ルーティングエンジンの保護
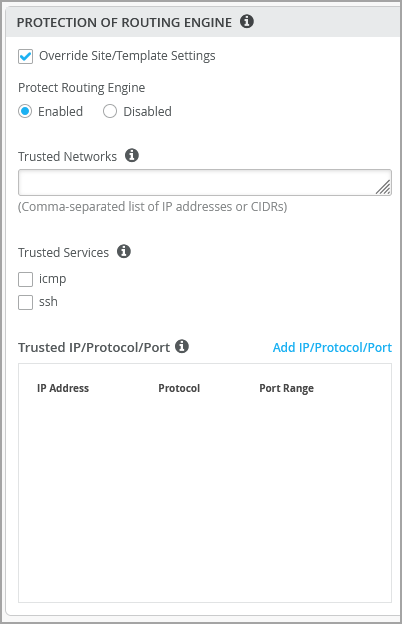
ルーティングエンジン保護機能は、ルーティングエンジンが信頼できるシステムからのトラフィックのみを受け入れることを確実にします。この機能を有効にすると、ステートレス ファイアウォール フィルターが作成され、指定された信頼できる送信元からのものを除き、ルーティングエンジン宛ての すべてのトラフィックを破棄します。ルーティングエンジンを保護するには、ルーターの lo0 インターフェイス上で受信トラフィックをフィルタリングする必要があります。ジュニパースイッチでこの機能を有効にすることが、ベストプラクティスとして推奨されます。
ルーティングエンジンの保護を設定する
ルーティングエンジン保護が有効になっている場合、デフォルトでは、Mistが次のサービス(設定されている場合)がスイッチと通信できることを確認します。 BGP、BFD、NTP、DNS、SNMP、TACACS、RADIUS、およびMistクラウド接続。
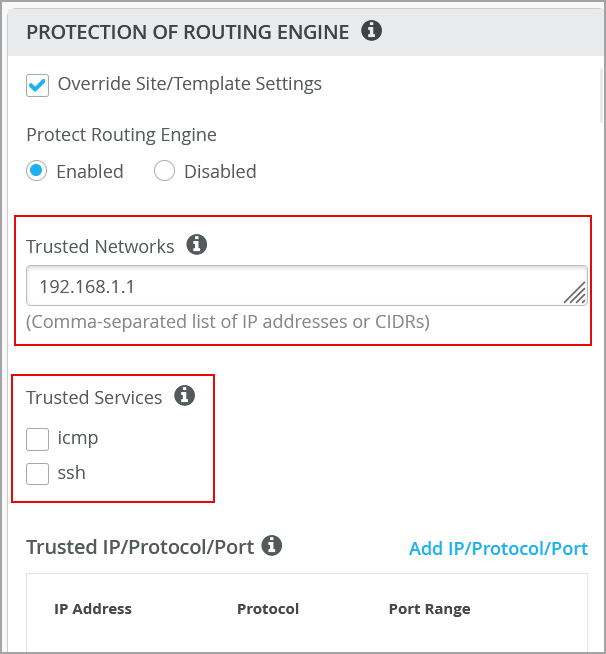
スイッチへのアクセス元のICMPまたはSSHを追加で設定する場合は、[Trusted Services]で有効にすることができます。ICMPとSSHを有効にすると、これらのプロトコルがすべてのネットワークに開かれることに注意してください。
スイッチへのアクセス元として一般的に使用されるIPネットワークを設定する場合は、[信頼済みネットワーク]で設定できます。ネットワーク全体からスイッチにアクセスする場合は、このオプションを使用します。
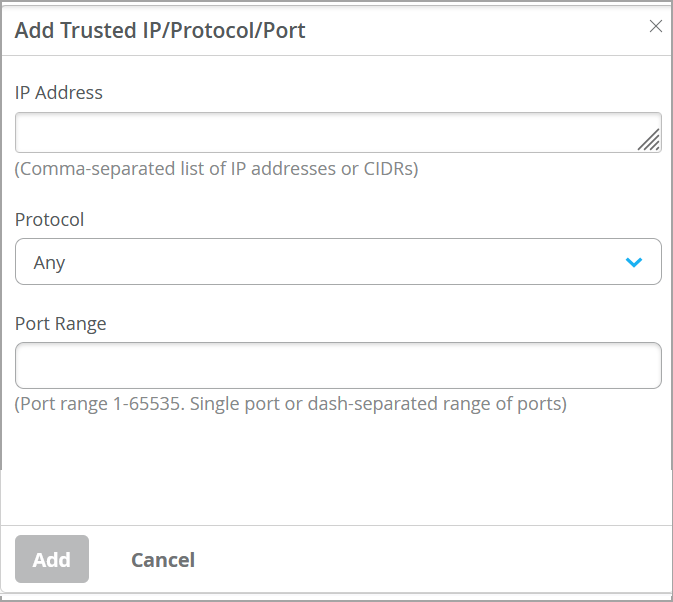
スイッチにアクセスしたい他のカスタムサービス(IP、ポート、プロトコルの特定の組み合わせ)がある場合は、信頼できるIP/ポート/プロトコルで設定できます。このオプションでは、特定のポートとプロトコルを使用してスイッチにアクセスできます。
ルーティングエンジンの保護は、組織レベル(組織>スイッチ テンプレート)、サイト レベル(サイト > スイッチ設定)、およびスイッチ レベル(スイッチ>スイッチ名)で設定できます。
以下の手順は、スイッチ レベルでルーティングエンジンの保護を設定する手順を示しています。
スイッチ レベルでルーティングエンジンの保護を設定するには:
設定コマンド(CLI)
"set groups top firewall family inet filter protect_re term allow_mist_obssh from source-port [ 2200 ]", "set groups top firewall family inet filter protect_re term allow_mist_obssh then accept", "set groups top firewall family inet filter protect_re term allow_dhcp from source-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from destination-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from protocol udp", "set groups top firewall family inet filter protect_re term allow_dhcp then accept", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from destination-port [ 179 ]", "set groups top firewall family inet filter protect_re term allow_bgp from protocol tcp", "set groups top firewall family inet filter protect_re term allow_bgp then accept", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from destination-port [ 3784 4784 ]", "set groups top firewall family inet filter protect_re term allow_bfd from protocol udp", "set groups top firewall family inet filter protect_re term allow_bfd then accept", "set firewall family inet filter protect_re term allow_ntp_src from protocol udp", "set firewall family inet filter protect_re term allow_ntp_src from source-port 123", "set firewall family inet filter protect_re term allow_ntp_src then accept", "set firewall family inet filter protect_re term allow_ntp_dest from protocol udp", "set firewall family inet filter protect_re term allow_ntp_dest from destination-port 123", "set firewall family inet filter protect_re term allow_ntp_dest then accept", "set groups top firewall family inet filter protect_re term allow_dns from source-port [ 53 ]", "set groups top firewall family inet filter protect_re term allow_dns from protocol [ tcp udp ]", "set groups top firewall family inet filter protect_re term allow_dns then accept", "set groups top firewall family inet filter protect_re term allow_radius from source-prefix-list radius_servers", "set groups top firewall family inet filter protect_re term allow_radius from destination-port [ 1812 1813 ]", "set groups top firewall family inet filter protect_re term allow_radius from protocol udp", "set groups top firewall family inet filter protect_re term allow_radius then accept", "set groups top firewall family inet filter protect_re term allow_tacacs from source-prefix-list tacacs_servers", "set groups top firewall family inet filter protect_re term allow_tacacs from destination-port [ 49 ]", "set groups top firewall family inet filter protect_re term allow_tacacs from protocol tcp", "set groups top firewall family inet filter protect_re term allow_tacacs then accept", "set groups top firewall family inet filter protect_re term allow_snmp_clients from source-prefix-list snmp_clients", "set groups top firewall family inet filter protect_re term allow_snmp_clients from destination-port [ 161 10161 ]", "set groups top firewall family inet filter protect_re term allow_snmp_clients from protocol udp", "set groups top firewall family inet filter protect_re term allow_snmp_clients then accept", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32", "set groups top firewall family inet filter protect_re term trusted_hosts then accept", "set groups top firewall family inet filter protect_re term otherwise then discard", "set groups top interfaces lo0 unit 0 family inet filter input protect_re",
ルーティングエンジン設定の保護の検証
ルーティングエンジンの保護(トラステッド ネットワーク設定)
設定コマンド(CLI)
set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32 set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32 set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32 set groups top firewall family inet filter protect_re term trusted_hosts then accept set groups top firewall family inet filter protect_re term otherwise then log set groups top firewall family inet filter protect_re term otherwise then syslog set groups top firewall family inet filter protect_re term otherwise then discard
API
“switch_mgmt”: {
“protect_re”: {
“enabled”: true,
“trusted_hosts”: [
“10.216.192.1”,
“100.100.100.2”,
“8.8.8.8”
],
“allowed_services”: [],
“custom”: []
},
BGP 接続のステータスの概要を取得するには、 show bgp summary コマンドを使用します。
{master:0}
mist@Border-switch-R2-U21> show bgp summary
Warning: License key missing; One or more members of the VC require ‘bgp’ license
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 4 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
10 6 0 0 0 0
bgp.evpn.0
68 34 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.255.240.3 65002 101 103 0 1 42:08 Establ
inet.0: 3/5/5/0
10.255.240.5 65003 35 33 0 3 11:51 Establ
inet.0: 3/5/5/0
100.100.100.2 65002 206 209 0 0 1:06:18 Establ
bgp.evpn.0: 25/34/34/0
default-switch.evpn.0: 22/30/30/0
default_evpn.evpn.0: 0/0/0/0
100.100.100.3 65003 57 55 0 3 11:48 Establ
bgp.evpn.0: 9/34/34/0
default-switch.evpn.0: 8/30/30/0
default_evpn.evpn.0: 0/0/0/0
Trusted Networks機能をテストするには、次に示すように、スイッチから100.100.100.2にpingを実行します。送信されたすべてのパケットがパケットロスなく受信されていることがわかります。
mist@Border-switch-R2-U21> ping 100.100.100.2
PING 100.100.100.2 (100.100.100.2): 56 data bytes
64 bytes from 100.100.100.2: icmp_seq=0 ttl=64 time=2.695 ms
64 bytes from 100.100.100.2: icmp_seq=1 ttl=64 time=8.756 ms
64 bytes from 100.100.100.2: icmp_seq=2 ttl=64 time=13.312 ms
64 bytes from 100.100.100.2: icmp_seq=3 ttl=64 time=9.025 ms
--- 100.100.100.2 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max/stddev = 2.695/8.447/13.312/3.781 ms
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.3
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.2
Password:
Last login: Fri Feb 3 04:57:20 2023 from 10.255.240.2
--- JUNOS 21.3R1.9 Kernel 64-bit JNPR-12.1-20210828.6e5b1bf_buil
root@CORE-1:RE:0%
また、信頼できるネットワーク以外のネットワークにpingまたはsshを実行します。以下に示すように、pingは100%のパケット損失を示しています。
mist@Border-switch-R2-U21> ssh root@100.100.100.3
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.4
{master:0}
mist@Border-switch-R2-U21> ping 100.100.100.3
PING 100.100.100.3 (100.100.100.3): 56 data bytes
--- 100.100.100.3 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
{master:0}
mist@Border-switch-R2-U21> ping 100.100.100.4
PING 100.100.100.4 (100.100.100.4): 56 data bytes
--- 100.100.100.4 ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
ルーティングエンジンの保護(トラステッドサービス設定)
設定コマンド(CLI)
"set groups top interfaces lo0 unit 0 family inet filter input protect_re", "set groups top firewall family inet filter protect_re term allow_mist_obssh from source-port [ 2200 ]", "set groups top firewall family inet filter protect_re term allow_mist_obssh then accept", "set groups top firewall family inet filter protect_re term allow_dhcp from source-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from destination-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from protocol udp", "set groups top firewall family inet filter protect_re term allow_dhcp then accept", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from destination-port [ 179 ]", "set groups top firewall family inet filter protect_re term allow_bgp from protocol tcp", "set groups top firewall family inet filter protect_re term allow_bgp then accept", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from destination-port [ 3784 4784 ]", "set groups top firewall family inet filter protect_re term allow_bfd from protocol udp", "set groups top firewall family inet filter protect_re term allow_bfd then accept", "set firewall family inet filter protect_re term allow_ntp_src from protocol udp", "set firewall family inet filter protect_re term allow_ntp_src from source-port 123", "set firewall family inet filter protect_re term allow_ntp_src then accept", "set firewall family inet filter protect_re term allow_ntp_dest from protocol udp", "set firewall family inet filter protect_re term allow_ntp_dest from destination-port 123", "set firewall family inet filter protect_re term allow_ntp_dest then accept", "set groups top firewall family inet filter protect_re term allow_dns from source-port [ 53 ]", "set groups top firewall family inet filter protect_re term allow_dns from protocol [ tcp udp ]", "set groups top firewall family inet filter protect_re term allow_dns then accept", "set groups top firewall family inet filter protect_re term allow_radius from source-prefix-list radius_servers", "set groups top firewall family inet filter protect_re term allow_radius from destination-port [ 1812 1813 ]", "set groups top firewall family inet filter protect_re term allow_radius from protocol udp", "set groups top firewall family inet filter protect_re term allow_radius then accept", "set groups top firewall family inet filter protect_re term allow_tacacs from source-prefix-list tacacs_servers", "set groups top firewall family inet filter protect_re term allow_tacacs from destination-port [ 49 ]", "set groups top firewall family inet filter protect_re term allow_tacacs from protocol tcp", "set groups top firewall family inet filter protect_re term allow_tacacs then accept", "set groups top firewall family inet filter protect_re term allow_snmp_clients from source-prefix-list snmp_clients", "set groups top firewall family inet filter protect_re term allow_snmp_clients from destination-port [ 161 10161 ]", "set groups top firewall family inet filter protect_re term allow_snmp_clients from protocol udp", "set groups top firewall family inet filter protect_re term allow_snmp_clients then accept", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32", "set groups top firewall family inet filter protect_re term trusted_hosts then accept", "set groups top firewall family inet filter protect_re term allow_ssh from destination-port [ 22 ]", "set groups top firewall family inet filter protect_re term allow_ssh from protocol tcp", "set groups top firewall family inet filter protect_re term allow_ssh then accept", "set groups top firewall family inet filter protect_re term allow_icmp from protocol icmp", "set groups top firewall family inet filter protect_re term allow_icmp then accept", "set groups top firewall family inet filter protect_re term otherwise then discard",
API
“switch_mgmt”: {
“protect_re”: {
“enabled”: true,
“trusted_hosts”: [
“10.216.192.1”,
“100.100.100.2”,
“8.8.8.8”
],
“allowed_services”: [
“ssh”,
“icmp”
],
“custom”: []
},
信頼済みサービスの設定をテストするには、信頼済みネットワーク上にないデバイスにログインします。
mist@Distribution-2-R2-U07-> ping 100.100.100.1
PING 100.100.100.1 (100.100.100.1): 56 data bytes
64 bytes from 100.100.100.1: icmp_seq=0 ttl=63 time=36.941 ms
64 bytes from 100.100.100.1: icmp_seq=1 ttl=63 time=45.158 ms
--- 100.100.100.1 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max/stddev = 36.941/41.050/45.158/4.108 ms
{master:0}
mist@Distribution-2-R2-U07-> ssh root@100.100.100.1
Password:
Last login: Fri Feb 3 07:23:35 2023 from 10.216.201.35
--- JUNOS 22.2R1.12 Kernel 64-bit JNPR-12.1-20220623.dbb31e0_buil
root@Border-switch-R2-U21:RE:0%
破棄されたパケットを確認するには、デバイスで次の追加のCLIコマンドを実行します。
set groups top firewall family inet filter protect_re term otherwise then log set groups top firewall family inet filter protect_re term otherwise then syslog mist@Distribution-1-R2-U06-> show firewall log Log : Time Filter Action Interface Protocol Src Addr Dest Addr 13:20:01 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:56 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:51 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:45 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:40 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:35 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:30 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:26 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:19 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:18 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:14 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:12 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:09 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:04 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:01 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 14:17:31 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:30 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:28 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:28 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:26 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:23 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:18 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:16 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:15 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:12 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:10 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:09 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:07 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:06 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:05 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:03 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:02 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:01 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:57 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:52 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:51 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:50 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:46 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:45 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:44 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:41 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:41 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:40 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:38 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:36 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:36 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:31 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:26 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:26 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:25 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:20 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:19 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:16 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6
あわせて読みたい: 例:信頼できる送信元からのトラフィックを受け入れるためのステートレスファイアウォールフィルターの設定 および 例:TCPおよびICMPフラッドから保護するためのステートレスファイアウォールフィルターの設定。