What is firewall design?
What is firewall design?
Firewall design includes an organization’s overall security policy decisions such as which firewall features to use, where to enforce the firewall, and, ultimately, how to configure the firewall.
How Does Firewall Design Work?
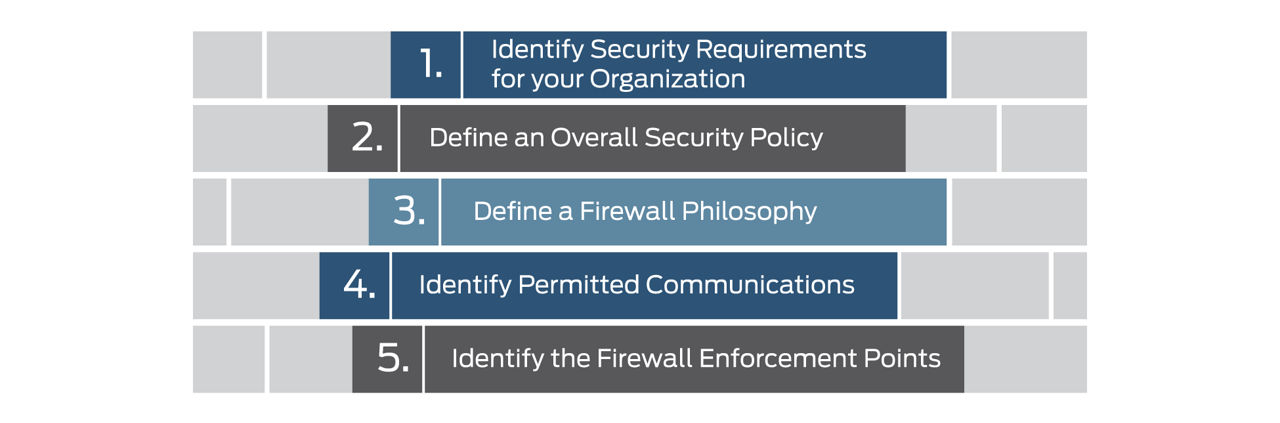
The five sequential steps to follow when designing a firewall include:
- Identify security requirements for the organization. Evaluate security requirements, assess security posture and use the information in defining the security requirements.
- Define an overall security policy. A well-defined security policy includes network resources, access policies and authorization controls and ensures that the firewall addresses all security requirements.
- Define a firewall philosophy. Identifying resources, applications, and services to be protected against threats from outside the organization and insider attacks makes it easier to define and configure the firewall.
- Identify permitted communications. Define an acceptable use policy to specify the types of network activities such as applications that are allowed and denied on the LAN and the Internet Web services.
- Identify the firewall enforcement points. Determining enforcement points is fundamental to firewall design. Firewalls are deployed at the edge, between the private LAN and a public network, such as the Internet.
As measures of protection, develop a network traffic baseline profile that identifies network’s normal traffic patterns. Setting a baseline enables measuring irregular behavior and then setting thresholds to protect against attacks.
Problems Firewall Design Addresses
Firewall technology has evolved from packet filter firewalls to next-generation firewalls. New services and solutions have emerged to address the complexity of the cyber landscape, to protect resources, and to block attempts by cyber attackers to breach the firewall for nefarious purposes. Deploying an effective firewall for the network entails a great deal more than configuration. The best practices contribute to creating a security policy, enhancing the firewall design and configuration process, and deploying a firewall that meets the security requirements for the network.
What Can You Do with Firewall Design?
Best practices recommend that characterizing the network, documenting security posture, and determining the organization’s position in regard to security.
- Identify network resources and security requirements.
- Identify known threats and how to deal with attacks.
- Document operating systems, versions, and applications.
- Define organization’s workflow for allowed communications, access rights based on employee roles and user requirements.
- Determine the firewall enforcement points: deploy a firewall to protect the edge (Internet-facing), the core (corporate-facing), or the DMZ (bastion first line of defense)
- Design the firewall for simplicity.
As measures of protection, develop a network traffic baseline profile that identifies network’s normal traffic patterns. Setting a baseline enables measuring irregular behavior and then setting thresholds to protect against attacks.
Juniper Networks Implementation
Juniper Networks SRX Series devices implement firewall security services, design and deployment simplicity that includes creating zones that are specific to functional requirements, separating groups of users from servers, assigning groups of users to a zone based on the group’s subnet and designing policies for the organization.

