示例:为 VPWS 配置 FEC 129 BGP 自动发现
此示例说明如何配置虚拟专用线路服务 (VPWS),其中 BGP 会自动动态发现远程提供商边缘 (PE) 设备,并通过 LDP 使用 FEC 129 发出伪线信号。这种安排可减少与静态配置的第 2 层电路相关的配置负担,同时仍然使用 LDP 作为底层信令协议。
要求
此示例要求 PE 设备上支持 Junos OS 13.2 或更高版本。
概述
由于 VPWS 是点对点服务,因此 FEC 129 VPWS 路由实例配置为 instance-type l2vpn。与 FEC 129 VPLS 一样,FEC 129 VPWS 使用该 l2vpn-id 语句定义路由实例所属的第 2 层 VPN。语句的存在 l2vpn-id 表示路由实例使用 FEC 129 LDP 信令。如果没有 l2vpn-id ,则表示已改为使用 BGP 信令。
VPWS 的点对点特性要求您指定源访问个人标识符 (SAII) 和目标访问个人标识符 (TAII)。此 SAII-TAII 对定义两个 PE 设备之间的唯一伪线。
SAII 使用 source-attachment-identifier FEC 129 VPWS 路由实例中的语句指定。您可以配置源附件标识符和接口,以与该源附件标识符相关联。您可以在每个接口下使用 target-attachment-identifier 语句配置 TAII。如果配置的目标标识符与远程 PE 设备通过 BGP 自动发现消息播发的源标识符匹配,则发出该源-目标对之间的伪线信号。如果播发的源标识符与配置的目标标识符之间没有匹配,则无法建立伪线。
示例:具有多个接口和站点的 VPWS 配置
routing-instances {
FEC129-VPWS {
instance-type l2vpn;
interface ge-0/0/1.0;
interface ge-0/0/2.0;
interface ge-0/0/3.0;
route-distinguisher 10.255.0.1:200;
l2vpn-id l2vpn-id:100:200;
vrf-target target:100:200;
protocols l2vpn {
site CUSTOMER-1 {
source-attachment-identifier 1;
interface ge-0/0/1.0 {
target-attachment-identifier 2;
}
interface ge-0/0/2.0 {
target-attachment-identifier 3;
}
}
}
}
}
您可以在一个站点内配置多个接口,因为每个 SAII-TAII 对都定义了一个唯一的伪线,如示例配置中的伪线 1-2 和 1-3 所示。源和目标访问标识符均为 4 字节编号,只能在存在 IS l2vpn 和l2vpn-id配置语句的 instance-type FEC 129 VPWS 实例中进行配置。
您可以将源标识符和目标标识符指定为 1 到 4,292,967,295 范围内的纯无符号整数。
第 2 层电路和第 2 层 VPN 服务允许在每伪线的基础上包含许多可选参数。FEC 129 VPWS 允许使用 MTU 设置、社区标记和包含控制字等参数,如下示例配置所示:
示例:带可选配置参数的 VPWS 配置
routing-instances {
FEC129-VPWS {
instance-type l2vpn;
interface ge-0/0/1.0;
interface ge-0/0/2.0;
interface ge-0/0/3.0;
route-distinguisher 10.255.0.1:200;
l2vpn-id l2vpn-id:100:200;
vrf-target target:100:200;
protocols l2vpn {
site CUSTOMER-1 {
source-attachment-identifier 1;
community COMM;
control-word ;
encapsulation-type ethernet;
ignore-encapsulation-mismatch;
ignore-mtu-mismatch;
mtu 1500;
no-control-word;
interface ge-0/0/1.0 {
target-attachment-identifier 2;
}
interface ge-0/0/2.0 {
target-attachment-identifier 3;
community COMM;
control-word;
encapsulation-type ethernet;
ignore-encapsulation-mismatch;
ignore-mtu-mismatch;
mtu 1500;
no-control-word;
}
}
}
}
}
在站点内配置时,定义的参数会影响来自该站点的任何伪线。在接口下配置时,定义的参数会影响该单个特定伪线。这允许您在配置中的一个位置上跨与特定本地站点关联的所有伪线操作参数。
与其他点对点服务一样,必须为 CCC 封装和 CCC 地址家族配置配置为 FEC 129 VPWS 实例成员的接口,如下所示:
interfaces {
ge-0/0/1 {
encapsulation ethernet-ccc;
unit 0 {
family ccc;
}
}
ge-0/0/2 {
encapsulation ethernet-ccc;
unit 0 {
family ccc;
}
}
ge-0/0/3 {
encapsulation ethernet-ccc;
unit 0 {
family ccc;
}
}
}
您可以使用 vlan-ccc 替代 ethernet-ccc。
要支持 FEC 129 VPWS 基本功能,PE 设备上的 BGP 会话还需要配置 BGP auto-discovery-only 地址系列,以允许交换自动发现路由。如果 PE 设备上也配置了传统 BGP VPLS 或 2 层 VPN 服务,则还需要地址系列 l2vpn signaling ,如下所示:
bgp {
group pe {
type internal;
local-address 10.255.0.1;
family l2vpn {
auto-discovery-only;
signaling;
}
neighbor 10.255.0.2;
neighbor 10.255.0.3;
}
}
以下配置示例显示了具有操作、管理和维护 (OAM)(ping 和 BFD) 配置选项的 FEC 129 VPWS 路由实例:
示例:采用 OAM 的 VPWS 配置
routing-instances {
FEC129-VPWS {
instance-type l2vpn;
interface ge-0/0/1.0;
route-distinguisher 10.255.0.1:200;
l2vpn-id l2vpn-id:100:200;
vrf-target target:100:200;
protocols l2vpn {
oam {
ping-interval 600;
bfd-liveness-detection {
minimum-interval 200;
}
}
site CUSTOMER {
source-attachment-identifier 1;
oam {
ping-interval 600;
bfd-liveness-detection {
minimum-interval 200;
}
}
interface ge-0/0/1.0 {
oam {
ping-interval 600;
bfd-liveness-detection {
minimum-interval 200;
}
}
target-attachment-identifier 2;
}
}
}
}
}
在下 protocols l2vpn 配置的 OAM 选项适用于路由实例中的所有站点和伪线。在特定站点下配置的 OAM 选项适用于该站点下配置的伪线。在特定接口下配置的 OAM 选项适用于该接口下配置的伪线。
配置
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到层级的 [edit] CLI 中。
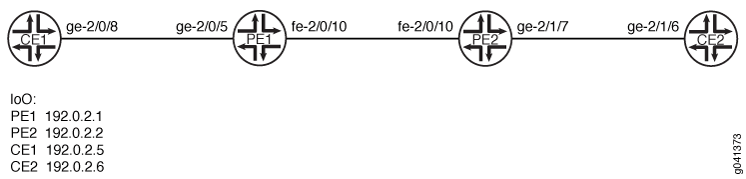
设备 CE1
set interfaces ge-2/0/8 unit 0 description CE1_to_PE1 set interfaces ge-2/0/8 unit 0 family inet address 172.16.0.1/24 set interfaces lo0 unit 0 family inet address 192.0.2.5/24 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface ge-2/0/8.0
设备 CE2
set interfaces ge-2/1/6 unit 0 description CE2_to_PE2 set interfaces ge-2/1/6 unit 0 family inet address 172.16.0.4/24 set interfaces lo0 unit 0 family inet address 192.0.2.6/24 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface ge-2/1/6.0
设备 PE1
set interfaces ge-2/0/5 encapsulation ethernet-ccc set interfaces ge-2/0/5 unit 0 description PE1_to_CE1 set interfaces ge-2/0/5 unit 0 family ccc set interfaces fe-2/0/10 unit 0 description to_PE2 set interfaces fe-2/0/10 unit 0 family inet address 10.0.0.1/30 set interfaces fe-2/0/10 unit 0 family mpls set interfaces lo0 unit 0 family inet address 192.0.2.1/24 set protocols mpls interface fe-2/0/10.0 set protocols bgp local-address 192.0.2.1 set protocols bgp group pe-pe type internal set protocols bgp group pe-pe family l2vpn auto-discovery-only set protocols bgp group pe-pe family l2vpn signaling set protocols bgp group pe-pe neighbor 192.0.2.2 set protocols ospf traffic-engineering set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface fe-2/0/10.0 set protocols ldp interface fe-2/0/10.0 set protocols ldp interface lo0.0 set routing-instances FEC129-VPWS instance-type l2vpn set routing-instances FEC129-VPWS interface ge-2/0/5.0 set routing-instances FEC129-VPWS route-distinguisher 192.0.2.1:100 set routing-instances FEC129-VPWS l2vpn-id l2vpn-id:100:100 set routing-instances FEC129-VPWS vrf-target target:100:100 set routing-instances FEC129-VPWS protocols l2vpn site ONE source-attachment-identifier 1 set routing-instances FEC129-VPWS protocols l2vpn site ONE interface ge-2/0/5.0 target-attachment-identifier 2 set routing-options autonomous-system 64510
设备 PE2
set interfaces ge-2/1/7 encapsulation ethernet-ccc set interfaces ge-2/1/7 unit 0 description PE2_to_CE2 set interfaces ge-2/1/7 unit 0 family ccc set interfaces fe-2/0/10 unit 0 description to_PE1 set interfaces fe-2/0/10 unit 0 family inet address 10.0.0.2/30 set interfaces fe-2/0/10 unit 0 family mpls set interfaces lo0 unit 0 family inet address 192.0.2.2/24 set protocols mpls interface fe-2/0/10.0 set protocols bgp local-address 192.0.2.2 set protocols bgp group pe-pe type internal set protocols bgp group pe-pe family l2vpn auto-discovery-only set protocols bgp group pe-pe family l2vpn signaling set protocols bgp group pe-pe neighbor 192.0.2.1 set protocols ospf traffic-engineering set protocols ospf area 0.0.0.0 interface fe-2/0/10.0 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ldp interface fe-2/0/10.0 set protocols ldp interface lo0.0 set routing-instances FEC129-VPWS instance-type l2vpn set routing-instances FEC129-VPWS interface ge-2/1/7.0 set routing-instances FEC129-VPWS route-distinguisher 192.0.2.2:100 set routing-instances FEC129-VPWS l2vpn-id l2vpn-id:100:100 set routing-instances FEC129-VPWS vrf-target target:100:100 set routing-instances FEC129-VPWS protocols l2vpn site TWO source-attachment-identifier 2 set routing-instances FEC129-VPWS protocols l2vpn site TWO interface ge-2/1/7.0 target-attachment-identifier 1 set routing-options autonomous-system 64510
程序
逐步过程
要配置 FEC 129 VPWS:
-
配置接口。
[edit interfaces] user@PE1# set ge-2/0/5 encapsulation ethernet-ccc user@PE1# set ge-2/0/5 unit 0 description PE1_to_CE1 user@PE1# set ge-2/0/5 unit 0 family ccc user@PE1# set fe-2/0/10 unit 0 description to_PE2 user@PE1# set fe-2/0/10 unit 0 family inet address 10.0.0.1/30 user@PE1# set fe-2/0/10 unit 0 family mpls user@PE1# set lo0 unit 0 family inet address 192.0.2.1/24
-
在面向核心的接口上配置 MPLS。
[edit protocols mpls] user@PE1# set interface fe-2/0/10.0
-
配置 BGP。
[edit protocols bgp] user@PE1# set local-address 192.0.2.1 user@PE1# set group pe-pe type internal user@PE1# set group pe-pe family l2vpn auto-discovery-only user@PE1# set group pe-pe family l2vpn signaling user@PE1# set group pe-pe neighbor 192.0.2.2
-
配置内部网关协议,如 IS-IS 或 OSPF。
如果使用 OSPF,请启用流量工程。默认情况下,IS-IS 支持流量工程。
[edit protocols ospf] user@PE1# set traffic-engineering user@PE1# set area 0.0.0.0 interface lo0.0 passive user@PE1# set area 0.0.0.0 interface fe-2/0/10.0
-
在面向核心的接口和环路接口上配置 LDP。
[edit protocols ldp] user@PE1# set interface fe-2/0/10.0 user@PE1# set interface lo0.0
-
配置 VPWS 路由实例。
LDP 侦听为 FEC 129 VPWS 配置的任何实例的实例的路由。这些路由由
instance-type l2vpn路由实例中的语句和语句存在l2vpn-id标识。请确保该
target-attachment-identifier站点与远程 PE 设备的相应站点匹配source-attachment-identifier。在此示例中,在设备 PE1 和设备 PE2 之间建立了伪线。设备 PE1 使用 SAI 1 和 TAI 2,而设备 PE2 则使用相反的 SAI 2 和 TAI 1。[edit routing-instances FEC129-VPWS] user@PE1# set instance-type l2vpn user@PE1# set interface ge-2/0/5.0 user@PE1# set route-distinguisher 192.0.2.1:100 user@PE1# set l2vpn-id l2vpn-id:100:100 user@PE1# set vrf-target target:100:100 user@PE1# set protocols l2vpn site ONE source-attachment-identifier 1 user@PE1# set protocols l2vpn site ONE interface ge-2/0/5.0 target-attachment-identifier 2
-
配置自治系统 (AS) 编号。
[edit routing-options] user@PE1# set autonomous-system 64510
-
完成设备配置后,提交配置。
[edit] user@PE1# commit
结果
在配置模式下,输入 、 、 show protocolsshow routing-instances和show routing-options命令,show interfaces以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以更正配置。
user@PE1# show interfaces
ge-2/0/5 {
encapsulation ethernet-ccc;
unit 0 {
description PE1_to_CE1;
family ccc;
}
}
fe-2/0/10 {
unit 1 {
description to_PE2;
family inet {
address 10.0.0.1/30;
}
family mpls;
}
}
lo0 {
unit 0 {
family inet {
address 192.0.2.1/24;
}
}
}
user@PE1# show protocols
mpls {
interface fe-2/0/10.0;
}
bgp {
local-address 192.0.2.1;
group pe-pe {
type internal;
family l2vpn {
auto-discovery-only;
inactive: signaling;
}
neighbor 192.0.2.2;
}
}
ospf {
traffic-engineering;
area 0.0.0.0 {
interface lo0.0 {
passive;
}
interface fe-2/0/10.0;
}
}
ldp {
interface fe-2/0/10.0;
interface lo0.0;
}
user@PE1# show routing-instances
FEC129-VPWS {
instance-type l2vpn;
interface ge-2/0/5.0;
route-distinguisher 192.0.2.1:100;
l2vpn-id l2vpn-id:100:100;
vrf-target target:100:100;
protocols {
l2vpn {
site ONE {
source-attachment-identifier 1;
interface ge-2/0/5.0 {
target-attachment-identifier 2;
}
}
}
}
}
user@PE1# show routing-options autonomous-system 64510;
验证
确认配置工作正常。
验证路由
目的
验证是否已学习到预期的路由。
行动
在操作模式下,输入 show route 命令。
user@PE1> show route
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.0.2.1/24 *[Direct/0] 6d 21:16:32
> via lo0.0
192.0.2.2/24 *[OSPF/10] 6d 21:15:31, metric 1
> to 10.0.0.2 via fe-2/0/10.0
10.0.0.0/30 *[Direct/0] 6d 21:16:31
> via fe-2/0/10.0
10.0.0.1/32 *[Local/0] 6d 21:16:32
Local via fe-2/0/10.0
203.0.113.0/24 *[OSPF/10] 6d 21:16:34, metric 1
MultiRecv
inet.3: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.0.2.2/24 *[LDP/9] 5d 22:25:19, metric 1
> to 10.0.0.2 via fe-2/0/10.0
mpls.0: 8 destinations, 8 routes (8 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
0 *[MPLS/0] 6d 21:16:33, metric 1
Receive
1 *[MPLS/0] 6d 21:16:33, metric 1
Receive
2 *[MPLS/0] 6d 21:16:33, metric 1
Receive
13 *[MPLS/0] 6d 21:16:33, metric 1
Receive
299808 *[LDP/9] 5d 22:25:19, metric 1
> to 10.0.0.2 via fe-2/0/10.0, Pop
299808(S=0) *[LDP/9] 5d 22:25:19, metric 1
> to 10.0.0.2 via fe-2/0/10.0, Pop
299824 *[L2VPN/7] 5d 22:25:18
> via ge-2/0/5.0, Pop
ge-2/0/5.0 *[L2VPN/7] 5d 22:13:02, metric2 1
> to 10.0.0.2 via fe-2/0/10.0, Push 299872
bgp.l2vpn.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.0.2.2:100:0.0.0.2/96 AD
*[BGP/170] 6d 20:51:23, localpref 100, from 192.0.2.2
AS path: I, validation-state: unverified
> to 10.0.0.2 via fe-2/0/10.0
ldp.l2vpn.0: 1 destinations, 1 routes (1 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.0.2.2:NoCtrlWord:5:100:100:0.0.0.2:0.0.0.1/176
*[LDP/9] 5d 22:13:02
Discard
FEC129-VPWS.l2vpn.0: 4 destinations, 4 routes (4 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
192.0.2.1:100:0.0.0.1/96 AD
*[L2VPN/170] 6d 20:53:26, metric2 1
Indirect
192.0.2.2:100:0.0.0.2/96 AD
*[BGP/170] 6d 20:51:23, localpref 100, from 192.0.2.2
AS path: I, validation-state: unverified
> to 10.0.0.2 via fe-2/0/10.0
192.0.2.2:NoCtrlWord:5:100:100:0.0.0.1:0.0.0.2/176
*[L2VPN/7] 6d 20:51:23, metric2 1
> to 10.0.0.2 via fe-2/0/10.0
192.0.2.2:NoCtrlWord:5:100:100:0.0.0.2:0.0.0.1/176
*[LDP/9] 5d 22:13:02
Discard
意义
输出显示所有学习的路由,包括自动发现 (AD) 路由。
检查 CE 设备之间的连接
目的
验证设备 CE1 是否可以对设备 CE2 执行 ping 操作。
行动
user@CE1> ping 192.0.2.6 PING 192.0.2.6 (192.0.2.6): 56 data bytes 64 bytes from 192.0.2.6: icmp_seq=0 ttl=64 time=0.679 ms 64 bytes from 192.0.2.6: icmp_seq=1 ttl=64 time=0.524 ms ^C --- 192.0.2.6 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.524/0.602/0.679/0.078 ms
意义
输出显示 VPWS 可正常运行。
检查 VPWS 连接
目的
请确保所有 FEC 129 VPWS 连接均正确连接。
行动
user@PE1> show l2vpn connections
Layer-2 VPN connections:
Legend for connection status (St)
EI -- encapsulation invalid NC -- interface encapsulation not CCC/TCC/VPLS
EM -- encapsulation mismatch WE -- interface and instance encaps not same
VC-Dn -- Virtual circuit down NP -- interface hardware not present
CM -- control-word mismatch -> -- only outbound connection is up
CN -- circuit not provisioned <- -- only inbound connection is up
OR -- out of range Up -- operational
OL -- no outgoing label Dn -- down
LD -- local site signaled down CF -- call admission control failure
RD -- remote site signaled down SC -- local and remote site ID collision
LN -- local site not designated LM -- local site ID not minimum designated
RN -- remote site not designated RM -- remote site ID not minimum designated
XX -- unknown connection status IL -- no incoming label
MM -- MTU mismatch MI -- Mesh-Group ID not available
BK -- Backup connection ST -- Standby connection
PF -- Profile parse failure PB -- Profile busy
RS -- remote site standby SN -- Static Neighbor
LB -- Local site not best-site RB -- Remote site not best-site
VM -- VLAN ID mismatch
Legend for interface status
Up -- operational
Dn -- down
Instance: FEC129-VPWS
L2vpn-id: 100:100
Local source-attachment-id: 1 (ONE)
Target-attachment-id Type St Time last up # Up trans
2 rmt Up Nov 28 16:16:14 2012 1
Remote PE: 192.0.2.2, Negotiated control-word: No
Incoming label: 299792, Outgoing label: 299792
Local interface: ge-2/0/5.0, Status: Up, Encapsulation: ETHERNET
意义
不出所料,连接已启动。输出包括源附件 ID 和目标附件 ID。
检查 PE 设备之间的连接
目的
验证设备 PE1 是否可以对设备 PE2 执行 ping 操作。命令ping mpls l2vpn fec129接受 SAI 和 TA 作为整数或 IP 地址,还允许您使用面向 CE 的接口,而不是其他参数 (instance、 local-id、 remote-idremote-pe-address)。
行动
user@PE1> ping mpls l2vpn fec129 instance FEC129-VPWS remote-id 2 remote-pe-address 192.0.2.2 local-id 1 !!!!! --- lsping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss
user@PE1> ping mpls l2vpn fec129 interface ge-2/0/5.0 !!!!! --- lsping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss
意义
输出显示 VPWS 可正常运行。