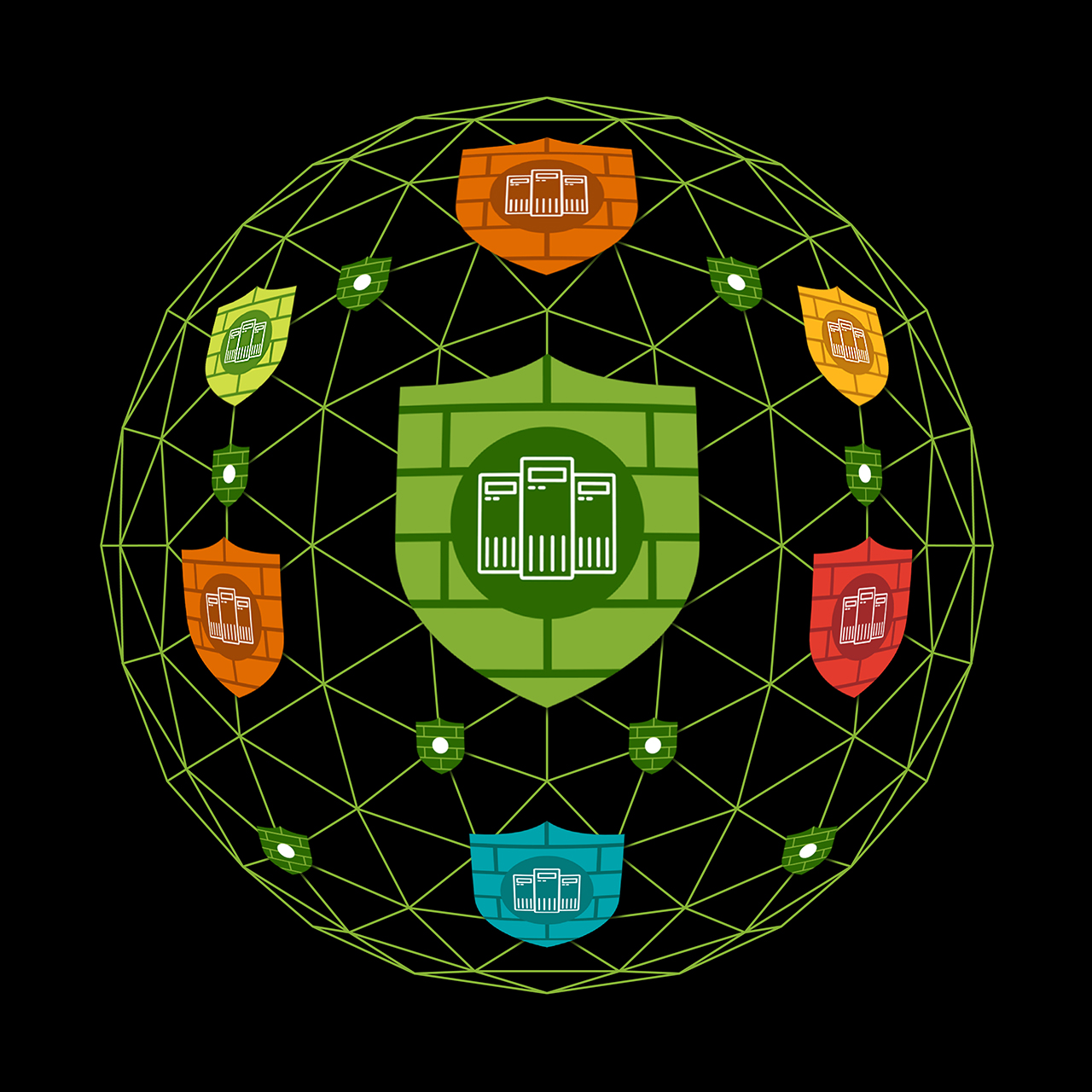
Operationalize security across your entire network with Juniper Connected Security
Security operators taking on architectural transformations must do so without compromising the user experience or increasing the risk of unauthorized access to applications and data. Juniper Connected Security helps you operationalize security across the entire network by enabling the network to take an active role in its own defense.
With a unified management experience that uses a single policy framework, you can easily extend security from client to workload for a seamless and secure transition to the cloud and other distributed architectures. Juniper Connected Security applies visibility, intelligence, and policy enforcement across every point of connection—from the edge to the data center—to help you operationalize security, adopt zero-trust architectures, and protect the business.
Benefits of Juniper Security Products
Visibility
Gain visibility to the entire network, from endpoint to edge and every cloud in between.
Intelligence
Automatically recognize threats, regardless of attack vector.
Enforcement
Every point of connection on the network, no matter how small, acts in its defense.
CUSTOMER SUCCESS
AI-driven, zero trust network yields business agility for AmeriTrust
AmeriTrust, a specialty insurance commercial underwriter and administration services company, looked to digital transformation to fuel growth. It embarked on an ambitious effort to streamline IT operations, strengthen cybersecurity, and drive business success in an unpredictable and changing world.


Juniper Threat Labs Podcast Series
Get rapid and actionable threat insights from world-class security researchers in the Juniper Threat Labs podcast series. Listen in as Mounir Hahad and Mike Spanbauer of Juniper Networks dive into the latest top-of-mind threat activity.
You'll learn
- Where the threat is coming from
- How the threat is disguised
- How to protect your organization
Recommended Content
Achieve Zero Trust with Hybrid Mesh Security
Learn how Juniper Connected Security helps you achieve more effective security across every point of connection on the network.

10 Elements of a Zero Trust Data Center
Interested in bringing zero trust principles into your data center? Discover what it truly means to have a zero-trust data center and the best practices you need to implement to protect your data and applications across physical data centers, private clouds, and public cloud environments simultaneously.
Resource Center
Practical Resources
Trials
Day One Books
Learn More
Products
Solutions
Gartner, Critical Capabilities for Network Firewalls, 16 May 2023, Adam Hils, Rajpreet Kaur, Thomas Lintemuth.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.