Ethernet Interfaces
Learn about Ethernet technology used to broadcast traffic on security devices, static ARP entries, creating and deleting the Ethernet interface, and enabling and disabling the promiscuous mode on these interfaces. Also learn about Aggregated Ethernet Interfaces
Ethernet Interfaces Overview
Ethernet is a Layer 2, point-to multipoint technology that operates in a shared bus topology, supports broadcast transmission, and has distributed access control.
In a shared bus topology, all devices connect to a single, shared physical link through which all data transmissions are sent. The devices within a single Ethernet topology make up a broadcast domain.
The physical hardware does not provide information to the sender about incoming and lost traffic. Higher layer protocols such as TCP/IP can provide this type of notification.
| Types | Description |
|---|---|
|
Ethernet Access Control and Transmission |
|
|
Collisions and Detection |
|
|
Collision Domains and LAN Segments |
|
|
|
Round |
Size of Set |
Elements in the Set |
|---|---|---|
|
1 |
2 |
|
|
2 |
4 |
|
|
3 |
8 |
|
|
4 |
16 |
|
|
5 |
32 |
|
|
6 |
64 |
|
|
7 |
128 |
|
|
8 |
256 |
|
|
9 |
512 |
|
|
10 |
1024 |
|
Ethernet Frames
Data is transmitted through an Ethernet network in frames. The frames are of variable length, ranging from 64 octets to 1518 octets, including the header, payload, and cyclic redundancy check (CRC) value.Figure 1 shows the Ethernet frame format.
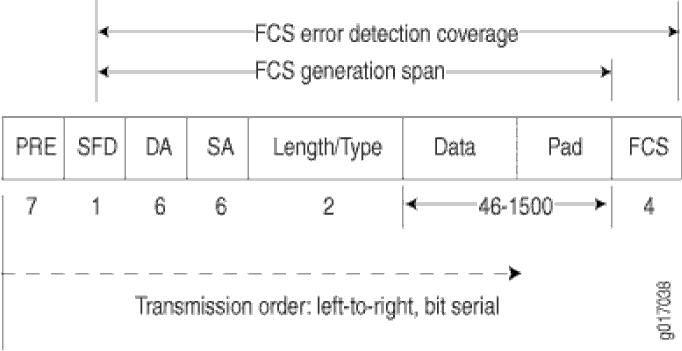
Ethernet frames have the following fields:
-
The preamble (PRE) field is 7 octets of alternating 0s and 1s. The predictable format in the preamble allows receiving interfaces to synchronize themselves to the data being sent. The preamble is followed by a 1-octet start-of-frame delimiter (SFD).
-
The destination address (DA) and source address (SA) fields contain the 6-octet (48-bit) MAC addresses for the destination and source ports on the network. These Layer 2 addresses uniquely identify the devices on the LAN.
-
The Length/Type field is a 2-octet field that either indicates the length of the frame's data field or identifies the protocol stack associated with the frame. Here are some common frame types:
-
AppleTalk—
0x809B -
AppleTalk ARP—
0x80F3 -
DECnet—
0x6003 -
IP—
0x0800 -
IPX—
0x8137 -
Loopback—
0x9000 -
XNS—
0x0600
-
-
The Data field contains the packet payload.
-
The frame check sequence (FCS) is a 4-octet field that contains the calculated CRC value. This value is calculated by the originating host and appended to the frame. When it receives the frames, the receiving host calculates the CRC and checks it against this appended value to verify the integrity of the received frame.
-
On SRX650 devices, MAC pause frame and FCS error frame counters are not supported for the interfaces ge-0/0/0 through ge-0/0/3. (Platform support depends on the Junos OS Release in your installation.)
Promiscuous Mode
-
When you enable promiscuous mode on a Layer 3 Ethernet interface, all received packets on are sent to the central point or Services Processing Unit (SPU) regardless of the destination MAC address of the packet.
-
You can also enable promiscuous mode on chassis cluster redundant Ethernet interfaces and aggregated Ethernet interfaces.
-
If you enable promiscuous mode on a redundant Ethernet interface, it is enabled on any child physical interfaces. If you enable promiscuous mode on an aggregated Ethernet interface, it is enabled on all member interfaces.
-
Promiscuous mode function is supported on 1-Gigabit, 10-Gigabit, 40-Gigabit, and 100-Gigabit Ethernet interfaces on the I/O cards (IOCs) and the SRX5000 line Module Port Concentrator (SRX5K-MPC).
-
By default, an interface enables MAC filtering. You can configure promiscuous mode on the interface to disable MAC filtering. When you delete the configuration, the interface will perform MAC filtering again.
-
You can change the interface MAC address when the interface is operating in promiscuous mode. When the interface is operating in normal mode, the MAC filtering function on the IOC uses the new MAC address to filter the packets.
Example: Configure Ethernet Interface
Overview
Table describes the steps to create and (optional) delete Ethernet interfaces on your routing device.
|
Configuration Step |
Command |
|---|---|
|
Step 1: Create the Ethernet interface and set the logical interface. |
[edit] user@host# edit interfaces ge-1/0/0 unit 0 |
|
Step 2: If you are done configuring the device, commit the configuration. |
[edit] user@host# commit |
|
Step 3: (Optional) Specify the interface you want to delete. |
[edit] user@host# delete interfaces ge-1/0/0 |
|
Step 4: If you are done configuring the device, commit the configuration. |
[edit] user@host# commit |
Example: Configuring Promiscuous Mode on the SRX5K-MPC
This example shows how to configure promiscuous mode on an SRX5K-MPC interface in an SRX5600 to disable MAC address filtering.
CLI Quick Configuration
Below table specifies the CLI quick configuration commands used for configuring and disabling promiscuous mode on SRX5K-MPC interface .
|
Configuration Step |
CLI Quick Configuration Commands |
|---|---|
| Configure promiscuous mode on the interface |
set interfaces et-4/0/0 unit 0 family inet address 10.1.1.1/24 set interfaces et-4/0/0 promiscuous-mode |
| Disable promiscuous mode on an interface |
user@host# delete interfaces et-4/0/0 promiscuous-mode |
Configure Promiscuous Mode on an Interface
Below table describes the step-by-step to configure promiscuous mode on an interface on your security device.
|
Configuration Step |
Command |
|---|---|
|
Step 1: Configure the ingress interface. |
[edit interfaces] user@host# set et-4/0/0 unit 0 family inet address 10.1.1.1/24 |
|
Step 2: Enable promiscuous mode on the interface. |
[edit interfaces] user@host# set et-4/0/0 promiscuous-mode |
|
Step 3: (Optional) Disable promiscuous mode on the interface. |
[edit] user@host# delete interfaces et-4/0/0 promiscuous-mode |
Use the show interfaces command to see the output of the configuration.
Verification
Purpose
Verify that promiscuous mode is enabled, its status, on the interface and disabled on the interface.
Action
-
To display information about the parameters configured on promiscuous mode Interface.
user@host> show interfaces
Physical interface: et-4/0/0, Enabled, Physical link is Up Interface index: 137, SNMP ifIndex: 511 Link-level type: Ethernet, MTU: 1518, Speed: 100Gbps, Loopback: Disabled, Source filtering: Disabled, Flow control: Enabled Device flags : Present Running Interface flags: Promiscuous SNMP-Traps Internal: 0x4000 CoS queues : 8 supported, 8 maximum usable queues Current address: 2c:21:72:3a:05:28, Hardware address: 2c:21:72:3a:05:28 Last flapped : 2014-01-17 14:44:53 PST (5d 06:30 ago) Input rate : 0 bps (0 pps) Output rate : 0 bps (0 pps) Active alarms : None Active defects : None PCS statistics Seconds Bit errors 0 Errored blocks 0 Logical interface et-4/0/0.0 (Index 71) (SNMP ifIndex 513) Flags: SNMP-Traps 0x4000 VLAN-Tag [ 0x8100.1351 ] Encapsulation: ENET2 Input packets : 0 Output packets: 0 Security: Zone: HOST Allowed host-inbound traffic : any-service bfd bgp dvmrp igmp ldp msdp nhrp ospf pgm pim rip router-discovery rsvp sap vrrp Protocol inet, MTU: 1500 Flags: Sendbcast-pkt-to-re Addresses, Flags: Is-Preferred Is-Primary Destination: 122.122.122/24, Local: 122.122.122.1, Broadcast: 122.122.122.255 Protocol multiservice, MTU: Unlimited Flags: Is-Primary Logical interface et-4/0/0.32767 (Index 72) (SNMP ifIndex 517) Flags: SNMP-Traps 0x4004000 VLAN-Tag [ 0x0000.0 ] Encapsulation: ENET2 Input packets : 0 Output packets: 0 Security: Zone: HOST Allowed host-inbound traffic : any-service bfd bgp dvmrp igmp ldp msdp nhrp ospf pgm pim rip router-discovery rsvp sap vrrp Protocol multiservice, MTU: Unlimited Flags: NoneThe
Interface flags: Promiscuousfield shows that promiscuous mode is enabled on the interface. -
Verify that promiscuous mode works on the
et-4/0/0interface. Send traffic into theet-4/0/0interface with a MAC address that is different from the interface MAC address and turn on promiscuous mode. From operational mode, enter themonitor interface trafficcommand.user@host> monitor interface traffic
Interface Link Input packets (pps) Output packets (pps) gr-0/0/0 Up 0 (0) 0 (0) ip-0/0/0 Up 0 (0) 0 (0) lt-0/0/0 Up 0 (0) 0 (0) xe-1/2/0 Down 0 (0) 0 (0) xe-1/2/1 Down 0 (0) 0 (0) xe-1/2/2 Down 0 (0) 0 (0) xe-1/2/3 Down 0 (0) 0 (0) xe-1/2/4 Down 0 (0) 0 (0) xe-1/2/5 Down 0 (0) 0 (0) xe-1/2/6 Down 0 (0) 0 (0) xe-1/2/7 Down 0 (0) 0 (0) xe-1/2/8 Down 0 (0) 0 (0) xe-1/2/9 Down 0 (0) 0 (0) et-4/0/0 Up 4403996 (100002) 0 (0) et-4/2/0 Up 3 (0) 4403924 (99997) avs0 Up 0 (0) 0 (0) avs1 Up 0 (0) 0 (0) dsc Up 0 0 em0 Up 15965 14056
The
input packetsandppsfields show that traffic is passing through theet-4/0/0interface as expected after promiscuous mode is enabled. -
Verify that disabled promiscuous mode works on the
et-4/0/0interface. Send traffic and turn off the promiscuous mode.user@host> monitor interface traffic
Interface Link Input packets (pps) Output packets (pps) gr-0/0/0 Up 0 (0) 0 (0) ip-0/0/0 Up 0 (0) 0 (0) lt-0/0/0 Up 0 (0) 0 (0) xe-1/2/0 Down 0 (0) 0 (0) xe-1/2/1 Down 0 (0) 0 (0) xe-1/2/2 Down 0 (0) 0 (0) xe-1/2/3 Down 0 (0) 0 (0) xe-1/2/4 Down 0 (0) 0 (0) xe-1/2/5 Down 0 (0) 0 (0) xe-1/2/6 Down 0 (0) 0 (0) xe-1/2/7 Down 0 (0) 0 (0) xe-1/2/8 Down 0 (0) 0 (0) xe-1/2/9 Down 0 (0) 0 (0) et-4/0/0 Up 11505495 (0) 0 (0) et-4/2/0 Up 6 (0) 11505425 (0) avs0 Up 0 (0) 0 (0) avs1 Up 0 (0) 0 (0) dsc Up 0 0 em0 Up 37964 31739
The
ppsfield shows that the traffic is not passing through theet-4/0/0interface after promiscuous mode is disabled.
