示例:为 EX 系列交换机上的端口、VLAN 和路由器流量配置防火墙过滤器
此示例说明如何配置和应用防火墙过滤器,以控制进出交换机端口、网络上的 VLAN 和交换机上的第 3 层接口的流量。防火墙过滤器定义用于确定是在数据包流中的特定处理点转发还是拒绝数据包的规则。
要求
此示例使用以下软件和硬件组件:
适用于 EX 系列交换机的 Junos OS 9.0 或更高版本。
两台瞻博网络 EX3200-48T 交换机:一个用作接入交换机,另一个用作分配交换机
一个瞻博网络 EX-UM-4SFP 上行链路模块
一台瞻博网络 J 系列路由器
在此示例中配置和应用防火墙过滤器之前,请确保您已:
了解防火墙过滤器概念、监管器和 CoS
已在配电交换机中安装上行链路模块。请参阅 在 EX3200 交换机中安装上行链路模块。
概述
此配置示例说明如何配置和应用防火墙过滤器,以提供规则来评估数据包的内容,并确定何时丢弃、转发、分类、计数和分析发往或源自处理所有 、 和 流量的 EX 系列交换机的数据包。 显示了此示例中为 EX 系列交换机配置的防火墙过滤器。voice-vlanemployee-vlanguest-vlan表 1
| 组件 | 用途/描述 |
|---|---|
端口防火墙过滤器, |
此防火墙过滤器执行两个功能:
此防火墙过滤器应用于接入交换机上的端口接口。 |
VLAN 防火墙过滤器, |
防止恶意设备使用 HTTP 会话来模仿管理 VoIP 呼叫的呼叫注册、准入和呼叫状态的网守设备。仅应使用 TCP 或 UDP 端口;而且只有网守使用 HTTP。也就是说,TCP 端口上的所有 流量都应发往网守设备。 此防火墙过滤器应用于接入交换机上的 VLAN 接口。 |
VLAN 防火墙过滤器, |
接受 发往企业子网的流量,但不监控此流量。 此防火墙过滤器应用于接入交换机上的 VLAN 接口。 |
VLAN 防火墙过滤器, |
防止访客(非员工)在 上 与员工或员工主持人交谈。 此防火墙过滤器应用于接入交换机上的 VLAN 接口。 |
路由器防火墙过滤器, |
确定 流量的优先级,为发往公司子网的员工流量提供最高的转发类优先级。 此防火墙过滤器应用于分布式交换机上的路由端口(第 3 层上行链路模块)。 |
图 1 显示了交换机上端口、VLAN 和第 3 层路由防火墙过滤器的应用。
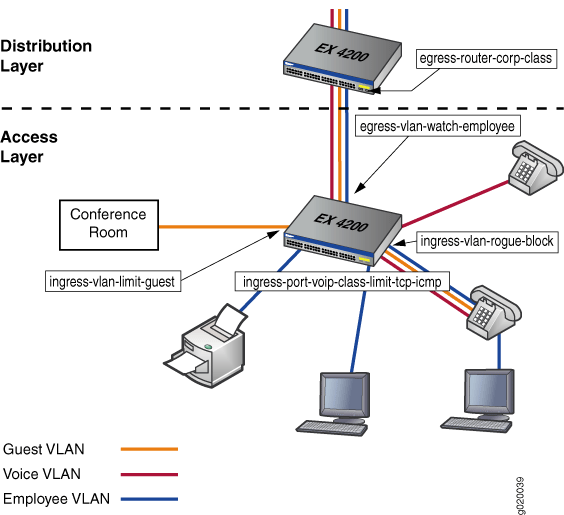
网络拓扑
此配置示例的拓扑由接入层的一台 EX-3200-48T 交换机和分布层的一台 EX-3200-48T 交换机组成。分布交换机的上行链路模块配置为支持与 J 系列路由器的第 3 层连接。
EX 系列交换机配置为支持 VLAN 成员资格。 显示了 VLAN 的 VLAN 配置组件。表 2
VLAN 名称 |
虚拟帧 ID |
VLAN 子网和可用 IP 地址 |
VLAN 说明 |
|---|---|---|---|
|
|
|
用于员工 VoIP 流量的语音 VLAN |
|
|
通过 是子网的广播地址 |
VLAN 独立 PC、通过 VoIP 电话、无线接入点和打印机中的集线器连接到网络的 PC。此 VLAN 完全包含语音 VLAN。必须在连接到电话的端口上配置两个 VLAN 和 )。 |
|
|
通过 是子网的广播地址 |
访客数据设备 (PC) 的 VLAN。该方案假定公司有一个向访客开放的区域,无论是在大厅还是在会议室中,该区域都有一个集线器,访客可以插入其 PC 以连接到 Web 和公司的 VPN。 |
|
|
通过 是子网的广播地址 |
用于企业安全摄像头的 VLAN。 |
EX 系列交换机上的端口支持以太网供电 (PoE),为连接到端口的 VoIP 电话提供网络连接和电源。 显示分配给 VLAN 的交换机端口以及连接到交换机端口的设备的 IP 和 MAC 地址:表 3
交换机和端口号 |
VLAN 成员资格 |
IP 和 MAC 地址 |
端口设备 |
|---|---|---|---|
ge-0/0/0, ge-0/0/1 |
|
IP 地址: MAC 地址: |
两个VoIP电话,每个电话连接到一台PC。 |
ge-0/0/2, ge-0/0/3 |
|
|
打印机、无线接入点 |
ge-0/0/4, ge-0/0/5 |
|
|
两个集线器,访客可以将他们的 PC 插入其中。枢纽位于对访客开放的区域,如大堂或会议室 |
ge-0/0/6, ge-0/0/7 |
|
|
两个安全摄像头 |
ge-0/0/9 |
|
IP 地址: MAC 地址: |
网守设备。网守管理 VoIP 电话的呼叫注册、准入和呼叫状态。 |
ge-0/1/0 |
IP 地址: |
与路由器的第 3 层连接;请注意,这是交换机上行链路模块上的端口 |
配置入口端口防火墙过滤器以优先处理语音流量并限制 TCP 和 ICMP 流量的速率
要为端口、VLAN 和路由器接口配置和应用防火墙过滤器,请执行以下操作:
程序
CLI 快速配置
要快速配置和应用端口防火墙过滤器,以确定发往 子网的语音流量和速率限制数据包的优先级,请复制以下命令并将其粘贴到交换机终端窗口中:employee-vlan
[edit]
set firewall policer tcp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m
set firewall policer tcp-connection-policer then discard
set firewall policer icmp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m
set firewall policer icmp-connection-policer then discard
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from source-mac-address 00.00.5E.00.53.01
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from source-mac-address 00.00.5E.00.53.02
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high from protocol udp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high then forwarding-class expedited-forwarding
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term voip-high then loss-priority low
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control from precedence net-control
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control then forwarding-class network-control
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term network-control then loss-priority low
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection from protocol tcp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then policer tcp-connection-policer
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then count tcp-counter
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term tcp-connection then loss-priority high
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection from protocol icmp
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then policer icmp-connection-policer
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then count icmp-counter
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term icmp-connection then loss-priority high
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term best-effort then forwarding-class best-effort
set firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp term best-effort then loss-priority high
set interfaces ge-0/0/0 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port"
set interfaces ge-0/0/0 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
set interfaces ge-0/0/1 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port"
set interfaces ge-0/0/1 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
set class-of-service schedulers voice-high buffer-size percent 15
set class-of-service schedulers voice-high priority high
set class-of-service schedulers net-control buffer-size percent 10
set class-of-service schedulers net-control priority high
set class-of-service schedulers best-effort buffer-size percent 75
set class-of-service schedulers best-effort priority low
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class expedited-forwarding scheduler voice-high
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class network-control scheduler net-control
set class-of-service scheduler-maps ethernet-diffsrv-cos-map forwarding-class best-effort scheduler best-effort 分步过程
要配置并应用端口防火墙过滤器,以确定发往 子网的语音流量和速率限制数据包的优先级,请执行以下操作:employee-vlan
定义监管器和:
tcp-connection-policericmp-connection-policer[edit] user@switch# set firewall policer tcp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m user@switch# set firewall policer tcp-connection-policer then discard user@switch# set firewall policer icmp-connection-policer if-exceeding burst-size-limit 30k bandwidth-limit 1m user@switch# set firewall policer icmp-connection-policer then discard
定义防火墙过滤器 :
ingress-port-voip-class-limit-tcp-icmp[edit firewall] user@switch# set family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp
定义术语 :
voip-high[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp ] user@switch# set term voip-high from source-mac-address 00.00.5E.00.53.01 user@switch# set term voip-high from source-mac-address 00.00.5E.00.53.02 user@switch# set term voip-high from protocol udp user@switch# set term voip-high then forwarding-class expedited-forwarding user@switch# set term voip-high then loss-priority low
定义术语 :
network-control[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp ] user@switch# set term network-control from precedence net-control user@switch# set term network-control then forwarding-class network-control user@switch# set term network-control then loss-priority low
定义术语 以配置 TCP 流量的速率限制:
tcp-connection[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term tcp-connection from destination-address 192.0.2.16/28 user@switch# set term tcp-connection from protocol tcp user@switch# set term tcp-connection then policer tcp-connection-policer user@switch# set term tcp-connection then count tcp-counter user@switch# set term tcp-connection then forwarding-class best-effort user@switch# set term tcp-connection then loss-priority high
定义术语以 配置 ICMP 流量的速率限制:
icmp-connection[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term icmp-connection from destination-address 192.0.2.16/28 user@switch# set term icmp-connection from protocol icmp user@switch# set term icmp-connection then policer icmp-policer user@switch# set term icmp-connection then count icmp-counter user@switch# set term icmp-connection then forwarding-class best-effort user@switch# set term icmp-connection then loss-priority high
在防火墙过滤器中与任何其他术语不匹配的所有数据包上定义没有匹配条件的术语 :
best-effort[edit firewall family ethernet-switching filter ingress-port-voip-class-limit-tcp-icmp] user@switch# set term best-effort then forwarding-class best-effort user@switch# set term best-effort then loss-priority high
将防火墙过滤器作为输入过滤器 应用于以下端口 接口:
ingress-port-voip-class-limit-tcp-icmpemployee-vlan[edit interfaces] user@switch# set ge-0/0/0 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port" user@switch# set ge-0/0/0 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp user@switch# set ge-0/0/1 description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port" user@switch# set ge-0/0/1 unit 0 family ethernet-switching filter input ingress-port-voip-class-limit-tcp-icmp
配置不同调度程序所需的参数。
注:为调度程序配置参数时,请定义与网络流量模式匹配的数字。
[edit class-of-service] user@switch# set schedulers voice-high buffer-size percent 15 user@switch# set schedulers voice-high priority high user@switch# set schedulers network—control buffer-size percent 10 user@switch# set schedulers network—control priority high user@switch# set schedulers best-effort buffer-size percent 75 user@switch# set schedulers best-effort priority low
使用调度器图将转发类分配给调度器:
[edit class-of-service] user@switch# set scheduler-maps ethernet-diffsrv-cos-map user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class expedited-forwarding scheduler voice-high user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class network-control scheduler net-control user@switch# set scheduler-maps ethernet-diffsrv-cos-map forwarding-class best-effort scheduler best-effort
将调度器图与传出接口关联:
[edit class-of-service] user@switch# set interfaces ge–0/1/0 scheduler-map ethernet-diffsrv-cos-map
成果
显示配置结果:
user@switch# show
firewall {
policer tcp-connection-policer {
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 30k;
}
then {
discard;
}
}
policer icmp-connection-policer {
if-exceeding {
bandwidth-limit 1m;
burst-size-limit 30k;
}
then {
discard;
}
}
family ethernet-switching {
filter ingress-port-voip-class-limit-tcp-icmp {
term voip-high {
from {
destination-mac-address 00.00.5E.00.53.01;
destination-mac-address 00.00.5E.00.53.02;
protocol udp;
}
then {
forwarding-class expedited-forwarding;
loss-priority low;
}
}
term network-control {
from {
precedence net-control ;
}
then {
forwarding-class network-control;
loss-priority low;
}
}
term tcp-connection {
from {
destination-address 192.0.2.16/28;
protocol tcp;
}
then {
policer tcp-connection-policer;
count tcp-counter;
forwarding-class best-effort;
loss-priority high;
}
}
term icmp-connection
from {
protocol icmp;
}
then {
policer icmp-connection-policer;
count icmp-counter;
forwarding-class best-effort;
loss-priority high;
}
}
term best-effort {
then {
forwarding-class best-effort;
loss-priority high;
}
}
}
}
}
interfaces {
ge-0/0/0 {
description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port";
unit 0 {
family ethernet-switching {
filter {
input ingress-port-voip-class-limit-tcp-icmp;
}
}
}
}
ge-0/0/1 {
description "voice priority and tcp and icmp traffic rate-limiting filter at ingress port";
unit 0 {
family ethernet-switching {
filter {
input ingress-port-voip-class-limit-tcp-icmp;
}
}
}
}
}
scheduler-maps {
ethernet-diffsrv-cos-map {
forwarding-class expedited-forwarding scheduler voice-high;
forwarding-class network-control scheduler net-control;
forwarding-class best-effort scheduler best-effort;
}
}
interfaces {
ge/0/1/0 {
scheduler-map ethernet-diffsrv-cos-map;
}
}
配置 VLAN 入口防火墙过滤器以防止恶意设备中断 VoIP 流量
要为端口、VLAN 和路由器接口配置和应用防火墙过滤器,请执行以下操作:
程序
CLI 快速配置
要快速配置 VLAN 防火墙过滤器以防止恶意设备使用 HTTP 会话来模仿管理 VoIP 流量的网守设备,请复制以下命令并将其粘贴到交换机终端窗口中:voice-vlan
[edit]
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper from destination-address 192.0.2.14
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper from destination-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term to-gatekeeper then accept
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper from source-address 192.0.2.14
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper from source-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term from-gatekeeper then accept
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper from destination-port 80
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper then count rogue-counter
set firewall family ethernet-switching filter ingress-vlan-rogue-block term not-gatekeeper then discard
set vlans voice-vlan description "block rogue devices on voice-vlan"
set vlans voice-vlan filter input ingress-vlan-rogue-block 分步过程
要配置 并应用 VLAN 防火墙过滤器以防止恶意设备使用 HTTP 模仿管理 VoIP 流量的网守设备,请执行以下操作:voice-vlan
定义防火墙过滤器,以指定与要允许和限制的流量匹配的过滤器 :
ingress-vlan-rogue-block[edit firewall] user@switch# set family ethernet-switching filter ingress-vlan-rogue-block
定义术语以 接受与网守目标 IP 地址匹配的数据包:
to-gatekeeper[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term to-gatekeeper from destination-address 192.0.2.14 user@switch# set term to-gatekeeper from destination-port 80 user@switch# set term to-gatekeeper then accept
定义术语以 接受与网守的源 IP 地址匹配的数据包:
from-gatekeeper[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term from-gatekeeper from source-address 192.0.2.14 user@switch# set term from-gatekeeper from source-port 80 user@switch# set term from-gatekeeper then accept
定义术语 以确保 TCP 端口上的所有 流量都发往网守设备:
not-gatekeepervoice-vlan[edit firewall family ethernet-switching filter ingress-vlan-rogue-block] user@switch# set term not-gatekeeper from destination-port 80 user@switch# set term not-gatekeeper then count rogue-counter user@switch# set term not-gatekeeper then discard
将防火墙过滤器作为输入过滤器 应用于 VoIP 电话的 VLAN 接口:
ingress-vlan-rogue-block[edit] user@switch# set vlans voice-vlan description "block rogue devices on voice-vlan" user@switch# set vlans voice-vlan filter input ingress-vlan-rogue-block
成果
显示配置结果:
user@switch# show
firewall {
family ethernet-switching {
filter ingress-vlan-rogue-block {
term to-gatekeeper {
from {
destination-address 192.0.2.14/32
destination-port 80;
}
then {
accept;
}
}
term from-gatekeeper {
from {
source-address 192.0.2.14/32
source-port 80;
}
then {
accept;
}
}
term not-gatekeeper {
from {
destination-port 80;
}
then {
count rogue-counter;
discard;
}
}
}
vlans {
voice-vlan {
description "block rogue devices on voice-vlan";
filter {
input ingress-vlan-rogue-block;
}
}
}
配置 VLAN 防火墙过滤器以计数、监控和分析员工 VLAN 上的出口流量
要为端口、VLAN 和路由器接口配置和应用防火墙过滤器,请执行以下操作:
程序
CLI 快速配置
配置防火墙过滤器并将其应用于 VLAN 接口以过滤 出口流量。employee-vlan 发往公司子网的员工流量将被接受,但不会受到监控。对发往 Web 的员工流量进行计数和分析。
要快速配置和应用 VLAN 防火墙过滤器,请复制以下命令并将其粘贴到交换机终端窗口中:
[edit]
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-corp from destination-address 192.0.2.16/28
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-corp then accept
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web from destination-port 80
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web then count employee-web-counter
set firewall family ethernet-switching filter egress-vlan-watch-employee term employee-to-web then analyzer employee-monitor
set vlans employee-vlan description "filter at egress VLAN to count and analyze employee to Web traffic"
set vlans employee-vlan filter output egress-vlan-watch-employee 分步过程
要配置和应用出口端口防火墙过滤器来计算和分析 发往 Web 的流量,请执行以下操作:employee-vlan
定义防火墙过滤器 :
egress-vlan-watch-employee[edit firewall] user@switch# set family ethernet-switching filter egress-vlan-watch-employee
定义术语以 接受但不监控发往企业子网的所有 流量:
employee-to-corpemployee-vlan[edit firewall family ethernet-switching filter egress-vlan-watch-employee] user@switch# set term employee-to-corp from destination-address 192.0.2.16/28 user@switch# set term employee-to-corp then accept
定义术语 来计算和监控发往 Web 的所有 流量:
employee-to-webemployee-vlan[edit firewall family ethernet-switching filter egress-vlan-watch-employee] user@switch# set term employee-to-web from destination-port 80 user@switch# set term employee-to-web then count employee-web-counter user@switch# set term employee-to-web then analyzer employee-monitor
注:请参阅 示例:配置端口镜像以本地监控 EX 系列交换机 上的员工资源使用情况 有关配置 分析器的信息。
employee-monitor将防火墙过滤器作为输出过滤器 应用于 VoIP 电话的端口接口:
egress-vlan-watch-employee[edit] user@switch# set vlans employee-vlan description "filter at egress VLAN to count and analyze employee to Web traffic" user@switch# set vlans employee-vlan filter output egress-vlan-watch-employee
成果
显示配置结果:
user@switch# show
firewall {
family ethernet-switching {
filter egress-vlan-watch-employee {
term employee-to-corp {
from {
destination-address 192.0.2.16/28
}
then {
accept;
}
}
term employee-to-web {
from {
destination-port 80;
}
then {
count employee-web-counter:
analyzer employee-monitor;
}
}
}
}
}
vlans {
employee-vlan {
description "filter at egress VLAN to count and analyze employee to Web traffic";
filter {
output egress-vlan-watch-employee;
}
}
}
配置 VLAN 防火墙过滤器以限制访客 VLAN 上的访客到员工流量和对等应用程序
要为端口、VLAN 和路由器接口配置和应用防火墙过滤器,请执行以下操作:
程序
CLI 快速配置
在以下示例中,第一个筛选器术语允许来宾与其他来宾交谈,但不允许员工在 上 交谈。employee-vlan 第二个筛选器术语允许来宾进行 Web 访问,但阻止来宾在 上使用 对等应用程序。guest-vlan
要快速配置 VLAN 防火墙过滤器以限制访客与员工之间的流量,阻止访客与 上的 员工或员工主机交谈或尝试在 上 使用对等应用程序,请复制以下命令并将其粘贴到交换机终端窗口中:employee-vlanguest-vlan
[edit]
set firewall family ethernet-switching filter ingress-vlan-limit-guest term guest-to-guest from destination-address 192.0.2.33/28
set firewall family ethernet-switching filter ingress-vlan-limit-guest term guest-to-guest then accept
set firewall family ethernet-switching filter ingress-vlan-limit-guest term no-guest-employee-no-peer-to-peer from destination-mac-address 00.05.5E.00.00.DF
set firewall family ethernet-switching filter ingress-vlan-limit-guest term no-guest-employee-no-peer-to-peer then accept
set vlans guest-vlan description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN"
set vlans guest-vlan forwarding-options filter input ingress-vlan-limit-guest 分步过程
要配置和应用 VLAN 防火墙过滤器以限制访客到员工的流量和对等应用程序 ,请执行以下操作:guest-vlan
定义防火墙过滤器 :
ingress-vlan-limit-guest[edit firewall] set firewall family ethernet-switching filter ingress-vlan-limit-guest定义术语 以允许 上的 来宾与其他来宾交谈,但不允许 上的 员工交谈:
guest-to-guestguest-vlanemployee-vlan[edit firewall family ethernet-switching filter ingress-vlan-limit-guest] user@switch# set term guest-to-guest from destination-address 192.0.2.33/28 user@switch# set term guest-to-guest then accept
定义术语以允许 Web 上的来宾访问,但阻止他们在 上使用 上的对等应用程序。
no-guest-employee-no-peer-to-peerguest-vlanguest-vlan注:是 默认网关,对于 VLAN 中的任何主机,它是下一跃点路由器。
destination-mac-address[edit firewall family ethernet-switching filter ingress-vlan-limit-guest] user@switch# set term no-guest-employee-no-peer-to-peer from destination-mac-address 00.05.5E.00.00.DF user@switch# set term no-guest-employee-no-peer-to-peer then accept
将防火墙过滤器作为输入过滤器 应用于以下接口 :
ingress-vlan-limit-guestguest-vlan[edit] user@switch# set vlans guest-vlan description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN" user@switch# set vlans guest-vlan forwarding-options filter input ingress-vlan-limit-guest
成果
显示配置结果:
user@switch# show
firewall {
family ethernet-switching {
filter ingress-vlan-limit-guest {
term guest-to-guest {
from {
destination-address 192.0.2.33/28;
}
then {
accept;
}
}
term no-guest-employee-no-peer-to-peer {
from {
destination-mac-address 00.05.5E.00.00.DF;
}
then {
accept;
}
}
}
}
}
vlans {
guest-vlan {
description "restrict guest-to-employee traffic and peer-to-peer applications on guest VLAN";
filter {
input ingress-vlan-limit-guest;
}
}
}
配置路由器防火墙过滤器以优先处理发往企业子网的出口流量
要为端口、VLAN 和路由器接口配置和应用防火墙过滤器,请执行以下操作:
程序
CLI 快速配置
要为路由端口(第 3 层上行链路模块)快速配置防火墙过滤器以过滤 流量,从而为发往企业子网的流量提供最高转发类优先级,请复制以下命令并将其粘贴到交换机终端窗口中:employee-vlan
[edit]
set firewall family inet filter egress-router-corp-class term corp-expedite from destination-address 192.0.2.16/28
set firewall family inet filter egress-router-corp-class term corp-expedite then forwarding-class expedited-forwarding
set firewall family inet filter egress-router-corp-class term corp-expedite then loss-priority low
set firewall family inet filter egress-router-corp-class term not-to-corp then accept
set interfaces ge-0/1/0 description "filter at egress router to expedite destined for corporate network"
set ge-0/1/0 unit 0 family inet address 203.0.113.0
set interfaces ge-0/1/0 unit 0 family inet filter output egress-router-corp-class 分步过程
要配置防火墙过滤器并将其应用于路由端口(第 3 层上行链路模块),以便为发往企业子网的流量提供 最高优先级:employee-vlan
定义防火墙过滤器 :
egress-router-corp-class[edit] user@switch# set firewall family inet filter egress-router-corp-class
定义术语 :
corp-expedite[edit firewall] user@switch# set family inet filter egress-router-corp-class term corp-expedite from destination-address 192.0.2.16/28 user@switch# set family inet filter egress-router-corp-class term corp-expedite then forwarding-class expedited-forwarding user@switch# set family inet filter egress-router-corp-class term corp-expedite then loss-priority low
定义术语 :
not-to-corp[edit firewall] user@switch# set family inet filter egress-router-corp-class term not-to-corp then accept
将防火墙过滤器用作交换机上行链路模块上端口的输出过滤器 ,该模块提供与路由器的第 3 层连接:
egress-router-corp-class[edit interfaces] user@switch# set ge-0/1/0 description "filter at egress router to expedite employee traffic destined for corporate network" user@switch# set ge-0/1/0 unit 0 family inet address 203.0.113.0 user@switch# set ge-0/1/0 unit 0 family inet filter output egress-router-corp-class
成果
显示配置结果:
user@switch# show
firewall {
family inet {
filter egress-router-corp-class {
term corp-expedite {
from {
destination-address 192.0.2.16/28;
}
then {
forwarding-class expedited-forwarding;
loss-priority low;
}
}
term not-to-corp {
then {
accept;
}
}
}
}
}
interfaces {
ge-0/1/0 {
unit 0 {
description "filter at egress router interface to expedite employee traffic destined for corporate network";
family inet {
source-address 203.0.113.0
filter {
output egress-router-corp-class;
}
}
}
}
}
验证
要确认防火墙过滤器工作正常,请执行以下任务:
验证防火墙过滤器和监管器是否正常运行
目的
验证交换机上配置的防火墙过滤器和监管器的运行状态。
操作
使用操作模式命令:
user@switch> show firewall Filter: ingress-port-voip-class-limit-tcp-icmp Counters: Name Packets icmp-counter 0 tcp-counter 0 Policers: Name Packets icmp-connection-policer 0 tcp-connection-policer 0 Filter: ingress-vlan-rogue-block Filter: egress-vlan-watch-employee Counters: Name Packets employee-web—counter 0
意义
该 命令将显示交换机上配置的防火墙过滤器、监管器和计数器的名称。show firewall 输出字段显示所有已配置计数器的字节和数据包计数以及所有监管器的数据包计数。
验证调度程序和调度器映射是否正常运行
目的
验证调度程序和调度程序图在交换机上是否正常运行。
操作
使用操作模式命令:
user@switch> show class-of-service scheduler-map
Scheduler map: default, Index: 2
Scheduler: default-be, Forwarding class: best-effort, Index: 20
Transmit rate: 95 percent, Rate Limit: none, Buffer size: 95 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 default-drop-profile
Low TCP 1 default-drop-profile
High non-TCP 1 default-drop-profile
High TCP 1 default-drop-profile
Scheduler: default-nc, Forwarding class: network-control, Index: 22
Transmit rate: 5 percent, Rate Limit: none, Buffer size: 5 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 default-drop-profile
Low TCP 1 default-drop-profile
High non-TCP 1 default-drop-profile
High TCP 1 default-drop-profileScheduler map: ethernet-diffsrv-cos-map, Index: 21657
Scheduler: best-effort, Forwarding class: best-effort, Index: 61257
Transmit rate: remainder, Rate Limit: none, Buffer size: 75 percent,
Priority: low
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
Scheduler: voice-high, Forwarding class: expedited-forwarding, Index: 3123
Transmit rate: remainder, Rate Limit: none, Buffer size: 15 percent,
Priority: high
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
Scheduler: net-control, Forwarding class: network-control, Index: 2451
Transmit rate: remainder, Rate Limit: none, Buffer size: 10 percent,
Priority: high
Drop profiles:
Loss priority Protocol Index Name
Low non-TCP 1 <default-drop-profile>
Low TCP 1 <default-drop-profile>
High non-TCP 1 <default-drop-profile>
High TCP 1 <default-drop-profile>
意义
显示有关已配置调度程序和调度程序映射的统计信息。
