本页内容
多节点高可用性中的非对称流量支持
概述
对于有状态服务或执行深度包检测,防火墙需要查看每个流会话的双向。当数据包流使用一条路径(通过节点 1)从源网络遍历到目标网络并采用不同的返回路径(使用节点 2)时,就会发生非对称流量。当流量流经第 3 层路由网络时,可能会发生这种非对称流量。
在典型的高可用性部署中,网络两端都有多个路由器和交换机。路由器使用下一跃点路径转发每个数据包流;但路由器可能不会对返回流量使用相同的路径。在多节点高可用性设置中,路由器根据当前路由路径将数据包发送到防火墙,这可能会导致流量不对称
这种对流量方向的不同处理可能会导致一些数据包被一个或多个高可用性节点丢弃。发生这种情况的原因是两个节点都无法捕获整个流量,从而导致潜在的不一致和丢包。
为了处理非对称流量,多节点高可用性需要一个称为机箱间数据通路 (ICD) 的附加链路。ICD 可以在两个节点之间路由流量。ICD 使节点能够将非对称流量流重定向到最初负责为流提供有状态服务的对等节点。
此功能可确保可以对非对称流量流与传统(强制)对称流量执行安全检查(例如三次握手和带有窗口缩放因子的序列检查)。
多节点高可用性如何支持非对称流量
不支持非对称流量
在多节点高可用性设置中,同一流的双向数据包由相邻路由器或交换机传送到不同的 SRX 系列设备,如图 1 所示
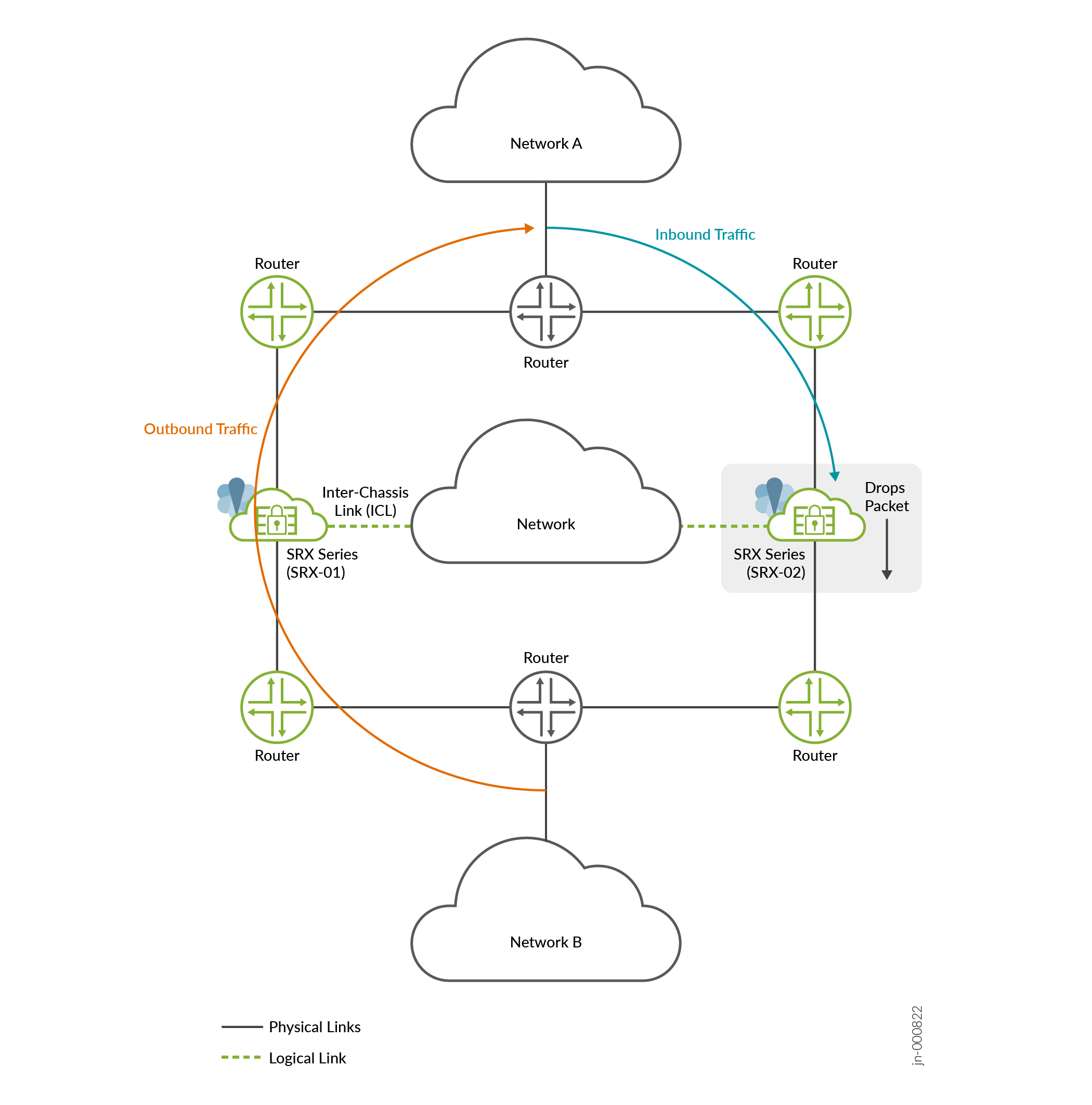 非对称流量的数据包流
非对称流量的数据包流
从网络 B 到网络 A 的出站流量通过节点 1 (SRX-01),返回流量(入站流量)从网络 A 流向网络 B 通过节点 2 (SRX-02)。
在出现非对称流量的情况下,由于缺乏关于同一流量的双向流量的完整状态信息,SRX 系列防火墙(此示例中称为 SRX-02)会丢弃数据包。
支持非对称流量
为了支持非对称流量,多节点高可用性使用机箱间数据通路 (ICD)。ICD 在高可用性设置中转发两个 SRX 系列设备之间的非对称流量数据包。
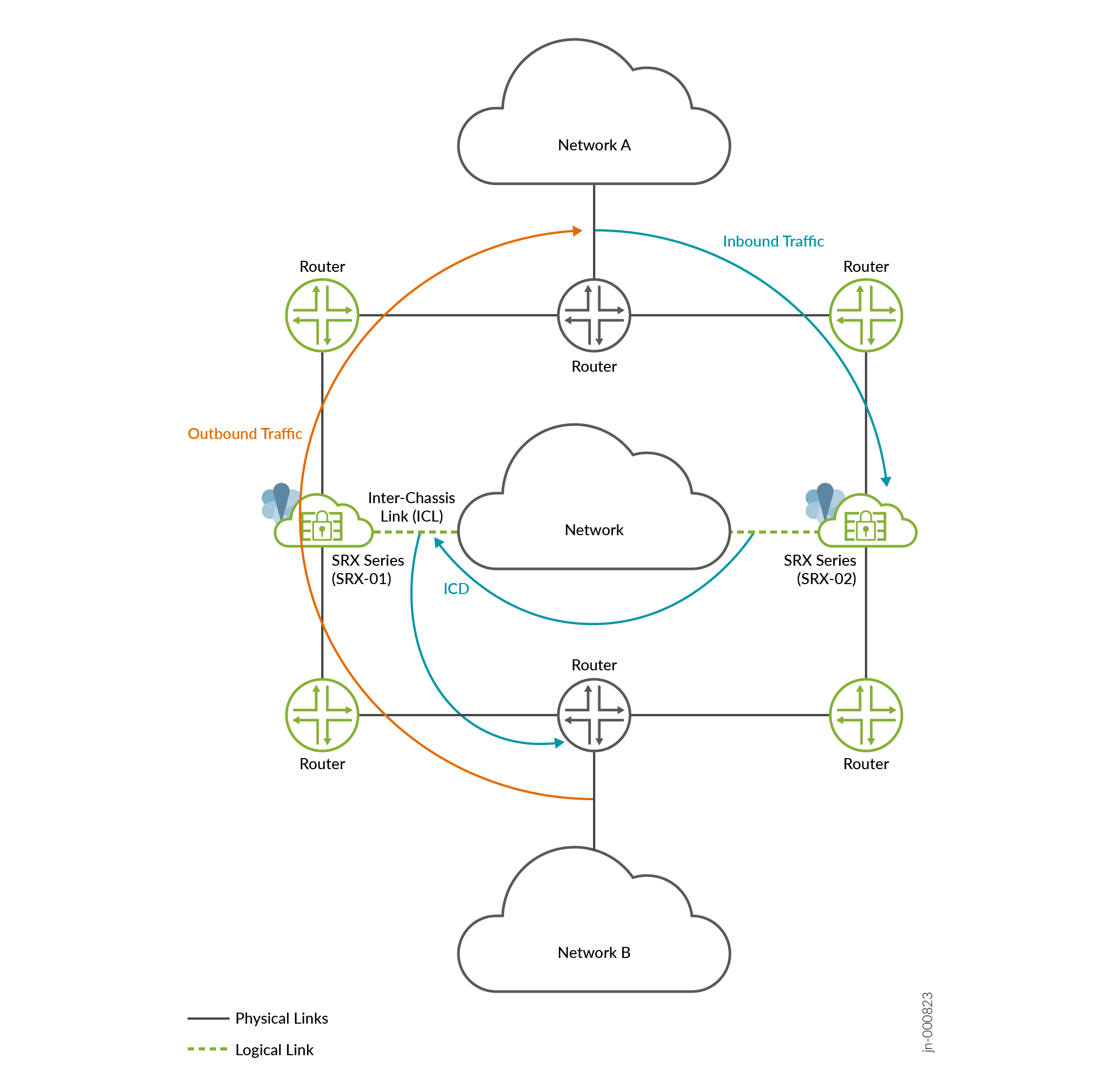 非对称流量的数据包流
非对称流量的数据包流
在这种情况下,多节点高可用性系统将在节点之间创建新的可路由链路。此可路由链路使节点能够将非对称流转发到原始节点,该节点可以对流执行安全检查。也就是说,节点 2 (SRX-02) 将入站流量转发至节点 1 (SRX-01),而非转发至下一跃点路由器。SRX 系列防火墙对双向流的数据包执行安全检查。
机箱间数据通路 (ICD) 的工作原理是什么?
多节点高可用性 ICD 携带数据流量并将数据流转发到对等节点。此链路不会转发机箱间链路 (ICL) 数据包。
工作流包括以下步骤:
- 当多节点高可用性节点收到数据包时,该节点上运行的安全服务会决定是将数据包转发至对等节点还是在本地处理。转发数据包的决定取决于:
- 数据包的流会话状态或服务类型
- 与数据包流关联的 SRG 状态
- 如果可通过 ICD 访问对等节点,则节点上的安全服务可以在节点之间发送和接收数据包。
- 当对等节点通过ICD接收到转发的数据包后,它就会根据配置的策略执行安全检查。
要使用 ICD 在节点之间转发数据包,您必须:
- 将 ICD 分配给环路接口,并提供到其他节点的可路由路径。
- 通过为 ICD 分配多个物理接口,确保 ICD 具有路径多样性,以实现最高的可靠性。
ICL 和 ICD 的规划接口
在多节点高可用性配置中,ICL 和 ICD 物理接口必须处于活动状态并可运行,才能适应非对称流量。ICL 和 ICD 接口促进高可用性设置中节点之间的通信,它们的状态将影响数据包处理。如果任一接口无法正常工作,将影响对非对称流量的支持。因此,确保这些接口正常运行对于获得最佳网络性能至关重要。
如果有多个物理接口连接到 ICL,而其中一个主动用于处理数据包的接口出现故障,则数据流将切换为使用与 ICL 关联的另一个可用物理接口。如果与 ICL 关联的所有物理接口均已关闭,SRX 系列防火墙将失去 ICL 连接。在这种情况下,SRX 系列节点无法交换 RTO 消息,并且不能支持非对称流量。
在多节点高可用性设置中,对 ICL 和 ICD 使用不同的环路接口。
节点通过静态或动态路由协议(例如:BGP)学习到达对等节点 ICD 的 IP 地址的路由。多节点高可用性设置利用每个 SRX 系列防火墙上的现有路由功能来路由数据包。
影响非对称流量的 ICL 和 ICD 状态
表 1 显示了节点之间的 BFD 状态如何依赖于 ICL 和 ICD 的已分配物理接口。
| ICL公司 | 《国际疾病分类》 | 非对称流量服务 | ||
| 物理接口 | BFD 状态 | 物理接口 | BFD 状态 | |
| 向上 | 向上 | 向上 | 向上 | 向上 |
| 向上 | 向上 | 下 | 下 | 下 |
| 下 | 下 | 向上 | 向上 | 下 |
| 向上 | 下 | 向上 | 下 | 下 |
| 下 | 下 | 下 | 下 | 下 |
在多节点高可用性中配置非对称流量支持
阅读本主题可了解如何为部署在多节点高可用性解决方案中的 SRX 系列防火墙配置非对称流量支持。该示例涵盖了当 SRX 系列防火墙连接到两端路由器(第 3 层部署)时在主动/备份模式下的配置。
Junos OS 23.4R1 版引入了支持非对称流量的新功能。非对称路由是指数据包在一个方向上的路径与源路径不同。
在典型的高可用性部署中,网络两端都有多个路由器和交换机。路由器使用下一跃点路径转发每个数据包流;但路由器可能不会对返回流量使用相同的路径。在多节点高可用性设置中,路由器根据当前路由路径将数据包发送到防火墙,这可能会导致流量不对称
为了处理非对称流量,多节点高可用性基础架构采用了称为机箱间数据通路 (ICD) 的新链路。ICD 能够在两个节点之间转发流量。它使节点能够将非对称流量流重定向到最初负责为这些流提供有状态服务的对等节点。
按照此配置示例设置多节点高可用性以支持非对称路由并验证设备上的配置。
| 阅读时间 |
少于 15 分钟。 |
| 配置时间 |
不到一个小时。 |
先决条件示例
表 3 列出了支持该配置的硬件和软件组件。
| 支持的硬件 |
|
| 支持的软件 |
Junos OS 23.4R1 版 |
| 许可要求 |
配置多节点高可用性不需要单独的许可证。许可证对于每个 SRX 系列都是唯一的,不能在多节点高可用性设置中的节点之间共享。因此,您必须在两个节点上使用相同的许可证。 |
在此示例中,我们使用了两个受支持的 SRX 系列防火墙和 Junos OS 23.4R1 版,以及两个瞻博网络 (R) MX960 通用路由平台作为上游和下游路由器。
准备工作
| 好处 |
多节点高可用性中的 SRX 系列防火墙可以高效处理非对称路由的数据包。此过程可确保可靠、一致地处理这些数据包的状态服务,从而提高整体性能并最大程度地减少网络中的数据包丢失和不一致。 |
| 了解更多 |
功能概述
表 4 提供了此示例中部署的配置组件的简要摘要。
| 使用的技术 |
|
| 主要验证任务 |
|
拓扑图示
图 3 显示了此示例中使用的拓扑。
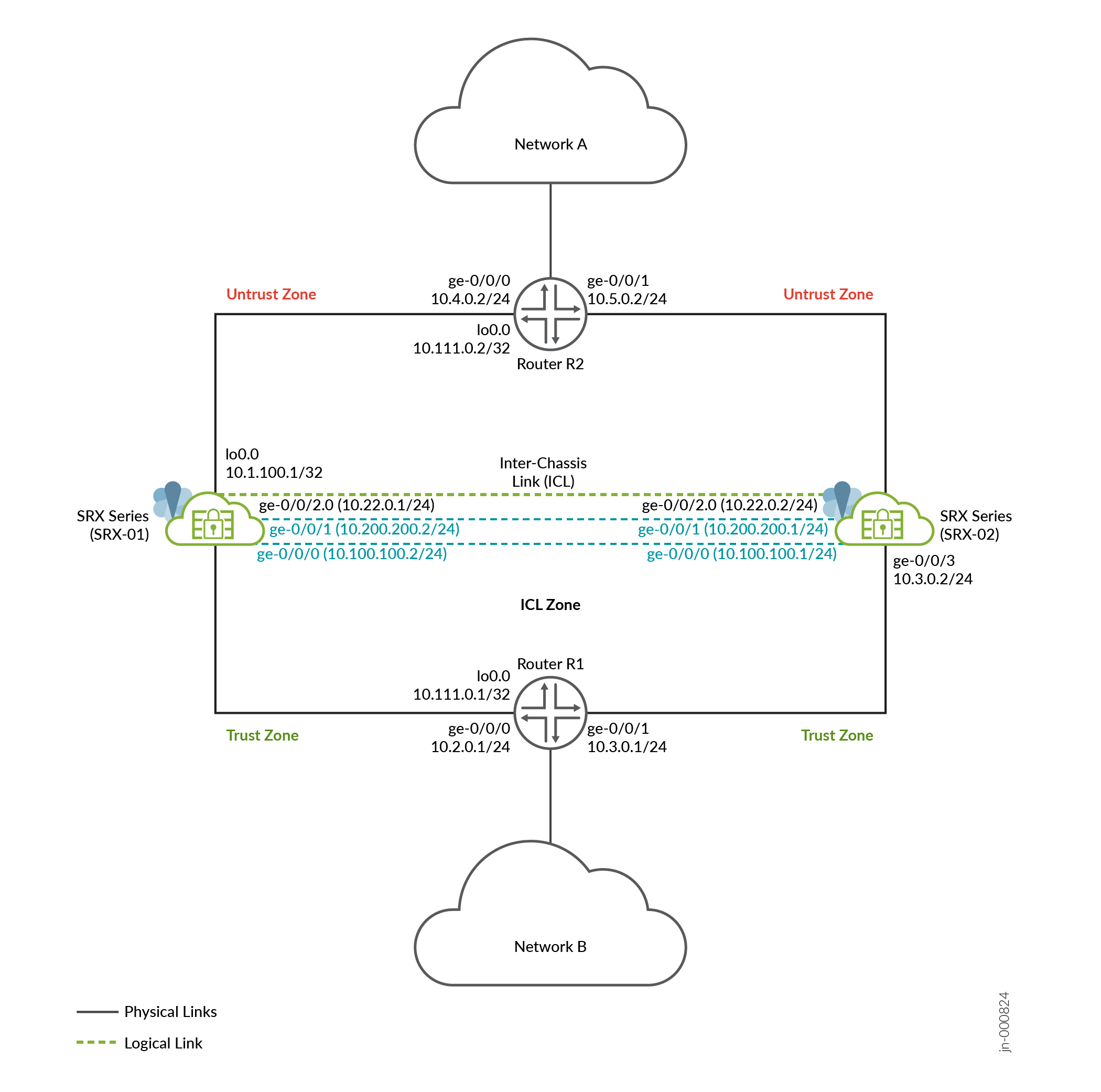 ) 的第 3 层网络中的多节点高可用性
) 的第 3 层网络中的多节点高可用性
如拓扑所示,两个 SRX 系列防火墙分别连接到信任侧和不信任侧的相邻路由器,形成 BGP 邻接方。
加密的逻辑机箱间链路 (ICL) 通过路由网络连接节点。节点使用网络上的可路由 IP 地址(浮动 IP 地址)相互通信。通常,您可以使用聚合以太网 (AE) 或 SRX 系列防火墙上的收入以太网端口来设置 ICL 连接。在此示例中,我们使用了 ICL 的 GE 端口。我们还为 ICL 路径配置了一个路由实例,以确保最大程度的分段。
两个物理链路 (ICD) 连接两个 SRX 系列防火墙。两个节点上的物理接口正在形成 MNHA ICD 连接。在此示例中,使用两个专用收入接口来配置 ICD。
环路接口用于托管 SRX 系列和路由器上的 IP 地址。
在典型的高可用性部署中,网络的北向和南向两侧有多个路由器和交换机。在此示例中,我们在 SRX 系列防火墙的两端使用了两个路由器。
拓扑概览
在此示例中,您将在 SRX 系列防火墙之间建立高可用性,并建立 ICD(机箱间数据路径),以便为处理非对称路由支持提供支持。
在典型的高可用性部署中,网络的北向和南向两侧有多个路由器和交换机。在此示例中,我们在 SRX 系列防火墙的两端使用了两个路由器。
| 设备 | 接口 | 区域 | 配置的 | IP 地址 |
|---|---|---|---|---|
| SRX-01型 | lo0 | 信任 | 10.1.100.1/32 | 用于通过 ICD 链路转发数据包的本地转发地址。 |
| ge-0/0/2 | ICL区 | 10.22.0.1/24 | 机箱间链路 (ICL) | |
| ge-0/0/1 和 ge-0/0/0 | 信任 |
|
连接两个 SRX 系列防火墙的机箱间数据链路 | |
| ge-0/0/4 | 不信任 | 10.4.0.1/24 | 连接到 R2 路由器 | |
| ge-0/0/3 | 信任 | 10.2.0.2/24 | 连接到 R1 路由器 | |
| SRX-02型 | lo0 | 信任 | 10.1.200.1/32 | 用于通过 ICD 链路转发数据包的本地转发地址。 |
| ge-0/0/2 | ICL区 | 10.22.0.2/24 | 机箱间链路 (ICL) | |
|
信任 |
|
机箱间数据链路 (ICD) | |
| ge-0/0/3 | 信任 | 10.3.0.2/24 | 连接到 R1 路由器 | |
| ge-0/0/4 | 不信任 | 10.5.0.1/24 | 连接到 R2 路由器 |
路由设备上的接口和 IP 地址配置
| 设备 | 接口 | IP 地址 | 配置为 |
|---|---|---|---|
| R2 | lo0 | 10.111.0.2/32 | R2 的环路接口地址 |
| ge-0/0/0 | 10.4.0.2/24 | 连接到 SRX-02 | |
| ge-0/0/1 | 10.5.0.2/24 | 连接到 SRX-01 | |
| ge-0/0/2 | 10.6.0.1/24 | 连接到外部网络 | |
| R1 | lo0 | 10.111.0.1/32 | R1 的环路接口地址 |
| ge-0/0/0 | 10.2.0.1/24 | 连接到 SRX-01 | |
| ge-0/0/1 | 10.3.0.1/24 | 连接到 SRX-02 | |
| ge-0/0/2 | 10.1.0.1/24 | 连接到内部网络 |
配置
SRX 系列防火墙需要 Junos IKE 软件包才能实现多节点高可用性配置。此软件包可作为默认软件包使用,也可以在 SRX 系列防火墙上作为可选软件包使用。有关详细信息,请参阅 对 Junos IKE 软件包的支持 。
如果默认情况下未在SRX 系列防火墙上安装软件包,请使用 请求系统软件添加 optional://junos-ike.tgz 进行安装。ICL 加密需要执行此步骤。
验证
在此示例中,使用以下 show 命令验证功能。
| 命令 | 验证任务 |
|---|---|
| 显示机箱高可用性信息 | 显示多节点高可用性详细信息,包括状态。 |
| 显示机箱高可用性数据平面统计信息 |
显示 ICD 数据包统计信息。 |
检查多节点高可用性详细信息
目的
查看并验证安全设备上配置的多节点高可用性设置的详细信息。
行动
在作模式下,运行以下命令:
SRX-01型
user@srx-01> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.1
Local Forwarding IP: 10.1.100.1
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Configured BFD Detection Time: 5 * 400ms
Cold Sync Status: COMPLETE
Peer Forwarding IP: 10.1.200.1 Interface: lo0.0
Peer ICD Conn State: UP
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: INELIGIBLE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: N/A
System Integrity Check: COMPLETE
Failure Events: [ IP ]
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
SRX-02型
user@srx-02> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
Local Forwarding IP: 10.1.200.1
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Configured BFD Detection Time: 5 * 400ms
Cold Sync Status: COMPLETE
Peer Forwarding IP: 10.1.100.1 Interface: lo0.0
Peer ICD Conn State: UP
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : INELIGIBLE
Health Status: UNHEALTHY
Failover Readiness: NOT READY
意义
从命令输出中验证以下详细信息:
-
本地节点和对等节点详细信息,例如 IP 地址和 ID。
-
该字段
Peer ICD Conn State: UP表示 ICD 链路已建立并运行。
验证 ICD 数据包统计信息
目的
检查 ICD 是否正常运行并促进节点之间的数据包传输。
行动
在作模式下,运行以下命令:
user@srx-01> show chassis high-availability data-plane statistics
Services Synchronized:
Service name RTOs sent RTOs received
Translation context 0 0
Incoming NAT 0 0
Resource manager 0 0
DS-LITE create 0 0
Session create 0 0
IPv6 session create 0 0
IPv4/6 session RTO ACK 0 0
Session close 0 0
IPv6 session close 0 0
Session change 0 0
IPv6 session change 0 0
ALG Support Library 0 0
Gate create 0 0
Session ageout refresh requests 0 0
IPv6 session ageout refresh requests 0 0
Session ageout refresh replies 0 0
IPv6 session ageout refresh replies 0 0
IPSec VPN 0 0
Firewall user authentication 0 0
MGCP ALG 0 0
H323 ALG 0 0
SIP ALG 0 0
SCCP ALG 0 0
PPTP ALG 0 0
JSF PPTP ALG 0 0
RPC ALG 0 0
RTSP ALG 0 0
RAS ALG 0 0
MAC address learning 0 0
GPRS GTP 0 0
GPRS SCTP 0 0
GPRS FRAMEWORK 0 0
JSF RTSP ALG 0 0
JSF SUNRPC MAP 0 0
JSF MSRPC MAP 0 0
DS-LITE delete 0 0
JSF SLB 0 0
APPID 0 0
JSF MGCP MAP 0 0
JSF H323 ALG 0 0
JSF RAS ALG 0 0
JSF SCCP MAP 0 0
JSF SIP MAP 0 0
PST_NAT_CREATE 0 0
PST_NAT_CLOSE 0 0
PST_NAT_UPDATE 0 0
JSF TCP STACK 0 0
JSF IKE ALG 0 0
Packet stats Pkts sent Pkts received
ICD Data 1035 1286
意义
该字段 ICD Data 指示 ICD 正在多节点高可用性设置中路由非对称流量。
在所有设备上设置命令
在所有设备上设置命令输出。
SRX-01(节点 1)
set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability local-id local-forwarding-ip 10.1.100.1 set chassis high-availability peer-id 2 peer-ip 10.22.0.2 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 2 peer-forwarding-ip 10.1.200.1 set chassis high-availability peer-id 2 peer-forwarding-ip interface lo0.0 set chassis high-availability peer-id 2 peer-forwarding-ip liveness-detection minimum-interval 1000 set chassis high-availability peer-id 2 peer-forwarding-ip liveness-detection multiplier 5 set chassis high-availability peer-id 2 liveness-detection minimum-interval 400 set chassis high-availability peer-id 2 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 2 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor ip 10.10.10.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/1 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url http://10.157.69.204/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3.0 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone trust interfaces ge-0/0/0.0 set security zones security-zone trust interfaces lo0.0 set security zones security-zone icl-zone host-inbound-traffic system-services ike set security zones security-zone icl-zone host-inbound-traffic system-services ping set security zones security-zone icl-zone host-inbound-traffic system-services high-availability set security zones security-zone icl-zone host-inbound-traffic system-services ssh set security zones security-zone icl-zone host-inbound-traffic protocols bfd set security zones security-zone icl-zone host-inbound-traffic protocols bgp set security zones security-zone icl-zone interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description icd-1 set interfaces ge-0/0/0 unit 0 family inet address 10.100.100.2/24 set interfaces ge-0/0/1 description icd-2 set interfaces ge-0/0/1 unit 0 family inet address 10.200.200.2/24 set interfaces ge-0/0/2 description interchassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description trust set interfaces ge-0/0/3 unit 0 family inet address 10.2.0.2/24 set interfaces ge-0/0/4 description untrust set interfaces ge-0/0/4 unit 0 family inet address 10.4.0.1/24 set interfaces lo0 description trust set interfaces lo0 unit 0 family inet address 10.1.100.1/32 set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then metric 30 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 65000 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 65000 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.4.0.2 set routing-options autonomous-system 65000 set routing-options static route 10.1.0.0/24 next-hop 10.2.0.1 set routing-options static route 10.6.0.0/24 next-hop 10.4.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.2.0.1 set routing-options static route 10.111.0.2/32 next-hop 10.4.0.2 set routing-options static route 10.1.200.1/32 next-hop 10.200.200.1 set routing-options static route 10.1.200.1/32 next-hop 10.100.100.1
SRX-02(节点 2)
set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability local-id local-forwarding-ip 200.1.1.1 set chassis high-availability peer-id 1 peer-ip 10.22.0.1 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 1 peer-forwarding-ip 100.1.1.1 set chassis high-availability peer-id 1 peer-forwarding-ip interface lo0.0 set chassis high-availability peer-id 1 peer-forwarding-ip liveness-detection minimum-interval 1000 set chassis high-availability peer-id 1 peer-forwarding-ip liveness-detection multiplier 5 set chassis high-availability peer-id 1 liveness-detection minimum-interval 400 set chassis high-availability peer-id 1 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 1 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 activeness-priority 1 set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url http://10.157.69.204/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3.0 set security zones security-zone trust interfaces lo0.0 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone trust interfaces ge-0/0/0.0 set security zones security-zone icl-zone host-inbound-traffic system-services ike set security zones security-zone icl-zone host-inbound-traffic system-services ping set security zones security-zone icl-zone host-inbound-traffic system-services high-availability set security zones security-zone icl-zone host-inbound-traffic system-services ssh set security zones security-zone icl-zone host-inbound-traffic protocols bfd set security zones security-zone icl-zone host-inbound-traffic protocols bgp set security zones security-zone icl-zone interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description icd-1 set interfaces ge-0/0/0 unit 0 family inet address 10.100.100.1/24 set interfaces ge-0/0/1 description icd-2 set interfaces ge-0/0/1 unit 0 family inet address 10.200.200.1/24 set interfaces ge-0/0/2 description interchassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description trust set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 set interfaces ge-0/0/4 description untrust set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24 set interfaces lo0 description trust set interfaces lo0 unit 0 family inet address 10.1.200.1/32 set policy-options route-filter-list ipsec 10.6.0.0/16 orlonger set policy-options route-filter-list loopback 10.11.0.0/24 orlonger set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then metric 35 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 65000 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 65000 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.5.0.2 set routing-options autonomous-system 65000 set routing-options static route 10.1.0.0/24 next-hop 10.3.0.1 set routing-options static route 10.6.0.0/24 next-hop 10.5.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.3.0.1 set routing-options static route 10.111.0.2/32 next-hop 10.5.0.2 set routing-options static route 10.1.100.1/32 next-hop 10.200.200.2 set routing-options static route 10.1.100.1/32 next-hop 10.100.100.2
路由器 -1
set interfaces ge-0/0/0 description ha set interfaces ge-0/0/0 unit 0 family inet address 10.2.0.1/24 set interfaces ge-0/0/1 description ha set interfaces ge-0/0/1 unit 0 family inet address 10.3.0.1/24 set interfaces ge-0/0/2 description lan set interfaces ge-0/0/2 unit 0 family inet address 10.1.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.1/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.1/32 preferred set routing-options autonomous-system 65000 set protocols bgp group mnha_r0 type internal set protocols bgp group mnha_r0 local-address 10.2.0.1 set protocols bgp group mnha_r0 local-as 65000 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0 neighbor 10.2.0.2 set protocols bgp group mnha_r0_b type internal set protocols bgp group mnha_r0_b local-address 10.3.0.1 set protocols bgp group mnha_r0_b local-as 65000 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0_b neighbor 10.3.0.2
路由器-2
set interfaces ge-0/0/0 description HA set interfaces ge-0/0/0 unit 0 family inet address 10.4.0.2/24 set interfaces ge-0/0/1 description HA set interfaces ge-0/0/1 unit 0 family inet address 10.5.0.2/24 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.6.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 65000 set protocols bgp group mnha_r0 type internal set protocols bgp group mnha_r0 local-address 10.4.0.2 set protocols bgp group mnha_r0 local-as 65000 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0 neighbor 10.4.0.1 set protocols bgp group mnha_r0_b type internal set protocols bgp group mnha_r0_b local-address 10.5.0.2 set protocols bgp group mnha_r0_b local-as 65000 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0_b neighbor 10.5.0.1
显示配置输出
在配置模式下,输入 show high availability、、 show security zones和 show interfaces,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
SRX-01(节点 1)
user@srx-01# show chassis high-availability
local-id {
1;
local-ip 10.22.0.1;
local-forwarding-ip 100.1.1.1;
}
peer-id 2 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
peer-forwarding-ip {
200.1.1.1;
interface lo0.0;
liveness-detection {
minimum-interval 1000;
multiplier 5;
}
}
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
2;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
ip 10.10.10.1;
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
interface {
ge-0/0/1;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
preemption;
activeness-priority 200;
}
user@srx-01# show interfaces
ge-0/0/0 {
description icd-1;
unit 0 {
family inet {
address 10.100.100.2/24;
}
}
}
ge-0/0/1 {
description icd-2;
unit 0 {
family inet {
address 10.200.200.2/24;
}
}
}
ge-0/0/2 {
description interchassis_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.2.0.2/24;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.4.0.1/24;
}
}
}
lo0 {
description trust;
unit 0 {
family inet {
address 10.1.100.1/32;
}
}
}
user@srx-01# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
ge-0/0/1.0;
ge-0/0/0.0;
lo0.0;
}
}
security-zone icl-zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
user@srx-01# show policy-options
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 30;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
user@srx-01# show routing-options
autonomous-system 65000;
static {
route 10.1.0.0/24 next-hop 10.2.0.1;
route 10.6.0.0/24 next-hop 10.4.0.2;
route 10.111.0.1/32 next-hop 10.2.0.1;
route 10.111.0.2/32 next-hop 10.4.0.2;
route 10.1.200.1/32 next-hop [ 10.200.200.1 10.100.100.1 ];
}
SRX-02(节点 2)
user@srx-02# show chassis high-availability
local-id {
2;
local-ip 10.22.0.2;
local-forwarding-ip 200.1.1.1;
}
peer-id 1 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
peer-forwarding-ip {
100.1.1.1;
interface lo0.0;
liveness-detection {
minimum-interval 1000;
multiplier 5;
}
}
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
1;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
activeness-priority 1;
}
user@srx-02# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
lo0.0;
ge-0/0/1.0;
ge-0/0/0.0;
}
}
security-zone icl-zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
user@srx-02# show interfaces
ge-0/0/0 {
description icd-1;
unit 0 {
family inet {
address 10.100.100.1/24;
}
}
}
ge-0/0/1 {
description icd-2;
unit 0 {
family inet {
address 10.200.200.1/24;
}
}
}
ge-0/0/2 {
description interchassis_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.3.0.2/24;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.5.0.1/24;
}
}
}
lo0 {
description trust;
unit 0 {
family inet {
address 10.1.200.1/32;
}
}
}
user@srx-02# show policy-options
route-filter-list ipsec {
10.6.0.0/16 orlonger;
}
route-filter-list loopback {
10.11.0.0/24 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 35;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
user@srx-02# show routing-options
autonomous-system 65000;
static {
route 10.1.0.0/24 next-hop 10.3.0.1;
route 10.6.0.0/24 next-hop 10.5.0.2;
route 10.111.0.1/32 next-hop 10.3.0.1;
route 10.111.0.2/32 next-hop 10.5.0.2;
route 10.1.100.1/32 next-hop [ 10.200.200.2 10.100.100.2 ];
}
