SRX 시리즈 방화벽의 서비스 상태 모니터링
웹 필터링, 침입 탐지 및 애플리케이션 보안 상태를 확인하려면 다음 단계를 따르십시오.
Juniper Mist™ 클라우드 포털의 주니퍼 네트웍스® SRX 시리즈 방화벽에서 다음 기능의 서비스 상태를 모니터링할 수 있습니다.
-
강화된 웹 필터링(EWF)
-
침입 탐지 및 방지(ID
-
애플리케이션 보안
이 기능을 사용하려면 SRX 시리즈 방화벽에 대한 유효한 라이선스가 필요합니다. 라이선스 요구 사항 및 설치에 대한 자세한 내용은 주니퍼 라이선싱 사용자 가이드를 참조하십시오.
SRX 시리즈 방화벽에서 명령을 사용하여 show system license 만료 날짜가 있는 라이선스 이름을 표시합니다.
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 2022-04-28 00:00:00 UTC
idp-sig 0 1 0 2022-04-28 00:00:00 UTC
dynamic-vpn 0 2 0 permanent
av_key_sophos_engine 0 1 0 2022-04-28 00:00:00 UTC
logical-system 1 3 0 permanent
wf_key_websense_ewf 0 1 0 2022-04-28 00:00:00 UTC
remote-access-ipsec-vpn-client 0 2 0 permanent
Licenses installed:
License identifier: DemoLabJUNOS386107562
License version: 4
Valid for device: CV4720AF0436
Customer ID: Juniper Internal
Features:
av_key_sophos_engine - Anti Virus with Sophos Engine
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
anti_spam_key_sbl - Anti-Spam
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
idp-sig - IDP Signature
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
wf_key_websense_ewf - Web Filtering EWF
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
EWF 상태 확인
EWF(Enhanced Web Filtering) 구성 상태를 확인하려면 다음을 수행합니다.
- CLI 운영 모드에서 SRX 시리즈 방화벽에서 EWF가 활성화되었는지 확인합니다.
user@host> show security utm web-filtering status UTM web-filtering status: Server status: no-config root@00c52c4c3204>
Server status: no-config는 EWF가 구성되지 않았음을 나타냅니다.
- [edit] 계층 수준에서 CLI를 사용하여 SRX 시리즈 방화벽에서 EWF를 구성합니다. 구성 모드를 사용하고 구성을 커밋합니다.
메모:
랩 환경에서 다음 구성을 캡처하여 참조용으로만 제공했습니다. 사용자 고유의 구성은 사용자 환경의 특정 요구 사항에 따라 달라질 수 있습니다.
[edit] set system syslog file utm-log any any set system syslog file utm-log match RT_UTM set security utm custom-objects url-pattern blacklist value https://*.poki.com set security utm custom-objects custom-url-category restricted value blacklist set security utm default-configuration anti-virus type sophos-engine set security utm default-configuration anti-virus scan-options uri-check set security utm default-configuration anti-virus scan-options timeout 30 set security utm default-configuration anti-virus sophos-engine sxl-timeout 5 set security utm default-configuration web-filtering url-blacklist restricted set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering juniper-enhanced server host rp.cloud.threatseeker.com set security utm default-configuration web-filtering juniper-enhanced server port 80 set security utm default-configuration web-filtering juniper-enhanced default permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Games action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Gambling action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Abused_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Material action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Command_and_Control action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Payloads action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bot_Networks action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Compromised_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Emerging_Exploits action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Files_Containing_Passwords action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Hacking action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Illegal_or_Questionable action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Keyloggers action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_iFrame action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Web_Sites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Militancy_and_Extremist action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Mobile_Malware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Network_Errors action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Newly_Registered_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pay_to_Surf action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Phishing_and_Other_Frauds action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Damaging_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Exploited_Documents action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Unwanted_Software action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Racism_and_Hate action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Spyware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Unauthorized_Mobile_Marketplaces action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Alcohol_and_Tobacco action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Application_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bandwidth action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Computer_Security action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Custom_Encrypted_Payloads action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Elevated_Exposure action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment_Video action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_File_Download_Servers action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Freeware_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Instant_Messaging action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Auctions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Radio_and_TV action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Intolerance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Lingerie_and_Swimsuit action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Marijuana action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Media_File_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Message_Boards_and_Forums action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions_and_Occult_and_Folklore action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Nudity action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Parked_Domain action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Peer_to_Peer_File_Sharing action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Personals_and_Dating action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Prescribed_Medications action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Private_IP_Addresses action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Choice action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Life action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Proxy_Avoidance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex_Education action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Social_Networking_and_Personal_Sites action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Surveillance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Tasteless action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Violence action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Web_and_Email_Spam action log-and-permit set security utm utm-policy custom-utm-policy anti-virus http-profile junos-av-defaults set security utm utm-policy custom-utm-policy web-filtering http-profile wf-home
-
CLI 운영 모드에서 상태를 확인합니다.
user@host> show security utm web-filtering status UTM web-filtering status: Server status: Juniper Enhanced using Websense server UP
이제 상태가 서버 상태: Websense 서버 UP을 사용하여 Juniper 향상으로 변경됩니다. 이 상태는 장치에서 EWF 서비스가 활성화되었음을 나타냅니다.
- 그림 1과 같이 Juniper Mist 클라우드 포털에서 상태를 확인할 수 있습니다.
침입 탐지 및 방지(IDP) 상태 확인
침입 탐지 및 방지(IDP)를 구성하기 전에 다음 단계에 따라 침입 탐지 및 방지(IDP) 보안 패키지를 다운로드하고 설치해야 합니다.
-
request security idp security-package download 명령의 지침을 사용하여 침입 탐지 및 방지(IDP) 패키지를 다운로드합니다.
-
request security idp security-package install 명령의 지침을 사용하여 패키지를 설치합니다.
이 예에서는 다음과 같이 다운로드하여 설치하는 침입 탐지 및 방지(IDP) 템플릿을 사용합니다.
- 명령의 request security idp security-package download policy-templates 지침에 따라 침입 탐지 및 방지(IDP) 템플릿을 다운로드합니다.
- 명령의 request security idp security-package install policy-templates 지침에 따라 템플릿을 설치합니다.
- 템플릿 커밋 스크립트를 활성화합니다.
[edit] user@host-1# set system scripts commit file templates.xsl
다운로드한 템플릿은 Junos OS 구성 데이터베이스에 저장되며 계층 수준의 CLI
[edit security idp idp-policy]에서 사용할 수 있습니다. 사전 정의된 정책을 활성 정책으로 활성화합니다. 이 예에서는 정책을 활성 정책으로 사용합니다
Recommended.[edit] user@host-1# set security idp default-policy Recommended user@host-1# set security idp active-policy Recommended
- 구성에서 침입 탐지 및 방지(IDP) 정책을 활성화합니다. 다음 코드 조각은 구성 예를 보여줍니다.
set security idp idp-policy idpengine rulebase-ips rule 1 match from-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match source-address any set security idp idp-policy idpengine rulebase-ips rule 1 match to-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match destination-address any set security idp idp-policy idpengine rulebase-ips rule 1 match application junos-echo set security idp idp-policy idpengine rulebase-ips rule 1 match attacks predefined-attack-groups Critical
- 운영 모드에서 다음 명령을 사용하여 침입 탐지 및 방지(IDP) 정책 상태를 확인합니다.
- 권장 침입 탐지 및 방지(IDP) 정책:
show security idp policies: - 정책 이름:
show security idp policies - 침입 탐지 및 방지(IDP) 상태:
show security idp status
- 그림 1과 같이 Juniper Mist Cloud 포털에서 침입 탐지 및 방지(IDP) 상태를 확인합니다.
- 권장 침입 탐지 및 방지(IDP) 정책:
애플리케이션 보안 구성
SRX 시리즈 방화벽에서 애플리케이션 보안은 유효한 라이선스가 있는 경우 기본적으로 활성화됩니다. OC 팀은 모든 장치에 최신 애플리케이션 서명 버전이 있는지 확인합니다. 버전을 변경하거나 사용자 지정 버전을 설치하려면 Predefined Application Signatures for Application Identification을 참조하십시오.
Juniper Mist Cloud 포털에서 보안 서비스 상태 보기
Juniper Mist 클라우드 포털의 SECURITY SERVICES(보안 서비스 ) 패널에서 보안 서비스의 상태를 볼 수 있습니다. 표 1 상태의 세부 정보를 제공합니다.
| 보안 서비스 | 표시 상태 | 의미 |
|---|---|---|
| 증권 시세 표시기 | 사용 | Websense 서버에 대한 연결이 작동 중입니다. |
| 비활성화 | 디바이스에 EWF가 구성되어 있지 않습니다. | |
| 솜털 | Websense 서버에 대한 연결이 끊어졌습니다. | |
| 침입 탐지 및 방지(ID | 사용 | 침입 탐지 및 방지(IDP) 구성되고 침입 탐지 및 방지(IDP) 정책이 적용됩니다. |
| 비활성화 | 침입 탐지 및 방지(IDP)가 구성되지 않았습니다. 이 경우 침입 탐지 및 방지(IDP) 정책 이름이 비어 있습니다. | |
| 애플리케이션 보안 | 사용 | 애플리케이션 보안이 활성화되어 있습니다. 애플리케이션 서명 버전이 표시됩니다. |
| 비활성화 | 애플리케이션 보안이 활성화되지 않았습니다. 애플리케이션 서명 버전이 0으로 표시됩니다. |
그림 1 은 클라우드 포털의 보안 서비스 상태를 보여 Juniper Mist.
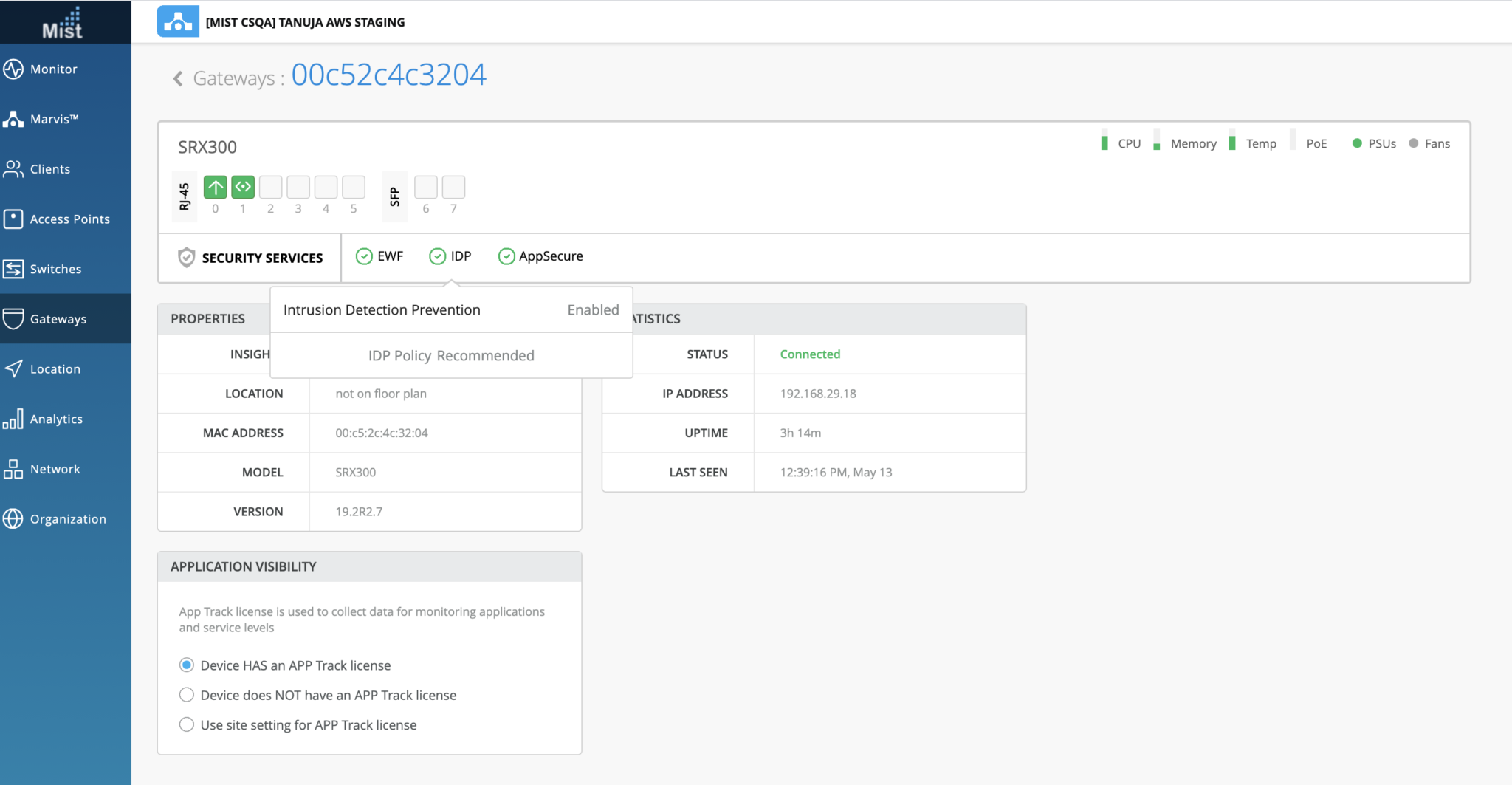
유효한 라이선스의 유무, 보안 서비스의 상태와 같은 세부 정보를 얻을 수 있습니다.
"service_status": {
"idp_status": "disabled", // either "enabled" or "disabled"
"idp_policy": "", // if the above is disabled this will be empty
"appid_status": "disabled", // either "enabled" or "disabled"
"ewf_status": "disabled", // either "enabled" (websense up), "disabled" (no config) or "down" (websense down)
"appid_version": 0 // this will be 0 if appid_status is disabled, as we then don't check the version number
},
