Deploy vSRX Virtual Firewall in Google Cloud Platform
The following procedures describe how to deploy vSRX Virtual Firewall in the Google Virtual Private Cloud (VPC):
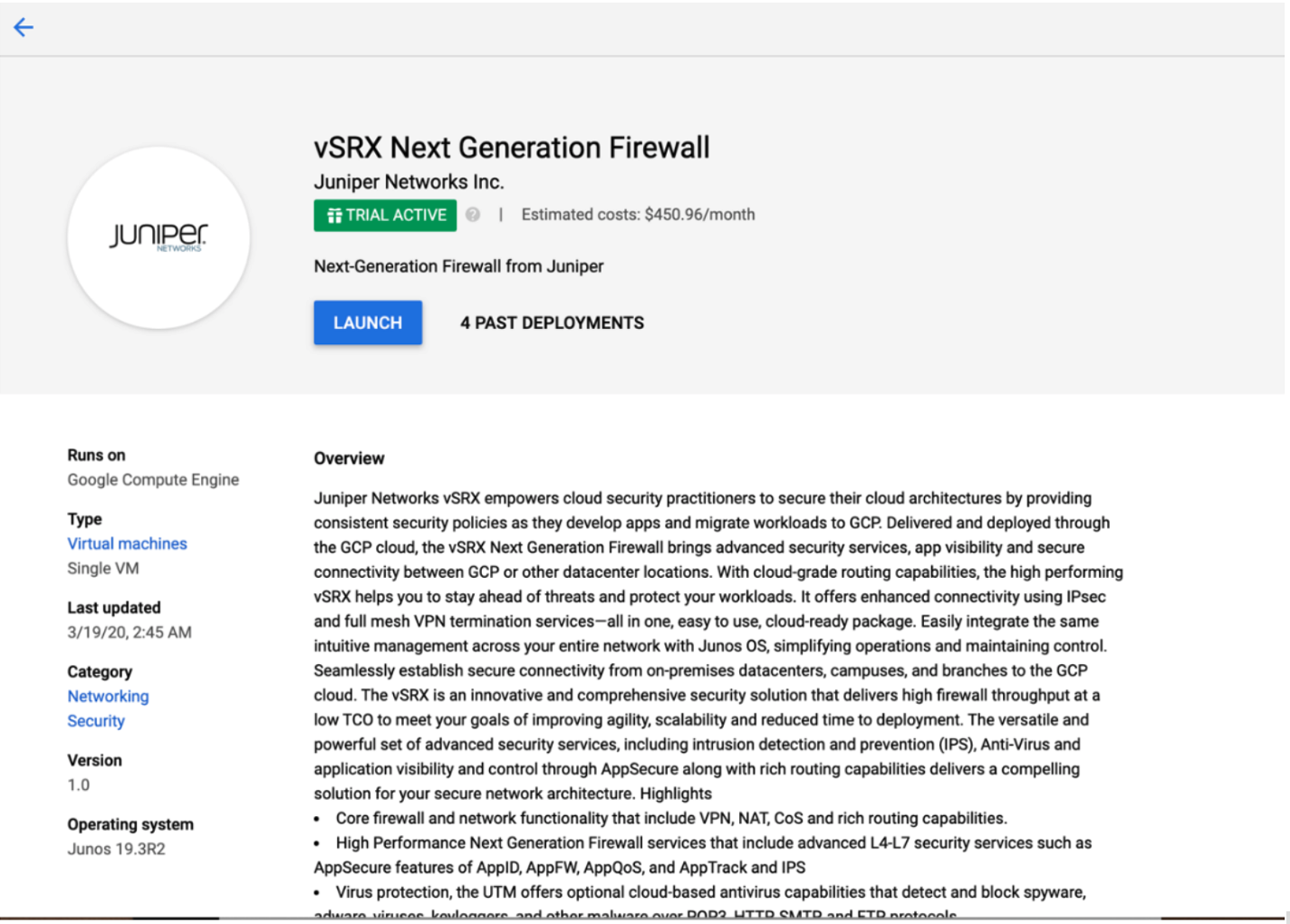
Deploy the vSRX Virtual Firewall Firewall from Google Cloud Platform Marketplace.
Use custom private image to deploy the vSRX Virtual Firewall Firewall from the GCP portal.
Use cloud-init to deploy the vSRX Virtual Firewall Firewall through gcloud using CLI.
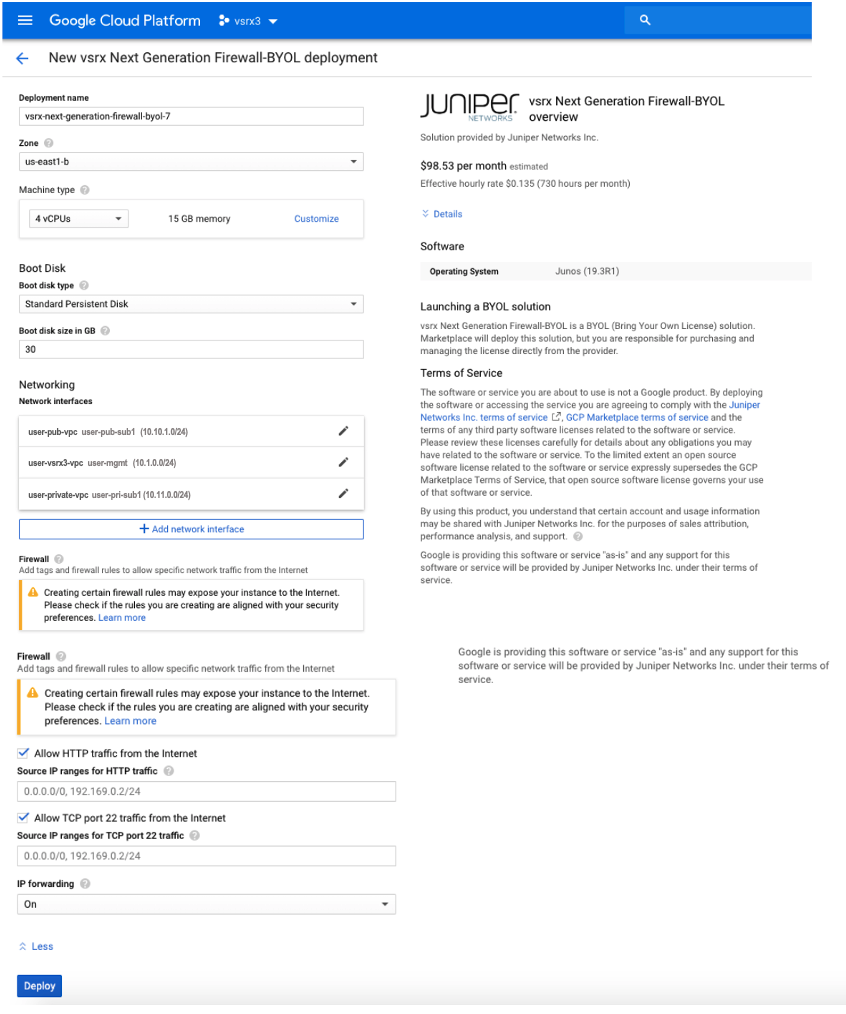
Deploy the vSRX Virtual Firewall Firewall from Marketplace Launcher
You can use the Google Cloud Platform Marketplace to deploy your vSRX3.0 with licenses as avirtual machine(VM) running on a Google Compute Engine instance.
Before you deploy the vSRX Virtual Firewall, you must create or choose a project in your organization and create any networks and subnets that will connect to the firewall. You cannot attach multiple network interfaces to the same VPC network. Every interface you create must have a dedicated network with at least one subnet.
This topic provide your step to deploy a vSRX Virtual Firewall Firewall from the Google Cloud Platform Marketplace Launcher.
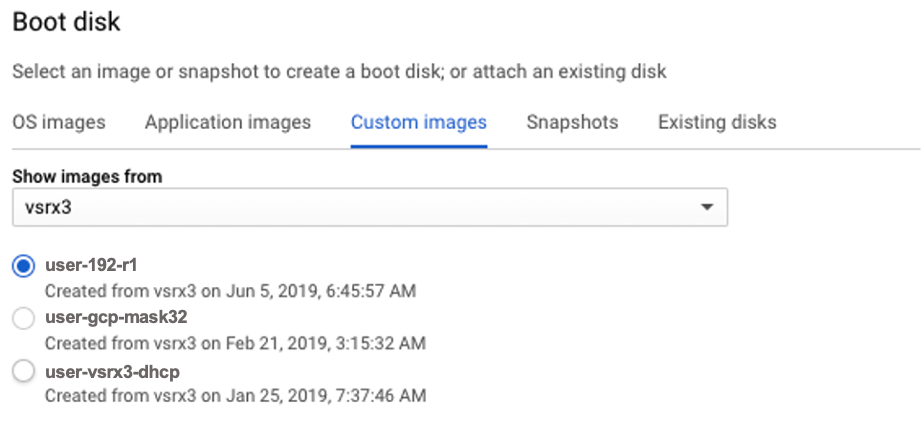
Deploy the vSRX Virtual Firewall Instance from GCP Portal Using Custom Private Image
You can also use your custom private image to deploy the vSRX Virtual Firewall instead of deploying an image from GCP marketplace. Firstly you need upload the private image to Google Cloud storage, then create compute image in GCP, and then deploy vSRX Virtual Firewall on Google Compute Engine.
Watch the video Deploying vSRX Virtual Firewalls on Google Cloud Platform to understand how you can deploy vSRX Virtual Firewall instances from GCP.
- Upload vSRX Virtual Firewall Image to Google Cloud Storage
- Create vSRX Virtual Firewall Image
- Deploy the vSRX Virtual Firewall Firewall from GCP Portal
Upload vSRX Virtual Firewall Image to Google Cloud Storage
To upload vSRX Virtual Firewall image to Google Cloud Storage:
Upload image through SDK shell:
Install Google Cloud SDK on Ubuntu.
You must install Google Cloud SDK on your operation system. below is the sample to install it on Ubuntu.
For more information on Google Cloud SDK installation on Ubuntu, see https://cloud.google.com/sdk/docs/quickstart-debian-ubuntu and for Gcloud command-line tool overview, see https://cloud.google.com/sdk/gcloud/.
To upload image through SDK shell:
Create google cloud storage.
gs://vsrx-imageCopy disk.raw to cloud storage.
gsutil cp vsrx-0115.tar.gz gs://vsrx-image
To upload image from Google Cloud Platform portal.
Click Storage->Create Bucket->Upload files as shown in Figure 6.
Figure 6: vSRX Virtual Firewall Image Upload from GCP Portal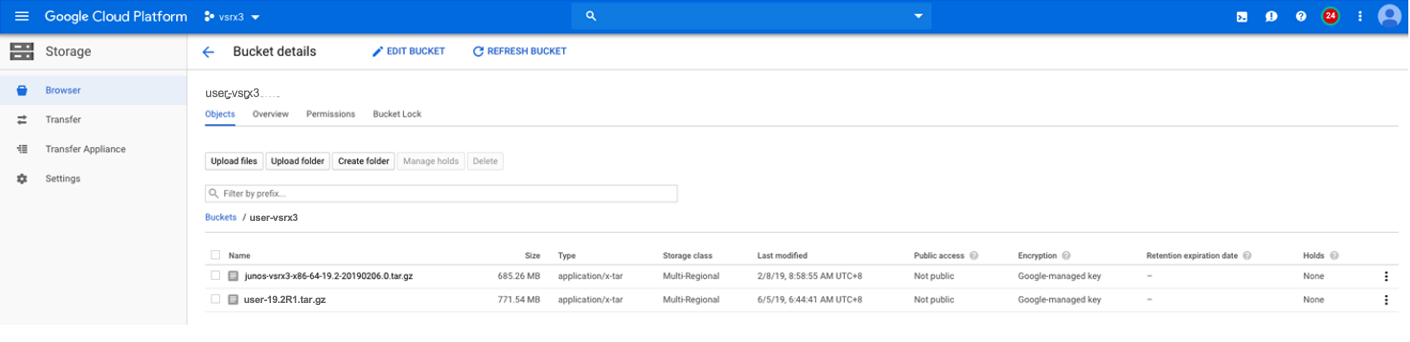
Check the private image is available in Google Cloud Storage by selecting Storage -> Bucket detail in Google Cloud Platform web as shown in Figure 7.
Figure 7: View Private Images in GCP Portal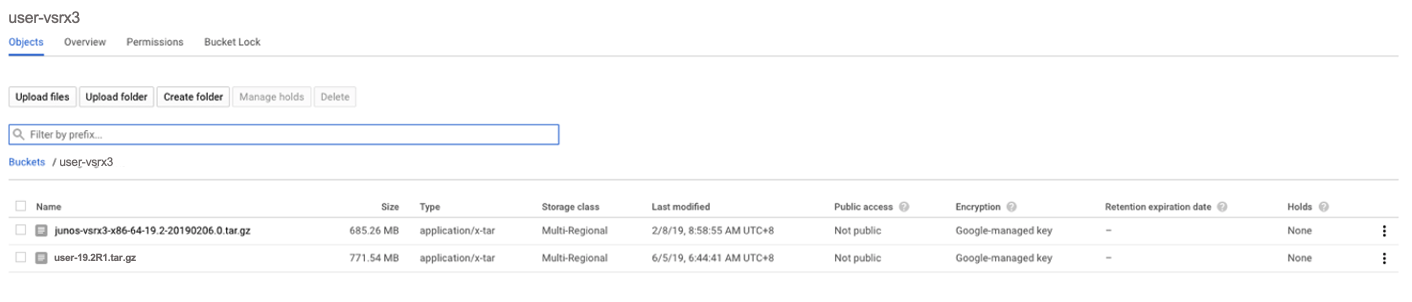
Create vSRX Virtual Firewall Image
After you upload the vSRX Virtual Firewall image file to GCP storage you need to create GCP compute image for vSRX Virtual Firewall deployment.
Using Google Console
You can rename the image file using the Google console as well.
Log in to your Google account and open the Google Cloud Platform home page.
Click theimages option on the Google Cloud Platform page. The Create an image page opens as shown in Figure 8
Figure 8: Google Cloud Platform Image Creation Page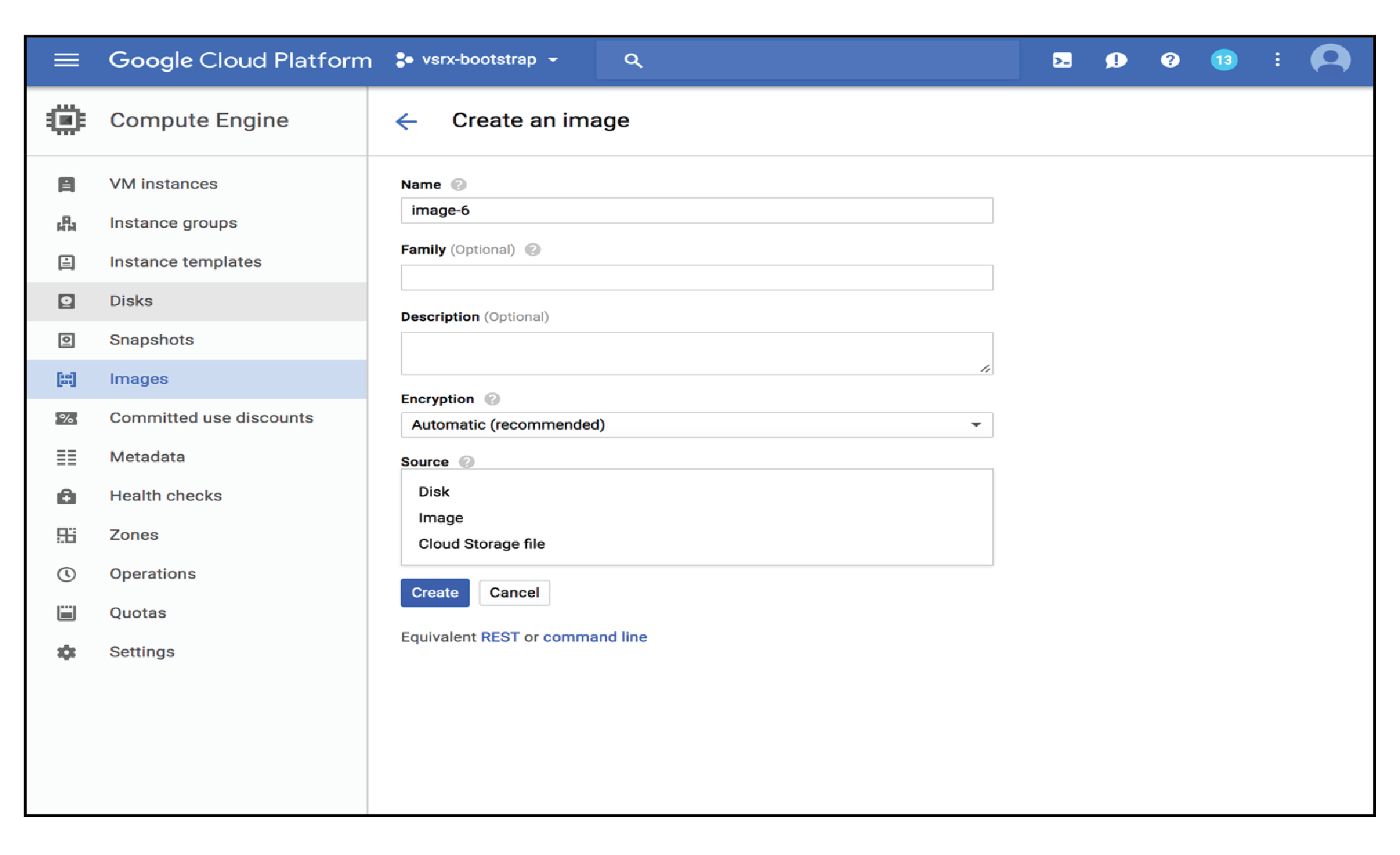
Fill in the required details in the Create an image page and click Create.
Note:It is mandatory to use “gcp-user” as username when you login to the vSRX Virtual Firewall for the first time vSRX Virtual Firewall.
Check the private image that available in Google Cloud Compute Engine. On Google Cloud Platform web, click Compute Engine->Images as shown in Figure 9.
Figure 9: Check Private Image in Google Cloud Compute Engine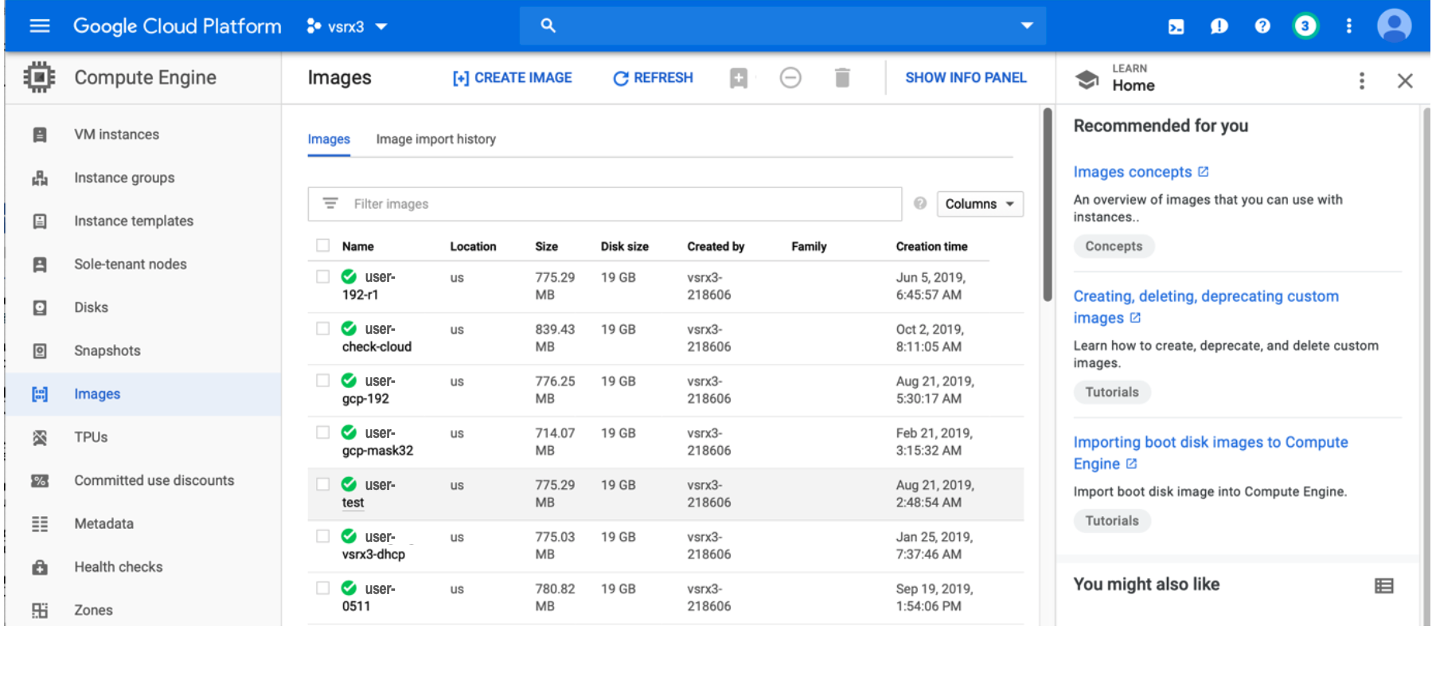
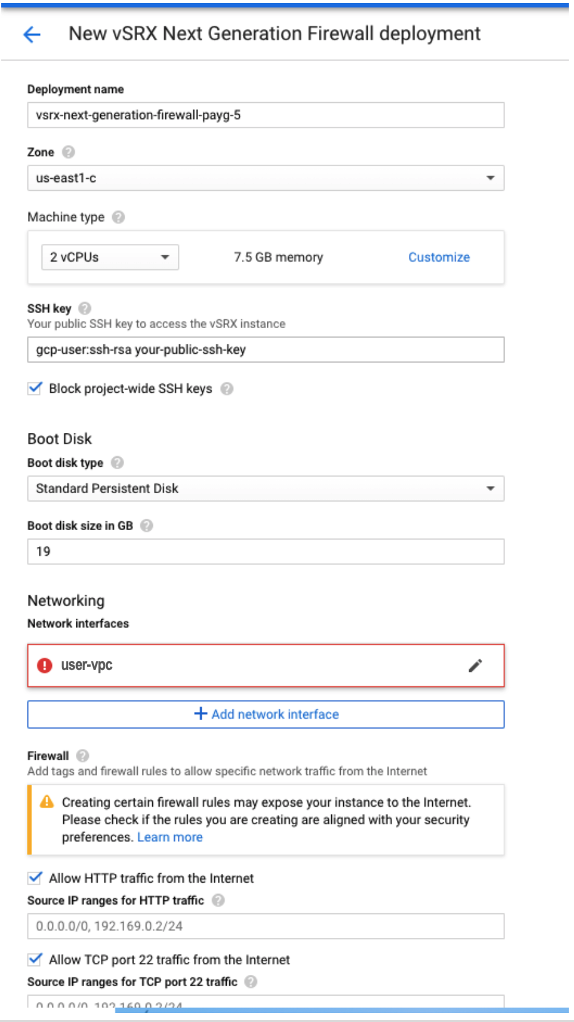
Deploy the vSRX Virtual Firewall Firewall from GCP Portal
You can follow below steps to deploy a vSRX Virtual Firewall instance:
Deploy the vSRX Virtual Firewall Firewall Using Cloud-init
vSRX Virtual Firewall supports cloud-init. Cloud-init is an open-source multi-distribution package that handles early initialization of a cloud instance. It allows user to customize VM instance with attributes like hostname and default IP on the first boot. Cloud-init is particularly useful when user wants to deploy large number of VM instances in the data center using automation tools.
Some of the initial provisioning parameters for first boot are:
Hostname
Root password
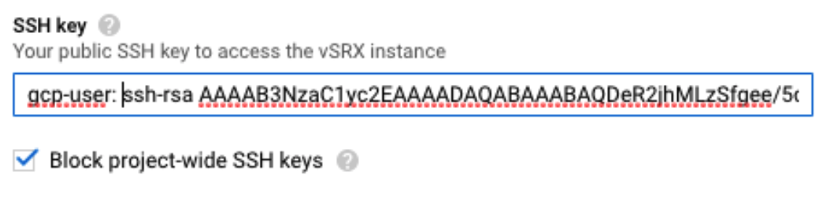
SSH public key
Note:for the ssh key file, it needs to be in the format "<username>:<key value>" as required by google cloud. Something like this:
Management interface (fxp0) IP
Default gateway IP
You can deploy vSRX Virtual Firewall Firewall using cloud-init in two ways:
From Google SDK
To deploy vSRX Virtual Firewall with cloud-init from Google portal, see Deploy the vSRX Virtual Firewall Firewall from GCP Portal. To add user-data to have cloud init enabled specify the metadata.
GCE supports cloud-init type instance configuration. To launch instance with user data, use the command below as an example.
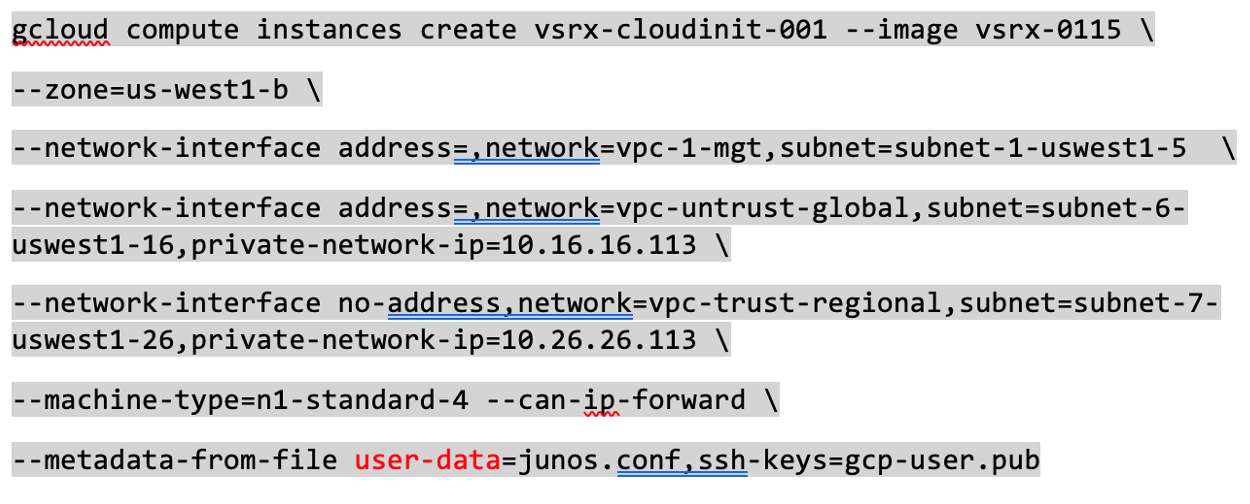
Please note the following points:
junos.conf is configuration file with ‘#junos-config’ in content
gcp-user.pub is ssh public key
vSRX Virtual Firewall 3.0 supports RSA key pair only
For the SSH key file, it needs to be in the format <username>:<key value> as required by Google cloud. Refer the sample SSH key file below.
root@cnrd-kvmsrv37:~# cat gcp-user.pub ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDeR2jhMLzSfgee/5cnduTa+13yVLKbTa/ OFnZSHQsZoA5LKHIXs/TbyooZTX5PnfNr6hx2Iyxjaodu01kT0UJ87wps8n9BH74DP6x0YK07OaZZl5T/ 5Iso9fXRCzl9+go9vKzNKhqXmqKUc3Fl6hTX2QzQbtrwN2twLzCxz+OSliCoobJr+/ 8wPcvI6fUbL6FRTgE1zC1HBlDKspK7x47YDYPJlUcyMhRtGvxd319jrx5i96mZq850+ dCfZkHSipT09hFRtk8C4MsOaKsw3RWUCY5LCPekrutrLLfhMKh88onv4ud7gXOklSwgVVod49aY2FfiaACMAVoaomfYXweP gcp-user ssh -i <private-key> gcp-user@<vSRX management public ip>
In junos.conf, please remove the “gcp-default” block in your user data. They will shadow the one created by vSRX Virtual Firewall init script. Refer the sample junos config
#junos-config security { policies { default-policy { permit-all; } } zones { security-zone trust { interfaces { ge-0/0/0.0; } } security-zone untrust { interfaces { ge-0/0/1.0; } } } } interfaces { ge-0/0/0 { unit 0 { family inet { 10.0.0.10/24; } } } ge-0/0/1 { unit 0 { family inet { 10.0.1.10/24; } } } }Note:gcloud connect to vSRX Virtual Firewall is not supported. Always use ssh with user provided key to connect to vSRX Virtual Firewall after instance is up.