/0/2.0user@host#set security zones security-zone untrust interfaces ge-0/0/3.0 -
Define interface and security zones for the ingress interface connecting the client device.
[edit]
user@host#set security zones security-zone trust host-inbound-traffic system-services alluser@host#set security zones security-zone trust host-inbound-traffic protocols alluser@host#set security zones security-zone trust interfaces ge-0/0/0.0user@host#set interfaces ge-0/0/0 unit 0 family inet address 4.0.0.1/24 -
Configure the routing instances.
[edit]
user@host#set routing-instances RI1 instance-type forwardinguser@host#set routing-instances RI1 routing-options static route 192.0.0.0/16 next-hop 192.0.2.254user@host#set routing-instances RI2 instance-type forwardinguser@host#set routing-instances RI2 routing-options static route 192.0.0.0/16 next-hop 192.0.3.254user@host#set routing-instances RI3 instance-type forwardinguser@host#set routing-instances RI3 routing-options static route 192.0.0.0/16 next-hop 192.0.4.254 -
Group one or more routing tables to form a RIB group called apbr-group and import routes into the routing tables.
[edit]
user@host#set routing-options rib-groups apbr-group import-rib inet.0user@host#set routing-options rib-groups apbr-group import-rib RI1.inet.0user@host#set routing-options rib-groups apbr-group import-rib RI2.inet.0user@host#set routing-options rib-groups apbr-group import-rib RI3.inet.0user@host#set routing-options interface-routes rib-group inet apbr-group -
Define the APBR rule with dynamic application HTTP as match criteria.
[edit]
user@host#set security advance-policy-based-routing profile p1 rule R1 match dynamic-application junos:HTTPuser@host#set security advance-policy-based-routing profile p1 rule R1 then routing-instance RI1APBR routes the traffic matching the HTTP application to the routing instance RI1.
-
Create another rule for DSCP and HTTP application.
[edit]
user@host#set security advance-policy-based-routing profile p1 rule R2 match dscp 56user@host#set security advance-policy-based-routing profile p1 rule R2 match dynamic-application junos:HTTPuser@host#set security advance-policy-based-routing profile p1 rule R2 then routing-instance RI2APBR routes the traffic matching the DSCP value 56 to the routing instance RI2.
-
Define one more rule with DSCP value 46.
[edit]
user@host#set security advance-policy-based-routing profile p1 rule R3 match dscp 46user@host#set security advance-policy-based-routing profile p1 rule R3 then routing-instance RI3user@host#set security zones security-zone trust advance-policy-based-routing-profile p1APBR routes the traffic matching the DSCP value 46 to the routing instance RI3.
-
Apply the APBR profile to the security zone.
[edit]
user@host#set security zones security-zone trust advance-policy-based-routing-profile p1
Results
From configuration mode, confirm your configuration by entering
the show security advance-policy-based-routing, show
routing-instances, and show security zones commands.
If the output does not display the intended configuration, repeat
the configuration instructions in this example to correct it.
[edit]user@host#show interfaces ge-0/0/0 { unit 0 { family inet { address 4.0.0.1/24; } } } ge-0/0/1 { unit 0 { family inet { address 192.0.2.1/24; } } } ge-0/0/2 { unit 0 { family inet { address 192.0.3.1/24; } } } ge-0/0/3 { unit 0 { family inet { address 192.0.4.1/24; } } }
[edit]user@host#show routing-instances RI1 { instance-type forwarding; routing-options { static { route 192.0.0.0/16 next-hop 192.0.2.254; } } } RI2 { instance-type forwarding; routing-options { static { route 192.0.0.0/16 next-hop 192.0.3.254; } } } RI3 { instance-type forwarding; routing-options { static { route 192.0.0.0/16 next-hop 192.0.4.254; } } }
[edit]user@host#show security advance-policy-based-routing profile p1 { rule R1 { match { dynamic-application junos:HTTP; } then { routing-instance RI1; } } rule R2 { match { dynamic-application junos:HTTP; dscp 56; } then { routing-instance RI2; } } rule R3 { match { dscp 46; } then { routing-instance RI3; } } }
[edit]user@host#show security zones security-zone untrust { host-inbound-traffic { system-services { all; } protocols { all; } } interfaces { ge-0/0/1.0; ge-0/0/2.0; ge-0/0/3.0; } } security-zone trust { host-inbound-traffic { system-services { all; } protocols { all; } } interfaces { ge-0/0/0.0; } advance-policy-based-routing-profile { p1; } }
Once you complete the configuration, enter commit from configuration mode.
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall with Junos OS Release 19.3R1 or later. This configuration example is tested on Junos OS Release 19.3R1.
-
Any supported SRX Series Firewall.
-
Valid application identification feature license installed on the SRX Series Firewall.
Overview
In this example, you want to forward HTTP traffic and traffic tagged with DSCP value 56 and DSCP value 46 to a specific device or interfaces at Site 1, Site 2, and Site 3 respectively. Security device forwards the traffic based on an application or DSCP value to a preferred route by using APBR feature.
When traffic arrives at the trust zone, APBR matches the traffic with configured APBR profile rules. If the traffic matches the rule, APBR forwards the traffic to the specific destination as defined in the APBR rule.
For example, you configure APBR to route the traffic to different destinations based on the type of the application as specified below:
-
Rule 1—Forward HTTP traffic from Client 1 to the Site 1 using next-hop address 192.0.2.254.
-
Rule 2—Forward traffic with DSCP value 56 and HTTP application to Site 2 using next-hop device 192.0.3.254.
-
Rule 3—Forward traffic with DSCP value 46 to Site 3 using the next-hop device 192.0.4.254.
Figure 4 shows the topology used in this example.
Table 6 provides the details of the parameters used in this example.
|
Parameter |
Value |
Associated Parameter |
Description |
|---|---|---|---|
|
APBR profile |
P1 |
Name of the APBR profile. |
Configure the profile with rules to match the applications and DSCP values and specify destination (example: routing-instances) for the matching traffic. |
|
RIB group |
RI1.inet.0 |
Associated routing instance—RI1 |
Configure the RIB group to import interface route entries from inet.0, RI1.inet.0, RI2.inet.0, and RI3.inet.0. |
|
RI1.inet.2 |
Associated routing instance—RI2 |
||
|
RI1.inet.3 |
Associated routing instance—RI3 |
||
|
Routing instance |
RI1 |
|
Configure the routing instances to include next-hop IP address. APBR forwards the qualified traffic destined for the static route to the next-hop device address in Site 1, Site 2, and Site 3. |
|
RI2 |
|
||
|
RI3 |
|
||
|
APBR Rule |
R1 |
|
Configure the APBR rules and specify dynamic application or DSCP values as matching criteria. APBR forwards the matching traffic to the associated routing instance. |
|
R2 |
|
||
|
R3 |
|
Verification
Verifying Advanced Policy-Based Routing Statistics
Purpose
Display the statistics for APBR such as the number of sessions processed for the application-based routing, number of times the APBR is applied for the session, and so on.
Action
From configuration mode, enter the show security
advance-policy-based-routing statistics command.
user@host>
show security advance-policy-based-routing statistics
Advance Profile Based Routing statistics: Sessions Processed 0 App rule hit on cache hit 0 App rule hit on HTTP Proxy/ALG 0 URL cat rule hit on cache hit 0 DSCP rule hit on first packet 0 App and DSCP hit on first packet 0 App rule hit midstream 0 URL cat rule hit midstream 0 App and DSCP rule hit midstream 0 DSCP rule hit midstream 0 Route changed on cache hits 0 Route changed on HTTP Proxy/ALG 0 Route changed midstream 0 Zone mismatch 0 Drop on zone mismatch 0 Next hop not found 0 Application services bypass 0
Meaning
The command output displays the following details:
-
Sessions processed for the application-based routing.
-
The number of times the application traffic or DSCP-tagged traffic matches the APBR profile.
-
The number of times traffic is switched to different route in the midstream.
Verifying Advanced Policy-Based Routing Sessions
Purpose
Display information about the sessions and packet flows active on the device, including detailed information about specific sessions.
Action
From configuration mode, enter the show security
flow session command to display information about all currently
active security sessions on the device.
Meaning
The command output displays the following details:
-
All active sessions and packet flows on your device.
-
List of incoming and outgoing IP flows, including services.
-
Security attributes associated with a flow, for example, the policies that apply to traffic belonging to that flow.
-
Session timeout value, when the session became active, how long the session has been active, and if there is active traffic on the session.
Disable APBR Midstream Routing for Specific APBR Rule
- Why Selectively Disabling the Midstream Routing is Required?
- Selectively Disabling APBR In Midstream
Why Selectively Disabling the Midstream Routing is Required?
Some sessions go through continuous classification in the middle
of the session as application signatures identify the application.
Whenever an application is identified by the application signatures,
APBR is applied, and this results in a change in the route of the
traffic. You can limit the number of times a route can change for
a session by using the max-route-change option. If you
set this option to 0, the APBR is disabled for the particular session.
However, this option also disables the APBR functionality globally
on your device which might not be required.
Selectively Disabling APBR In Midstream
You can selectively turn-off the APBR service in the middle of a session for a specific APBR rule, while retaining the global APBR functionality for the remaining sessions. When you disable midstream routing for a specific APBR rule, the system does not apply midstream APBR for corresponding application traffic, and routes the traffic through a non-APBR route.
To selectively disable the midstream APBR, you can configure
the APBR rule with disable midstream routing option (disable-midstream-routing) at [edit security advance-policy-based-routing profile apbr-profile-name rule apbr-rule-name
] hierarchy level.
Table 7 shows the behavior of the selectively disabling midstream APBR option.
|
Traffic Type |
Traffic Matches APBR Rule |
Result |
|---|---|---|
|
New Sessions (when the cache entry does not exists for the session) |
With |
Session uses the default route. |
|
The |
||
|
Without |
Apply midstream APBR |
|
|
Apply APBR till the last application is identified or as defined
in the |
||
|
Established Sessions (when the cache entry exists for the session) |
With |
Apply APBR. |
|
Disengage APBR for the further sessions. That is—even if further applications are identified in the session after the cache hit, APBR is not applied to them. |
||
|
Without |
Apply APBR. |
|
|
Continue to apply APBR till the last application is identified
or as defined in the |
Disabling midstream routing for a specific APBR rule will reroute the application traffic back through a default non-APBR route.
Using Disable Midstream Routing Option to Selectively Disable APBR for Specific APBR Rule
If you have already configured an APBR rule for a specific application, and now you want to selectively disable the APBR midstream routing, use the following option:
user@host# set security advance-policy-based-routing profile apbr-profile-name rule apbr-rule-name disable-midstream-routing
Example:
[edit security advance-policy-based-routing]
user@host#
show
profile p1 {
rule r1 {
disable-midstream-routing;
match {
dynamic-application junos:YAHOO;
}
then {
routing-instance RI1;
}
}
}
from-zone trust {
policy policy-1 {
match {
source-address any;
destination-address any;
application any;
}
then {
application-services {
advance-policy-based-routing-profile profile-1;
}
}
}
}
Use the show security advance-policy-based-routing statistics command to verify the APBR status:
Advance Profile Based Routing statistics: Sessions Processed 9 App rule hit on cache hit 0 App rule hit on HTTP Proxy/ALG 0 Midstream disabled rule hit on cache hit 2 URL cat rule hit on cache hit 0 DSCP rule hit on first packet 2 App and DSCP hit on first packet 0 App rule hit midstream 1 Default rule match 0 Midstream disabled rule hit midstream 1 URL cat rule hit midstream 0 App and DSCP rule hit midstream 0 DSCP rule hit midstream 0 Route changed on cache hits 2 Route changed on HTTP Proxy/ALG 0 Route changed midstream 0 Default rule applied 0 Zone mismatch 0 Drop on zone mismatch 0 Next hop not found 0 Application services bypass 0
In this sample output, the fields Midstream disabled rule
hit on cache hit and Midstream disabled rule hit midstream indicate the number of times a route remains unchanged in the middle
of a session after the rule with defined application is matched and
the number of times the rule with a disabled midstream has a matching
entry in the application system cache (ASC).
Default Mechanism to Forward the Traffic Through APBR Rule
You can configure “any” as match criteria for dynamic application in a APBR rule. The criteria “any” acts as a wildcard and applies to any dynamic application.
Example
user@hots#set security advance-policy-based-routing profile p1 rule R1 match dynamic-application anyuser@hots#set security advance-policy-based-routing profile p1 rule R1 then routing-instance RI1
Application traffic that match the other parameters in a APBR rule matches the policy regardless of the dynamic application type.
Note the following while using the any keyword
for dynamic applications in an APBR rule:
-
You can configure only one APBR rule with
anykeyword for the dynamic application in an APBR profile. -
Configuring a same APBR rule with DSCP and URL-based categories with the
anykeyword is not supported. -
APBR rule with dynamic applications configured as
anyis applied only during the first packet processing. -
Configuring a same APBR rule with dynamic application as
anyand other dynamic applications or dynamic application groups is not supported.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
