配置客户端设备以进行 EAP-TTLS 身份验证
使用 Juniper Mist Access Assurance 时,在对 Apple 设备使用 EAP-TTLS/PAP(基于凭据)身份验证时,您需要进行其他配置。对于此任务,您必须使用免费的 Apple 配置器工具创建配置文件。
观看以下视频,了解如何为 EAP-TLS 创建网络配置文件以供测试或实验室使用:
But how do you configure your client devices based on different operating systems? So you use certificates to authenticate to a Wi-Fi network.
Note that this video is only useful if you're doing lab testing, if you' re actually using your test certificates. And this is not designed for production environments. But in production environments, clients are typically configured by MDMs or group policies or any other onboarding solutions. And none of these steps are required in production. We are just talking about simple lab tests so you could repeat these steps in your testing environment.
So first platform we'll talk about is iOS, or actually iOS, MacOS, and iPadOS. The steps are identical for all the three platforms. So what we will need to do to configure test clients that are running Apple operating systems is the Apple Configurator utility that you can download from Apple directly. It only works on MacOS, obviously. But that's how you configure profiles manually.
So go to Apple Configurator. You'll create a new profile. And we'll just say this is our mist secure net profile. What we are interested in here is Certificate section. We'll need to import the client certificate we've generated in the previous step. So we're going to click Configure. I have my test lab client PFX th at we've exported from a different video.
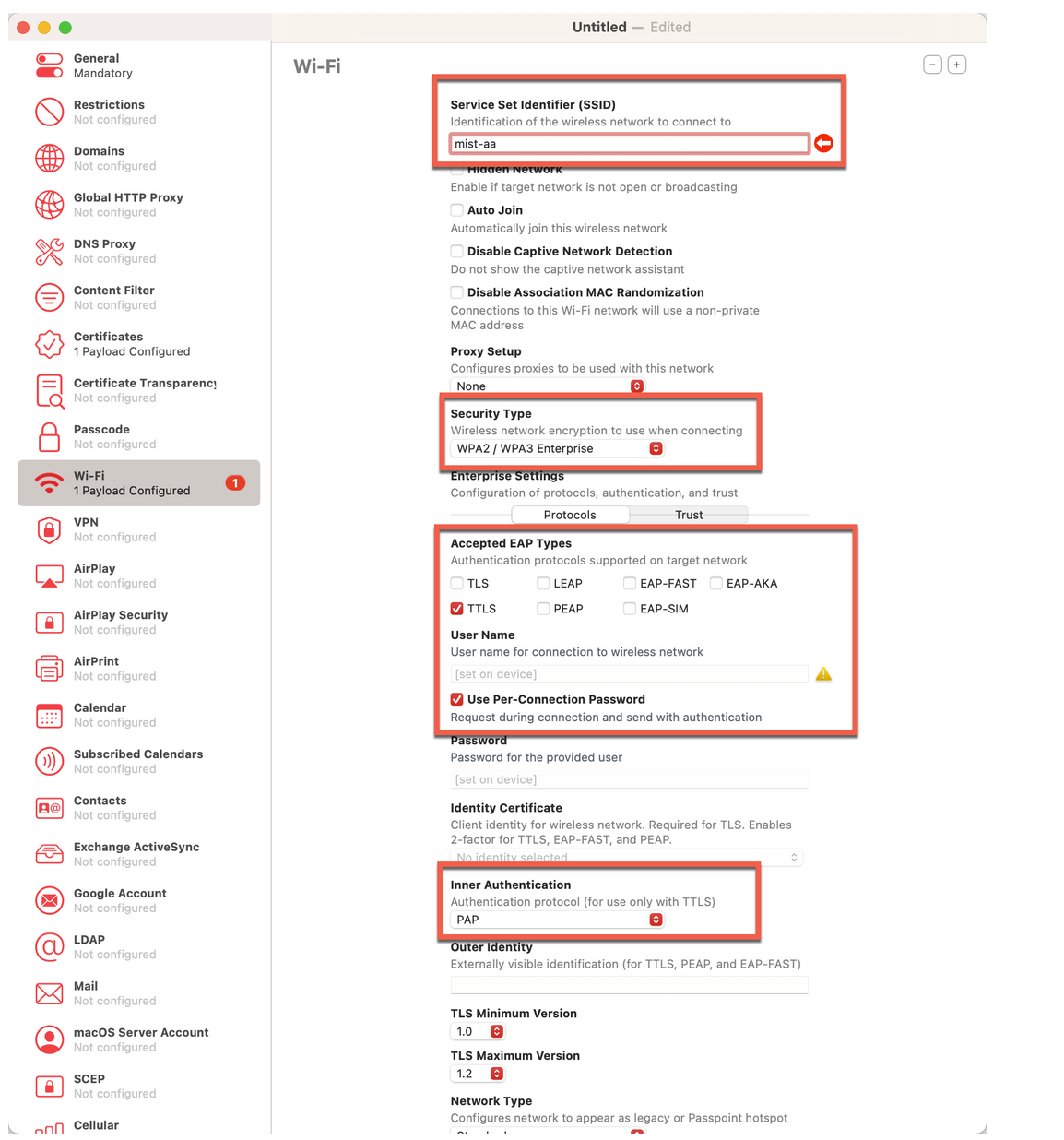
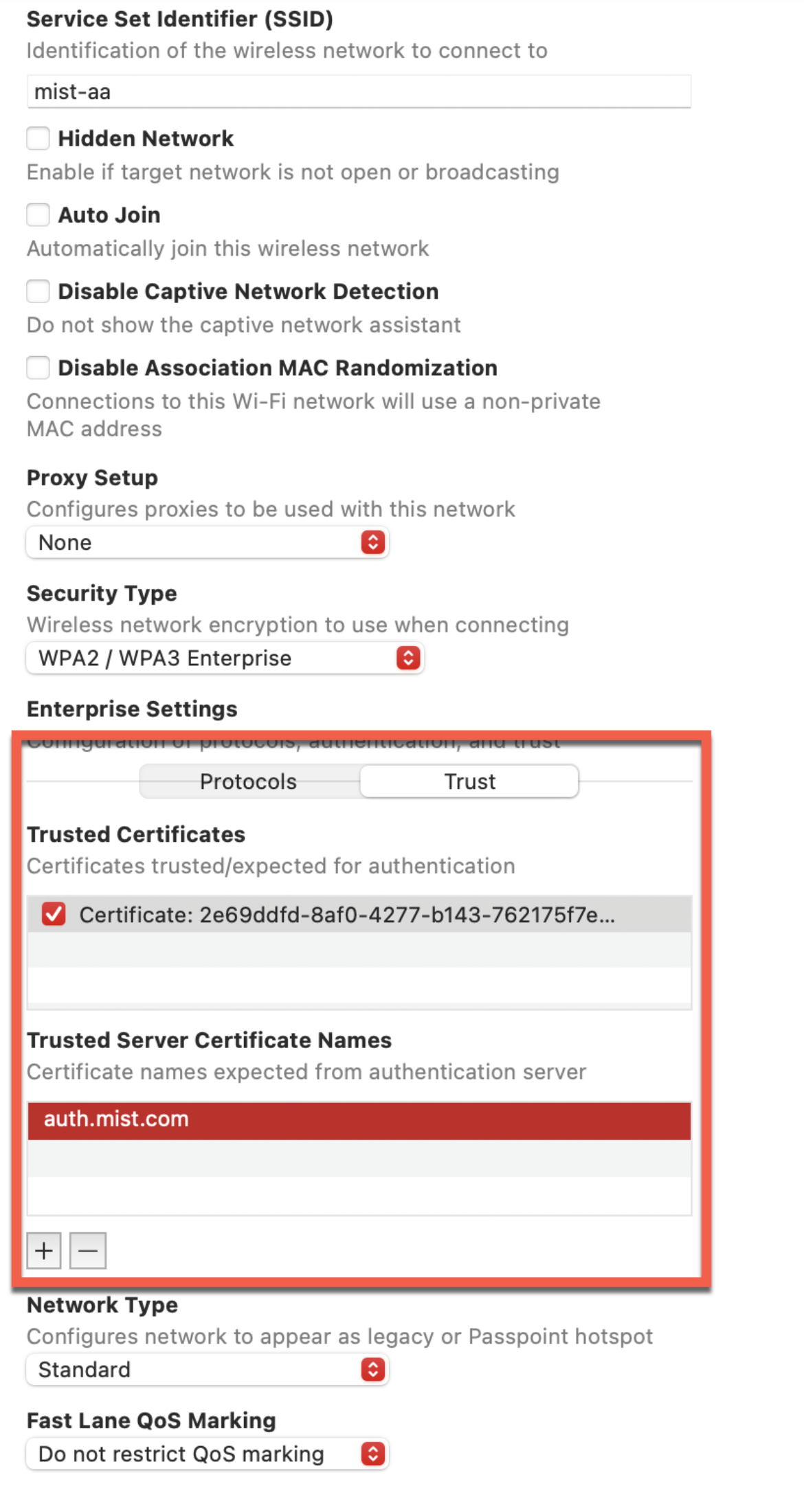
We'll need to provide a password that we used during the export. I think it's "1234." Great. So our client certificate has been importe d. The other certificate we will need is actually the server certificate that we will display from mist access assurance when client will try to connect. This server certificate is actually available here. So we'll copy this. Save it as a text file. And then save it in the same folder. And we'll call it mist-certificate .crt. So now we'll go back to our profile. We'll import one more cert. And we'll import the Mist certificate in here. Now, the next step is to configure the Wi-Fi profile. So we'll config ure Wi-Fi profile. This is where we'll put our SSID name. And our SSID name was mist-securenet. Just make sure you're using the one you've configured. Under Security Type, we'll use WPA3 Enterprise. Unless you're using an older device, WPA3 is supported on all the Apple - recent Apple products, I should say.
Under Protocols, we'll select TLS because we want to use certific ates to authenticate. We'll then select the client certificate that we' ve imported in the previous step. We'll then go to Trust section. And this is where we are saying client will trust the mist certificate when it will try to authenticate to th e network. So we are doing this mutual trust in here. So in this phase, the client trust the server. The server, in this case, is mist access assurance. In this section, client presents its client certificate. And mist access assurance will have to trust the client cert. We'll then go ahead and save this profile. And this will be saved as .mobileconfig file. And now, how do we distribute this? Obviously, if you're on a Mac , you could go and double-click and install it. But we can also distribute this to our clients using AirDrop, for instance. Now, I will distribute this to my iPad through AirDrop.