Juniper and the Policy of the Future

Policy complexity bringing you down? Here’s what we’re doing to help.
Today, customers like you are facing increased policy complexity and device security concerns, which have emerged from the vast proliferation of atypical devices connected to enterprise networks. Push play to hear Juniper’s Sanjoy Dey discuss how we are taking on these complexities with a strategy and vision for policy, onboarding, and self-provisioning.
You’ll learn
How Juniper is providing effective IoT Assurance
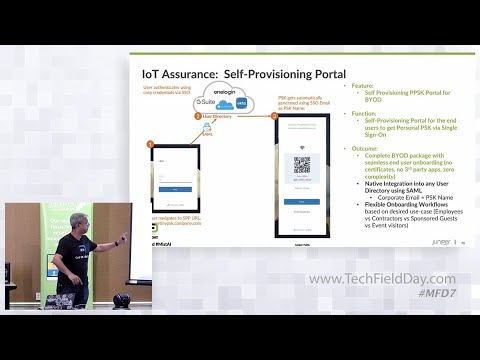
The scoop on the new Self Provisioning Portal for BYOD, including its purpose, intended outcomes, and how it works
How Juniper is bringing insight and scale to next-gen NAC with Mist AI™
Who is this for?
Host

Transcript
0:09 very quickly
0:10 if you look at any enterprise right
0:12 there are primarily
0:14 four types of devices
0:16 there is uh your guest device there is
0:19 iot devices
0:21 you have byod users and then your
0:23 corporate users so if you look at like
0:26 you know what we have done as part of
0:28 the miss journey over the last three to
0:31 four years
0:32 we have built like you know probably the
0:35 most comprehensive guest solution and
0:38 yes i put in the word captive portal in
0:40 there we started with a captive portal
0:42 uh captive portals are kind of the
0:44 abomination for guest wi-fi with all the
0:46 issues around
0:48 the cna the pop-ups not working etc but
0:51 we still supported it and then
0:53 over the last couple of years we have
0:55 built in every single workflow whether
0:58 it's around sponsored guests whether
1:00 it's around oauth mechanisms with social
1:02 credentials
1:04 even hotspot 2.0 right like you know we
1:06 are starting to see especially in the
1:08 retail market customers starting to
1:11 pilot uh hotspot 2.0 and like you know
1:14 we have a good support so we have built
1:16 out a comprehensive
1:18 guest solution right so what's next for
1:21 us
1:22 let's actually conquer iot byod and and
1:26 the corporate devices are laptops and
1:28 macbook pros right and for any of these
1:31 different types of devices like you know
1:33 what we want to get to is seamless
1:36 onboarding
1:37 um unified policy
1:40 most importantly user experience and
1:42 having good visibility around who are
1:45 the people actors on my network and who
1:48 may not be sanctioned to be there
1:50 and overall stitch it together with a
1:52 simplified operation story right
1:55 so
1:57 last november we announced this service
2:00 for iot assurance and there are only a
2:03 few key things to
2:05 note about it
2:06 this was basically a service that came
2:08 out of customers asking for a simple
2:11 solution for headless iot devices
2:14 that do not support 802.1x
2:17 authentication right epls they they are
2:19 headless
2:22 so they have to use multi-pre shared
2:23 keys or private pre-shared keys and what
2:26 customers were struggling with was like
2:28 in a complex workflows in today's like
2:32 you know radius snack solutions to get
2:34 them onboarded assign the right policy
2:36 do the right kind of traffic engineering
2:39 and then most importantly right when you
2:42 think about a distributed enterprise and
2:44 you are actually thinking about uh like
2:47 you know potentially hundreds of
2:48 thousands of these different sensors in
2:51 the in the context of retail networks it
2:53 could be your food safety uh could be
2:56 your thermal humidity sensors in the
2:58 context of the enterprise campus it
3:00 could be your hvac
3:02 and lighting so all of these
3:04 different thousands of devices need to
3:06 be onboarded
3:08 and you need to do it at scale and
3:10 whatever we do at mist obviously one of
3:13 the foundational thing is ai but the
3:16 other thing whatever we build we we do
3:18 build for scale right so in a short
3:20 video we are basically just going to
3:22 explore uh
3:24 iot assurance in action and like you
3:27 know what what this video is going to
3:29 demonstrate
3:30 is our capability to go and
3:33 with a private pre-shared key where we
3:35 use the key as an identity right the mac
3:38 address is not the identity anymore why
3:40 because over the last three years we
3:42 have seen
3:43 google's and apple's of the world what
3:45 they have done with android ios and and
3:48 random macs right so with the key
3:50 becomes the identity how can i onboard
3:51 the device how can i assign the right
3:54 policy set them up for like you know the
3:56 right whether it's tunneling or whether
3:58 it's locally bridging uh the traffic and
4:01 most importantly how do you provide
4:03 visibility right
4:06 so
4:07 in in this particular example like you
4:09 know org wide like you know we have like
4:12 thousands of keys that you can create
4:14 literally there is no limit to the
4:16 number of keys now keep in mind that all
4:19 of this
4:20 can potentially be done natively through
4:21 whatever we provide right what we have
4:24 done here is given your portal to look
4:26 at administer and life cycle manage all
4:29 of these different keys
4:31 in a simple easy to use manner with the
4:34 right set of visibility so here i'm
4:36 actually like you know honing on you can
4:39 have like you know the email address or
4:41 the identity of a user as your key name
4:44 right and with that you can actually go
4:47 and
4:48 like you know assign a right segment of
4:50 the network so this will belong to like
4:53 you know vlan such and such and and that
4:55 iot device will be on a different vlan
4:57 all without the use of any kind of an
4:59 overlay neck radius system right so over
5:03 here you see like you know vlan 750 has
5:06 been assigned to the particular key the
5:09 key again to stress
5:10 is actually the identity because that is
5:13 what prove like you know insulates it
5:16 against your
5:17 uh uh mac randomization and then
5:20 with the role or with the right like you
5:23 know segmentation you can decide that
5:25 this these set of iot devices need to
5:28 tunnel traffic to an application server
5:30 like you know that is like you know in a
5:32 data center somewhere whereas the rest
5:35 of the devices iot devices or users
5:38 sharing the same ssid could potentially
5:41 just locally bridge their traffic right
5:44 the next important thing is visibility
5:46 right who are the users that are
5:48 actually currently using that particular
5:51 key right there have been instances
5:54 uh
5:55 where
5:57 people have actually done pilots right
5:59 and as part of pilots say i have this
6:00 ssid i have this preset key let me
6:02 actually go and administer these keys on
6:05 on these few devices
6:07 then i'm done with my pilot and then
6:09 i've left those devices forgotten that
6:11 provides a security intrusion threat
6:14 right in your in your building so it's
6:16 very important to have visibility into
6:19 who all are using that pre-shared key
6:22 but most importantly also have
6:24 visibility on
6:26 clients that have been registered to use
6:29 but currently not
6:30 using that particular key and that will
6:32 give you some insights
6:36 the next thing that is like you know uh
6:38 important is around administration of
6:40 keys so in our in as part of this
6:42 service we give you the the portal from
6:45 where you can actually look at
6:47 administering or life cycle managing the
6:49 keys uh and probably it has not happened
6:52 to uh
6:53 to any of you but in many cases what
6:56 happens is that we go and
6:58 rotate keys so there's like you know the
7:00 left hand not talking to the right hand
7:02 uh someone rotates the keys
7:05 and then the result is devices get
7:07 disconnected and like you know we are
7:09 going to be able to catch that through
7:10 marvis our connection sls but that is
7:13 actually a real problem and expose facto
7:16 so what if i could actually give you a
7:18 very easy to administer process
7:20 whereby
7:21 like you know you go and
7:23 rotate your keys out
7:25 without having to touch the end user or
7:28 the connectivity of the of the end user
7:30 so here i'm going to filter for all of
7:33 my like i filtered on iot devices and
7:36 i'm just going to duplicate that key
7:38 right so i'm going to duplicate that key
7:40 such that all the connected users are
7:42 still connected and all of my uh
7:45 like and then i can on the original key
7:48 i can go do my key rotation right if i
7:50 have to change attributes on the on the
7:53 expedition or the number of devices that
7:55 can connect like you know all of that is
7:58 done through this process if you had a
8:00 question
8:01 do you need anything on the client
8:03 device that can accept that change key
8:06 uh
8:08 today we do like you know for for any
8:10 client device management you need an mdm
8:13 solution so we are not claiming here to
8:16 be your mdm solution but what we are
8:19 claiming to be is all of your identity
8:21 vectors we are going to just manage
8:23 those right
8:28 the point keith is is that it is still
8:30 the enterprise's responsibility to push
8:33 the new keys to these devices
8:35 we're giving an option for old keys to
8:38 work and new keys to work simultaneously
8:42 and showing you visibility of who's
8:44 hanging on to dear life with the old
8:45 keys
8:47 right perfect thanks thanks keith so
8:49 sorry just because are these new
8:51 different keys or the same key with
8:53 different properties it is actually the
8:56 exact same key so what i did as part of
8:58 this process was i duplicated the
8:59 original key the client devices are
9:01 connected to the duplicate key while i
9:03 go and like you know rotate my
9:06 administer the the original key and then
9:08 at the right time
9:10 that
9:11 particular key can potentially be the
9:12 past phase or whatever needs to change
9:14 can be administered on the client
9:16 devices right
9:19 from the client's perspective is still
9:21 using the same key and then on the
9:23 infrastructure has different properties
9:24 that is correct so the client doesn't
9:26 care what's that is correct yes the
9:28 client doesn't care so this is
9:29 completely transparent to the client
9:31 okay
9:32 so connected to the same society that
9:34 support the ppsk yes can so you can have
9:37 clients that
9:39 are have different policies and their
9:41 traffic get tunneled somewhere and then
9:43 you can have other clients that get
9:45 locally switched that is correct on the
9:47 single ssid we can achieve micro
9:49 segmentation through roles uh and you
9:52 will be able to uh like you know tunnel
9:55 one set of devices so my sony iot
9:57 devices need to go to talk to the sony
10:00 application server i cannot let that
10:02 touch my corporate network that can get
10:04 tunneled and and by the way our
10:06 tunneling solution is missed edge a
10:09 shameless plug over there bob talked
10:11 about it like you know it's a wonderful
10:13 solution so they are all going to get
10:15 tunneled to a mistake and the traffic
10:17 will be dropped at a pop
10:19 while the others will be locally bridged
10:21 can you configure that at the uh wx lan
10:24 policy level well you can actually do
10:27 that just by your network segment so
10:29 like you know you you can use vlan 750
10:32 on that ssid
10:34 for tunnel traffic you can use vlan 710
10:38 for all your locally bridged traffic
10:40 okay right and then the ppsk works with
10:42 wpa3 isu
10:44 um ppsk wpa3 is currently a work in
10:49 progress
10:50 uh and and potentially just stay tuned
10:52 like you know we will have an update for
10:53 you soon okay
10:55 having a hard time tying this with vxlan
11:00 and the policy so how do you tie
11:03 a great question so as i was kind of
11:05 alluding to with with april april um the
11:09 cloud is a place where we stitch things
11:12 together right so you might actually
11:14 have a policy framework for
11:17 vxlan using gbp
11:20 i on the wireless side like you know we
11:22 have wxlam
11:24 on the cloud side the needful stitching
11:26 goes through and the right policies get
11:28 pushed out to access points and switches
11:31 right whether it's like an acl or or
11:34 like you know whatever it may be or a wx
11:37 lan policy so i'm just going to move
11:39 forward to the next use case
11:42 and
11:43 that is around extension and this is
11:45 basically your work in progress
11:48 to be released hopefully by end of this
11:50 month
11:52 like you know if you if you are familiar
11:54 with like you know byod
11:56 like you know workflows they can get
11:58 awfully complex and many times people
12:01 need simple mechanisms for students in a
12:04 in a higher ed uh like in a campus or
12:07 corporate devices corporate users
12:10 bringing their own devices and
12:13 self-administering like you know how to
12:15 get their devices on the network so as
12:18 we are we were developing this uh the
12:20 the private pre-shared key or
12:22 multi-pre-shared key based iot assurance
12:25 solution
12:26 we are extending that and to be released
12:28 this month hopefully like you know with
12:30 uh what we call the self-provisioning
12:33 portal extension to iot assurance and
12:36 what that allows you to do is use the
12:40 say for example your your directory will
12:42 have the identity of the user the
12:44 credential
12:45 and you are going to
12:47 it is completely self-administered a
12:49 user goes and enters his his or her
12:52 credentials
12:53 we are going to do a roll look up roll
12:55 look up like you know whether it's octa
12:57 or azure or adfs
13:00 and then we are going to get
13:03 a qr code returned back to the user the
13:05 user can just scan the qr code and
13:08 basically get on the network right so we
13:11 stitch together a demo uh that basically
13:14 shows the process through
13:16 this role integration with octa
13:21 so like you know over here uh so this is
13:23 basically the the client onboarding
13:26 piece
13:26 and if i just fast forward a little bit
13:30 so you as as part of your administration
13:34 like you know you are going to
13:36 provide a url for all of the users to go
13:39 and register themselves right so that is
13:42 basically so we provide you with a psk
13:44 portal configuration this is this is
13:46 basically where you provide your idp uh
13:50 information
13:51 and then
13:52 from
13:53 like you know
13:55 you also will modify the different
13:58 attributes of that particular psk
14:01 so things like like you know if you have
14:03 to assign a vlan or you have to assign
14:06 like an expiration and all that
14:08 configuration is out there so from a
14:11 user experience perspective what it
14:13 looks like is in this particular case
14:15 i'm going to like in a url that has been
14:18 advertised this is basically your
14:20 octa is used as a role directory
14:23 provider i'm going to go and like you
14:25 know enter my
14:27 email address over there the email
14:28 address is basically the identity of the
14:31 user on the directory uh i am
14:35 signing in and
14:37 we have once the authentication actually
14:39 goes through there's a callback to our
14:41 portal and we are going to give you a qr
14:44 code you can scan the qr code and get on
14:46 the network and the rest of the demo
14:49 covers that in the interest of time i'm
14:51 just going to skip this particular demo
14:54 and move on
14:55 to the last bastion that we are yet to
14:58 conquer
15:01 right so
15:03 if you have we have so we have talked
15:04 about guests we have talked about iot we
15:06 have talked about byod so really the
15:08 last thing to tackle is uh what do we do
15:12 with
15:13 like you know for corporate users right
15:14 and for the longest time we actually
15:17 have very good integration
15:18 with cisco ice aruba clear pass for
15:21 scout
15:22 like you know pretty much or microsoft
15:24 nps free radius anything that you can
15:26 think of like you know we have very well
15:28 documented tight integration of how we
15:31 ingest filter id attributes from clear
15:33 pass into our wx lan policy etc right
15:37 but as and when we were building this
15:39 solution up like you know we started to
15:41 look at like you know what is really
15:42 wrong with
15:44 today's overlay systems for
15:46 and radius and really there are three
15:49 things that that kind of jump up number
15:51 one is deployment and provisioning like
15:53 you know is basically a pain even if
15:56 they offer like in a software containers
15:58 it's rack and stack virtualization not
16:01 quite micro services driven but more
16:03 importantly when it when like you know
16:05 the examples that you have seen today
16:09 there is no single system that is
16:11 actually correlating data from the edge
16:13 the client data from the edge or the
16:15 client experience from the edge to what
16:17 is going on in the rest of the network
16:19 so today what we do is we highlight that
16:21 if a user has had an authentication
16:23 problem we will say that go check
16:26 the radius side of the house right
16:28 especially if wi-fi or wired is not to
16:30 blame
16:31 but someone still needs to know what is
16:33 going on the radio system and you have
16:35 to go through log mining and parsing to
16:37 figure out like you know what is wrong
16:39 and what is broken and and that is
16:42 basically a pain for the user and then
16:44 last but not least like you know goes to
16:47 uh
16:48 all the solutions being non-cloud native
16:50 non-cloud driven
16:52 they lack the agility and scale like you
16:54 know so uh in the world of mist we've
16:57 actually solved all this problem in the
17:00 in the enterprise edge right so our
17:03 aspiration is to really
17:06 provide the or bring the same micro
17:08 services architecture and the ai driven
17:11 insights that we have done for network
17:13 devices
17:14 and then bring it into the
17:16 mac radius market right
17:18 so this is not a product announcement
17:21 this is not a launch of any kind but i'm
17:24 just going to give you a teaser of what
17:26 that actually looks like
17:28 uh in in our world
17:31 and
17:32 role like you know if you've seen wxlan
17:34 like and it will seem very familiar one
17:36 of the important aspects is the policy
17:38 configuration right and and what we show
17:41 in this demo is a simplified like in a
17:44 policy framework instead of having to go
17:46 through three or four different tabs
17:49 to have simple policies for your wired
17:51 and wireless devices in like you know
17:53 this is set up like a wxlan engine uh
17:57 where you have like you know your
17:59 wireless devices that are using uh epls
18:02 uh authentication on the left hand side
18:04 are all the different like you know
18:07 identities the different users
18:10 and the attributes that will provide
18:12 rules to match on so you're going
18:14 through this list like a regular
18:15 firewall trying to find the best match
18:18 and assign the right set of policies and
18:20 and rules right so here we're showing it
18:23 so it's a wireless user using epls
18:26 corporate like an end you can filter on
18:29 like subject of a of a certificate if
18:31 the subject of the certificate is this
18:33 like you know i am now going to put that
18:35 user in that
18:37 like in a corporate vlan and potentially
18:40 assign uh an
18:42 advanced role right uh similarly like
18:45 you know um i'm not going to go through
18:47 the whole thing uh but if you look at
18:49 like you know we do this exact same
18:51 thing for wired devices like you know so
18:53 if you have a uh like a dot one x device
18:56 or if you're doing like in a map and
18:59 it's a
19:00 it's a it's a printer you will assign it
19:02 the the printer vlan right so so this is
19:05 basically one aspect of what we are
19:07 bringing to the table on the surface of
19:09 it is like in a simplified policy
19:12 framework that can be now pushed to the
19:14 switches and um and and the access
19:16 points and by the way our
19:19 the goal number one is to do this on
19:22 juniper miss devices and eventually we
19:24 are going to expand over to third party
19:27 uh infrastructure
19:28 um
19:30 i am
19:31 going to go to the money slide here like
19:33 you know basically this is the bread and
19:35 butter
19:36 of
19:37 where the problems today lie right and
19:39 it is like you know this
19:41 troubleshooting like you know what is
19:43 going on on the infrastructure and the
19:45 clients and what is going on the radius
19:47 side and as i said april cloud is a
19:50 place where we are stitching all of this
19:52 together right
19:54 so here you are going to basically see
19:56 that when i've had an authorization
19:58 failure like in an authentication fail
20:00 exactly why did the authentication fail
20:03 did your certificate like can i have an
20:05 expired year was it incorrect so on and
20:08 so forth right
20:11 yes franco so the radius server is in
20:14 the cloud and you're getting all of that
20:15 regis log into marvis for
20:18 that is exactly correct right it's a
20:20 very resilient high availability
20:21 architecture with like you know lots of
20:24 geo-redundant pods that are going to and
20:26 and i'm probably getting a two-bit ahead
20:28 of myself we will come back and do an
20:30 architecture deep dive but to answer
20:32 your question simply yes so we are
20:35 taking all of the data the cloud is
20:36 where
20:37 uh we configure the cloud is where we
20:39 get visibility but the radius
20:41 authentication really happens
20:43 at a point of presence closer to the uh
20:46 to the user location okay yes it was
20:49 this integrate with something like
20:50 eduroam so if i've got
20:52 it will different like you know
20:54 eventually that is the goal
20:56 whatever mechanisms we have today like
20:58 you know whether it's hotspot 2.0 uh
21:00 like you know to be the like you know
21:02 kind of the provider for a clearing
21:04 house or
21:06 uh like you know all of your
21:08 social social credentials all of that is
21:11 going to be stitched and come under this
21:13 umbrella
21:14 open roaming right
21:17 so so so francois and raul um
21:20 what mist has done
21:21 to the wireless players in the industry
21:24 when when we started
21:26 is what we're planning to do
21:29 what this is going to do for ice and
21:31 clear pass right
21:32 completely step function change the
21:35 paradigm
21:36 of how
21:37 policy get administered natively
21:41 to the systems and cloud native right
21:44 so france what to your point the radius
21:47 server is not in the cloud it the radius
21:50 server is the missed cloud right so um
21:54 so anyway um we're not ready for uh for
21:58 pilots and and production yet
22:00 but we're excited we're we're just
22:02 showing you the progress we're making um
22:05 i think uh we're gonna put the industry
22:07 on notice um on uh when this truly comes
22:10 out uh it's going to be
22:12 an
22:13 exciting uh sort of a turn in in the
22:16 industry in terms of policy and
22:19 thank you very much for everybody that
22:20 was that are watching the live stream uh
22:23 if you're watching this recording uh you
22:25 know post process
22:26 or uh for uh for all the delegates um
22:29 sort of um uh in the room uh truly again
22:32 as as we started um you are part of our
22:35 extended family you you've really helped
22:38 us uh uh through throughout this journey
22:41 and um and you know i hope what you saw
22:44 today is is very simply a manifestation
22:48 of our sort of client to cloud strategy
22:51 of continuing to add you know breadth um
22:55 and depth uh in this client-to-cloud
22:57 journey and obviously there's a lot more
23:00 to do there is a lot more we can do
23:02 everal to your point of things we can do
23:05 so the last thing i will tell you you
23:07 know what is around the corner and what
23:09 is uh you know exciting as we as as the
23:12 year unfolds for us is where does marvis
23:14 go
23:16 um
23:16 where we think marvis can go is imagine
23:19 if marvis had an army of minions
23:22 you know doing things and and learning
23:26 and and coming back and reporting and
23:28 and asserting on the network
23:31 before a user a single individual user
23:35 has to suffer
23:36 we believe there is a
23:38 even better future on on we could get to
23:43 ai that is not predictive not reactive
23:47 but
23:48 100 proactive
23:50 before users experience a single failure
23:53 so there's a lot more we're excited
23:55 about what's around the corner for us
23:57 think of mario's marvis with a bunch of
23:59 minions uh you know checking out the
24:02 network and validating it for you




