SRXシリーズファイアウォールのサービスステータスを監視する
以下の手順に従って、Web フィルタリング、侵入検知、およびアプリケーションセキュリティのステータスを確認します。
Juniper Mist™ Cloud PortalのJuniper Networks® SRXシリーズ Firewallで、以下の機能のサービスステータスを監視できます。
-
拡張Webフィルタリング(EWF)
-
IDP
-
アプリケーションセキュリティ
この機能を使用するには、SRXシリーズファイアウォールの有効なライセンスが必要です。ライセンス要件とインストールの詳細については、 ジュニパーライセンスユーザーガイドを参照してください。
SRXシリーズファイアウォールで、 show system license コマンドを使用して、有効期限付きのライセンス名を表示します。
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
anti_spam_key_sbl 0 1 0 2022-04-28 00:00:00 UTC
idp-sig 0 1 0 2022-04-28 00:00:00 UTC
dynamic-vpn 0 2 0 permanent
av_key_sophos_engine 0 1 0 2022-04-28 00:00:00 UTC
logical-system 1 3 0 permanent
wf_key_websense_ewf 0 1 0 2022-04-28 00:00:00 UTC
remote-access-ipsec-vpn-client 0 2 0 permanent
Licenses installed:
License identifier: DemoLabJUNOS386107562
License version: 4
Valid for device: CV4720AF0436
Customer ID: Juniper Internal
Features:
av_key_sophos_engine - Anti Virus with Sophos Engine
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
anti_spam_key_sbl - Anti-Spam
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
idp-sig - IDP Signature
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
wf_key_websense_ewf - Web Filtering EWF
date-based, 2021-04-27 00:00:00 UTC - 2022-04-28 00:00:00 UTC
EWF ステータスの確認
拡張 Web フィルタリング(EWF)の構成ステータスを確認するには、次の手順に従います。
- CLI運用モードで、SRXシリーズファイアウォールでEWFが有効になっているかどうかを確認します。
user@host> show security utm web-filtering status UTM web-filtering status: Server status: no-config root@00c52c4c3204>
[Server status: no-config] は、EWF が構成されていないことを示します。
- CLIを使用して、SRXシリーズファイアウォール上のEWFを[edit]階層レベルで設定します。設定モードを使用し、設定をコミットします。
手記:
次の構成をラボ環境からキャプチャし、参照目的でのみ提供しました。独自の構成は、環境の特定の要件に基づいて異なる場合があります。
[edit] set system syslog file utm-log any any set system syslog file utm-log match RT_UTM set security utm custom-objects url-pattern blacklist value https://*.poki.com set security utm custom-objects custom-url-category restricted value blacklist set security utm default-configuration anti-virus type sophos-engine set security utm default-configuration anti-virus scan-options uri-check set security utm default-configuration anti-virus scan-options timeout 30 set security utm default-configuration anti-virus sophos-engine sxl-timeout 5 set security utm default-configuration web-filtering url-blacklist restricted set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering juniper-enhanced server host rp.cloud.threatseeker.com set security utm default-configuration web-filtering juniper-enhanced server port 80 set security utm default-configuration web-filtering juniper-enhanced default permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Games action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Gambling action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Abused_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Adult_Material action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Command_and_Control action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Advanced_Malware_Payloads action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bot_Networks action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Compromised_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Drugs action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Emerging_Exploits action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Files_Containing_Passwords action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Hacking action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Illegal_or_Questionable action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Keyloggers action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Embedded_iFrame action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Malicious_Web_Sites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Militancy_and_Extremist action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Mobile_Malware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Network_Errors action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Newly_Registered_Websites action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pay_to_Surf action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Phishing_and_Other_Frauds action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Damaging_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Exploited_Documents action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Potentially_Unwanted_Software action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Racism_and_Hate action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Spyware action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Content action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Suspicious_Embedded_Link action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Unauthorized_Mobile_Marketplaces action block set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Alcohol_and_Tobacco action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Application_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Bandwidth action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Computer_Security action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Custom_Encrypted_Payloads action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Elevated_Exposure action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Entertainment_Video action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_File_Download_Servers action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Freeware_and_Software_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Instant_Messaging action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Auctions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Internet_Radio_and_TV action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Intolerance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Lingerie_and_Swimsuit action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Marijuana action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Media_File_Download action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Message_Boards_and_Forums action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Non_Traditional_Religions_and_Occult_and_Folklore action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Nudity action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Parked_Domain action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Peer_to_Peer_File_Sharing action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Personals_and_Dating action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Prescribed_Medications action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Private_IP_Addresses action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Choice action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Pro_Life action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Proxy_Avoidance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Sex_Education action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Social_Networking_and_Personal_Sites action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Surveillance action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Tasteless action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Violence action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile wf-home category Enhanced_Web_and_Email_Spam action log-and-permit set security utm utm-policy custom-utm-policy anti-virus http-profile junos-av-defaults set security utm utm-policy custom-utm-policy web-filtering http-profile wf-home
-
CLI動作モードでステータスを確認します。
user@host> show security utm web-filtering status UTM web-filtering status: Server status: Juniper Enhanced using Websense server UP
これで、ステータスが [Server status: Juniper Enhanced using Websense サーバー UP] に変わります。この状態は、デバイスで EWF サービスが有効になっていることを示します。
- ステータスは、 図1に示すように、Juniper Mistクラウドポータルで確認できます。
IDPステータスの確認
侵入検出および防止(IDP)を設定する前に、次の手順を使用してIDPセキュリティパッケージをダウンロードしてインストールする必要があります。
-
コマンドの手順に従って、IDP パッケージを request security idp security-package download ダウンロード します。
-
コマンドの手順に従って、パッケージを request security idp security-package install インストール します。
この例では、次のようにダウンロードしてインストールする IDP テンプレートを使用します。
- コマンドの手順に従って、IDP テンプレートを request security idp security-package download policy-templates ダウンロードします。
- コマンドの手順に従って、テンプレートを request security idp security-package install policy-templates インストールします。
- テンプレート コミット スクリプトをアクティブにします。
[edit] user@host-1# set system scripts commit file templates.xsl
ダウンロードされたテンプレートは、Junos OS設定データベースに保存され、CLIの
[edit security idp idp-policy]階層レベルで使用できます。 事前定義されたポリシーをアクティブなポリシーとしてアクティブ化します。この例では、
Recommendedポリシーをアクティブポリシーとして使用します。[edit] user@host-1# set security idp default-policy Recommended user@host-1# set security idp active-policy Recommended
- 設定でIDPポリシーを有効にします。次のスニペットは、構成例を示しています。
set security idp idp-policy idpengine rulebase-ips rule 1 match from-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match source-address any set security idp idp-policy idpengine rulebase-ips rule 1 match to-zone any set security idp idp-policy idpengine rulebase-ips rule 1 match destination-address any set security idp idp-policy idpengine rulebase-ips rule 1 match application junos-echo set security idp idp-policy idpengine rulebase-ips rule 1 match attacks predefined-attack-groups Critical
- 以下のコマンドを動作モードで使用して、IDP ポリシーのステータスを確認します。
- 推奨されるIDPポリシー:
show security idp policies: - ポリシー名:
show security idp policies - IDPステータス:
show security idp status
- Juniper Mist CloudポータルでIDPステータスを確認します( 図1 を参照)。
- 推奨されるIDPポリシー:
アプリケーションセキュリティの設定
SRXシリーズファイアウォールでは、有効なライセンスがある場合、アプリケーションセキュリティがデフォルトで有効になっています。OCチームは、すべてのデバイスのアプリケーションシグネチャバージョンが最新であることを確認します。バージョンを変更する場合、またはカスタム バージョンをインストールする場合は、 アプリケーションを識別するための事前定義されたアプリケーション シグニチャを参照してください。
Juniper Mist Cloudポータルでセキュリティサービスのステータスを確認
Juniper Mist クラウド ポータルでは、[ SECURITY SERVICES] パネルでセキュリティ サービスのステータスを表示できます。 表 1 は、ステータスの詳細を示しています。
| セキュリティ サービス | 表示ステータス | の意味 |
|---|---|---|
| EWFの | 有効 | Websense サーバーへの接続がアップしています。 |
| 無効 | お使いのデバイスで EWF が構成されていません。 | |
| 下 | Websense サーバーへの接続がダウンしています。 | |
| IDP | 有効 | IDPが設定され、IDPポリシーが適用されます。 |
| 無効 | IDP は設定されていません。この場合、IDP ポリシー名は空白で表示されます。 | |
| アプリケーションセキュリティ | 有効 | アプリケーション・セキュリティーが使用可能です。アプリケーション署名のバージョンが表示されます。 |
| 無効 | アプリケーション・セキュリティーが有効になっていません。アプリケーション・シグネチャのバージョンはゼロと表示されます。 |
図1 は、クラウドポータルのセキュリティサービスのステータスJuniper Mist示しています。
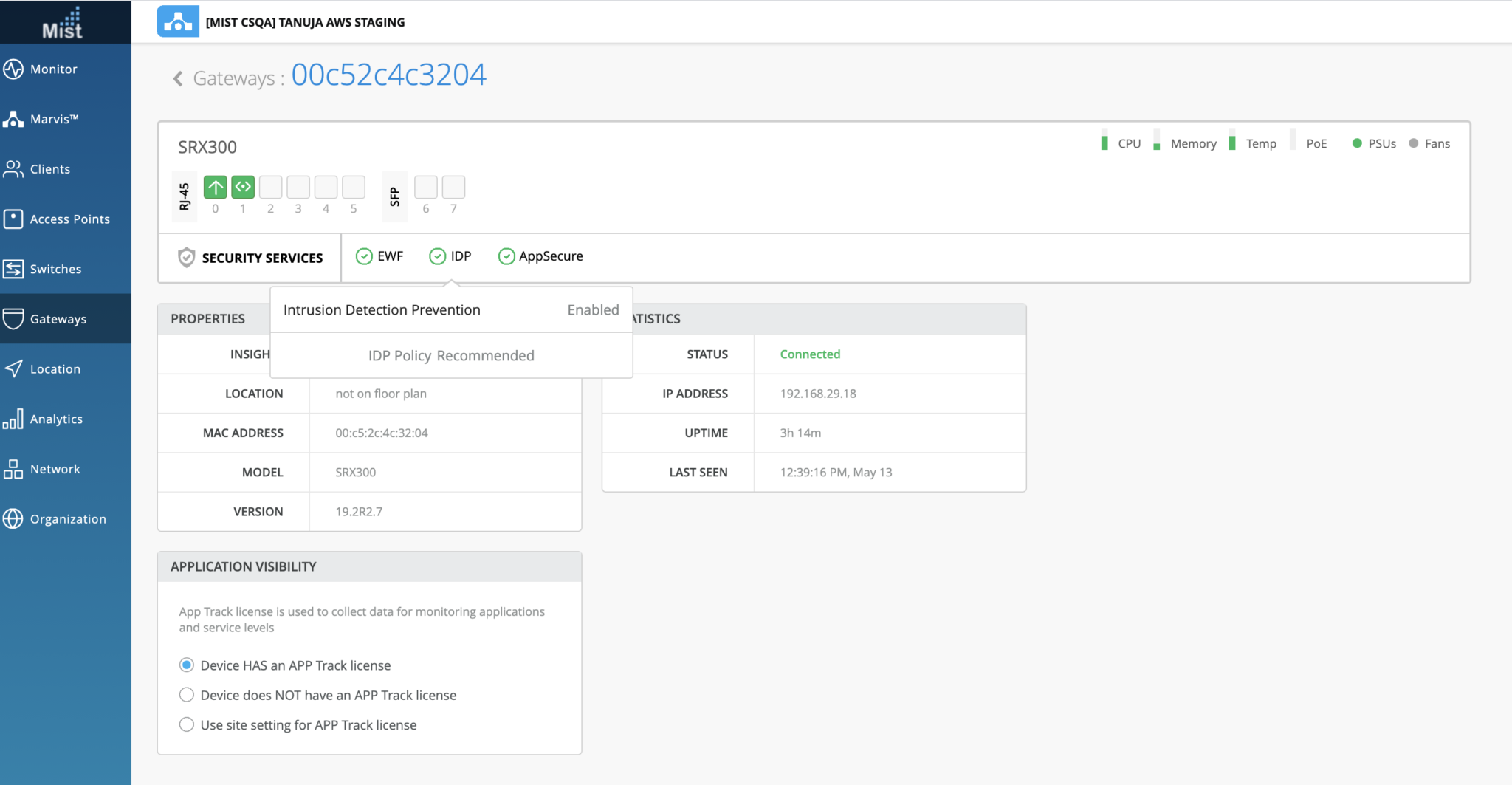
有効なライセンスの有無やセキュリティサービスのステータスなどの詳細を取得できます。
"service_status": {
"idp_status": "disabled", // either "enabled" or "disabled"
"idp_policy": "", // if the above is disabled this will be empty
"appid_status": "disabled", // either "enabled" or "disabled"
"ewf_status": "disabled", // either "enabled" (websense up), "disabled" (no config) or "down" (websense down)
"appid_version": 0 // this will be 0 if appid_status is disabled, as we then don't check the version number
},
