配置基于 MAC 的身份验证和 MAC 身份验证旁路 (MAB)
按照以下步骤配置有线设备,以根据设备的 MAC 地址对设备进行身份验证。
您可以将 MAC 身份验证与基于证书或基于凭据的身份验证一起使用,作为额外的安全层。
Juniper Mist Access Assurance 支持 MAC 身份验证旁路 (MAB),以实现跨有线和无线网络的统一访问控制。本主题提供为有线设备配置 MAB 的示例。
该示例说明除了基于证书的 EAP-TLS 身份验证外,还如何为有线设备创建 MAC 身份验证。该任务还包括为不支持点1x的有线端设备(如菲利普斯集线器)创建身份验证策略的步骤。
先决条件
-
您必须已配置基于证书的身份验证。请参阅 为无线网络配置基于证书的 (EAP-TLS) 身份验证
-
瞻博网络 EX 系列交换机。
为有线设备配置基于 MAC 的身份验证
观看以下视频,了解如何为有线设备配置和验证基于 MAC 的身份验证:
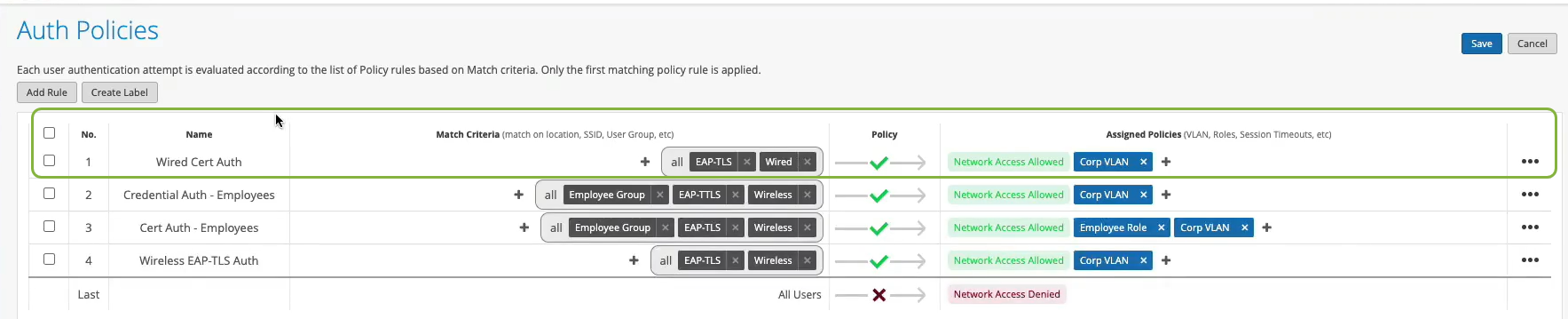
Well, what about wired devices? How do we authenticate an authorized wired client? Well, it turns out we could do it right here in the same place. So we could create a couple of more rules. So we can say OK, if we look at wired devices that are using certificates to authenticate , we could just call this rule wired certificate authentication. We can effectively apply the same matching criteria as for wireless. There's no difference whatsoever here.
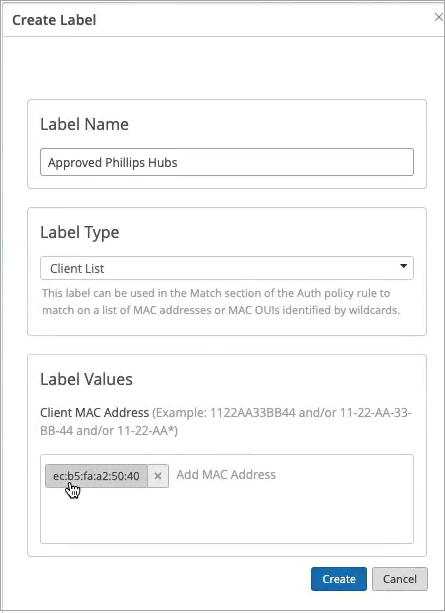
On the right-hand side, we'll decide where we want to move these devices after authentication and the right policy match. And finally, what about non-.1x capable devices on the wired side? So for example, I have here a Phillips hub that does not support .1x. How can I authenticate a Phillips app? So I could create a label for the Phillips device. The label will be client list. And I'll just say approved Phillips app. And I'll just put the MAC address of that device in. Oh. And you could put a list of MAC addresses. You can put the list of Mac OUIs. And remember that all of these labels that I'm creating in the UI - they're all available through the REST API. So there is always an endless possibility of integration with existing, say, inventory management systems that can just put all the new device MAC addresses in those lists for authentication and authorization.
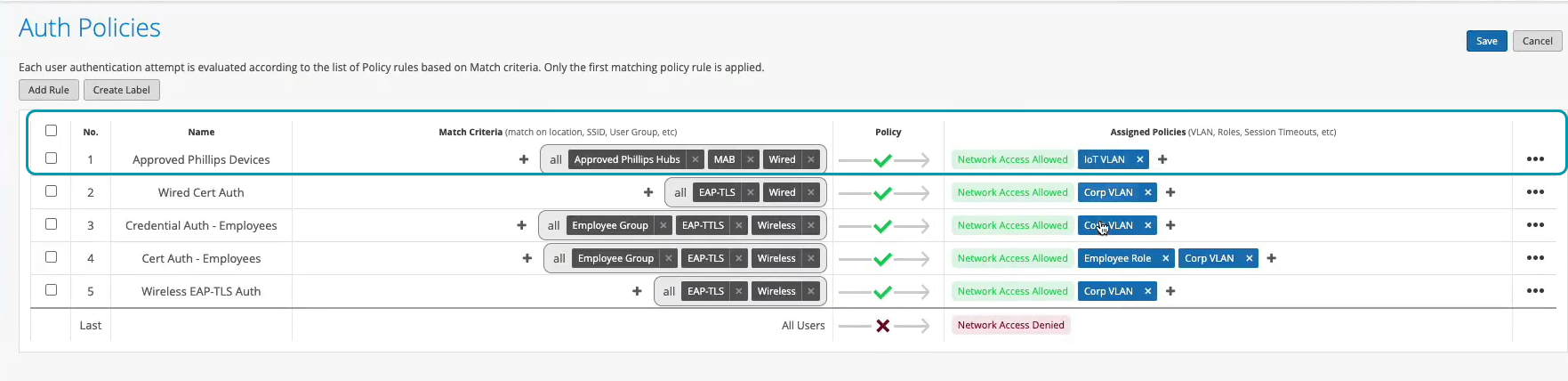
So we'll just click Create. Create this label. And we'll create a rule. We'll call it approved Phillips devices. And here we are matching on wired devices that are doing MAC address authentication bypass that are part of this client list label. And in this case, we will move them to - well, I don't want to move them to Corp VLAN. That's not what I want. I will create an IoT VLAN. And in our case, that's going to be VLAN 3000. And I'm going to add this to an IoT VLAN. And now, we have our authentication policies configuration done.
OK, so how do we validate, right? So we've connected a couple of clients to the switch. One is a laptop that's doing .1x using certificate. Another one is the Phillips Hue app. That doesn't do any .1x, and just doing MAC authentication. So we could see those two clients are connected.
Let's take a look at the laptop one. So we could click on the port. We see that there is a client with a username flashing up. Let's take a look at the wired client insights. And what we can see here is that the user has been authenticated. You could see the port up and down events from the switch side. We see all the authentication phases, same as we saw in the wireless side. The client trusts the server. The server trusts the client certificate. We get all the metadata here. We then are saying client access is allowed. And voila. We matched the same authentication policy rule. Great. So now, we know that this part is working.
Now, we go to switch back. And let's look at the Philips device. That device is not doing any form of .1x authentication. So let's just take a look at the wired client insights. Yeah, and we are seeing that here the user is authenticated. And there is a client access allowed event here as well. And in this case, the authentication type is Mac address bypass - the MAC address that we've added to the client list. And voila. We are matching the right approved Phillips device rule.
使用以下步骤通过 Juniper Mist 门户在网络中设置基于 MAC 的身份验证:
- 创建身份验证策略。
- 要为 LAN 端的非 dot1.x 设备提供身份验证,请创建新的策略标签。
- 创建新的身份验证策略。
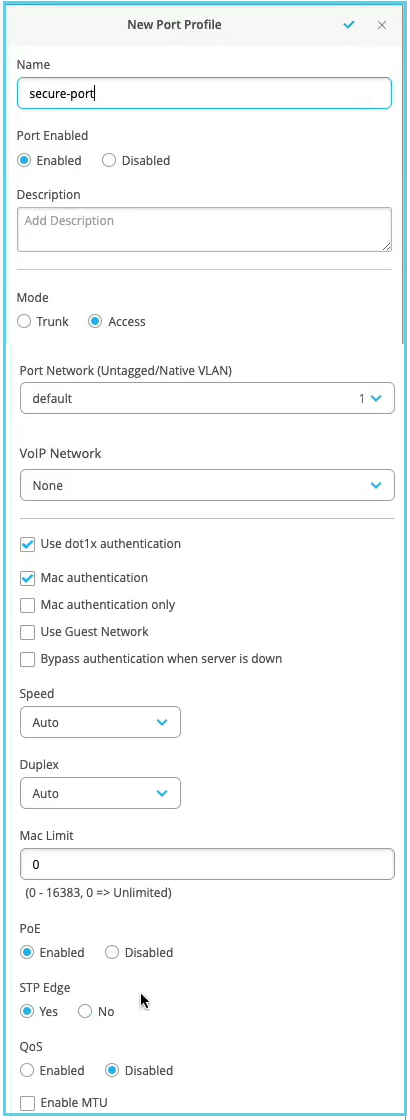
- 配置交换机以执行身份验证。
现在,您的网络已准备好安全地对客户端进行身份验证。Juniper Mist云根据身份验证策略配置验证客户端证书并授予访问权限和授权。
您可以在Juniper Mist门户上查看关联的客户端。
- 选择“ 客户端”>“有线客户端” 以查看客户端详细信息
- 选择 “监控>服务级别”>“洞察 ”以查看客户端事件。