Overview of Service Chains with vSRX Virtual Firewall
You can use Contrail to chain various Layer 2 through Layer 7 services such as firewall, NAT, and IDP through one or more vSRX Virtual Firewall VMs. For example, you can insert a vSRX Virtual Firewall firewall VM between two other virtual machines (VMs). By using vSRX Virtual Firewall and service chains, you can tailor the security needs to a targeted virtual network and VM set. This provides agility and scalability in line with the fluidity of cloud network environments.
Understanding Service Chains
To create a service through vSRX Virtual Firewall, you instantiate one or more vSRX Virtual Firewall VMs to dynamically apply single or multiple services to network traffic.
Figure 1 shows a basic service chain with a single vSRX Virtual Firewall VM. The vSRX Virtual Firewall service VM spawns a service, such as a firewall. The left interface (left IF) points to the internal end customer, who uses the service; and the right interface (right IF) points to the external network or Internet. You can also instantiate multiple vSRX Virtual Firewall VMs to chain multiple services together. For example, you could add an IDP service after the firewall.
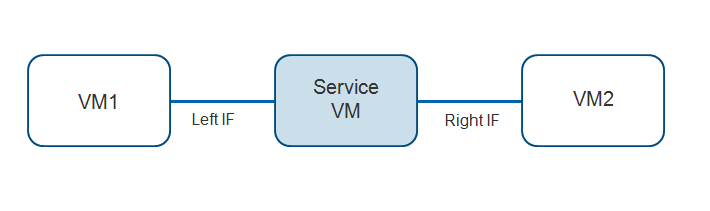
When you create a service chain, Contrail creates tunnels across the underlay network that span all services in the chain.
Service Chain Modes
You can configure the following service modes:
Transparent or bridge mode—Used for services that do not modify the packet. Also known as bump-in-the-wire or Layer 2 mode. Examples include Layer 2 firewall and IDP.
In-network or routed mode—Provides a gateway service that routes packets between the service instance interfaces. Examples include NAT, Layer 3 firewall, and load balancing.
In-network-nat mode—Similar to in-network mode; however, packets from the left (private) network are not routed to the right (public) source network. In-network-nat mode is particularly useful for NAT services.
Note:Ensure that you define the service policy with the private network on the left and public on the right in order to get the public routes (usually the default) advertised into the left network.
Components of a Service Chain
Service chaining requires the following configuration components to build the chain:
Service template
Virtual networks
Service instance
Network policy
Service Templates
Service templates map out the basic configuration that Contrail uses to instantiate a service instance, or VM. Within Contrail, you configure service templates in the scope of a domain, and you can use the templates on all projects within a domain. You can use a template to launch multiple service instances of the same type in different projects within a domain. Within a service template, you select the service mode, a vSRX Virtual Firewall image name for the VM that will provide the service, and an ordered list of interfaces for the service. vSRX Virtual Firewall service VMs require the management interface to be the first interface in that ordered list. You can use OpenStack Horizon or Glance to add the vSRX Virtual Firewall image. You also select the OpenStack flavor to associate with all service instances that use the service template. An OpenStack flavor defines the number of vCPUs, storage, and memory you can assign to a VM. OpenStack includes default flavors, and you can create new flavors in the OpenStack dashboard.
Virtual Networks
Virtual networks provide the link between the service instance and the network traffic in the virtualized environment. You can create the virtual networks in Contrail or OpenStack and use those networks to direct traffic to or through the service instance.
Service Instances
A service instance is the instantiation of the selected service template to create one or more VMs that provide the service (for example, a firewall). When you create a service instance, you select a service template that defines the instance. You also associate the interfaces in the service template with the virtual networks needed to direct traffic into and out of the service instance. If you enable service scaling in the selected service template, you can instantiate more than one VM when you create the service instance.
Network Policies
By default, all traffic in a virtual network remains isolated. You configure a network policy to allow traffic between virtual networks and through the service instance. The network policy filters traffic to and from the service VM based on the rules you configure. You select the service instance VM and the virtual networks for the right and left interfaces of that VM that the network policy applies to. As a final step. you associate the network policy with each virtual network the policy applies to.
