本页内容
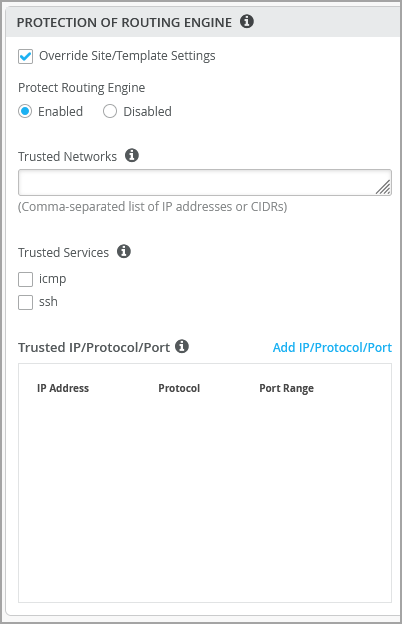
路由引擎保护
路由引擎保护功能可确保路由引擎仅接受来自可信系统的流量。启用此功能将创建无状态防火墙过滤器,该过滤器丢弃发往路由引擎的所有流量,但来自指定可信源的流量除外。保护路由引擎涉及过滤路由器 lo0 接口上的传入流量。建议在瞻博网络交换机上启用此功能作为最佳做法。
配置路由引擎保护
启用路由引擎保护后,Mist默认情况下会确保允许以下服务(如果已配置)与交换机通信:BGP、BFD、NTP、DNS、SNMP、TACACS、RADIUS 和Mist云连接。
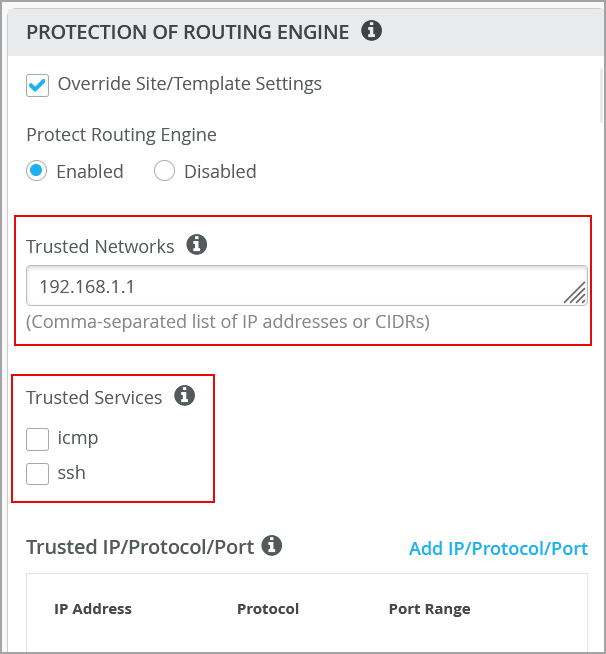
如果您想要额外配置 ICMP 或 SSH 来访问交换机,可以在“受信任的服务”下启用它们。请注意,启用 ICMP 和 SSH 会向所有网络开放这些协议。
如果要配置常用的 IP 网络来访问交换机,可以在可信网络下进行配置。如果要从整个网络访问交换机,请使用此选项。
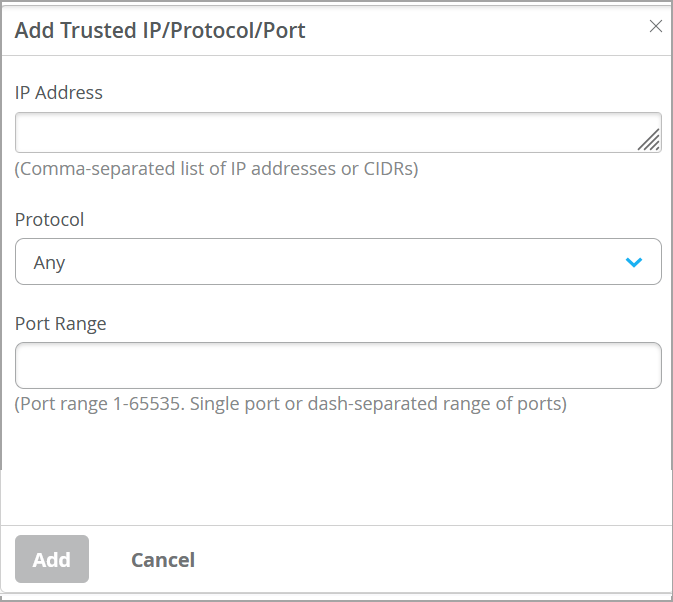
如果您希望通过其他自定义服务(即 IP、端口和协议的特定组合)连接到交换机,则可以在可信 IP/端口/协议下进行配置。此选项允许您使用特定端口和协议访问交换机。
您可以在组织级别(组织>交换机模板)、站点级别(站点>交换机配置)和交换机级别(交换机>交换机名称)配置路由引擎保护。
以下过程列出了在交换机级别配置路由引擎保护的步骤。
要在交换机级别配置路由引擎保护:
配置命令 (CLI)
"set groups top firewall family inet filter protect_re term allow_mist_obssh from source-port [ 2200 ]", "set groups top firewall family inet filter protect_re term allow_mist_obssh then accept", "set groups top firewall family inet filter protect_re term allow_dhcp from source-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from destination-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from protocol udp", "set groups top firewall family inet filter protect_re term allow_dhcp then accept", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from destination-port [ 179 ]", "set groups top firewall family inet filter protect_re term allow_bgp from protocol tcp", "set groups top firewall family inet filter protect_re term allow_bgp then accept", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from destination-port [ 3784 4784 ]", "set groups top firewall family inet filter protect_re term allow_bfd from protocol udp", "set groups top firewall family inet filter protect_re term allow_bfd then accept", "set firewall family inet filter protect_re term allow_ntp_src from protocol udp", "set firewall family inet filter protect_re term allow_ntp_src from source-port 123", "set firewall family inet filter protect_re term allow_ntp_src then accept", "set firewall family inet filter protect_re term allow_ntp_dest from protocol udp", "set firewall family inet filter protect_re term allow_ntp_dest from destination-port 123", "set firewall family inet filter protect_re term allow_ntp_dest then accept", "set groups top firewall family inet filter protect_re term allow_dns from source-port [ 53 ]", "set groups top firewall family inet filter protect_re term allow_dns from protocol [ tcp udp ]", "set groups top firewall family inet filter protect_re term allow_dns then accept", "set groups top firewall family inet filter protect_re term allow_radius from source-prefix-list radius_servers", "set groups top firewall family inet filter protect_re term allow_radius from destination-port [ 1812 1813 ]", "set groups top firewall family inet filter protect_re term allow_radius from protocol udp", "set groups top firewall family inet filter protect_re term allow_radius then accept", "set groups top firewall family inet filter protect_re term allow_tacacs from source-prefix-list tacacs_servers", "set groups top firewall family inet filter protect_re term allow_tacacs from destination-port [ 49 ]", "set groups top firewall family inet filter protect_re term allow_tacacs from protocol tcp", "set groups top firewall family inet filter protect_re term allow_tacacs then accept", "set groups top firewall family inet filter protect_re term allow_snmp_clients from source-prefix-list snmp_clients", "set groups top firewall family inet filter protect_re term allow_snmp_clients from destination-port [ 161 10161 ]", "set groups top firewall family inet filter protect_re term allow_snmp_clients from protocol udp", "set groups top firewall family inet filter protect_re term allow_snmp_clients then accept", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32", "set groups top firewall family inet filter protect_re term trusted_hosts then accept", "set groups top firewall family inet filter protect_re term otherwise then discard", "set groups top interfaces lo0 unit 0 family inet filter input protect_re",
验证路由引擎配置的保护
路由引擎保护(受信任的网络配置)
配置命令 (CLI)
set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32 set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32 set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32 set groups top firewall family inet filter protect_re term trusted_hosts then accept set groups top firewall family inet filter protect_re term otherwise then log set groups top firewall family inet filter protect_re term otherwise then syslog set groups top firewall family inet filter protect_re term otherwise then discard
蜜蜂属
“switch_mgmt”: {
“protect_re”: {
“enabled”: true,
“trusted_hosts”: [
“10.216.192.1”,
“100.100.100.2”,
“8.8.8.8”
],
“allowed_services”: [],
“custom”: []
},
show bgp summary使用命令获取 BGP 连接状态的摘要:
{master:0}
mist@Border-switch-R2-U21> show bgp summary
Warning: License key missing; One or more members of the VC require ‘bgp’ license
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 4 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
10 6 0 0 0 0
bgp.evpn.0
68 34 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.255.240.3 65002 101 103 0 1 42:08 Establ
inet.0: 3/5/5/0
10.255.240.5 65003 35 33 0 3 11:51 Establ
inet.0: 3/5/5/0
100.100.100.2 65002 206 209 0 0 1:06:18 Establ
bgp.evpn.0: 25/34/34/0
default-switch.evpn.0: 22/30/30/0
default_evpn.evpn.0: 0/0/0/0
100.100.100.3 65003 57 55 0 3 11:48 Establ
bgp.evpn.0: 9/34/34/0
default-switch.evpn.0: 8/30/30/0
default_evpn.evpn.0: 0/0/0/0
要测试可信网络功能,请从交换机 ping 100.100.100.2,如下所示。您可以看到已接收所有传输的数据包,而不会丢失任何数据包。
mist@Border-switch-R2-U21> ping 100.100.100.2
PING 100.100.100.2 (100.100.100.2): 56 data bytes
64 bytes from 100.100.100.2: icmp_seq=0 ttl=64 time=2.695 ms
64 bytes from 100.100.100.2: icmp_seq=1 ttl=64 time=8.756 ms
64 bytes from 100.100.100.2: icmp_seq=2 ttl=64 time=13.312 ms
64 bytes from 100.100.100.2: icmp_seq=3 ttl=64 time=9.025 ms
--- 100.100.100.2 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max/stddev = 2.695/8.447/13.312/3.781 ms
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.3
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.2
Password:
Last login: Fri Feb 3 04:57:20 2023 from 10.255.240.2
--- JUNOS 21.3R1.9 Kernel 64-bit JNPR-12.1-20210828.6e5b1bf_buil
root@CORE-1:RE:0%
此外,对受信任网络以外的网络执行 ping 命令或 ssh。如下图所示,ping 显示 100% 的数据包丢失。
mist@Border-switch-R2-U21> ssh root@100.100.100.3
{master:0}
mist@Border-switch-R2-U21> ssh root@100.100.100.4
{master:0}
mist@Border-switch-R2-U21> ping 100.100.100.3
PING 100.100.100.3 (100.100.100.3): 56 data bytes
--- 100.100.100.3 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
{master:0}
mist@Border-switch-R2-U21> ping 100.100.100.4
PING 100.100.100.4 (100.100.100.4): 56 data bytes
--- 100.100.100.4 ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
路由引擎保护(受信任的服务配置)
配置命令 (CLI)
"set groups top interfaces lo0 unit 0 family inet filter input protect_re", "set groups top firewall family inet filter protect_re term allow_mist_obssh from source-port [ 2200 ]", "set groups top firewall family inet filter protect_re term allow_mist_obssh then accept", "set groups top firewall family inet filter protect_re term allow_dhcp from source-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from destination-port [ 67 68 ]", "set groups top firewall family inet filter protect_re term allow_dhcp from protocol udp", "set groups top firewall family inet filter protect_re term allow_dhcp then accept", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bgp from destination-port [ 179 ]", "set groups top firewall family inet filter protect_re term allow_bgp from protocol tcp", "set groups top firewall family inet filter protect_re term allow_bgp then accept", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from source-prefix-list bgp_vrf_neighbors", "set groups top firewall family inet filter protect_re term allow_bfd from destination-port [ 3784 4784 ]", "set groups top firewall family inet filter protect_re term allow_bfd from protocol udp", "set groups top firewall family inet filter protect_re term allow_bfd then accept", "set firewall family inet filter protect_re term allow_ntp_src from protocol udp", "set firewall family inet filter protect_re term allow_ntp_src from source-port 123", "set firewall family inet filter protect_re term allow_ntp_src then accept", "set firewall family inet filter protect_re term allow_ntp_dest from protocol udp", "set firewall family inet filter protect_re term allow_ntp_dest from destination-port 123", "set firewall family inet filter protect_re term allow_ntp_dest then accept", "set groups top firewall family inet filter protect_re term allow_dns from source-port [ 53 ]", "set groups top firewall family inet filter protect_re term allow_dns from protocol [ tcp udp ]", "set groups top firewall family inet filter protect_re term allow_dns then accept", "set groups top firewall family inet filter protect_re term allow_radius from source-prefix-list radius_servers", "set groups top firewall family inet filter protect_re term allow_radius from destination-port [ 1812 1813 ]", "set groups top firewall family inet filter protect_re term allow_radius from protocol udp", "set groups top firewall family inet filter protect_re term allow_radius then accept", "set groups top firewall family inet filter protect_re term allow_tacacs from source-prefix-list tacacs_servers", "set groups top firewall family inet filter protect_re term allow_tacacs from destination-port [ 49 ]", "set groups top firewall family inet filter protect_re term allow_tacacs from protocol tcp", "set groups top firewall family inet filter protect_re term allow_tacacs then accept", "set groups top firewall family inet filter protect_re term allow_snmp_clients from source-prefix-list snmp_clients", "set groups top firewall family inet filter protect_re term allow_snmp_clients from destination-port [ 161 10161 ]", "set groups top firewall family inet filter protect_re term allow_snmp_clients from protocol udp", "set groups top firewall family inet filter protect_re term allow_snmp_clients then accept", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 10-216-192-1_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 100-100-100-2_32", "set groups top firewall family inet filter protect_re term trusted_hosts from source-prefix-list 8-8-8-8_32", "set groups top firewall family inet filter protect_re term trusted_hosts then accept", "set groups top firewall family inet filter protect_re term allow_ssh from destination-port [ 22 ]", "set groups top firewall family inet filter protect_re term allow_ssh from protocol tcp", "set groups top firewall family inet filter protect_re term allow_ssh then accept", "set groups top firewall family inet filter protect_re term allow_icmp from protocol icmp", "set groups top firewall family inet filter protect_re term allow_icmp then accept", "set groups top firewall family inet filter protect_re term otherwise then discard",
蜜蜂属
“switch_mgmt”: {
“protect_re”: {
“enabled”: true,
“trusted_hosts”: [
“10.216.192.1”,
“100.100.100.2”,
“8.8.8.8”
],
“allowed_services”: [
“ssh”,
“icmp”
],
“custom”: []
},
要测试受信任的服务配置,请登录到不在受信任网络上的设备。
mist@Distribution-2-R2-U07-> ping 100.100.100.1
PING 100.100.100.1 (100.100.100.1): 56 data bytes
64 bytes from 100.100.100.1: icmp_seq=0 ttl=63 time=36.941 ms
64 bytes from 100.100.100.1: icmp_seq=1 ttl=63 time=45.158 ms
--- 100.100.100.1 ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max/stddev = 36.941/41.050/45.158/4.108 ms
{master:0}
mist@Distribution-2-R2-U07-> ssh root@100.100.100.1
Password:
Last login: Fri Feb 3 07:23:35 2023 from 10.216.201.35
--- JUNOS 22.2R1.12 Kernel 64-bit JNPR-12.1-20220623.dbb31e0_buil
root@Border-switch-R2-U21:RE:0%
要检查丢弃的数据包,请在设备上运行以下附加 CLI 命令:
set groups top firewall family inet filter protect_re term otherwise then log set groups top firewall family inet filter protect_re term otherwise then syslog mist@Distribution-1-R2-U06-> show firewall log Log : Time Filter Action Interface Protocol Src Addr Dest Addr 13:20:01 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:56 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:51 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:45 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:40 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:35 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:19:30 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:26 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:19 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:18 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:14 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:12 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:09 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:04 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 13:18:01 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 13:18:00 pfe D vtep.32769 UDP 0.0.0.0 255.255.255.255 14:17:31 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:30 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:28 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:28 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:26 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:23 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:18 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:16 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:15 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:12 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:10 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:09 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:07 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:06 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:05 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:17:03 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:17:02 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:17:01 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:57 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:52 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:51 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:50 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:46 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:45 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:44 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:41 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:41 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:40 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:38 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:36 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:36 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:31 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:26 protect_re D vme.0 UDP 10.216.199.80 255.255.255.255 14:16:26 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:25 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:20 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6 14:16:19 protect_re D vme.0 UDP 8.8.8.8 10.216.202.6 14:16:16 protect_re D vme.0 UDP 66.129.233.81 10.216.202.6
另请阅读: 示例:配置无状态防火墙过滤器以接受来自可信源的流量 和 示例:配置无状态防火墙过滤器以防止 TCP 和 ICMP 泛洪。